Inventory Assets
In Censys Attack Surface Management (ASM), your attack surface Inventory consists of hosts, web entities, certificates, domains, and storage buckets. Additionally, information about software present in your inventory is aggregated and presented in your Inventory.
Information about your assets is obtained from Censys scans. The resulting data from these scans is organized into data objects and fields using the ASM data schema.
This article walks through the Inventory page and provides an overview of the types of inventory assets and some example data fields available for each of them. Detailed information about each asset type can be found in the asset-specific pages in this section of the documentation.
Inventory page
In the ASM web console, the Inventory page shows the assets in your attack surface.
You can explore, browse, and investigate these assets with basic and advanced searching, clickable shortcuts, and aggregations.
Go to the ASM web console, and click Inventory > All Inventory.
When you first open this page, all asset types are listed by their ID, which is dependent on their type.
You can reorder the columns by clicking the dots in the column heading and then selecting Move column left or Move column right. You can also grab the right edge of a column name and resize it.
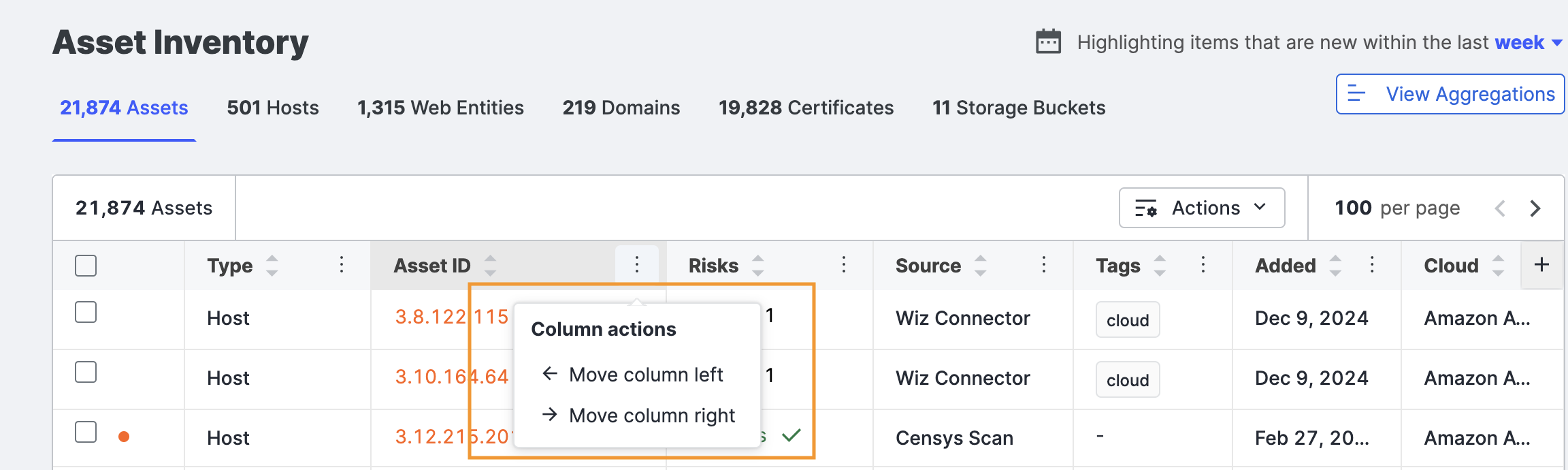
Columns in the view include:
- Type: The classification of an asset, which determines its unique identifier (ID) in the inventory. Different asset types may include domains, IP addresses, certificates, or cloud resources.
- Risks: A count of any risks detected on an asset, listed by their severity.
- Source: An enumeration indicating how an asset was added to your attack surface: as a seed, from a cloud connector, or via Censys discovery scans. Sources include:
- Seed you Provided: Your organization manually provided the seed.
- Censys Found Seed: Censys found the seed during Censys Seed Discovery.
- Censys Scan: Asset was found from Censys Attribution.
- AWS Connector: Asset was added through the AWS Connector.
- GCP Connector: Asset was added through the GCP Connector.
- Azure Connector: Asset was added through the Azure Connector.
- Tags: Any tags your team applied to an asset.
- Added: The date an asset was associated to your organization.
- Cloud: The name of the hosting provider or the name of the cloud or data center in which the IP address is hosted.
- Expiration Date: The date on which a certificate or domain expires/expired.
- Account ID: A unique identifier associated with a cloud account (such as AWS, GCP, or Azure) that owns or manages the asset. This helps track assets across different cloud environments.
Column selection
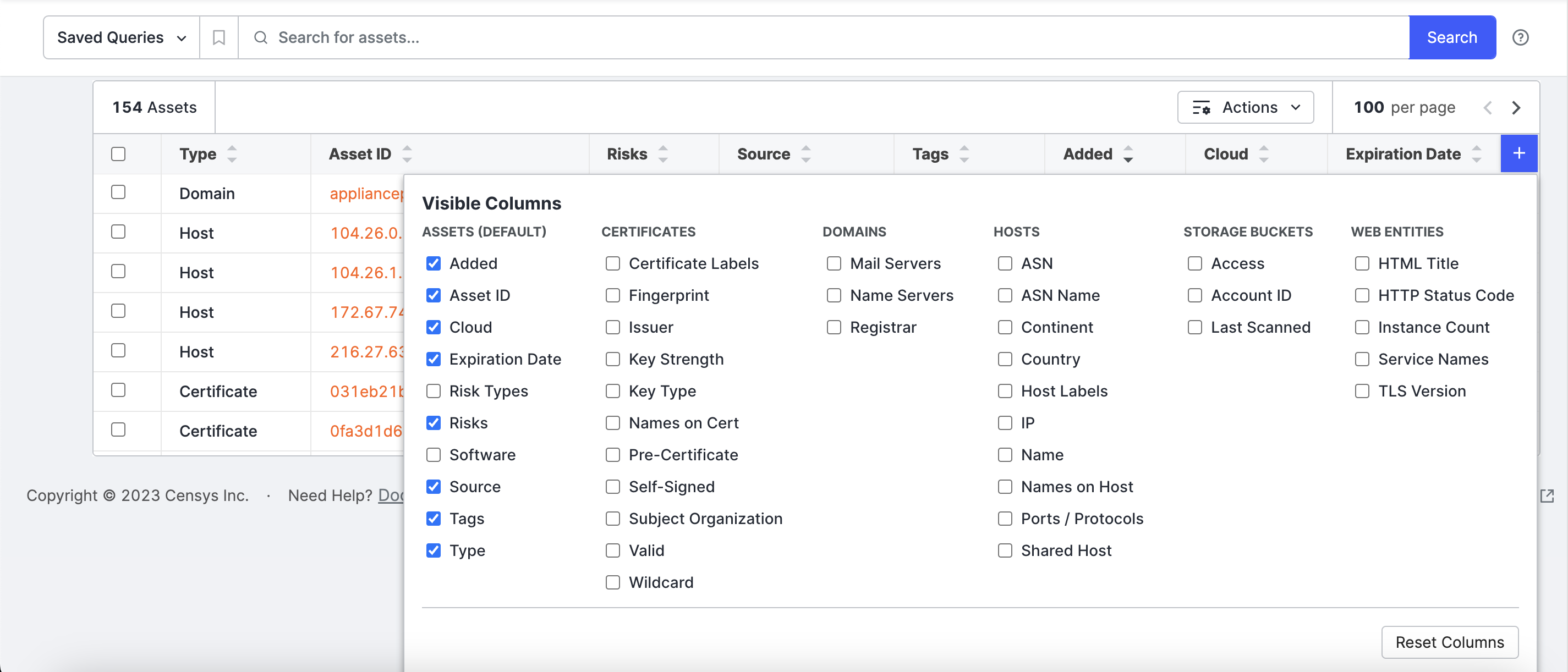
Additional columns depend on asset type. Select the columns you want to see by clicking the plus (+) at the right of the header row.
Aggregations
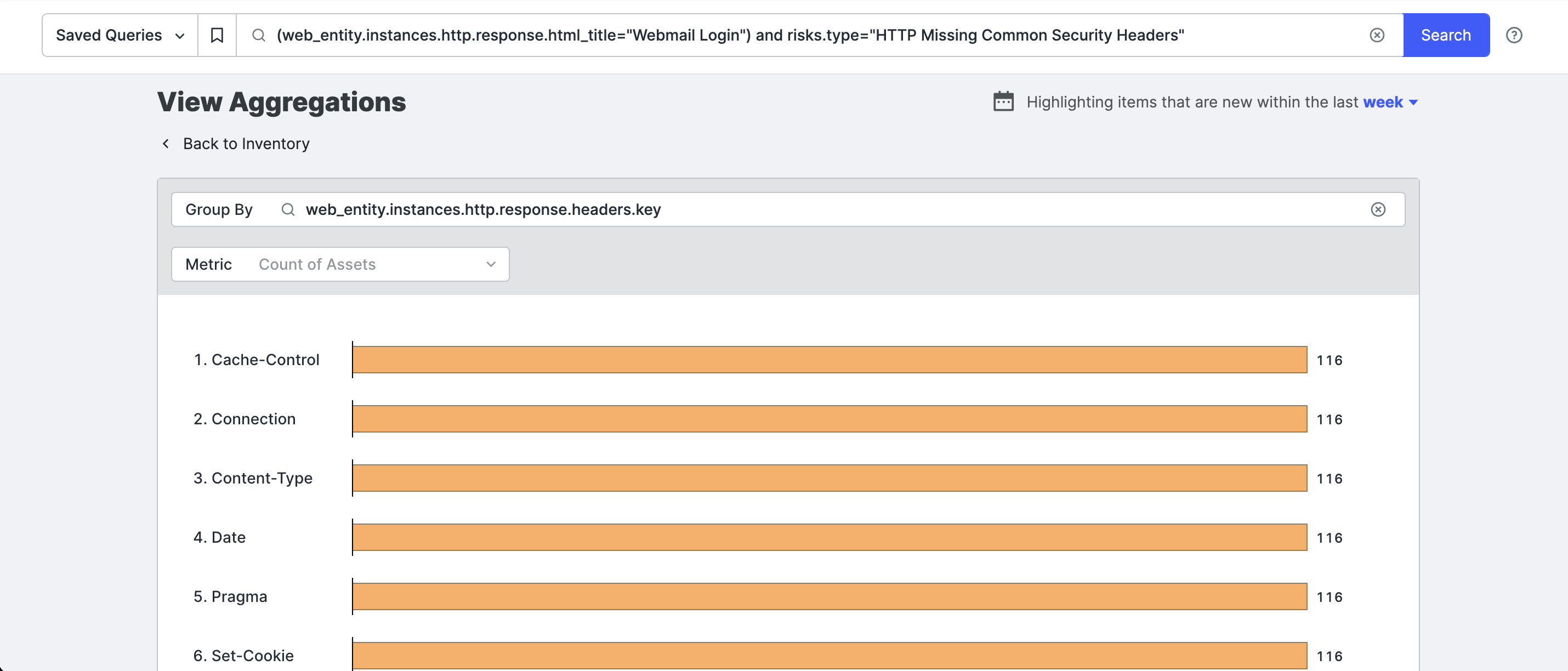
To view top values for less common fields than are shown in the Search shortcuts panel, click View Aggregations.

Use autocomplete to select the field you want to see top values for.
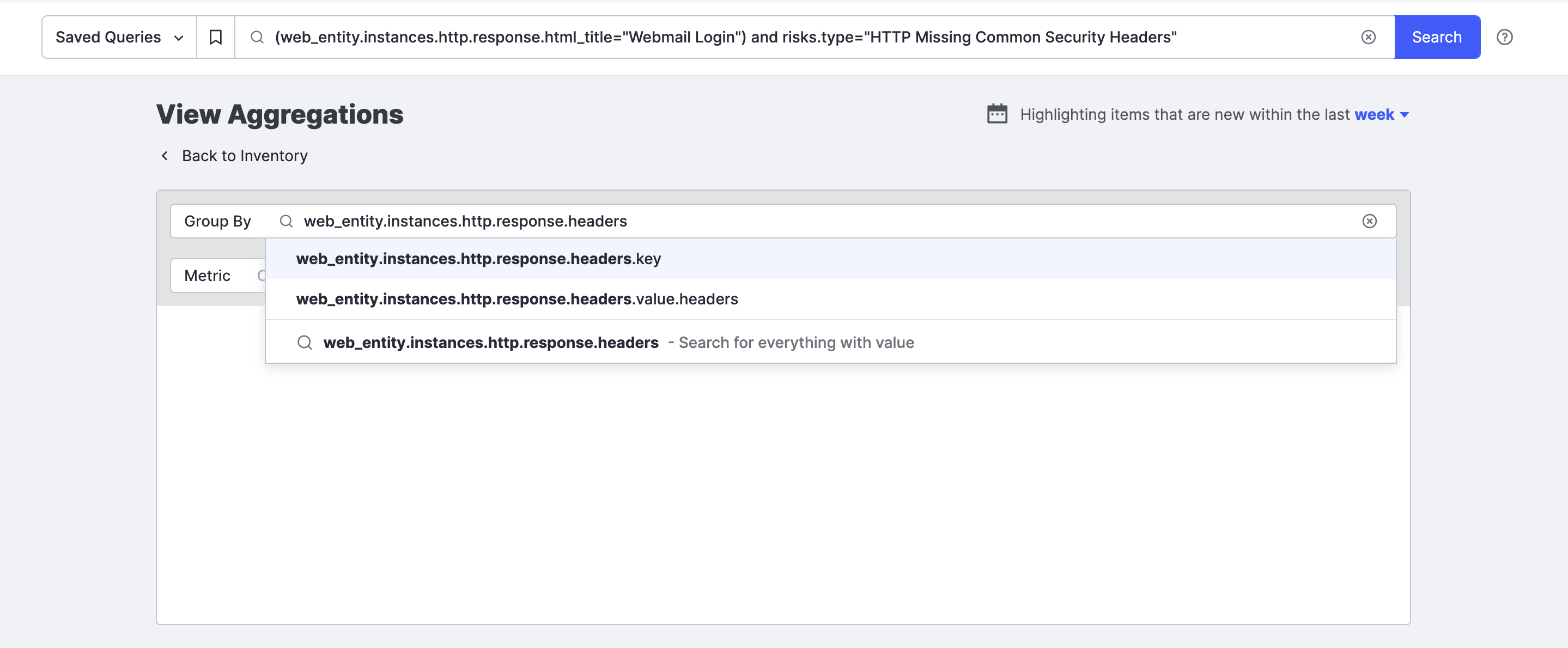
A term aggregation can be applied to any field in the schema and is performed on the assets returned by the query in the search bar. If no query is entered in the search bar when you click View Aggregations, the aggregation will apply to all relevant assets.
Export data
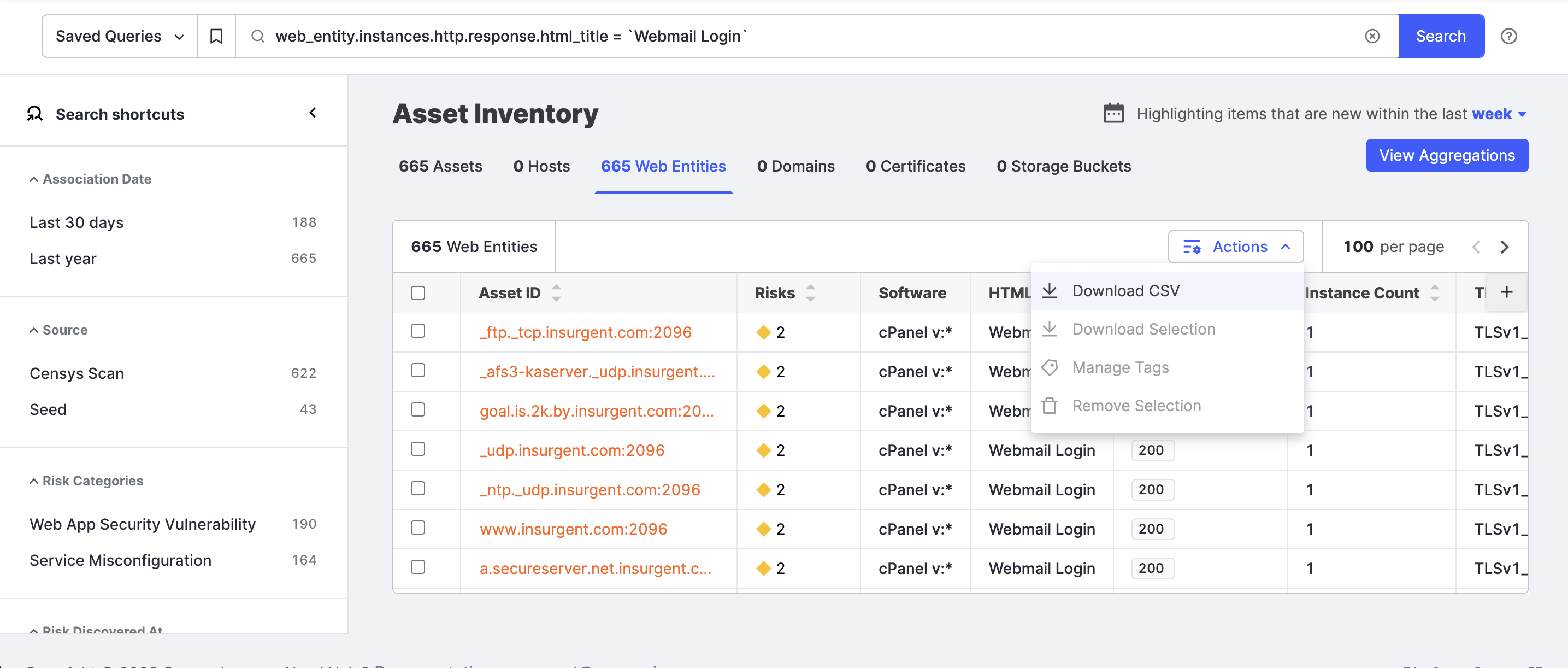
You can download an asset list as a comma-separated value (CSV) for use in other products and workflows.
Click Actions > Download CSV.
The filename is {timestamp}_{customerName}_InventoryExport.csv. The columns in the CSV file are the columns shown in the table when you export the file.
Asset details page
Click a linked asset in the table to see that asset's details page with additional information.
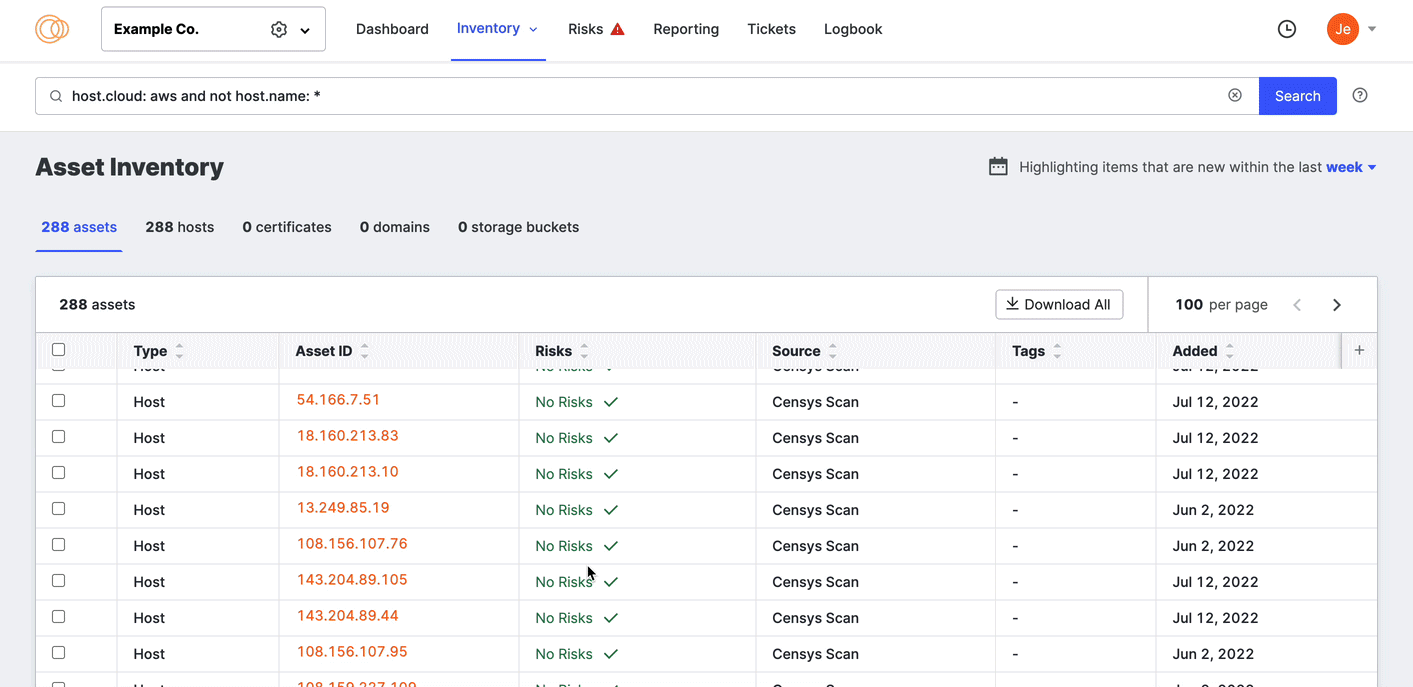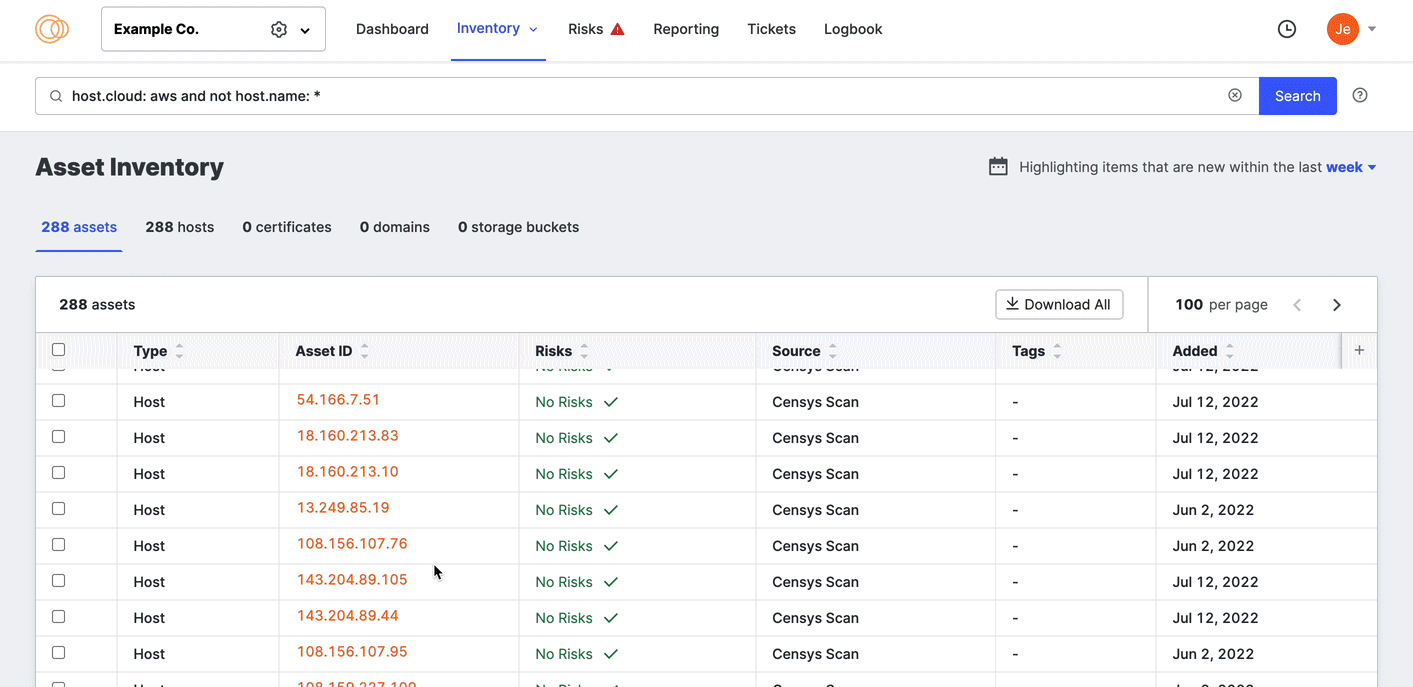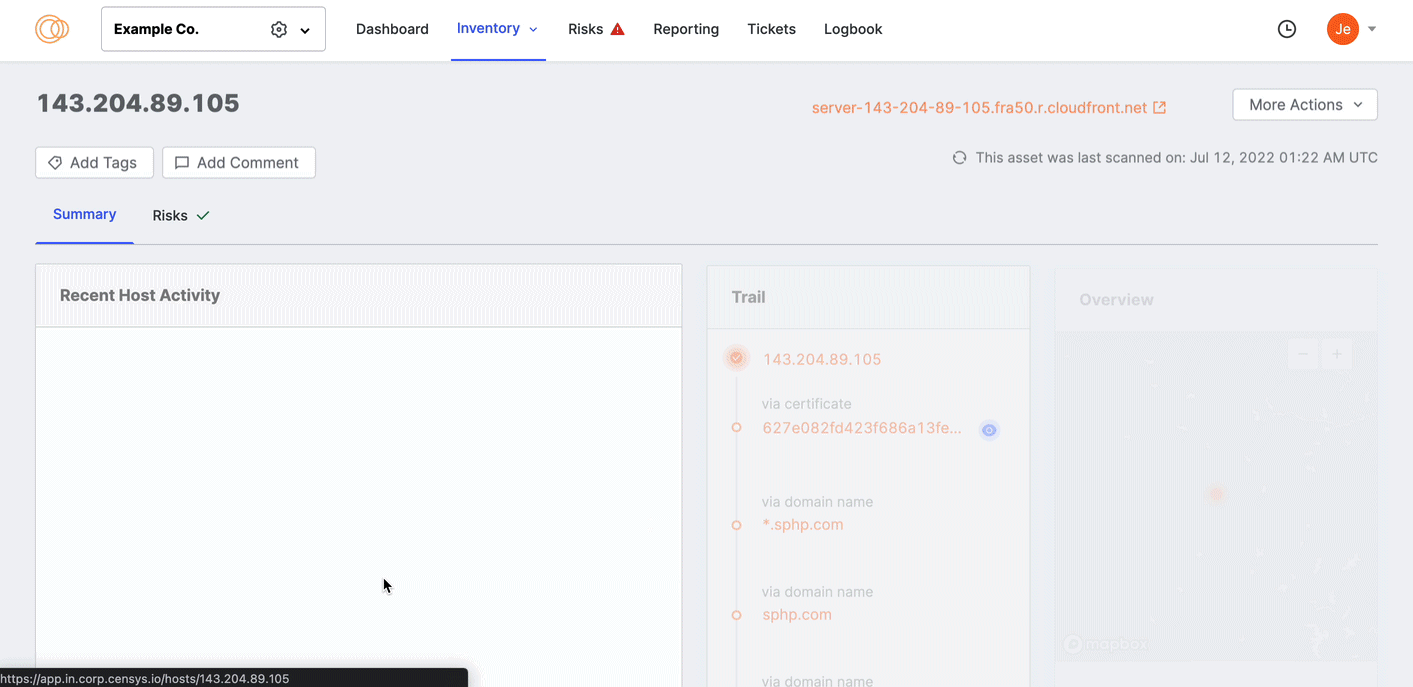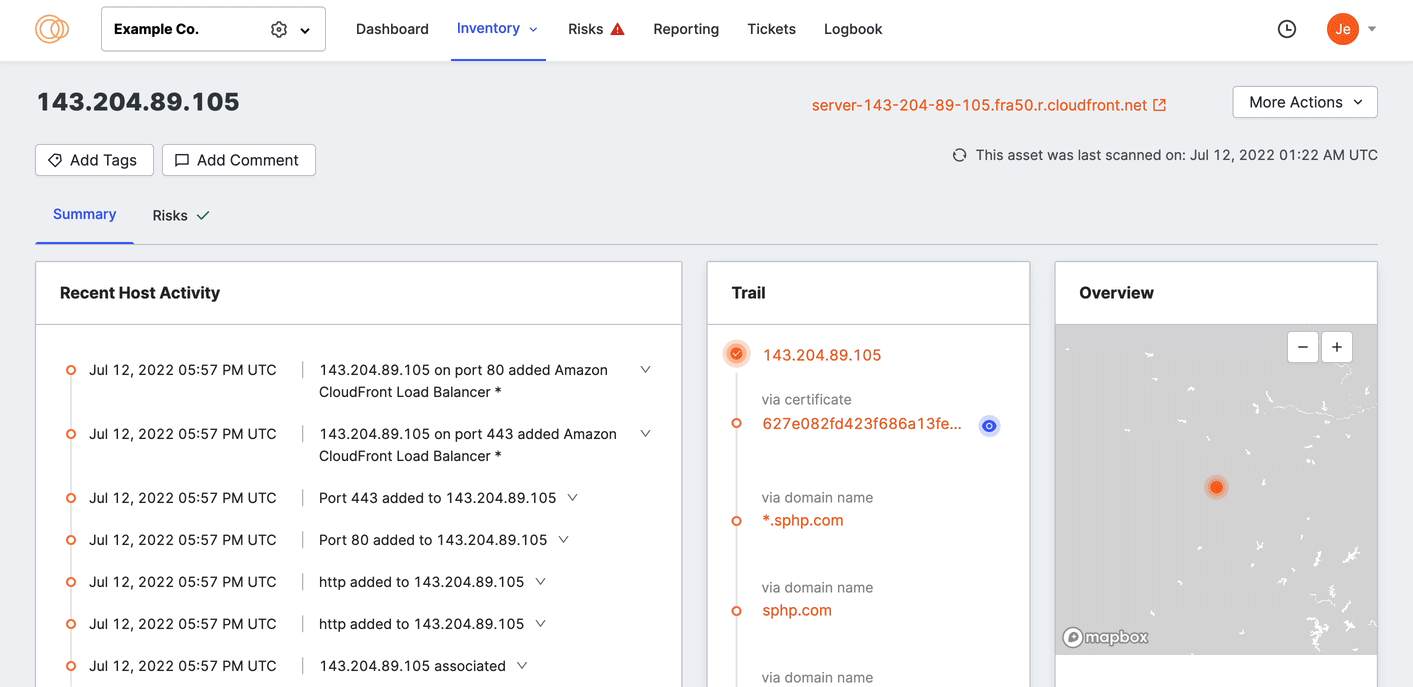
Asset types
Hosts
Hosts are computers, virtual machines, or devices with an IP address connected to the Internet. Host fields include those that apply to the whole host (such as geolocation or Internet routing) and those that apply to services observed on open ports.
Example host fields are provided in the table below.
| Field | Description |
|---|---|
host.autonomous_system.asn | The numerical identifier of the autonomous system that a host’s IP address is part of. |
host.autonomous_system.name | The human readable name of the autonomous system that a host’s IP address is part of. |
host.location.country | The country where the IP address is located. |
host.dns.names | Names from the Domain Name System that resolve to the host. |
host.services.port | The numerical identifiers of the open ports on the host, annotated with the application-layer protocols that the host services are using. |
Certificates
Certificates are electronic documents used to prove the ownership of a public key, often used during a TLS handshake. Certificate fields include the parsed contents, and trust information from root stores, certificate transparency logs, ZLint, and Censys collection metadata.
Example certificate fields are provided in the table below.
| Field | Description |
|---|---|
certificate.fingerprint_sha256 | The identifier of the certificate: a SHA-256 digest of its contents. |
certificate.parsed.issuer.organization | The certificate authority that issued the certificate. |
certificate.parsed.signature.self_signed | Whether or not the certificate is self-signed. |
certificate.parsed.subject.organization | The name of the organization to which the certificate was issued, if available. |
Domains
Any name registered in the Domain Name System with the format eTLD+1 (e.g., censys.io). Domain fields include DNS data such as name servers, mail servers, and registration information.
Example domain fields are provided in the table below.
| Field | Description |
|---|---|
domain.registrar | The registrar or reseller with which the domain name was registered. |
domain.name_servers | The names of the servers responsible for answering DNS lookups, as obtained from the DNS record for the domain name. Usually, there are two or more for redundancy. |
domain.mail_exchange_servers | The names of any servers that receive mail for mailboxes in the domain, if applicable, as obtained from MX records for the domain name. |
Storage buckets
A cloud object storage system, supporting files or other objects, which includes solutions like Amazon S3, Google Cloud Storage, and Azure Blob Storage. Storage bucket fields include account information (if available from a Censys Cloud Connector) and externally observed access settings.
Example storage bucket fields are provided in the table below.
Field | Description |
|---|---|
| The account ID associated with this bucket. |
| The cloud storage provider hosting this bucket. |
| The access configuration for this bucket. Access levels include Readable, Writeable, and Editable Settings. These fields contain boolean values. |
Web entities
Web entities are name-based HTTP services that represent products, services, and content reached through the world wide web using a name and a port number. Web entities are represented as a collection of instances, the identifier of which includes the IP address of the host serving the web entity.
Example web entity fields are provided in the table below.
| Field | Description |
|---|---|
web_entity.instances.http.response.html_title | The title(s) of any web page(s) returned by a web entity’s instances during a scan. |
web_entity.instances.http.response.status_code | The status code(s) returned by a web entity’s instances during a scan. |
web_entity.instance_count | The total number of instances of the web entity observed during all Censys scans. Only the first 100 instances are searchable. |
web_entity.instances.tls.versions | The TLS version(s) selected by a web entity’s instances during a scan. |
web_entity.instances.labels | Descriptive tags assigned to a web entity based on its characteristics, behaviors, or technologies detected during scan. |
Software
In ASM, you can search for software that needs to be updated or contains a vulnerability in your organization’s Internet-accessible hosts.
Three sources for software information are pulled from scan results:
- A fingerprint (for example, a Censys mapping to CPE-formatted software names)
- The HTTP x-powered-by field in an HTTP header
- The HTTP server header field in an HTTP field. This information is provided in a source field in our APIs and in the Source column on the Software list page.
Censys ASM matches more than 1,433 software fingerprints to software. As additional fingerprints are created, the latter two methods will eventually be deprecated. Read more about software in ASM here.
Updated 11 months ago
