CensEye
CensEye helps you identify assets on the internet that share a specific key-value pair with the asset you are currently viewing. It extracts data values then shows how many other assets present the same value. This allows you to pivot into related infrastructure and begin building queries based on shared characteristics. CensEye can also be executed via API.
CensEye saves you time during investigations and supports the creation of queries or fingerprints to identify activity linked to specific methods, indicators, or threat actors—even those that may not have been fingerprinted or categorized already.
Once you identify related assets, you can group and monitor them using collections. Collections enable you to track threat-related infrastructure over time. Use webhooks with collections to receive alerts about new assets affiliated with a threat in near-real-time.
NoteRead this detailed blog written by a Censys team member to learn about how to use CensEye for advanced threat hunting.
Video walkthrough
Use CensEye in the Platform web UI
To use CensEye:
- In the Platform web console, go to an asset.
- Click the Discover Pivots tab.
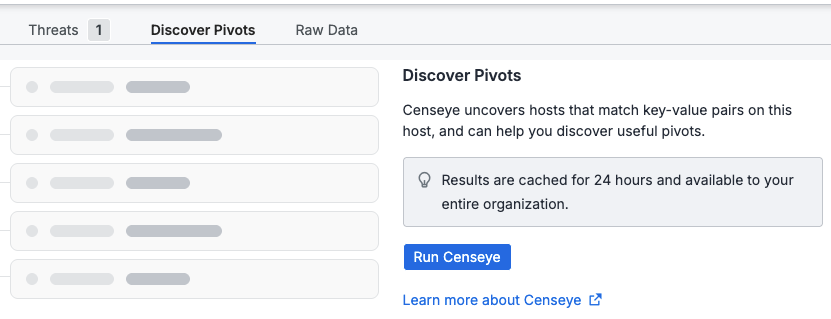
-
Click Run CensEye.
-
Review the extracted key-value pairs.
CensEye identifies key-value pairs that the asset shares with other data records. In the screenshot below, the number to the left shows how many internet-facing assets share the same attribute for the indicated field-value pair.
This data can be used to pivot from one asset to a broader set of related infrastructure that share the same attribute. You can track patterns across assets with similar characteristics and investigate the assets to determine shared usage or intent.
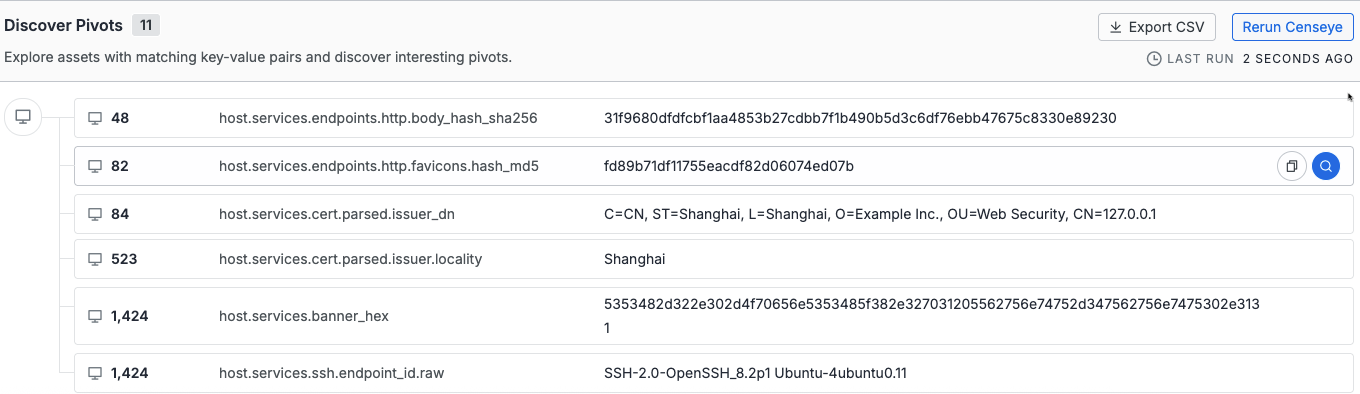
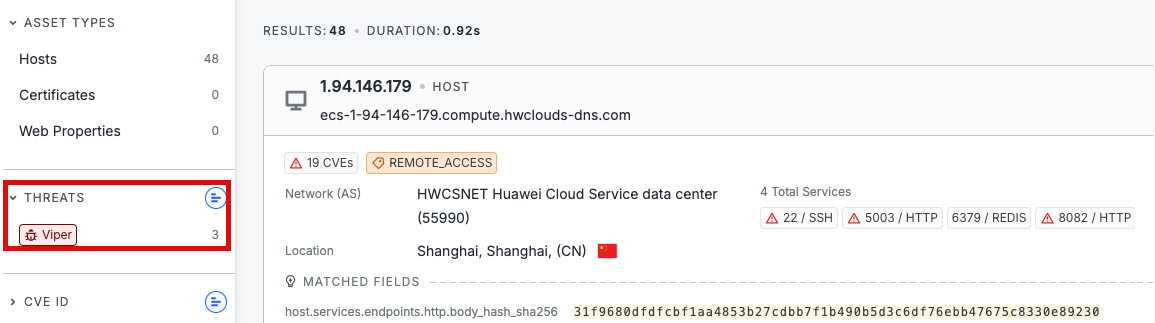
- Click 🔍 to the right of the key-value pair to execute a search. Using the example above, a search is executed the
host.services.endpoints.http.body_hash_sha256field-value pair. - The search returned 48 assets. Filter the data to isolate the most relevant infrastructure. In the left-hand navigation, the Threats filter shows that 3 of these assets are associated with Viper malware. At this point, you might look for other outliers such as unusual port numbers.
NoteWhen you use CensEye on a historical host record, the key-value pairs are obtained from the historical appearance of that host and compared against current data.
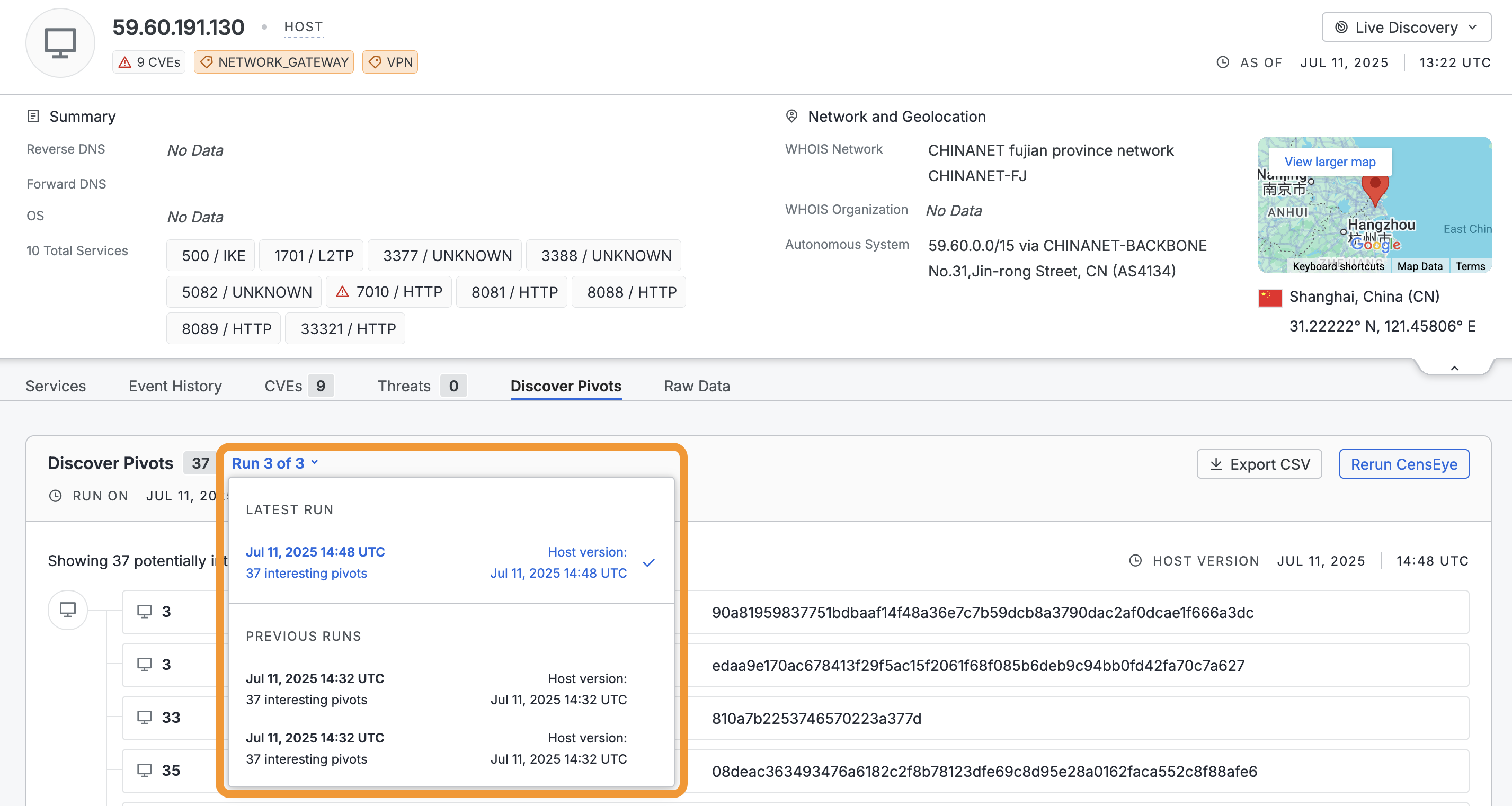
View historical CensEye runs
You can see previous CensEye runs against web assets executed by members of your organization by clicking the run count dropdown within the Discover Pivots tab. Each historical run lists its timestamp and the number of interesting pivots discovered. Click the entry for a historical run to see the full list of results.
Default pivot fields
CensEye searches across the following fields for assets with matching values. To define specific fields to target with CensEye, use the value counts API endpoint.
Host fields
Banner information
host.services.banner_hexhost.services.banner_hash_sha256
Certificate information
host.services.cert.fingerprint_sha256host.services.cert.parsed.subject_dnhost.services.cert.parsed.subject.common_namehost.services.cert.parsed.subject.organizationhost.services.cert.parsed.subject.organizational_unithost.services.cert.parsed.issuer_dnhost.services.cert.parsed.issuer.common_namehost.services.cert.parsed.issuer.localityhost.services.cert.parsed.ja4x
TLS hashes
host.services.jarm.fingerprinthost.services.tls.ja4shost.services.tls.ja3s
HTTP
host.services.endpoints.banner_hash_sha256host.services.endpoints.http.headershost.services.endpoints.http.html_titlehost.services.endpoints.http.body_hash_sha256host.services.endpoints.http.favicons.hash_sha256host.services.endpoints.http.favicons.name
SSH
host.services.ssh.endpoint_id.rawhost.services.ssh.server_host_key.fingerprint_sha256
Cobalt Strike
host.services.endpoints.cobalt_strike.x64.http_post.urihost.services.endpoints.cobalt_strike.x64.public_keyhost.services.endpoints.cobalt_strike.x64.user_agenthost.services.endpoints.cobalt_strike.x64.watermarkhost.services.endpoints.cobalt_strike.x86.http_post.urihost.services.endpoints.cobalt_strike.x86.public_keyhost.services.endpoints.cobalt_strike.x86.user_agenthost.services.endpoints.cobalt_strike.x86.watermark
Other endpoints
host.services.endpoints.kubernetes.nodes.namehost.services.endpoints.scada_view.title
Other protocols
host.services.cwmp.serverhost.services.pc_anywhere.namehost.services.pptp.hostnamehost.services.smb.group_namehost.services.winrm.ntlm_info.netbios_computer_namehost.services.redline.settings_responsehost.services.mssql.instance_namehost.services.vnc.desktop_namehost.services.s7.plant_idhost.services.bacnet.object_namehost.services.dhcpdiscover.params.device_info.machine_namehost.services.snmp.oid_system.name
Web property fields
Certificate information
web.cert.fingerprint_sha256web.cert.parsed.subject_dnweb.cert.parsed.subject.common_nameweb.cert.parsed.subject.organizationweb.cert.parsed.subject.organizational_unitweb.cert.parsed.issuer_dnweb.cert.parsed.issuer.common_nameweb.cert.parsed.issuer.localityweb.cert.parsed.ja4x
HTTP
web.endpoints.banner_hash_sha256web.endpoints.http.body_hash_sha256web.endpoints.http.favicons.hash_sha256web.endpoints.http.favicons.nameweb.endpoints.http.headersweb.endpoints.http.html_title
TLS hashes
web.jarm.fingerprintweb.tls.ja4sweb.tls.ja3s
Cobalt Strike
web.endpoints.cobalt_strike.x64.http_post.uriweb.endpoints.cobalt_strike.x64.public_keyweb.endpoints.cobalt_strike.x64.user_agentweb.endpoints.cobalt_strike.x64.watermarkweb.endpoints.cobalt_strike.x86.http_post.uriweb.endpoints.cobalt_strike.x86.public_keyweb.endpoints.cobalt_strike.x86.user_agentweb.endpoints.cobalt_strike.x86.watermark
Other endpoints
web.endpoints.kubernetes.nodes.nameweb.endpoints.scada_view.title
Certificate fields
Subject
cert.parsed.subject_dncert.parsed.subject.organizationcert.parsed.subject.organizational_unit
Issuer
cert.parsed.issuer_dncert.parsed.issuer.common_namecert.parsed.issuer.locality
Other
cert.parsed.ja4x
Additional resources
The Censys team maintains the Censeye-NG tool for advanced configuration options and threat hunting.
Updated about 1 month ago
