Introductory Use Cases
The datasets available in Legacy Search support security practitioners in their efforts to make Internet-facing systems—and the internet in general—more secure and safe.
NoteCensys Legacy Search is an older tool used to search across the Censys Internet Map. Use the Censys Platform to find more data and explore deeper connections on the internet. Learn about how to get started with the Platform here.
Key use cases
- Investigate indicators of compromise (IoCs): Find and track threat actors on the internet via the infrastructure they set up.
- Enrich internal threat feeds with host and certificate data: Augment network logs with the most accurate, up-to-date public profile of the entities within and connecting to your network.
- Create a timeline of adversary infrastructure: Investigate how and when an adversary weaponized infrastructure. See the history of a compromised or suspicious host.
- Understand the global impact of vulnerabilities across the Internet: Conduct security research to understand the global impact of vulnerabilities across the Internet from CVEs to zero-days like SolarWinds or Microsoft Exchange.
- Map your external attack surface: Investigate and view your attack surface from an external perspective by finding your Internet-facing assets and evaluating them for vulnerabilities.
Investigate indicators of compromise
The rich, highly indexed datasets available in Legacy Search allow you to find the needles in the haystacks when you’re threat hunting. With Legacy Search, you can take threat intelligence from internal or public sources to build, validate, and investigate IoCs on hosts across the Internet.
Understanding the Censys host fields where the indicators are located is essential for finding them.
Examples
In the Censys Search web UI:
- Ask a question like, "Which hosts are serving reused/reusable malicious content?"
- Query for fingerprints using hashes:
services.http.response.body_hash: {SHA1-hash of a site serving malicious content}
- Query for fingerprints using hashes:
- Ask a question like, "Which hosts that I tagged have another characteristic I’m interested in?"
-
Search within your tags:
tags: {my-tag-name, my-other-tag-name} and services.service_name: DNS
-
Advanced technique
- Ask, "What are the most common values for this one field on hosts matching my query?"
- See a breakdown of values for interesting fields from your search results by creating reports. For example, you can create a report for operating system vendors of hosts in an AWS netblock.
Enrich internal threat feeds with Censys host and certificate data
As you monitor network activity, you can look up IPs that your hosts are connecting to or receiving connections from. The Legacy Search view host API endpoint is fast and performant, so you can immediately enrich your network security logs with host profiles from Censys.
Example
You can use the API to retrieve host profiles programmatically.
- Ask a question like, "What does this host that’s connecting to my network look like from an external perspective?"
- Use the API to
GET https://search.censys.io/api/v2/hosts/{ip-address}- Parse the host’s location data to look for geographic irregularities
- Check for non-standard protocol/port pairs in the service info
- Look for suspicious certificates (self-signed, issued by Let’s Encrypt, or containing suspicious names)
- Check the DNS names resolving to the host
- Use the API to
Advanced technique
Layer Legacy Search host profiles with Greynoise analysis and IP reputation data to help determine whether a host is suspicious.
Create a timeline of adversary infrastructure
See how a host has changed over time. Observe how services appeared, disappeared, or how new certificates were presented to chart how this infrastructure was weaponized.
Example
- Ask the question, "What changes have been observed on this host in the past?"
-
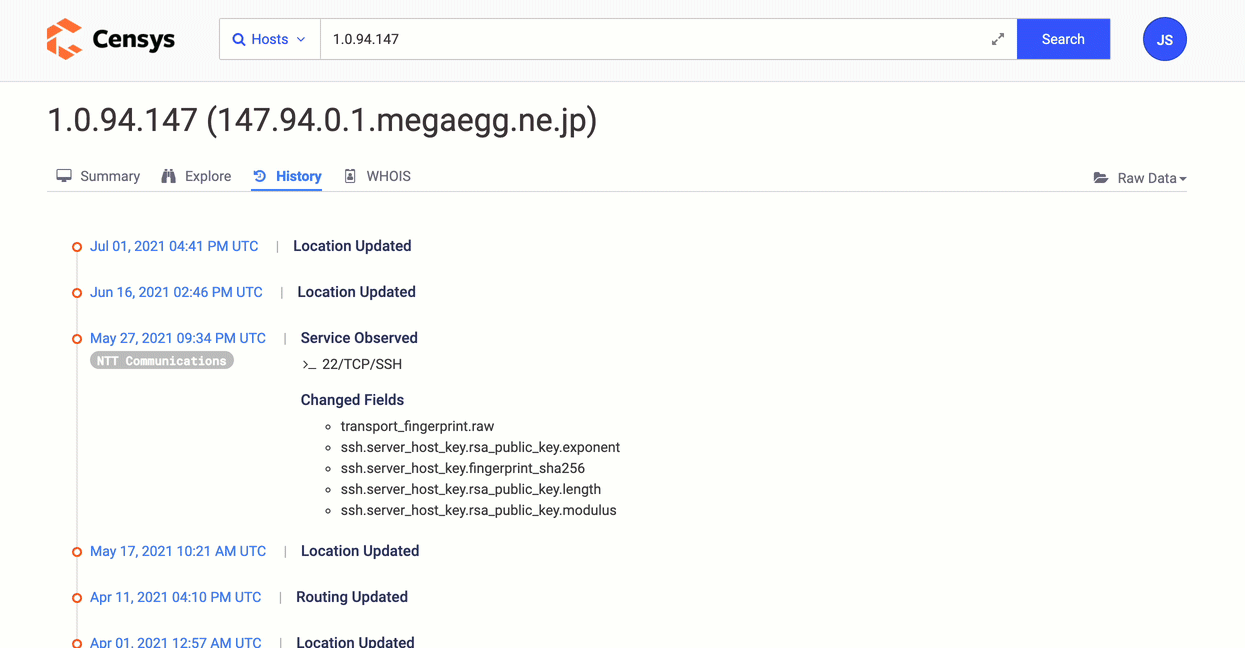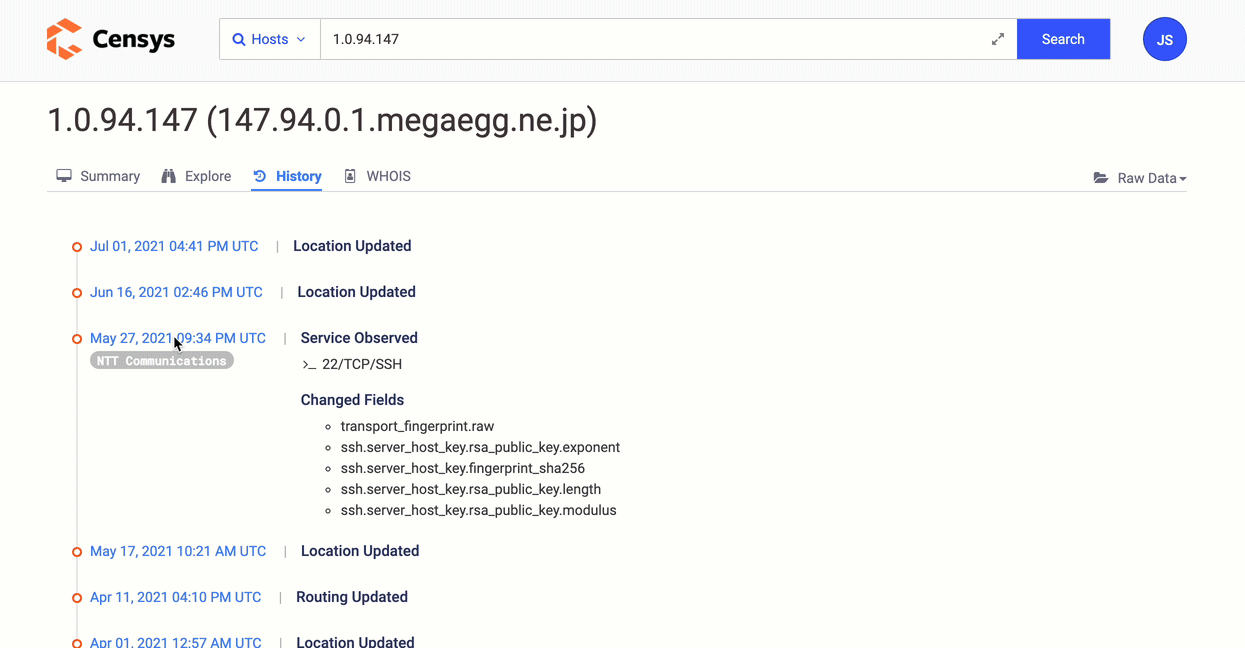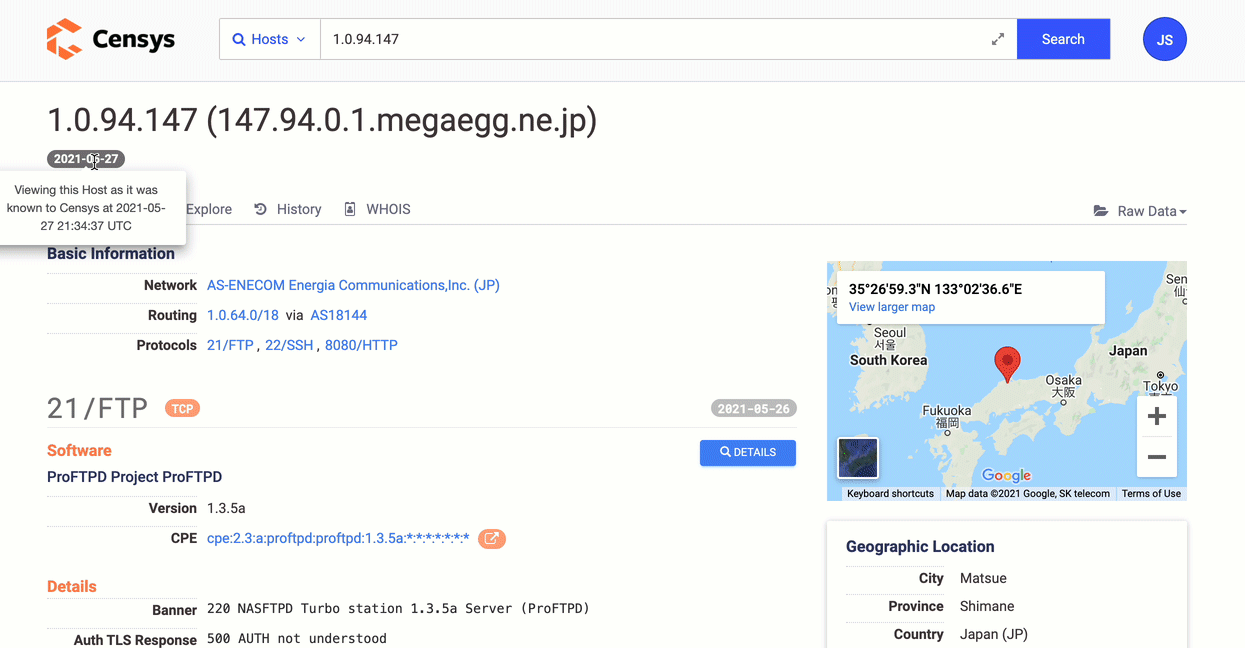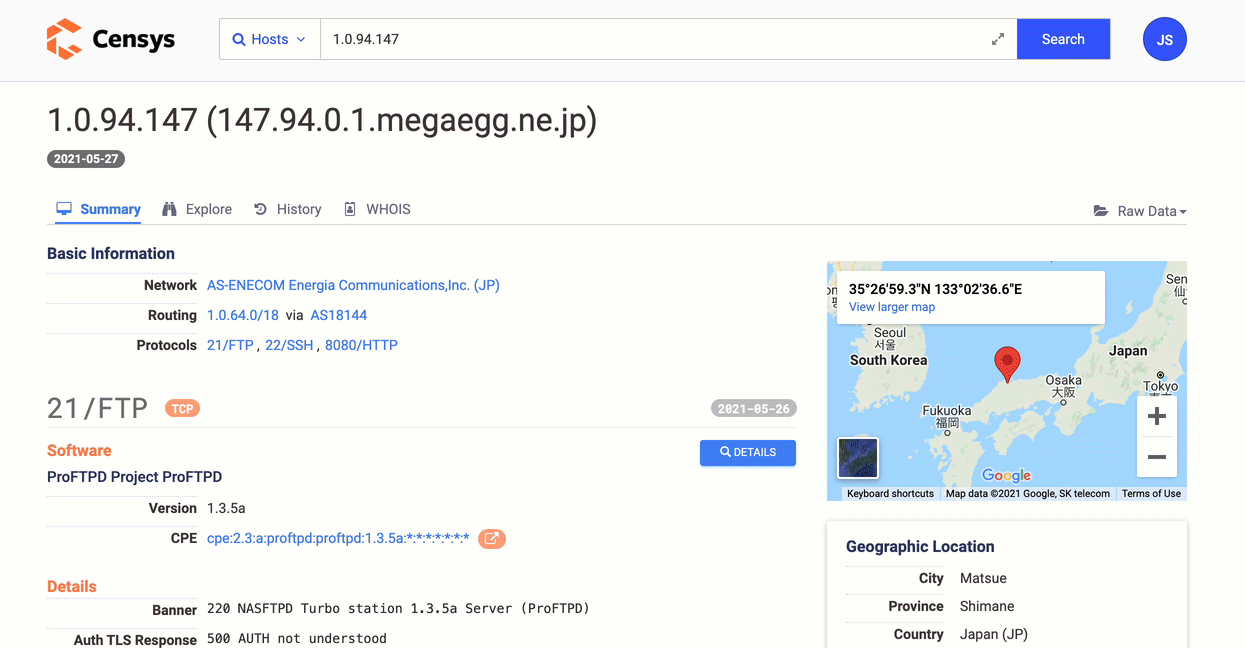
On every host details page, the History tab lists reverse-chronologically ordered host events.
You can browse events, select two points in time to calculate a diff or go back in time to view a host as it was recorded in Censys datasets then.
-
Advanced technique
- Ask questions like, "What are the differences between two different hosts?"
- To generate diffs, use the host diff API call, which offers greater flexibility than the UI.
Understand the global impact of vulnerabilities across the Internet
Search the entire Internet for hosts vulnerable to a new or existing vulnerability. Common Platform Enumeration (CPE) formatted software fields are available in Censys datasets and can be used in tandem with the Common Vulnerability Enumeration (CVE) framework. Leverage CVE Context on Censys Search for deeper and more efficient queries.
Example
In the Legacy Search web interface:
- Ask a question like, "Which hosts are running a software version that I know is vulnerable to a particular vulnerability?"
- Search for CPE-formatted software identifiers:
services.software.uniform_resource_identifer: {CPE-formatted software URI}- For example, you can search for hosts with Pulse Connect Secure software.
- Search for CPE-formatted software identifiers:
Advanced technique
Upgrade to a Pro account to use regular expressions for even more fine-grained searching.
Map your external attack surface
Look at your organization’s Internet presence from the outside. Profile hosts, services, and certificates to assess your overall security posture and make improvements. Reduce public exposure, patch outdated or vulnerable systems, and practice good hygiene with Internet assets.
Examples
In the Legacy Search UI:
- Ask a question like, "What other entities are connected to this one?"
-
On the Host Summary pages, click the Explore tab to use the visual explorer to find related certificates, names, and hosts.
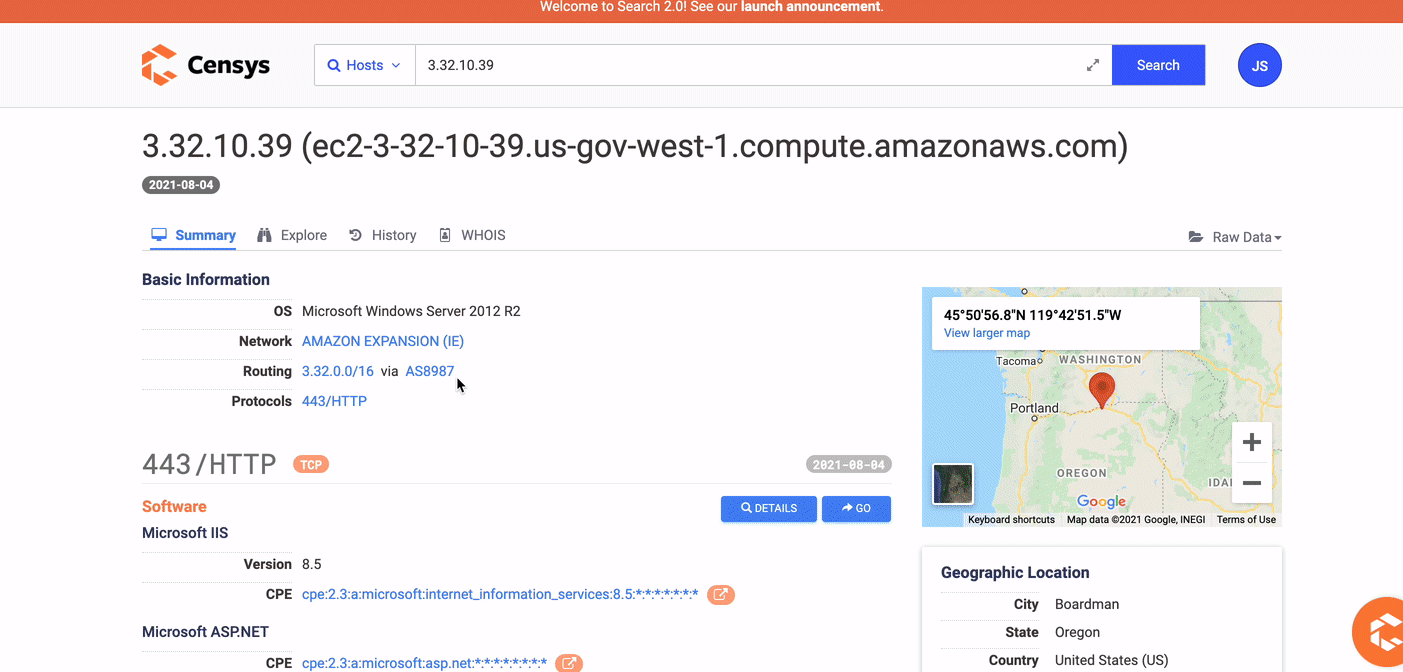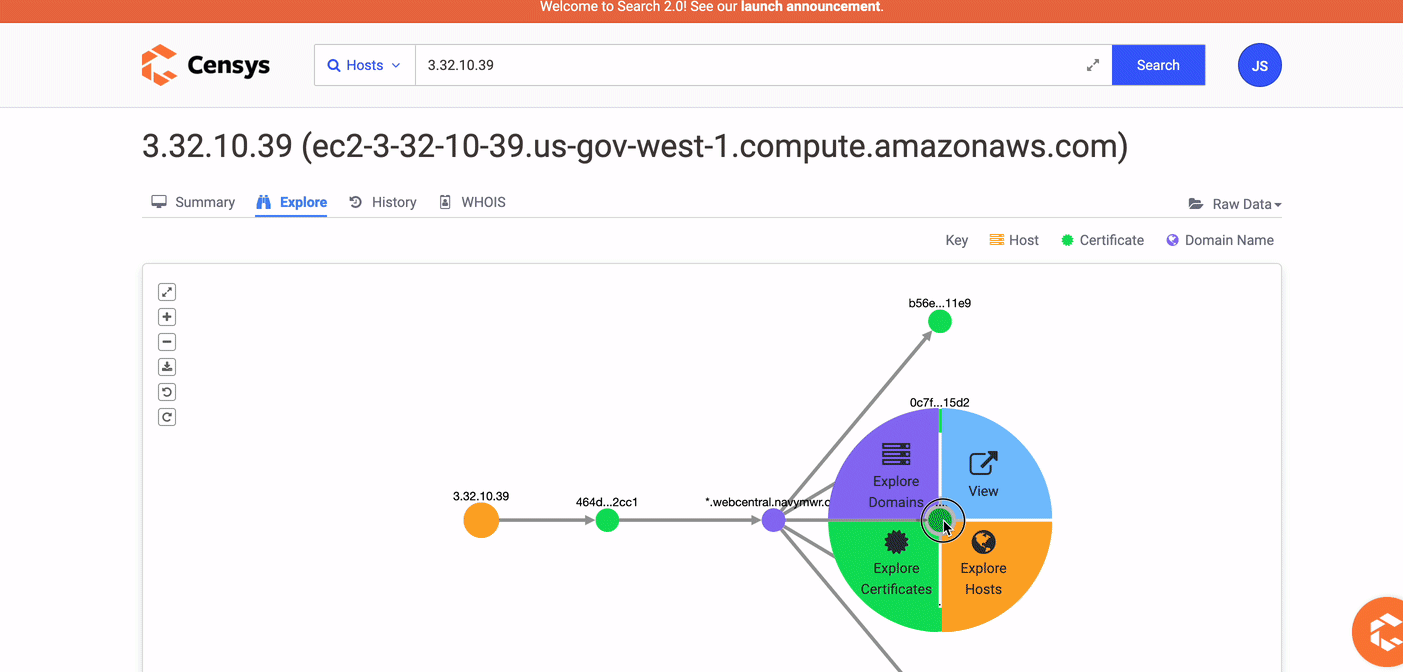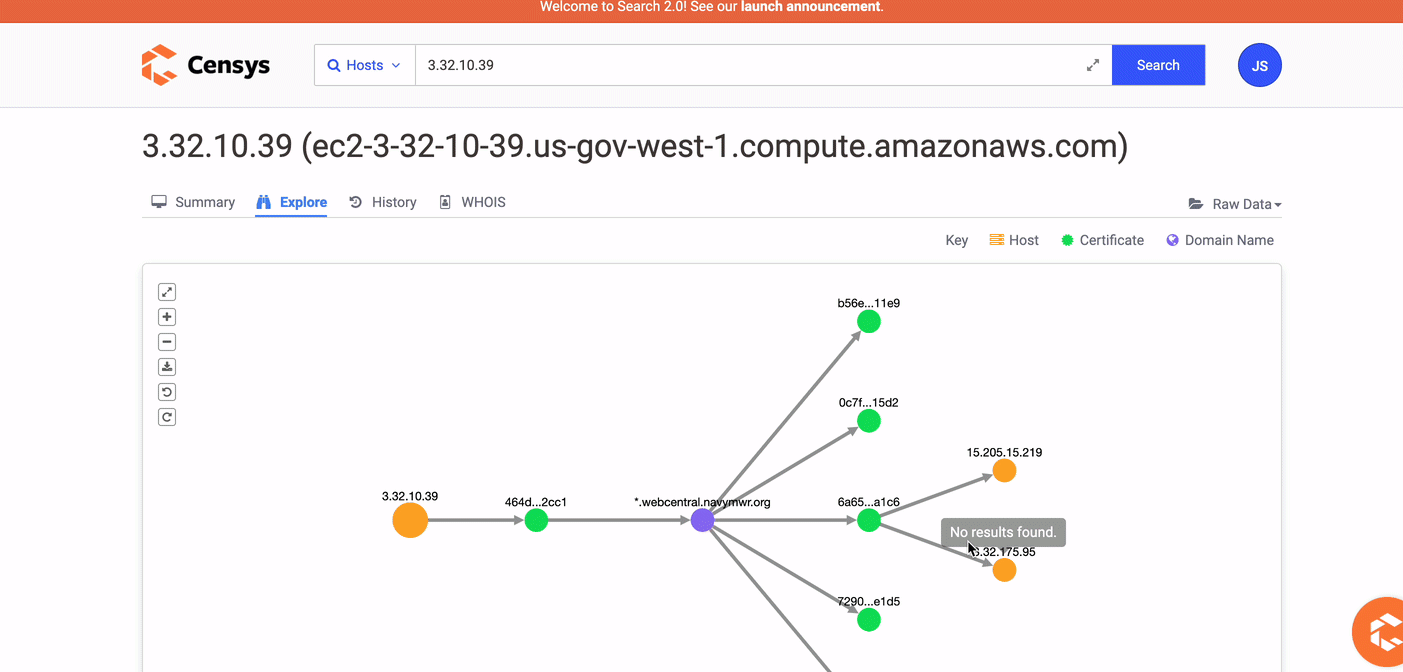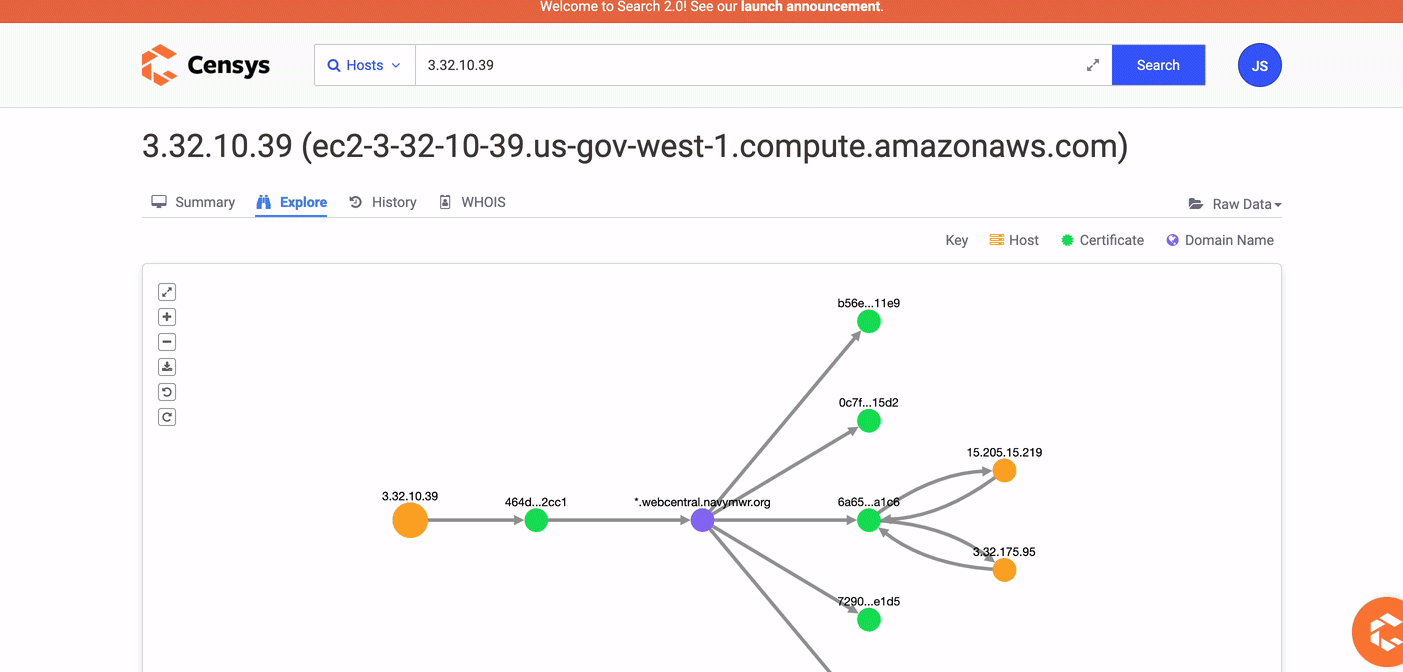
-
- Ask a question like, "Which hosts within my organization’s registered netblocks are online or have this characteristic?"
- Search for and within CIDR blocks assigned to your organization:
ip: X.X.X.X/# and …
- Search for and within CIDR blocks assigned to your organization:
- See an example search within a CIDR.
Advanced technique
Check out the [Censys Attack Surface Management tool](https://censys.com/attack-surface-management/, which helps you shrink your attackable network surface area with best-in-class asset discovery, comprehensive inventory, risk analysis, and a cloud security offering tailored for cloud-based organizations.
Next steps
Now that you understand what you can accomplish with Legacy Search, learn how to write queries using the Censys Search Language.
Updated 3 months ago
