Threat Data
The Censys threat dataset provides a real-time view of active adversary infrastructure by scanning and mapping malware, threat actors, and tactics to services or endpoints running on exposed hosts and web properties. The threat dataset is continuously updated, empowering you to query the data to identify, investigate, and block threats earlier in the attack lifecycle.
The dataset adds threat-specific objects and fields to host and web property records that Threat Hunting users can search and pivot across. This enriched data powers the Threat Hunting module, enabling you to query threat records, pivot with CensEye to discover related infrastructure, and validate suspicious findings using Live Discovery and Live Rescan.
Threat data is visible on assets in the Platform UI and is retrievable via API.
Censys defines a threat as infrastructure that has identifiable malware fingerprints. Censys identifies threats by matching behavioral patterns, such as fingerprints, protocol responses, or infrastructure traits, to known malware or adversary tooling. Context is provided from URL endpoints associated with generic malware operations. Each threat is tied to a specific service on a host or endpoint on a web property.
NoteThe Censys threat research team identifies scan data attributes that are specific to malware families and develops and updates fingerprints for them. For some malware families, Censys creates and manages more advanced fingerprinting and analysis infrastructure, such as custom scanners for Cobalt Strike or scanning for URL endpoints that are affiliated with specific families.
To attribute malware to specific threat groups, Censys uses a data source called Malpedia that provides up-to-date articles about malware families and threat groups associated with those families.
Threat data in the Platform web UI
Users with access to the threat dataset see additional threat information on host and web property records. To explore threat data in the Platform, you can start from a query you build on the Explore Threats page or any query that targets threat data or returns results with threat data. For example, you can search for hosts running threats identified as C2 servers by running the query host.services.threats.type = "C2_SERVER".
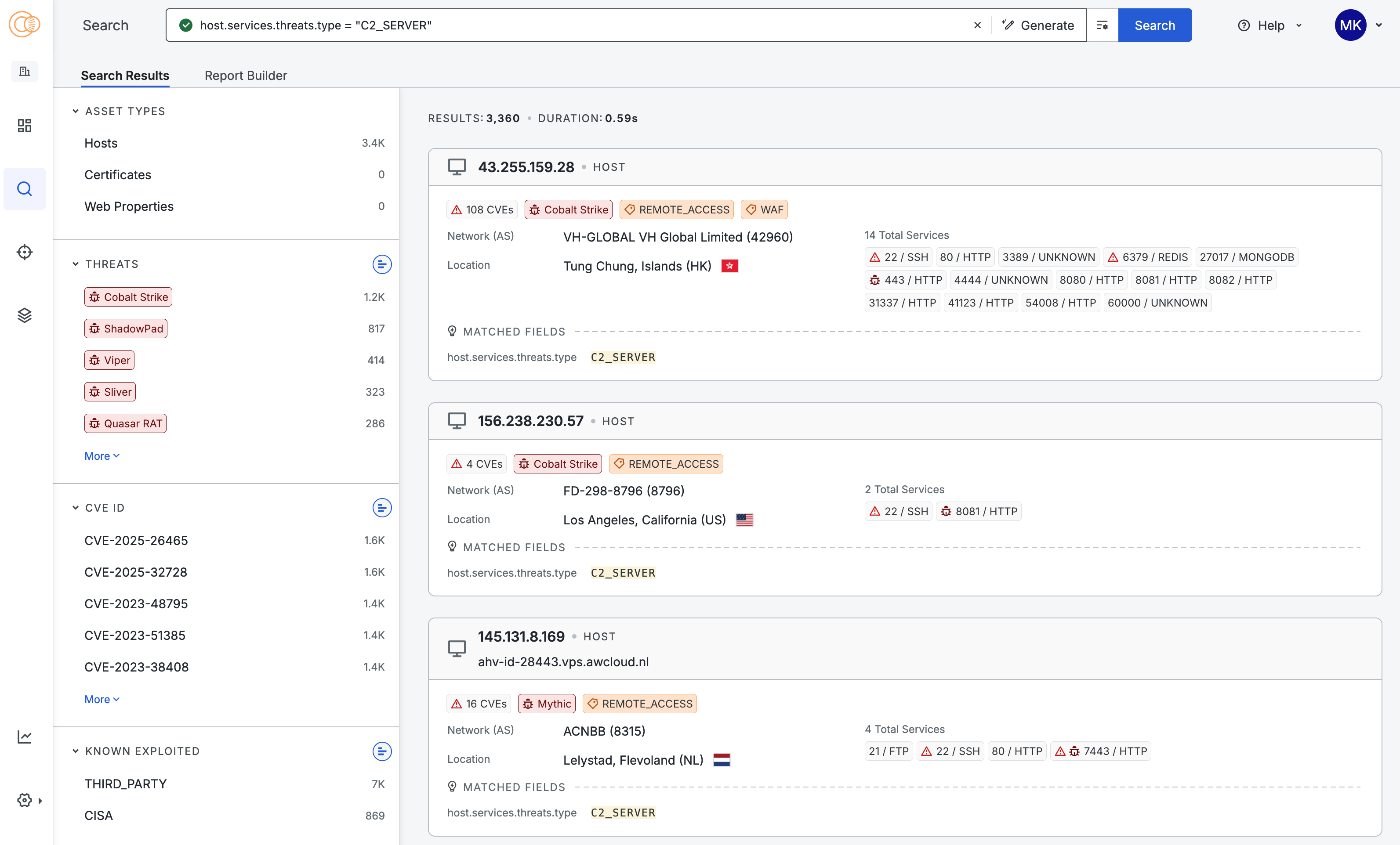
Refine your results using the filters on the left-side panel. The Threat Hunting module provides an additional Threats filter.
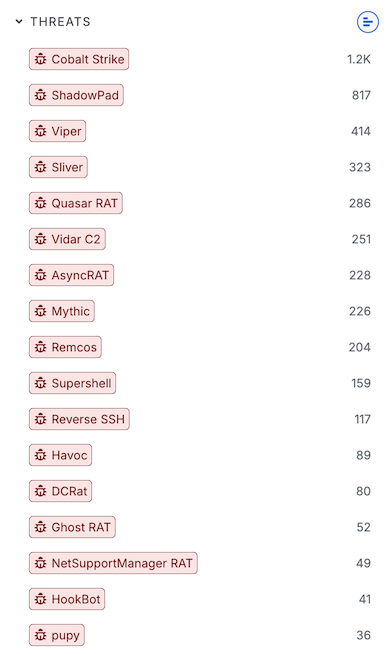
Threat data on host and web property records
In the example host preview card below, Cobalt Strike and Sliver have been detected on the host. Services associated with threats are marked with a bug icon.
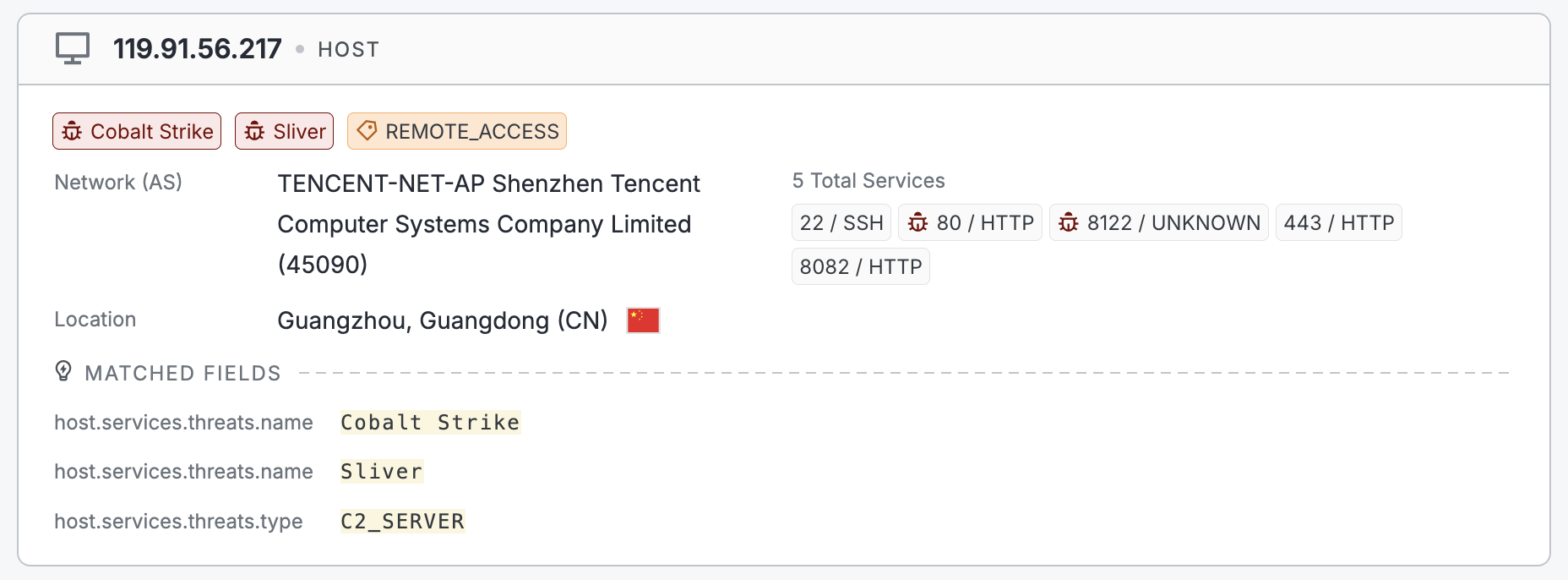
Threats tab
Users with access to threat data see the Threats tab on host and web property assets. Each threat detected on a record is listed in this section.
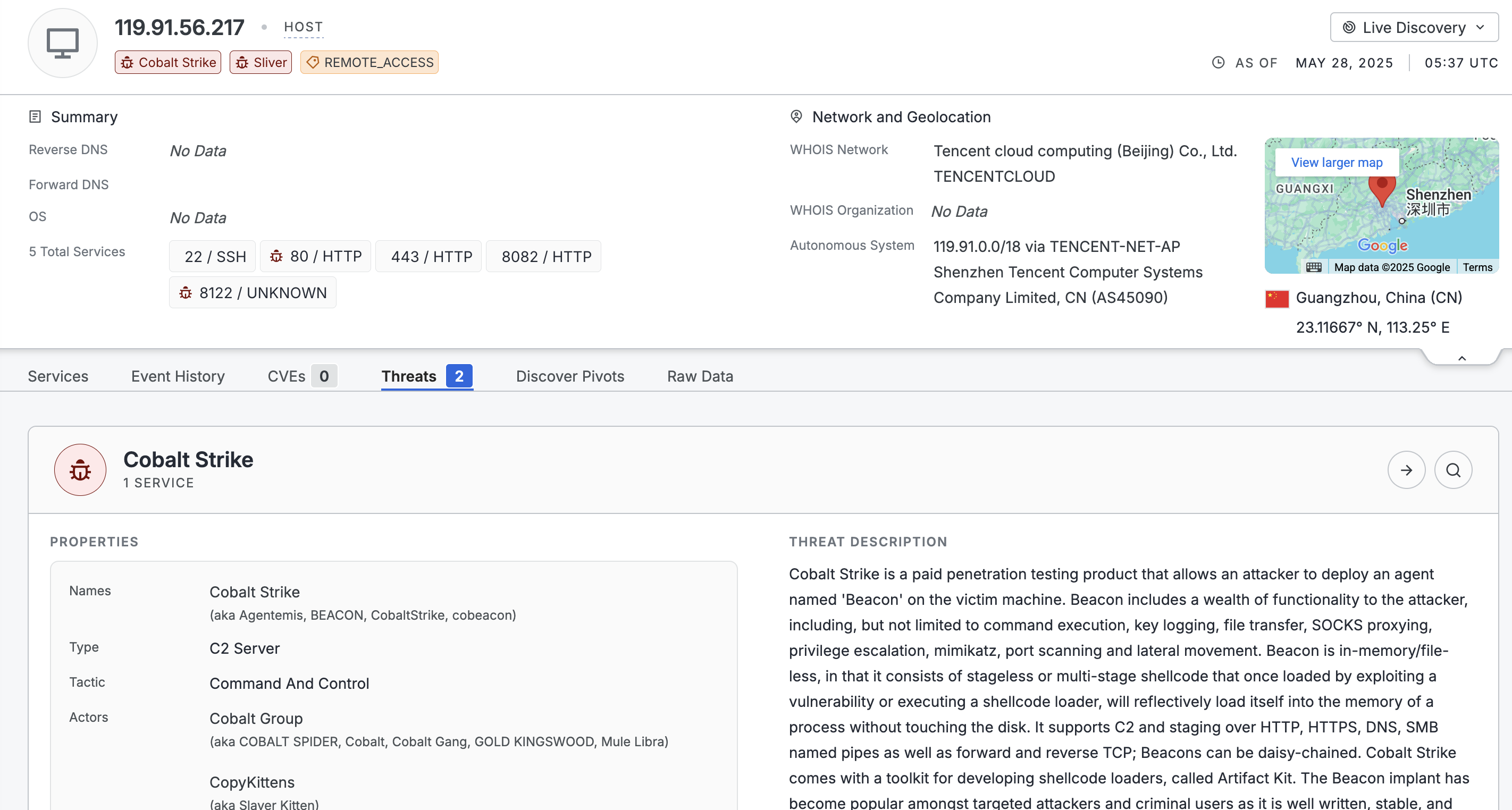
Each threat card contains metadata about the threat including its related actors, type, and associated tactics. At the top of a threat card, click the arrow icon to go to that threat's details page. Click the magnifying glass icon to see all assets associated with the threat.
On hosts, information about the the service the threat was detected on is shown at the bottom of the card. The protocol and port used for the threat, when the service was scanned by Censys, as well as the confidence level associated with the detection are provided in the service section.
Next to service information, click the arrow icon to go to the service information for the threat. Click the magnifying glass icon to run a query for that threat ID and port and protocol pair.

You can use Live Rescan and Live Discovery to examine whether previously scanned services or new services are present on assets.
Threat history
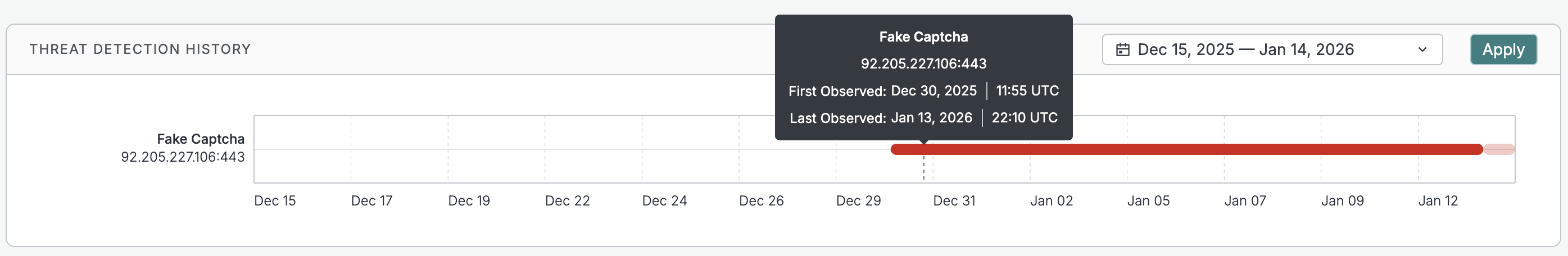
The Threats tab features a chart that shows the historical detections of threat fingerprints on a host or web property. Use this timeline to quickly understand previous threat presence on an asset.
Hover over a plot line to see the first observed and last observed timestamps. By default, the date range displayed is the previous 30 days. Use the date picker to adjust the displayed range.
The Threats tab is shown on assets that have historical threat detections within your historical data window even if the most recent scans of that asset do not show "active" threats.
Threat history visual overlaps
Threat timelines are constructed from discrete scan observations over time. For a given hostname and port or IP and port, scans may briefly identify different protocols (for example, UNKNOWN followed by HTTP) as the service responds differently between scans. These transitions could occur closely in time and represent changes in how the service was observed, not multiple services running simultaneously.
When these rapid transitions are displayed over longer time ranges, they can visually appear to overlap. This does not mean data is duplicated, or that scan results are conflicting. It also does not indicate missing data or a failure in detection. This is a visualization effect and it reflects the underlying scan results as captured by the Censys scanning engine.
Threat evidence
Customers with access to the Threat Hunting module can see the Censys scan data that was used to identify a threat on a host or web property on the threat card.
In the bottom right corner of the card, click See Evidence to view the information that Censys used to determine that the service or endpoint is a threat. Click See raw evidence data to see the values in the Raw Data table.
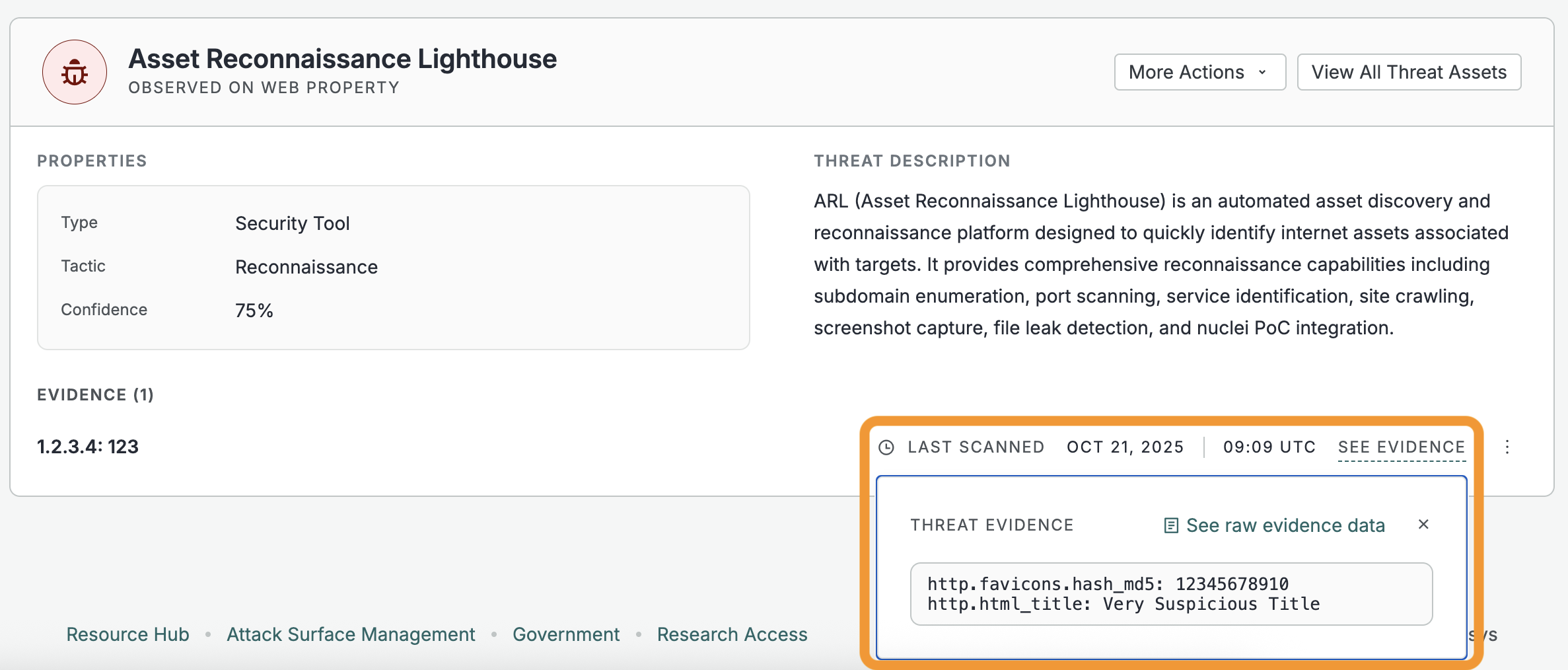
The following evidence data fields are visible to Threat Hunting users and can be retrieved via API.
| Data field | Description |
|---|---|
*.threats.evidence.data_path | The location of the data on the asset used to detect the threat. |
*.threats.evidence.found_value | The value located at the data path that indicates the service or endpoint is a threat. |
Data model structure
The diagram below illustrates how the Platform Threat Hunting module structures threat-related data. The following objects and relationships define how threats are identified, contextualized, and correlated across infrastructure.
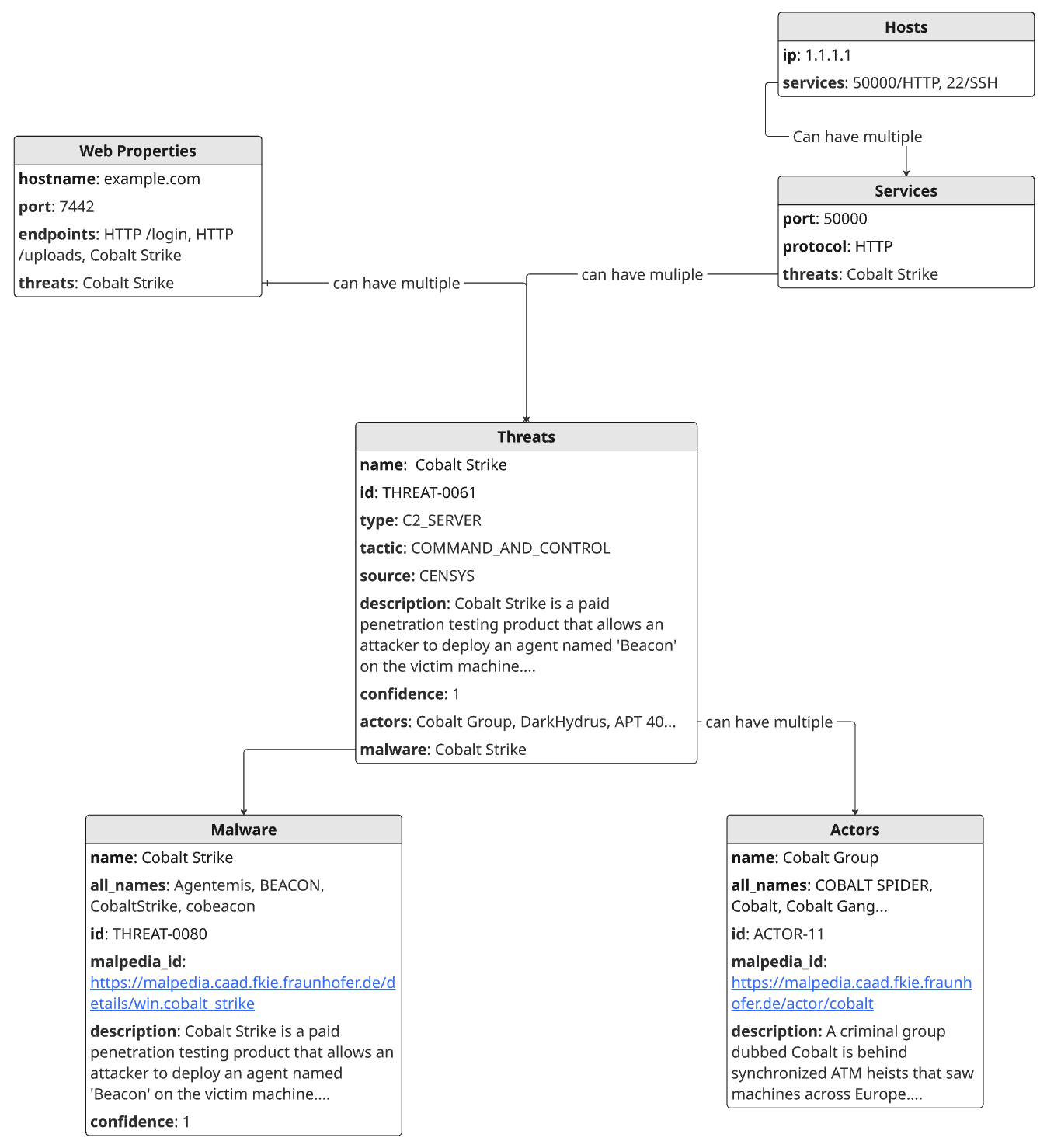
In the diagram above, each object is shown with its corresponding fields. The top-level asset can be a host (1.1.1.1) or a web property (example.com:7442). Hosts can expose multiple services, and threats are detected at the web property and service level. A service (50000/HTTP) may be linked to one or more threats when Censys identifies behavioral patterns, such as HTTP response characteristics or protocol fingerprints. These patterns form the basis of detection.
Each threat is tied to a specific service on a host or endpoint on a web property. Threats include metadata and can be linked to one or more actors and malware. Actors are groups that have used the identified malware in past or current operations. The data connects the presence of this malware on this host or service to the groups known to have used it in the past.
Dataset objects
In the Platform data schema, threat-related data is contained within a threats object on host services and web properties. Threat actors and malware objects are nested within the threats object.
You can see the entire list of threat, threat actor, and malware objects and fields for hosts and web properties on the Data Definitions page in the Platform web UI.
Threat object
A threat object represents an accumulation of relationships between observed infrastructure behavior and known adversary activity. It connects what Censys sees (a pattern on a service) to what Censys knows (malware, tactics, and threat actors). Threat types and tactics offer context to the nature and intent of the threat.
Each threats instance on a host or web property includes:
-
name: Name of the threat,Cobalt Strikefor example. -
id: A unique identifier for the threat. -
description: A detailed description of the threat. -
type: Describes the role of the service, such as C2 server or botnet node. These are available on the Explore Threats page in the Threat Type dropdown. Threat types are described in the following table.Threat Type Description C2_SERVERHosts or web properties running control tooling for malware or deploying malicious payloads. PHISHING_SERVERHosts or web properties related to phishing activity. BOTNET_SERVERHosts infected with malware or running tooling that is directed by a malicious third party. SECURITY_TOOLSecurity testing tools. WEBSHELLHosts or web properties running malicious web-based administration tools. -
tactic: Describes how the threat behaves and the purpose of the activity, such asCOMMAND_AND_CONTROLandPERSISTENCE. -
source: Indicates whether the threat was discovered by Censys or another provider. -
confidence: Measures how reliably Censys identifies a threat on internet-exposed assets. -
malware: The malware a threat is associated with. See below for more information. -
actors: List of actors associated with the malware. These are available on the Explore Threats page, in the Threat Group dropdown. More information on data in theactorsobject is provided below.
Actors object
Actors are groups that have used the identified malware in past or current operations.
Each actors object includes:
primary_name: The top-level name is the primary name used to identify the group, APT40 for example.all_names: Lists all known aliases and names. This makes it easier to search and across different tools, regardless of the naming conventions. In the screenshot above, it's the list of names under APT40.mitre_group_id: The MITRE group ID for the actor.malpedia_group_id: The malpedia group ID.description: A detailed description of the actor.
Malware object
Each malware object includes:
id: A unique identifier for the malware object.primary_name: The primary name Censys uses to identify the malware.all_names: Known names or aliases for the malware, used for threat correlation and search.malpedia_id: The ID for the malware entry in Malpedia.description: A detailed description of the malware.
Context hashes
The Threat Hunting module also contains JA3, JA4, and JARM data for all observed TLS services. This data is contained in objects and fields like host.services.tls.ja3s, host.services.tls.ja4s, host.services.jarm, host.services.jarm.fingerprint, and web.jarm. Learn more about JARM and context hashes here.
Updated 14 days ago
