ASM Overview Dashboard
The Overview dashboard in the Attack Surface Management (ASM) web console includes multiple views of your attack surface and alerts you about security issues that can compromise your organization.
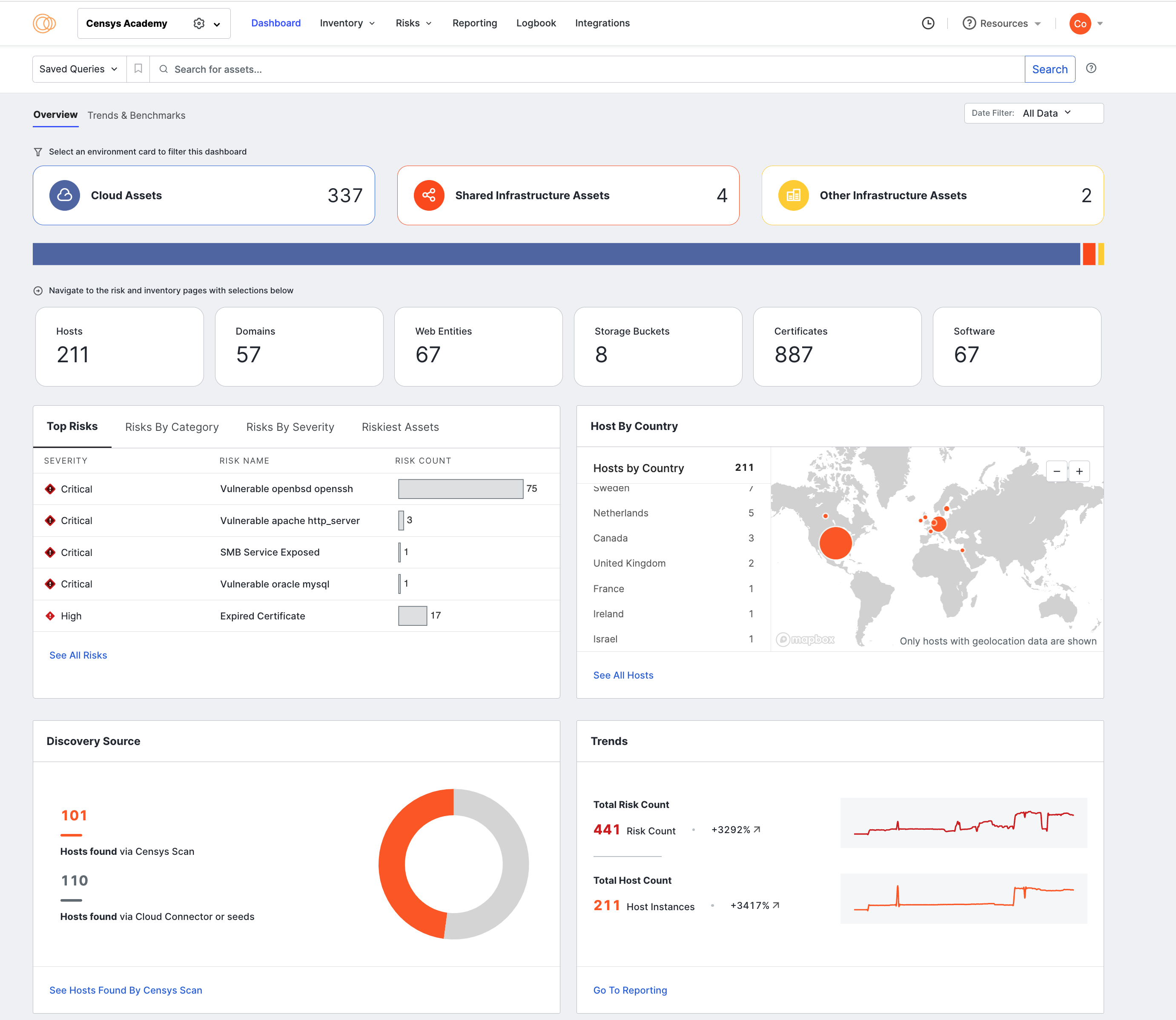
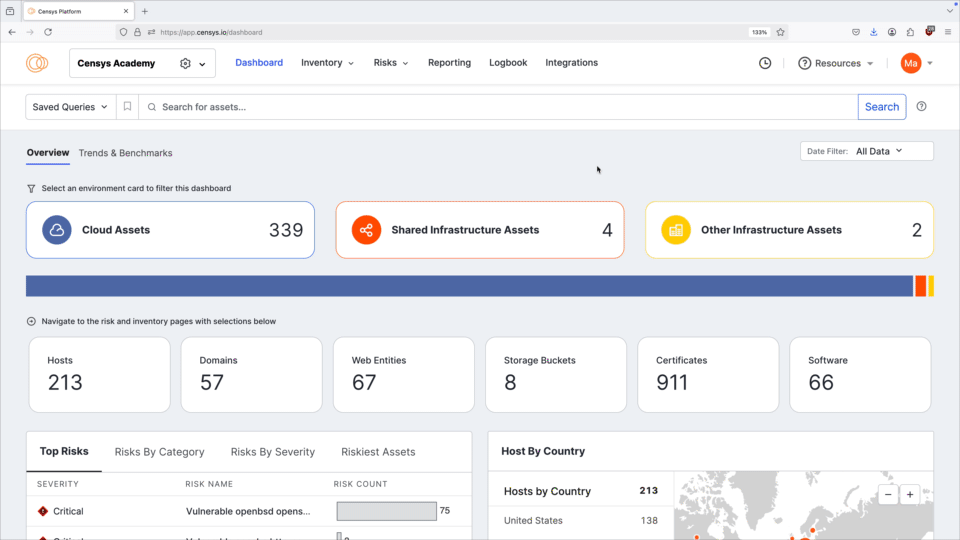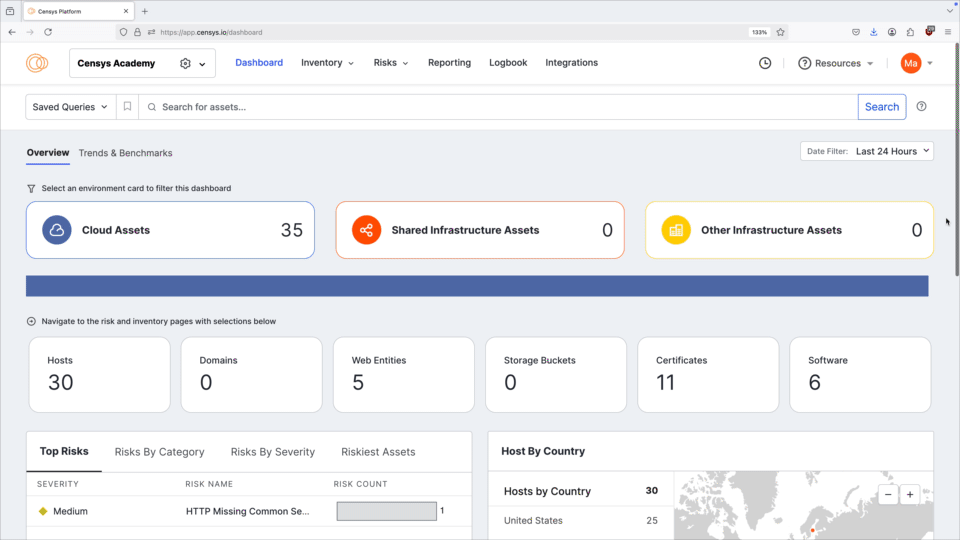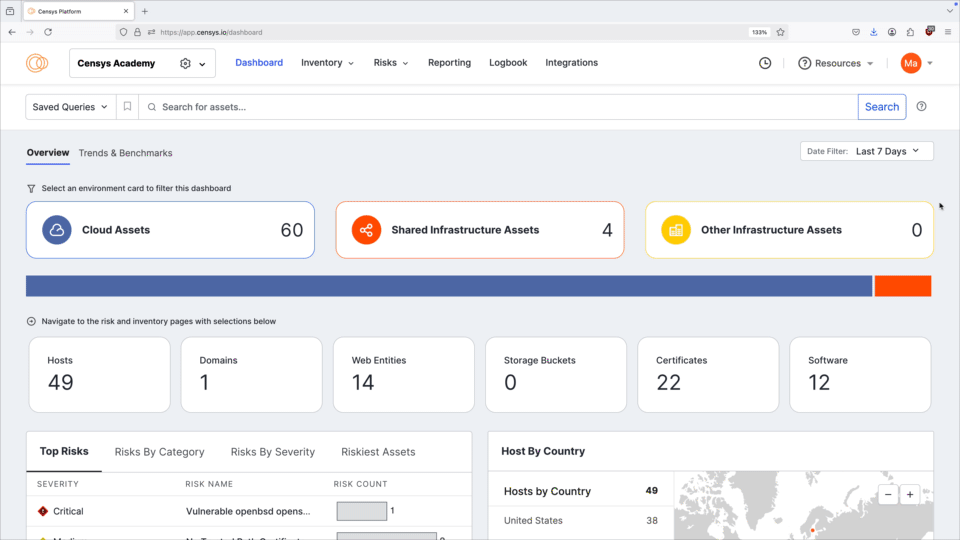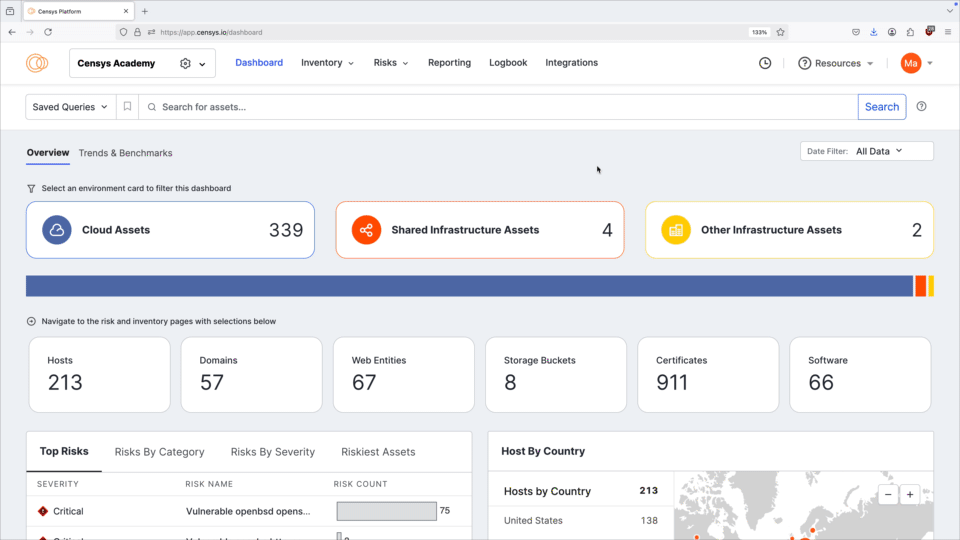
The dashboard's default view is unfiltered, displaying all the assets for which ASM has collected information.
Date filter
Use the date filter dropdown menu to filter the entire dashboard to display all inventory assets or assets discovered in the last 24 hours, 7 days, or 30 days.
Environment filter
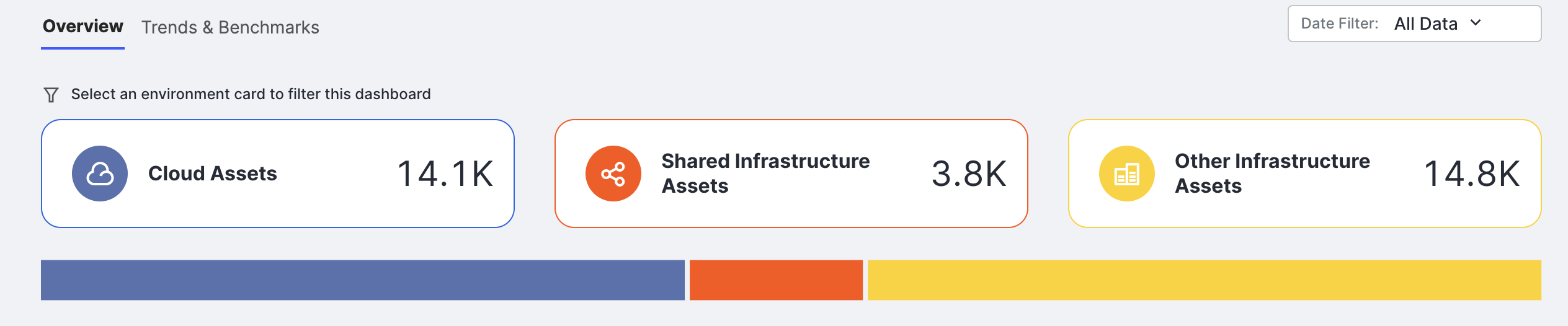
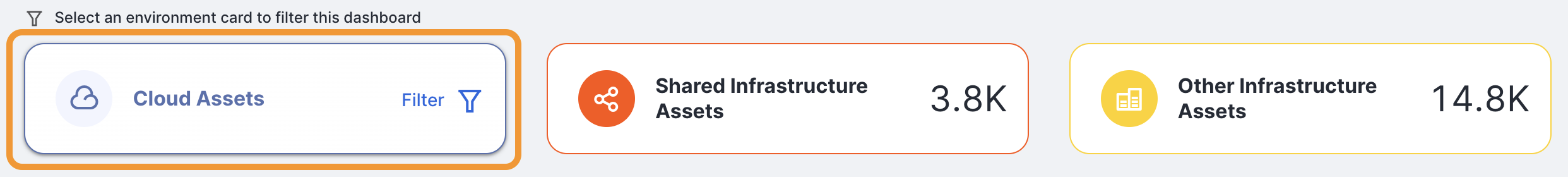
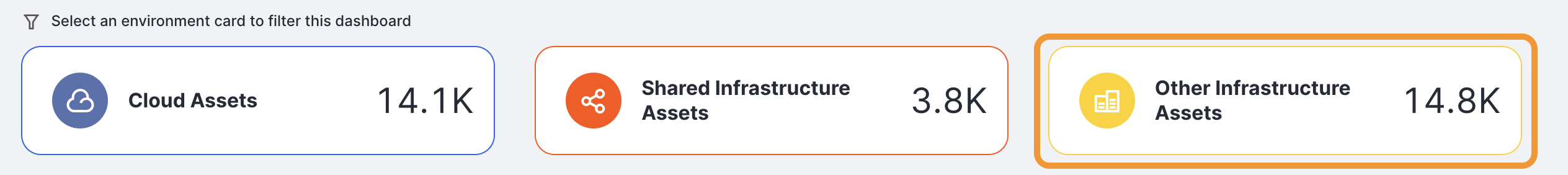
In the unfiltered view, the bar chart shows assets by environment. This view lets you quickly determine whether the bulk of your Internet presence is located in the cloud, on shared infrastructure, or elsewhere. Select one of these three environments to filter the entire Overview dashboard.
Cloud
Attack surface management in the cloud is a high priority due to the proliferation of accounts, the accessibility of free-tier services, and the ease with which settings can be misconfigured. This filter shows applicable Overview dashboard panels populated with cloud data.
Censys ASM includes the following cloud service providers (CSPs) in its definition of cloud. If a host, domain, subdomain, or storage bucket is found within these CSPs, it is considered a cloud asset.
CSP assets included in ASM Cloud category
- Amazon AWS
- Alibaba Cloud
- Digital Ocean Inc
- Oracle Cloud
- Switch Communications Group LLC
- American Internet Services
- Confluence Networks Inc
- Google Cloud
- Soft Layer Technologies Inc
- Hetzner Online
- Huawei Cloud Service
- Internap Corporation
- Arvixe
- Microsoft Azure
- Tencent Cloud
- Verizon Communications Inc
- US Signal
- Tier Point LLC
- Cologix Inc
Shared
The shared environment is a list of shared web hosts and content delivery network (CDN) hosts.

Other
The remainder of your organization’s hosts, domains, and subdomains are categorized as Other Infrastructure Assets.
Asset counts
This section sums up your organization’s total asset counts by type. Each card shows a total count of assets.
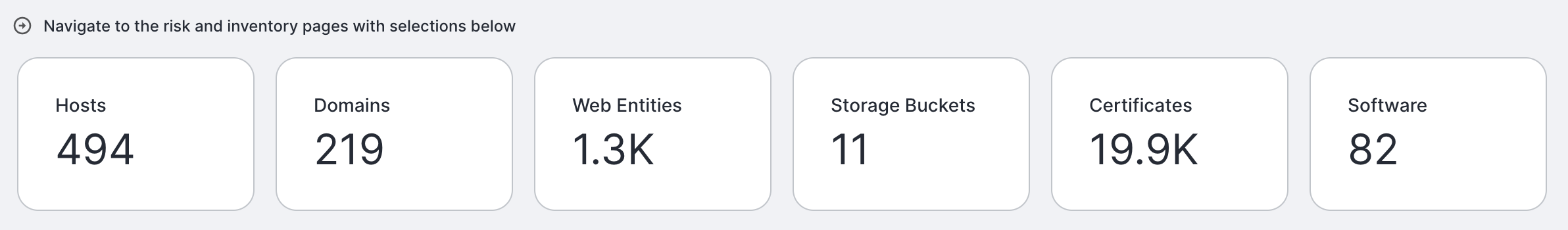
- IPs: A computer or service connected to the Internet that’s located at and identified by an IP address.
- Domains: Names that serve as domains in the Domain Name System (DNS), with a format commonly known as an eTLD+1 (for example, censys.io).
- Subdomains: Subdomains are names that resolve to hosts that are part of your attack surface.
- Storage Buckets: Containers provided by a cloud object storage service that are related by name or keyword to your organization.
- Certificates: X.509 certificates related to your organization, found by querying public Certificate Transparency logs and when scanning the Internet.
- Software: Software packages and versions detected during hosts scans.
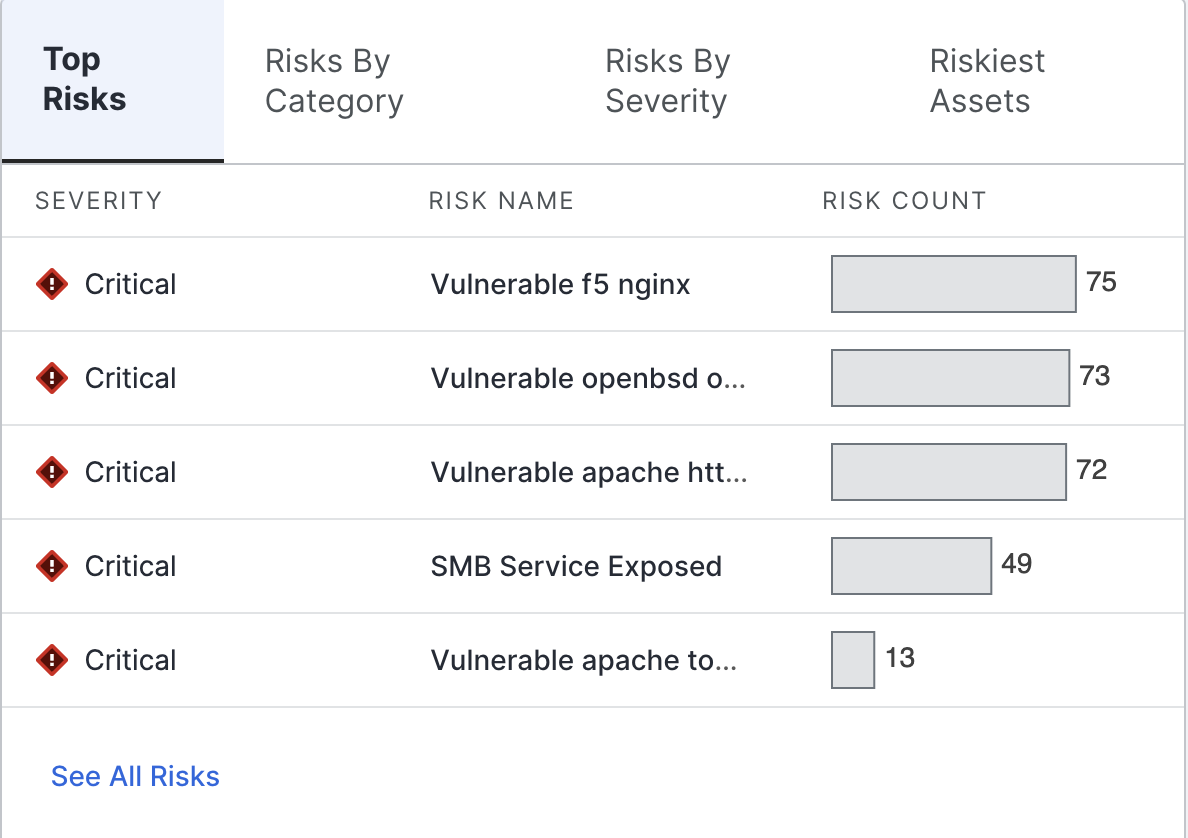
Top Risks
This visualization shows a list of top risks affecting your organization.
This area previews the most serious risks affecting your organization’s assets, filtered by severity and number of affected assets. The list changes based on the environment selected at the top of the dashboard.
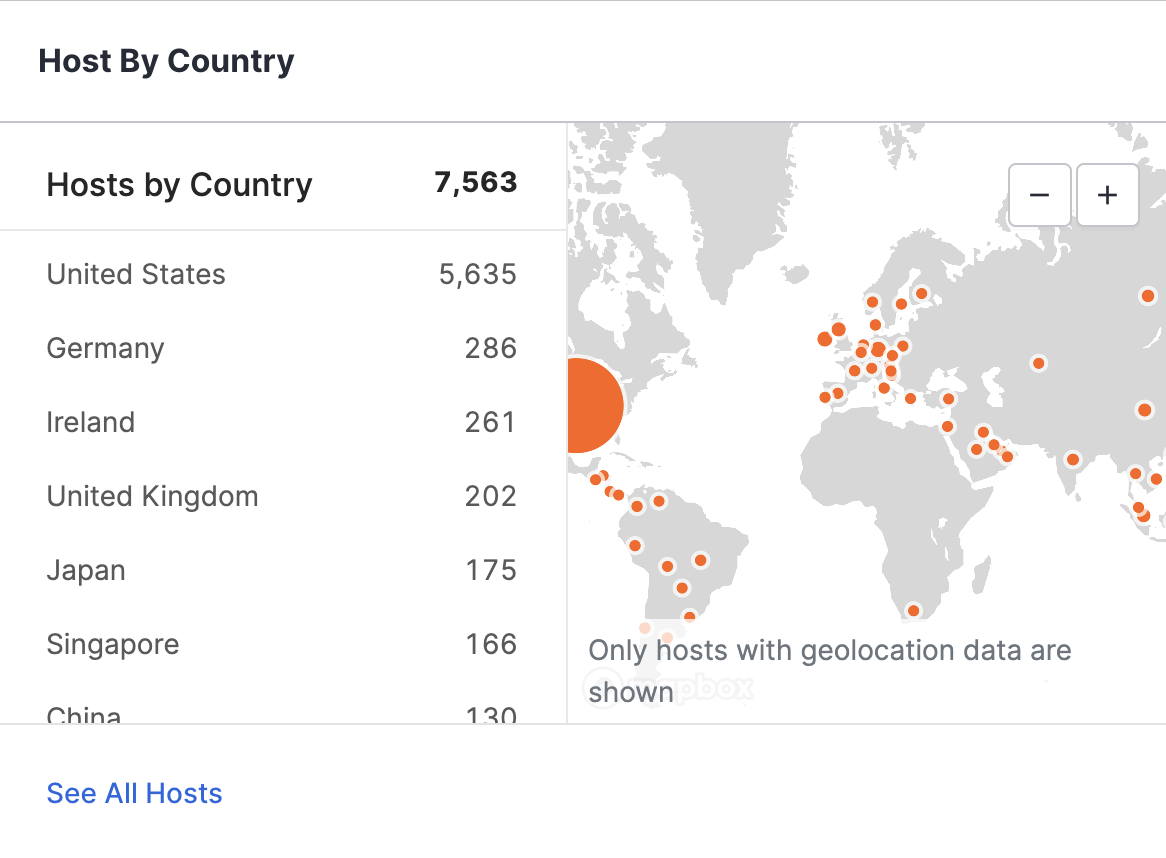
Hosts by Country
The hosts map shows a count of hosts located within a country for all of your organization’s hosts whose location is known.
Hosts that appeared within the time frame selected in the date filter are flagged as new, and their locations appear on the map in orange.
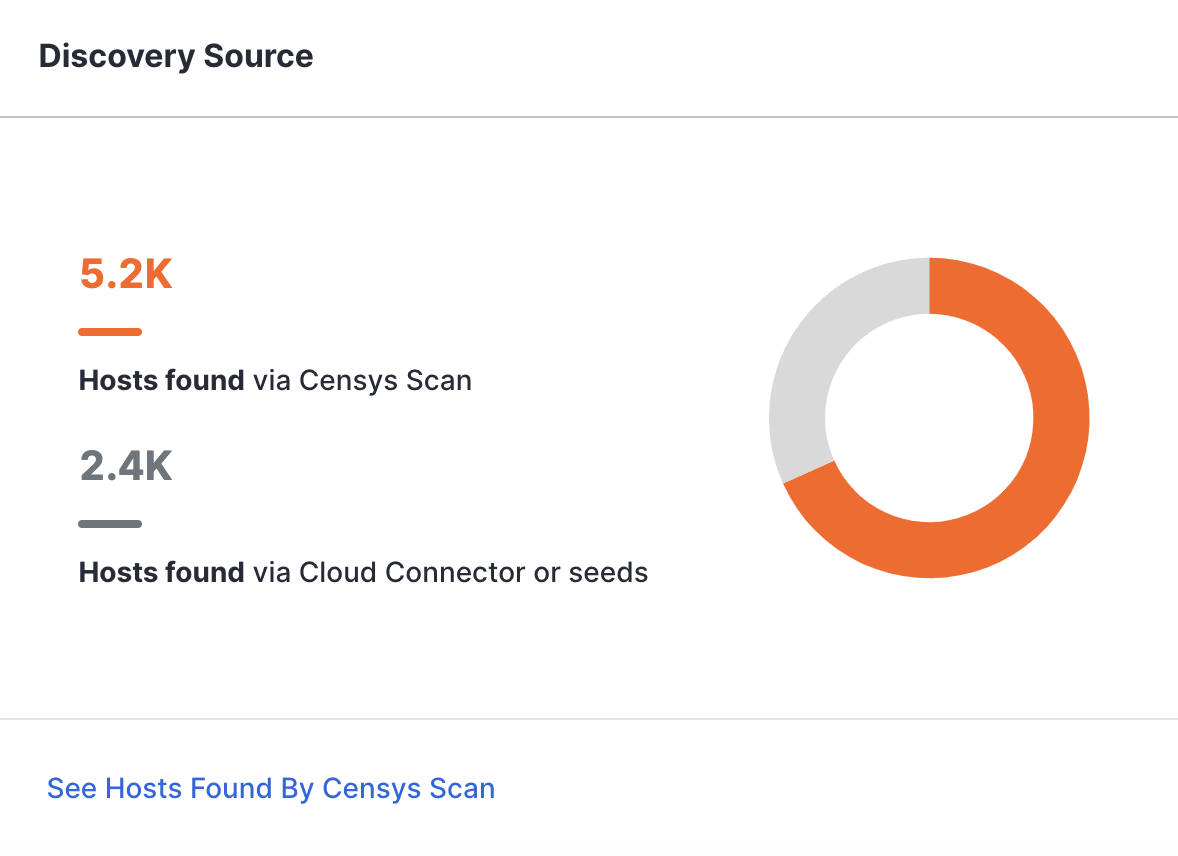
Discovery Source
This section shows hosts by their discovery source and metric trends regarding asset and risk counts.
Censys Attack Surface Management uses discovery sources to classify hosts in your attack surface as known or unknown. Knowing whether a host was found from a provided asset, such as a CIDR block or a cloud connector, allows you to engage with risks and administrative tasks from an ownership perspective.
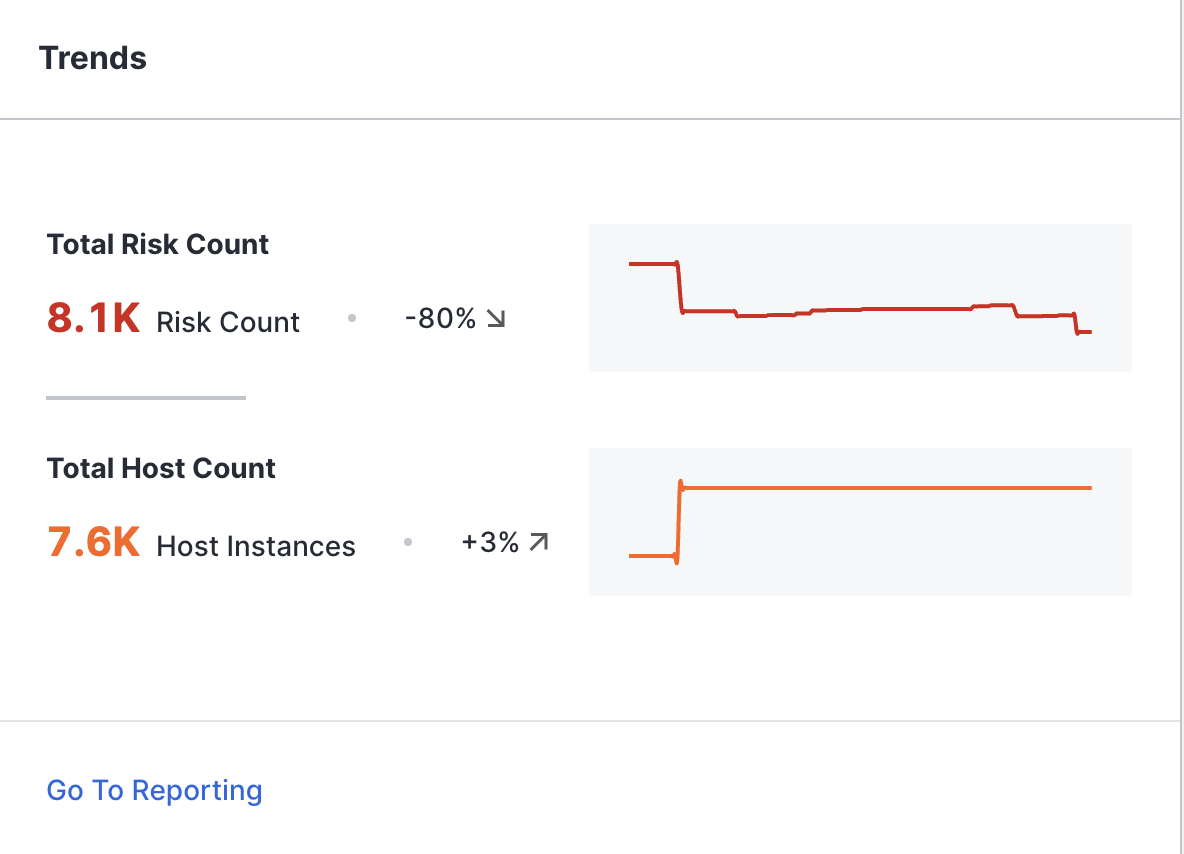
Trends
This panel shows trends taken from the ASM reporting feature, including your organization’s total cost and risk counts over time.
Where to go from here
Read articles about the information included about your organization’s hosts, domains, certificates, and risks to learn how to leverage the rich data of the Attack Surface Management platform and enhance your Internet security.
Updated about 1 month ago
