Threat Hunting MCP Server
Use the Threat Hunting Model Context Protocol (MCP) Server to give your AI agents access to Censys Threat Hunting APIs, empowering you to find and investigate potential threats at machine speed.
MCP is an open standard designed by Anthropic to help AI agents leverage trusted external data and tools.
The Threat Hunting MCP Server is a service hosted by Censys that you can integrate with tools like Cursor, Claude Code, and Continue.dev. The server can be used by any Platform user with access to the API and the Threat Hunting module. API calls executed via integration with the server count against your credit balance.
Prerequisites
- Obtain or set up a Platform Personal Access Token (PAT).
- You must have the API Access role to create a PAT.
- Obtain your Platform organization ID.
- Your organization must have access to the Threat Hunting module.
Integrate with the Censys hosted MCP Server
Use the instructions below to integrate the Censys hosted Threat Hunting MCP Server with your tools. Note that the following are just some examples; the MCP Server can be incorporated into many different applications.
Add the following to your Cursor MCP configuration file (~/.cursor/mcp.json). You can access this file in the UI by going to Cursor Settings > Tools & Integrations and clicking + New MCP Server.
{
"mcpServers": {
"censys-threat-hunting": {
"url": "https://mcp.platform.censys.io/threat-hunting/mcp/"",
"headers": {
"X-Organization-ID": "your-organization-id",
"Authorization": "Bearer your-censys-personal-access-token"
}
}
}
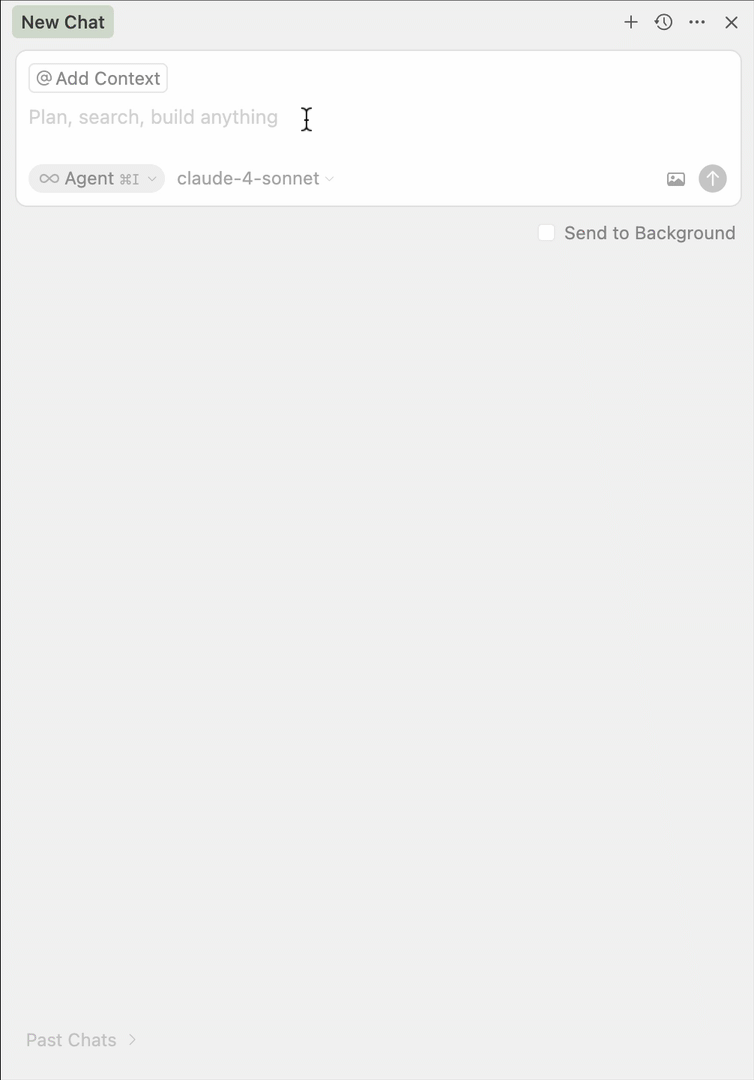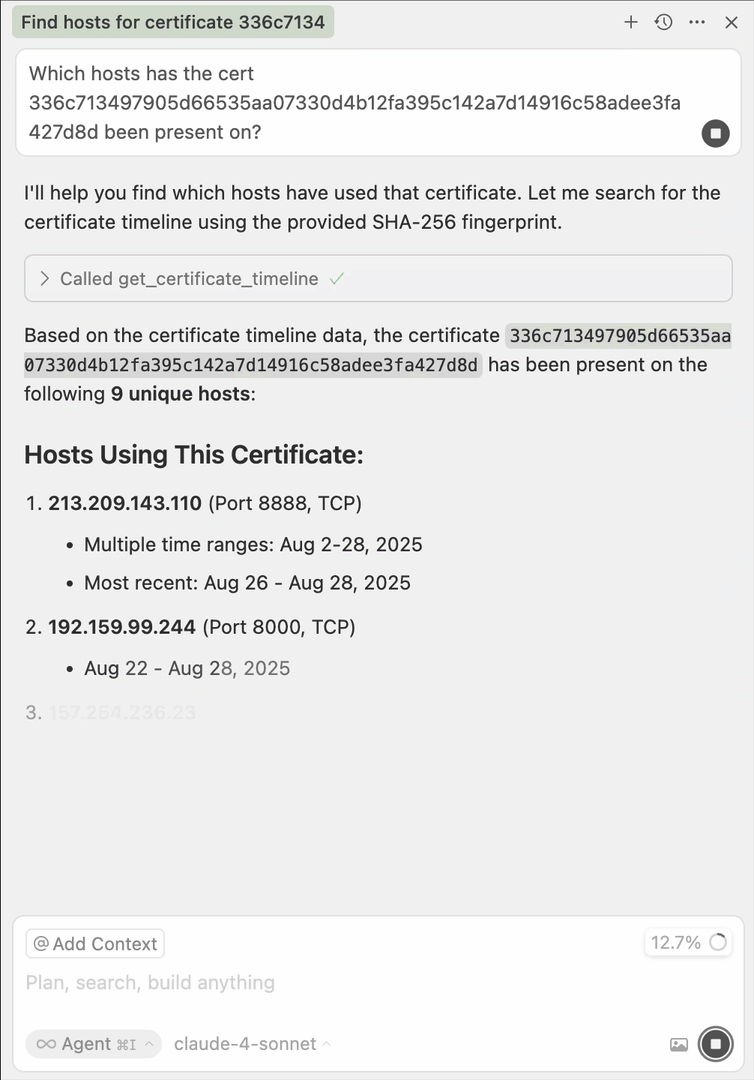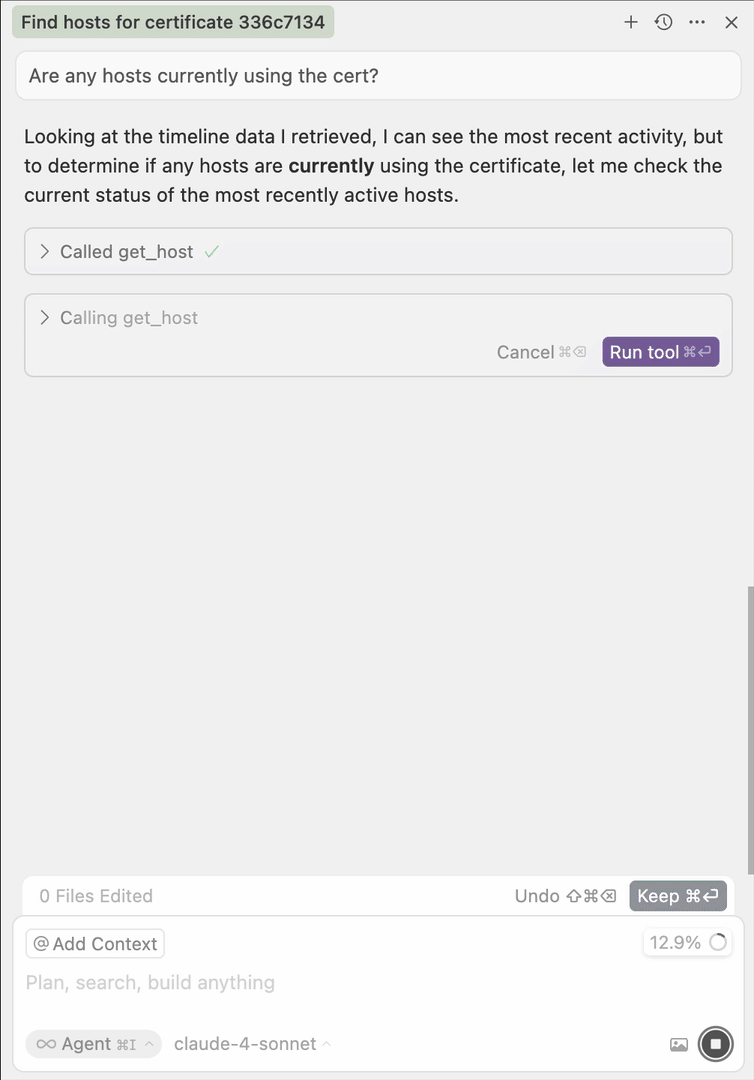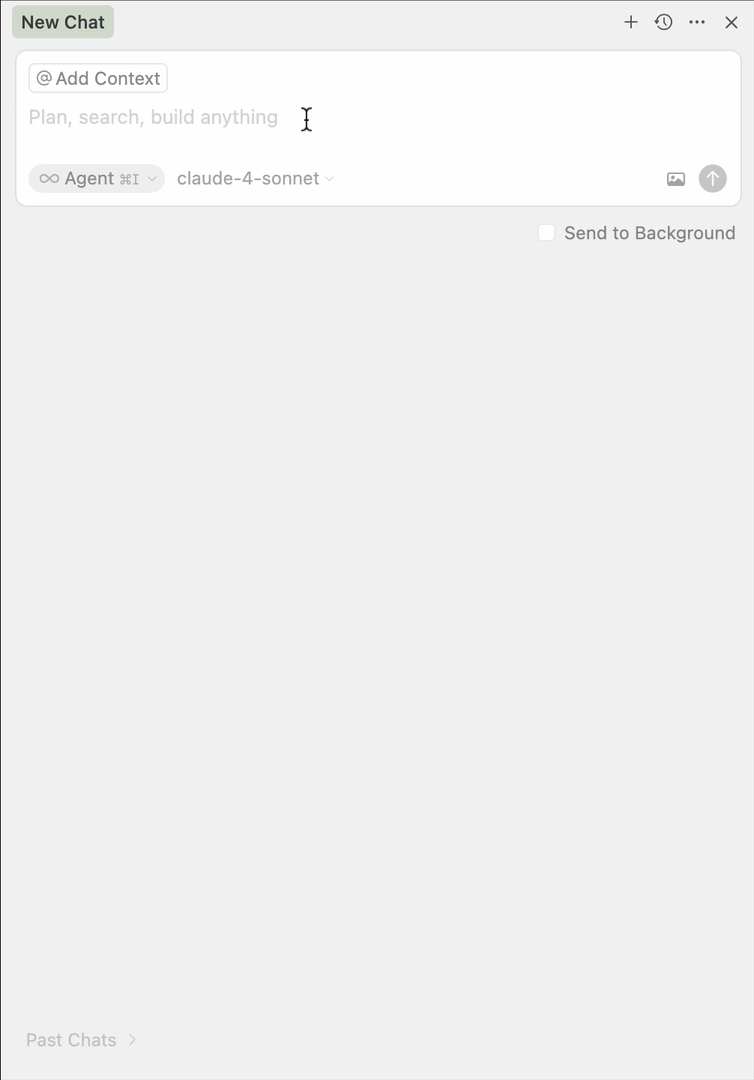
}After configuring your integration, test it by prompting your agent to use Threat Hunting functionality, such as finding hosts that have historically used a certificate based on the certificate's fingerprint.
The output may depend on your specific configuration, but your agent should use the GET host history endpoint to retrieve information about the hosts that have been historically used by the certificate.
Example use cases
Initiate a scan for a currently unobserved service on a host or web property
Use the agent to target a currently unobserved service at a specific IP and port or hostname and port. For example, instruct your agent to scan port 12345 on host 1.1.1.1.
Track active command and control (C2) frameworks
Instruct your agent to show all hosts running a particular type of C2 software, such as "show me all hosts running Cobalt Strike."
Map adversary infrastructure by network
Prompt your agent to report which ASNs are being used for a particular threat. For example, "in which ASNs do we see hosts running PolarEdge Botnet?"
Pivot on infrastructure characteristics
Instruct your agent to find interesting pivots for a particular IP address. For example, "find interesting pivots for 38.159.89.211."
Investigate certificate re-use
Find hosts that historically have used a certificate. Use a prompt like "show me all hosts that presented the certificate fingerprint 136fbfd2d255a7fc69c16fe115138d7a53ed0a7db8302017ee0e692b42d82ffe in July 2025."
Threat Hunting MCP tools
In addition to functionality that is equivalent to the Platform and Threat Hunting APIs, the Threat Hunting MCP server features the following tools.
| Tool | Description |
|---|---|
generate_query | Converts natural language requests into valid CenQL queries. |
generate_and_search_query | Generates a Censys search query from natural language and searches the query. |
Updated 4 days ago
