Multi-factor Authentication
You can secure your Censys Platform account by adding multi-factor authentication (MFA) with an authenticator app like Google Authenticator, Microsoft Authenticator, Duo Mobile, and more.
Organization admins can require organization users to enable MFA in order to access the Platform.
Enable MFA for your account
To enable MFA for your account:
-
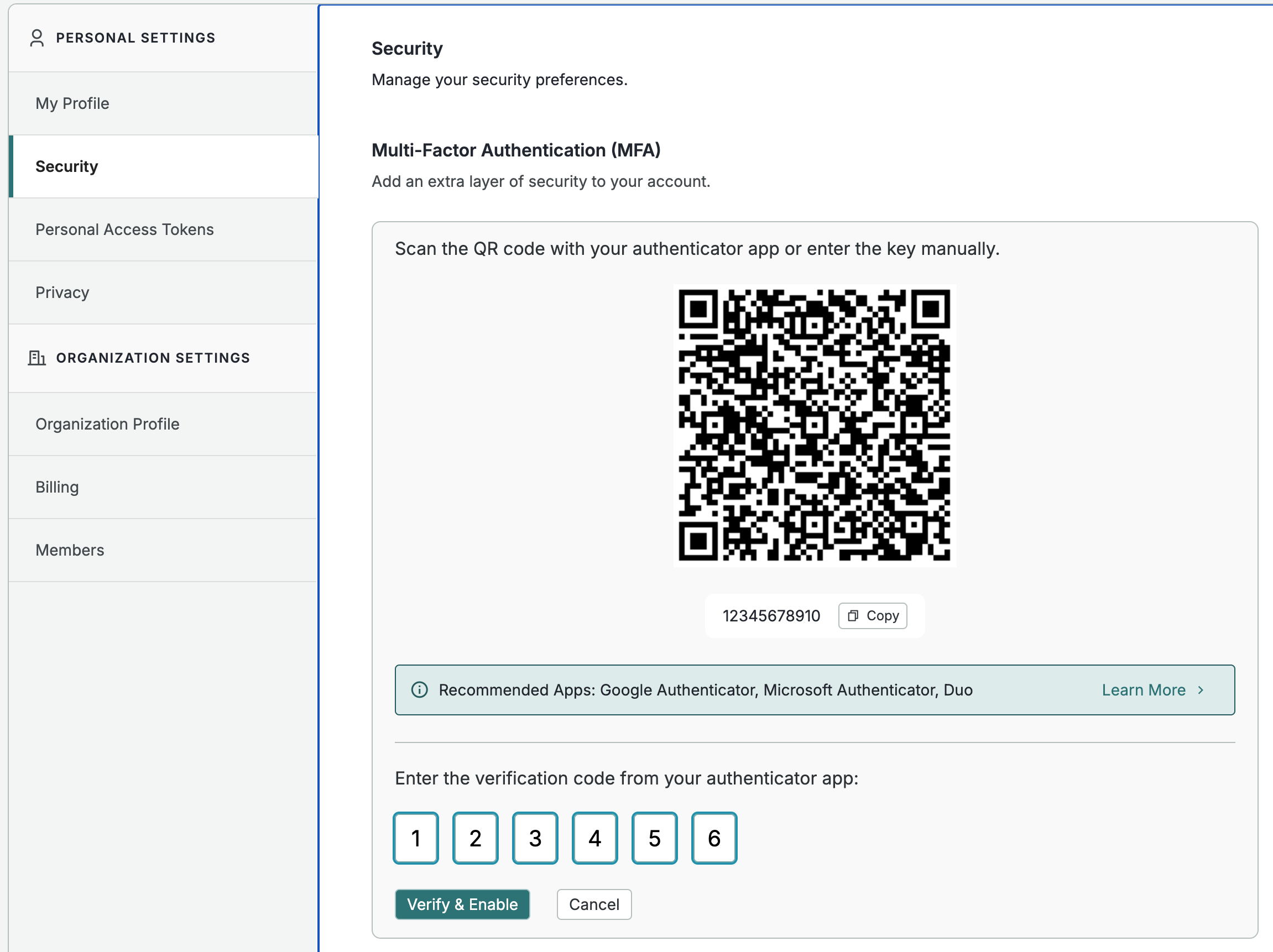
In the Platform web console, go to Settings > Account Management > Personal Settings > Security.
-
Under Multi-Factor Authentication (MFA), Click Configure MFA.
-
Scan the QR code or enter the generated key using your authenticator app of choice.
-
Generate and enter a verification code from your app.
-
Click Verify & Enable. Store your recovery codes in a secure place.
The next time that you log in, you will be required to enter a code from your authenticator app.
Update your MFA configuration
To update the MFA configuration for your account:
- Go to Settings > Account Management > Personal Settings > Security.
- Under Multi-Factor Authentication (MFA), click Update Configuration and follow the process shown above to set up your new MFA app.
Unlink your MFA configuration
To unlink MFA for your account:
- Go to Settings > Account Management > Personal Settings > Security.
- Under Multi-Factor Authentication (MFA), click Unlink Authenticator App and confirm your choice.
Organization MFA management
NoteOnly organization admins can configure MFA settings for their entire organization.
To manage whether MFA is required for users in your organization:
- Go to Settings > Account Management > Organization Settings > Security.
- Next to Multi-factor Enforcement, set the toggle to on or off.
- Click Update Organization Security to save your configuration.
If you turn on MFA enforcement for your organization, users will be required to set up MFA the next time they log in.
MFA and SAML SSO
If you enable MFA enforcement and have SAML SSO configured, MFA enforcement will only apply to users in your organization that are not authenticated with SAML via your identity provider.
Updated about 2 months ago
