ASM MCP Server
Use the ASM Model Context Protocol (MCP) Server to give your AI agents and workflows secure, governed, and direct access to your ASM inventory, empowering you to explore and understand your attack surface at machine speed.
MCP is an open standard designed by Anthropic to help AI agents leverage trusted external data and tools.
The MCP Server is a service hosted by Censys that you can integrate with tools like Copilot Studio, Cursor, Claude Code, and Continue.dev. The server can be used by any ASM user with access to the API.
Prerequisites
- Obtain your API key. It is located at the top of the Integrations page in the ASM web console.
- Obtain your workspace ID.
-
To retrieve your workspace ID, log in to the ASM web console, then click the gear icon next to your workspace at the top of the page.
-
Your workspace ID will be provided in the URL after
https://app.censys.io/workspace/edit/
-
Integrate with the Censys hosted ASM MCP Server
Use the instructions below to integrate the Censys hosted ASM MCP Server with your tools. The following instructions are just some examples; the ASM MCP Server can be incorporated into many different applications.
Note that including the workspace ID in your configuration is optional. However, if you do not include your workspace ID, you will be prompted to provide it when you query the ASM MCP Server.
Note that because the Copilot configuration does not include your workspace ID, you may need to provide it in your prompts. For example, "How many SSH services are exposed in workspace [workspace ID]?"
- Log in to Copilot Studio.
- In the left sidebar, select Agents.
- Create a new agent or select your existing agent.
- In the agent window, in the top navigation bar, click Tools.
- Click + Add a tool and then click + New tool in the window that appears.
- Select Model Context Protocol.
- Enter a name and description.
- In the Server URL field, enter
https://mcp.asm.censys.io/asm/mcp/. - In the Authentication section, select API Key.
- In the Type box, select Header and enter
Authorization. - Click Create.
- On the next page, next to Connection, click the drop down and select Create new connection.
- Leave the top drop down menu set to its default option. In the text field, enter your ASM API key prefixed with
Bearer(for example,Bearer 12345678-1234-5678-9101-112131415, then click Create. - Click Add to agent.
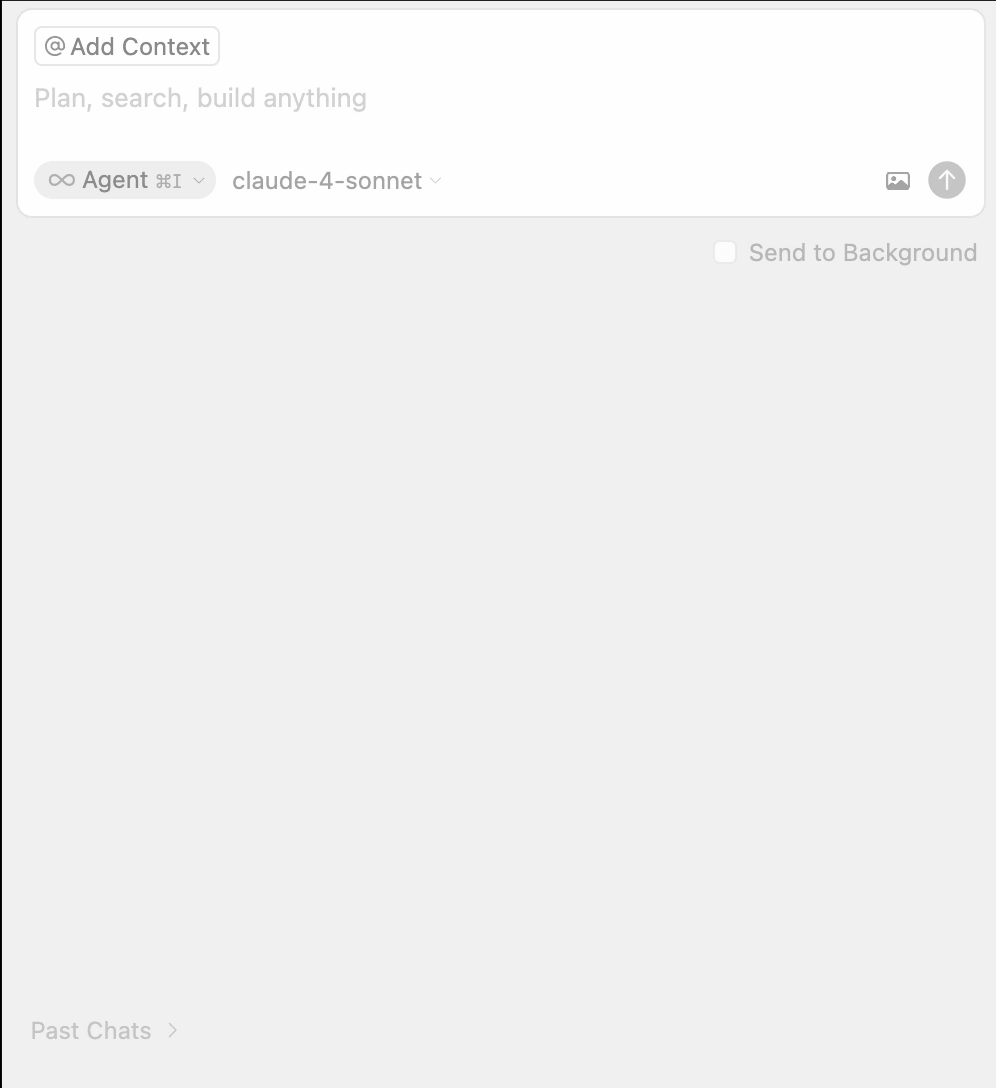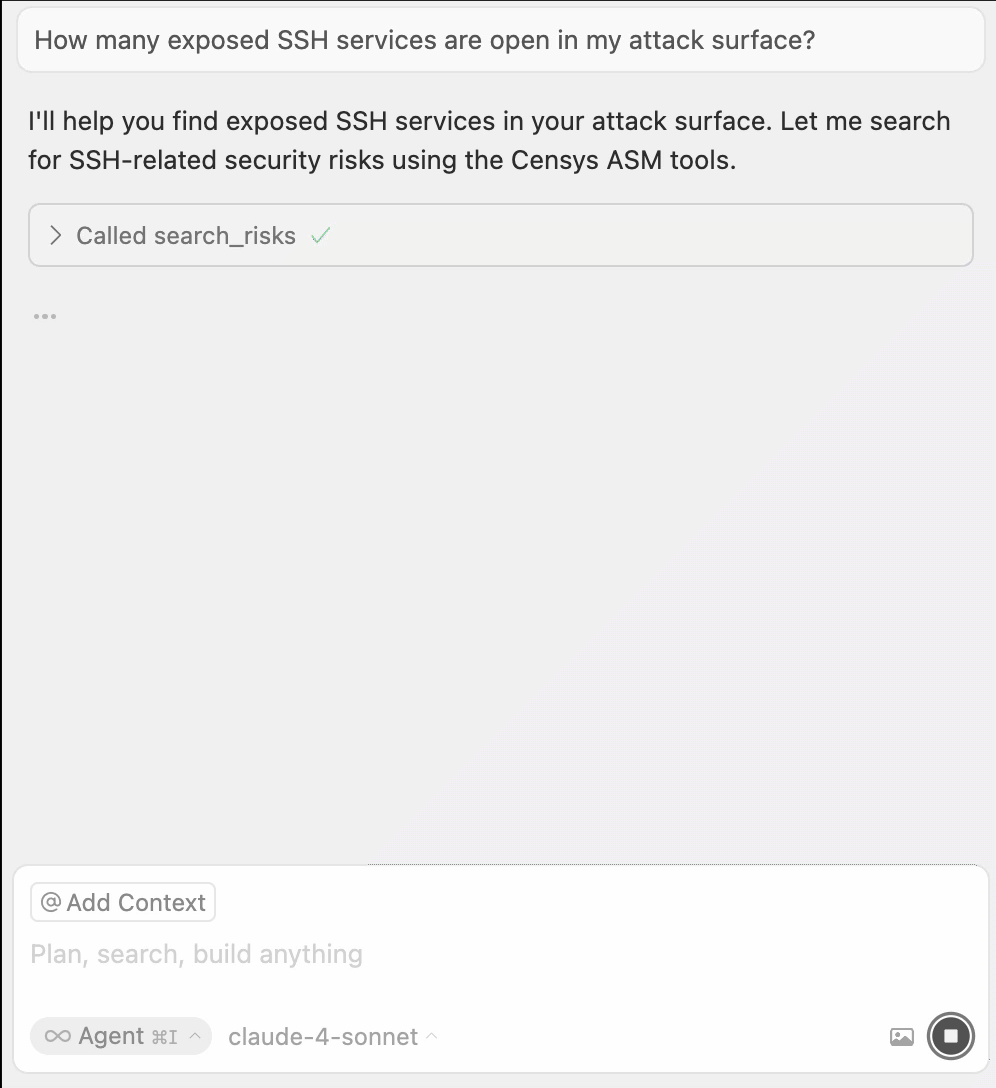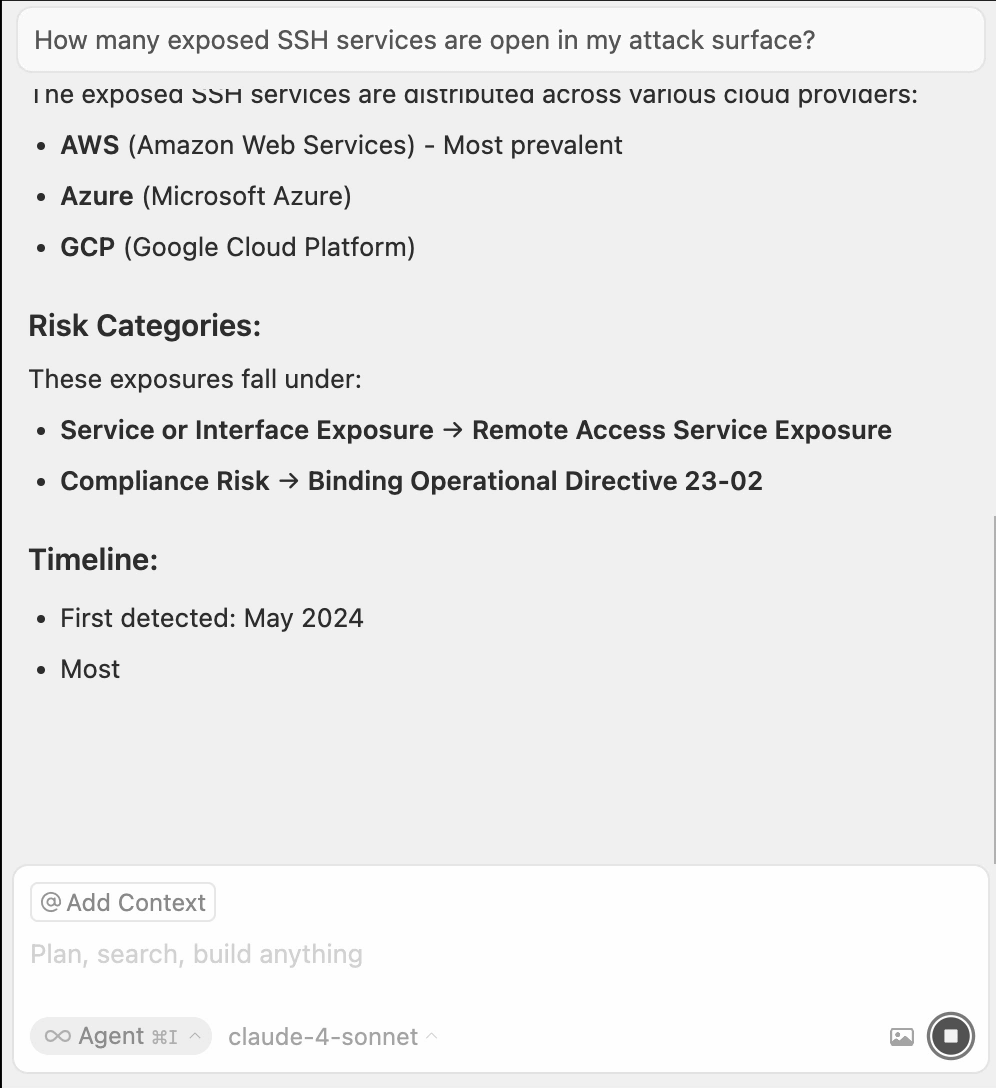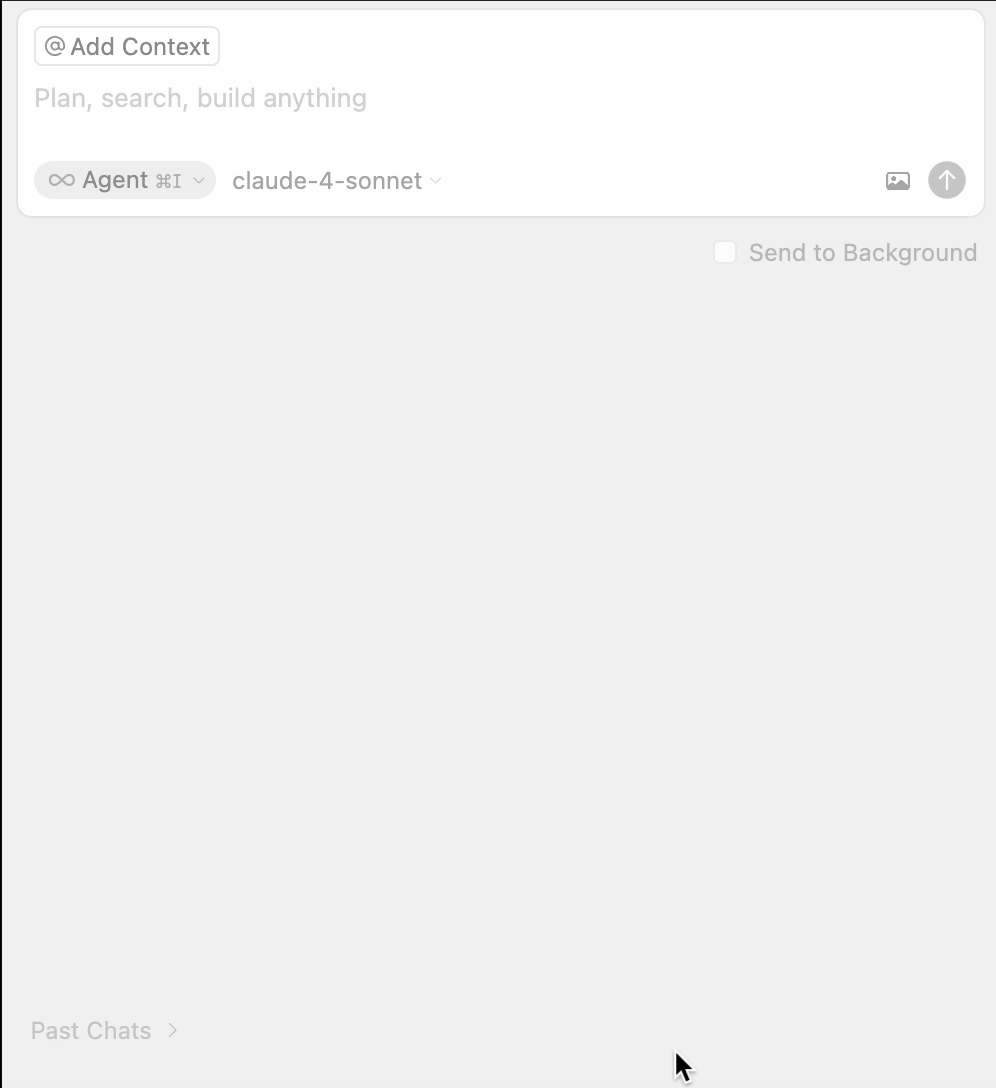
After configuring your integration, test it by prompting your agent with a question like "How many domains are in my attack surface?"
The output may depend on your specific configuration and your prompt, but your agent should use the search_assets tool to retrieve information about your attack surface.
Example use cases
The ASM MCP Server currently works best for retrieving and summarizing information about assets in your inventory, aggregating information about your inventory, and examining specific components of your attack surface to surface risks and other issues.
The following prompts are some useful examples.
- Are any assets in my inventory vulnerable to CVE-2025-54309?
- Which cloud vendors are present in my attack surface?
- Which of my assets has the highest number of critical vulnerabilities?
- Which critical risk is most prevalent in my attack surface?
ASM MCP tools
In addition to functionality that is equivalent to ASM APIs, the ASM MCP server features the following tools.
| Tool | Description |
|---|---|
search_risks | Searches for security risk instances using simple, intuitive filters. Find risks by status, severity, affected assets, or risk types for comprehensive security assessment. |
summarize_cloud_footprint | Provides comprehensive analytics about your organization's cloud infrastructure footprint and growth. Get executive-level overview of your cloud attack surface, track asset growth, and understand cloud provider distribution. |
risk_prioritization | Automatically discovers, analyzes, and prioritizes security risks with actionable remediation guidance. |
attack_surface_discovery | Complete discovery and visualization of an organization's internet-facing attack surface with relationship mapping. |
vulnerability_workflow | Proactive threat hunting that identifies emerging threats, suspicious patterns, and exploitable vulnerabilities across the attack surface. |
Updated 8 days ago
