Explore Threats
The Explore Threats page in the Censys Platform provides you with a centralized view into internet-facing infrastructure linked to malware and threat actors to proactively detect and track adversary activity, uncover patterns, and reduce your organization's attack risk by identifying infrastructure early.
It combines interactive visualizations, curated threat profiles, and simplified filtering to help you quickly identify relevant threats. You can review metadata describing a threat for context on affiliated attacks and actors on its Threat Details page and track these threats in a collection for real-time infrastructure updates.
Using the Explore Threats page, you can take several actions to strengthen your security posture and improve threat intelligence workflows:
- Enrich existing threat intelligence: Correlate threat infrastructure with internal logs, enrich existing threat data, and provide broader context for analysis.
- Inform threat hunting activities: Use the threat dataset as a starting point for advanced hunts to track down clusters of potentially related malicious assets.
- Validate security controls: Continuously update existing security controls (firewalls, proxies, intrusion prevention systems) against the threat infrastructure to identify gaps in coverage.
- Automate alerts and correlation: Configure security tools (SIEM, EDR, etc.) to generate alerts based on webhooks from your collections, enabling near real-time detection of potentially malicious activity within your environment.
- Support incident response efforts: During an active incident, leverage the current and historical threat data from a collection to quickly inform containment and remediation strategies.
NoteCustomers who have purchased the Threat Hunting module have access to threat data throughout the entire Platform. If you have access to the module, threat data and filters will appear for all of your search results when applicable. The Explore Threats page is a central dashboard for navigating Censys threat data.
Use the Explore Threats page
Follow the steps below to begin exploring threats. You can explore threats by type, name, group, and geography.
-
Go to Explore Threats in the left navigation panel of the Censys Platform.
-
Use the dropdown menus at the top of the map to filter the displayed results by Threat Type, Threat Name, and Threat Group. These filters also modify the results shown below the map.
-
The map populates the number of threats along with their geographical locations. When you select values from the threat dropdown menus, it refines the counts for each country and updates the map. For example, the screenshot below has been filtered to show results for the
C2_SERVERthreat type andAsyncRATthreat name.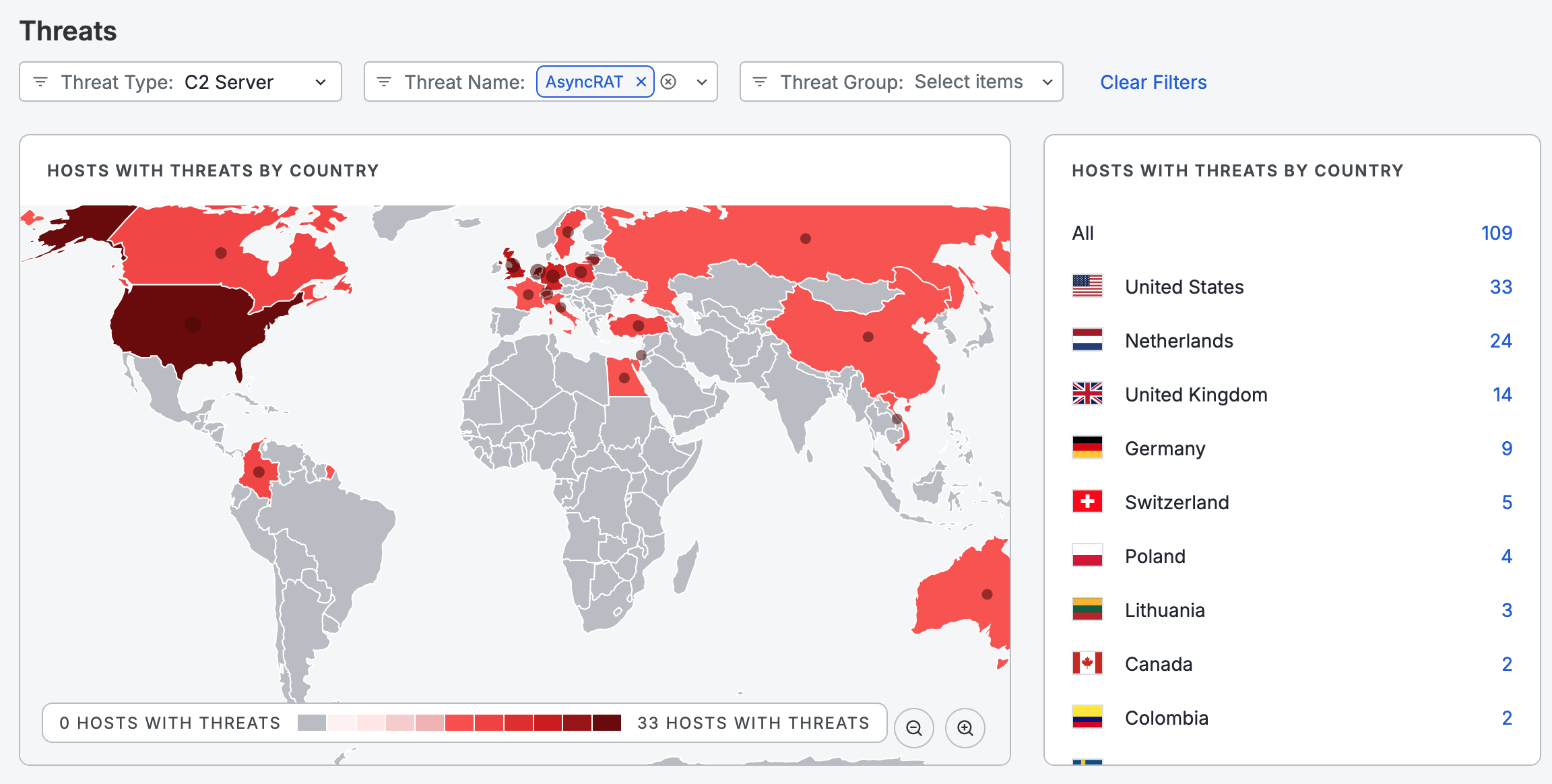
-
In the Hosts with threats by country section, click on a linked number to execute a query using the filters you have configured.
Threat Results
Scroll down on the page to the Threat Results section to view trendlines for threats, search for threats, and filter by Time Period or Count. To the right of threat type, you can view the trend based on the timeframe you selected.
NoteAsset counts for threats include host and web property assets. The Hosts with threats by country list next to the map only includes host counts.
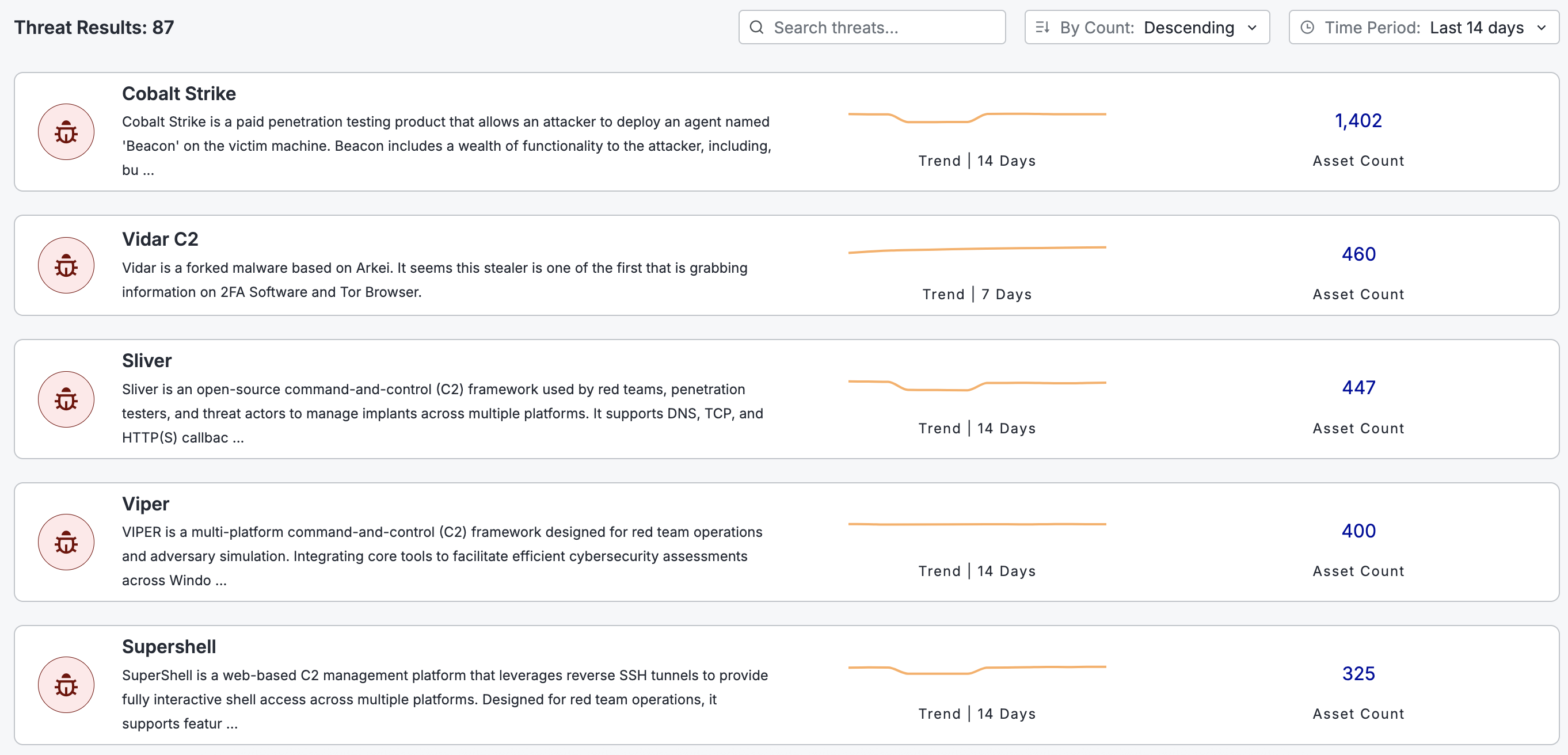
Click a threat entry to open its details page.
Threat details page
The threat details page provides a comprehensive view of a single threat. The top of the page shows a trendline of the count of hosts and web property assets associated with the threat.
Example screenshots of the threat are also provided on the threat details page. These include C2 web admin panels, phishing kits, malware download pages, and other relevant web content affiliated with the threat.
Click + Add to My Collections to create a collection to monitor and set up alerts for the threat. Click View All Threat Assets to run a query and see all assets associated with the threat.
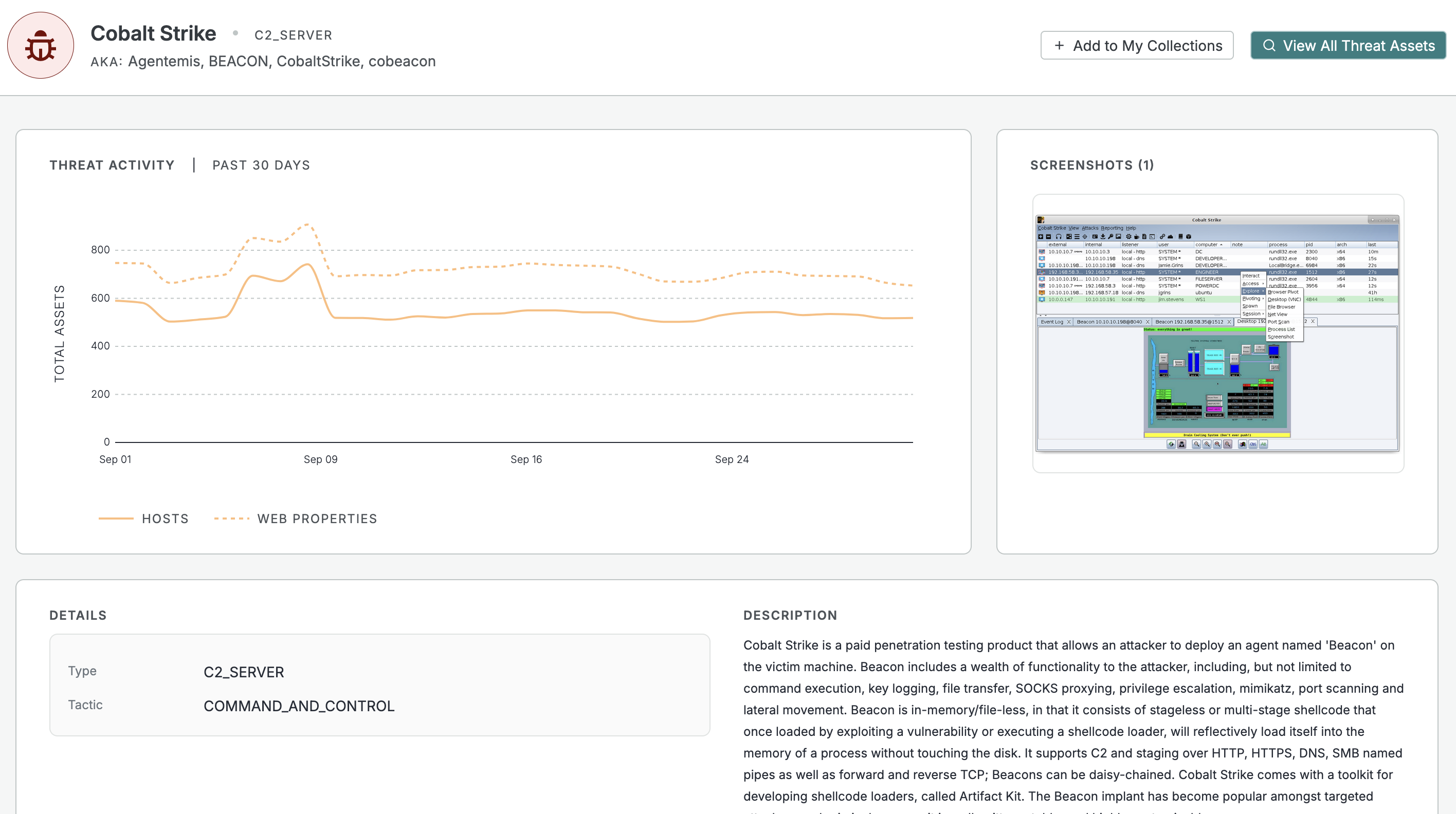
The threat details page for Cobalt Strike.
Beneath the asset plot, additional details about the threat are provided, including its type, description, and a list of actors associated with the threat, if present.
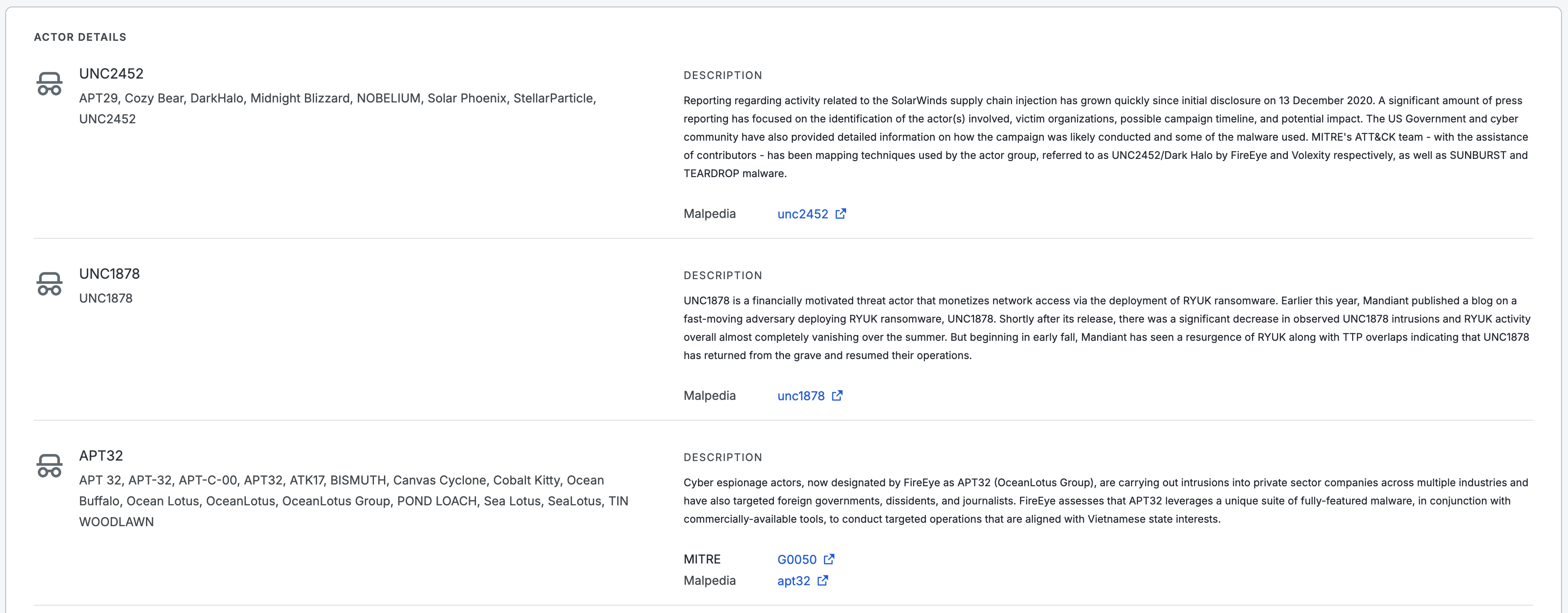
A list of actors associated with Cobalt Strike, provided below the details section of the threat details page.
Updated about 1 month ago
