CVE Context
Manage vulnerabilities and monitor your threat landscape with searchable CVEs in your host dataset using Censys Legacy Search. Censys CVE data enriches host data with known CVE information for operating systems, software, and hardware.
CVE fields include:
- CVE ID
- Whether a CVE is present in CISA's Known Exploited Vulnerability (KEV) catalog and when it was added to the KEV catalog
- CVE CVSS v3.0 score
- CVE Attack Complexity rating
The hosts data definitions page contains a complete list of CVE fields available for host records.
CVE data in Censys Search is available as an add-on to Search Pro and above customers. To learn more about this feature, please contact your Censys team representative.
Use and view host CVE data in the Legacy Search UI
CVE data for hosts is available in the web interface and can be viewed and used in several different ways.
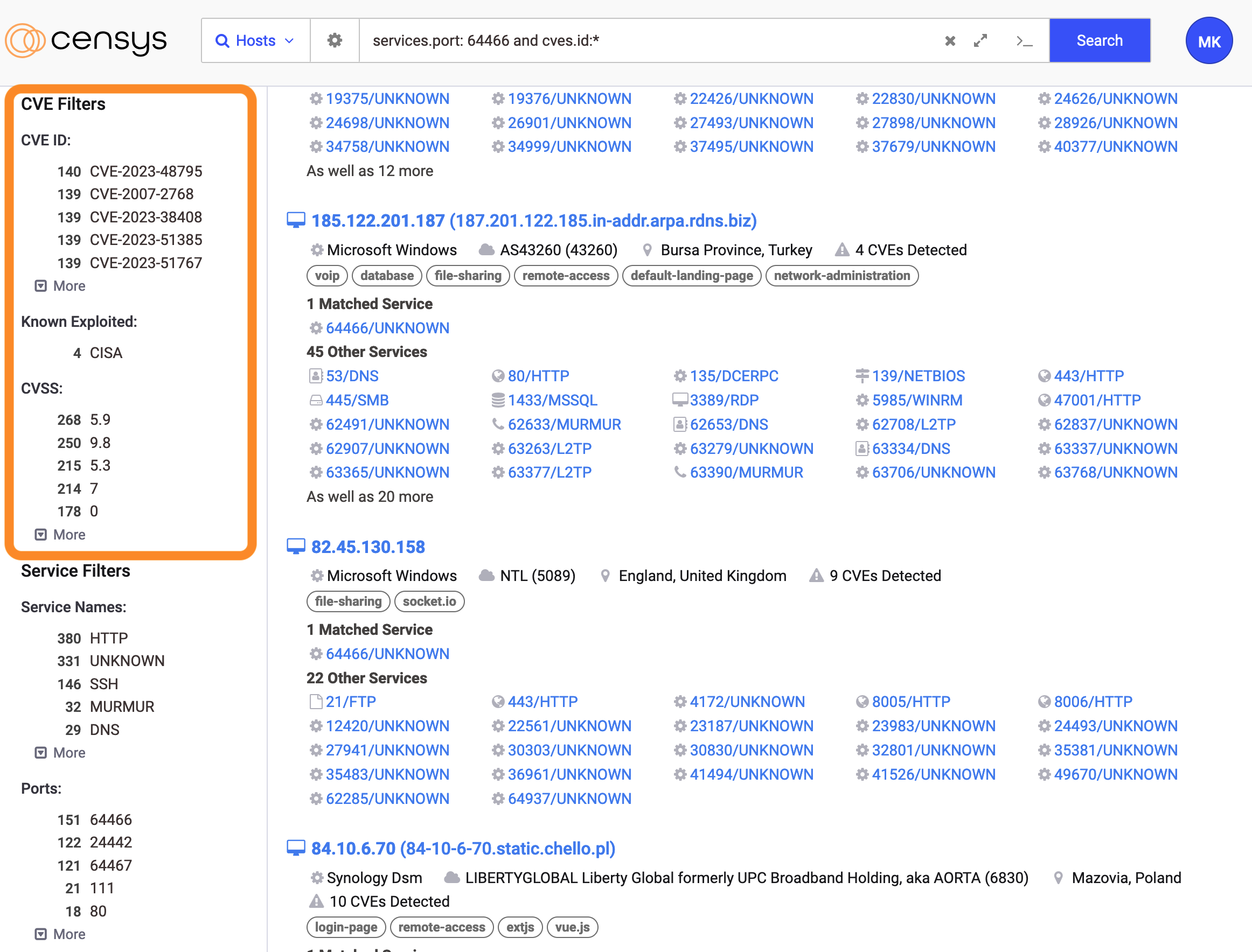
Filters in search results
-
Filter by CVE ID, CVSS scores, and CISA’s KEV catalog in the left navigation panel.
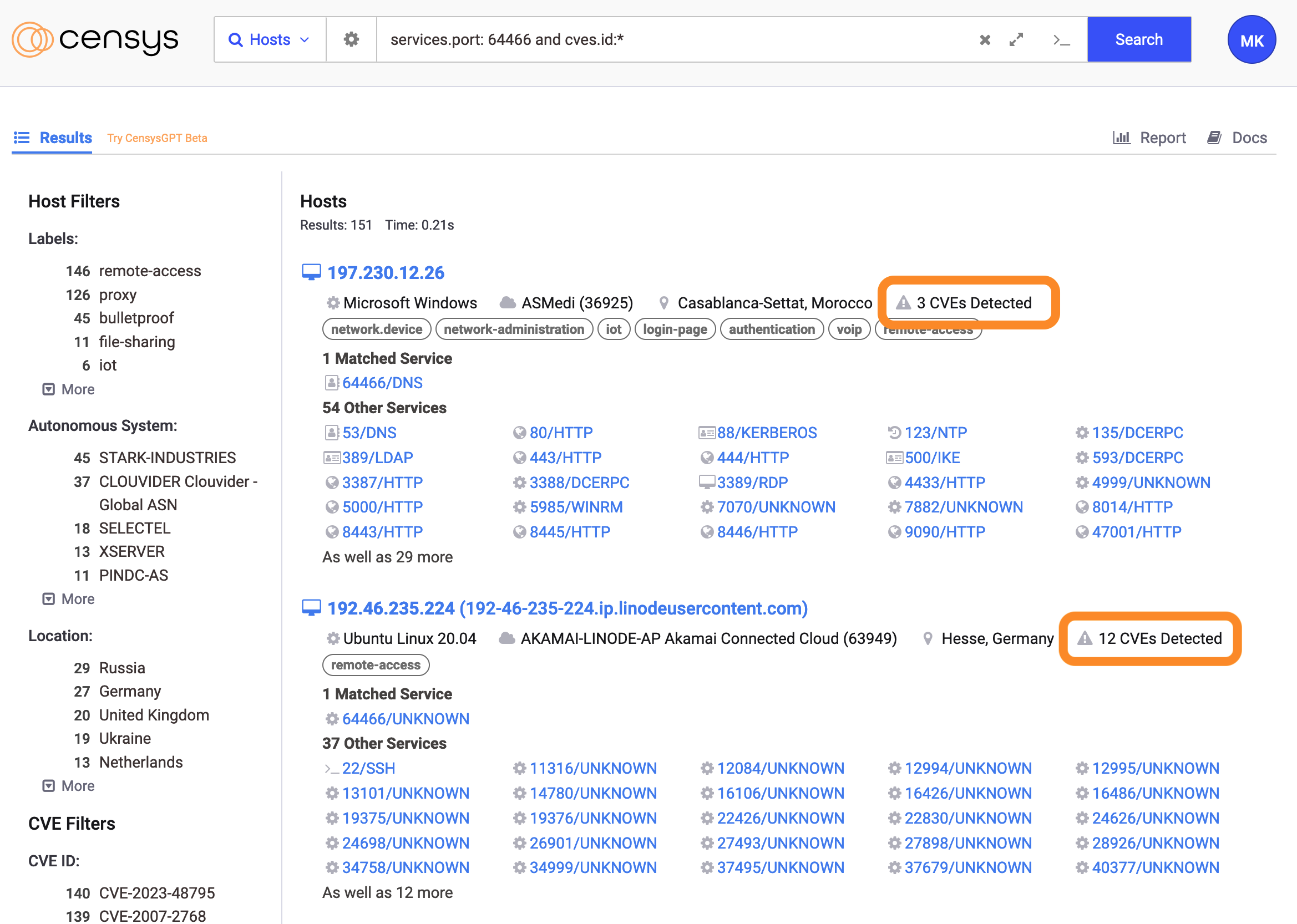
CVE count in host record preview
-
See the total number of CVEs for a host at a glance in the host record preview in search results.
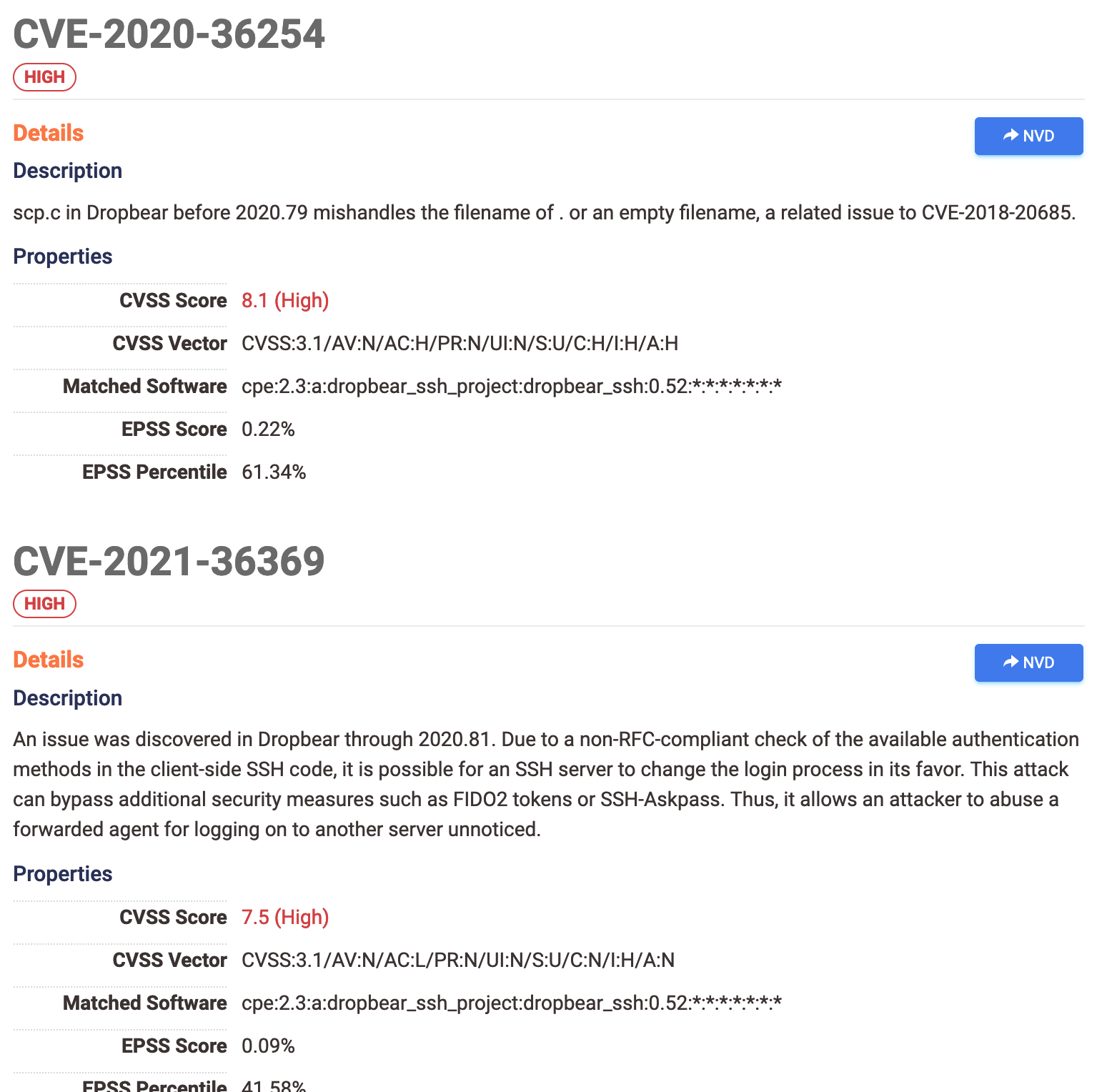
CVEs tab and page on host records
-
The CVEs tab displays the total number of CVEs associated with a host record. Click this tab to view detailed information about all CVEs detected on a host, sorted by CVSS score and KEV catalog status.
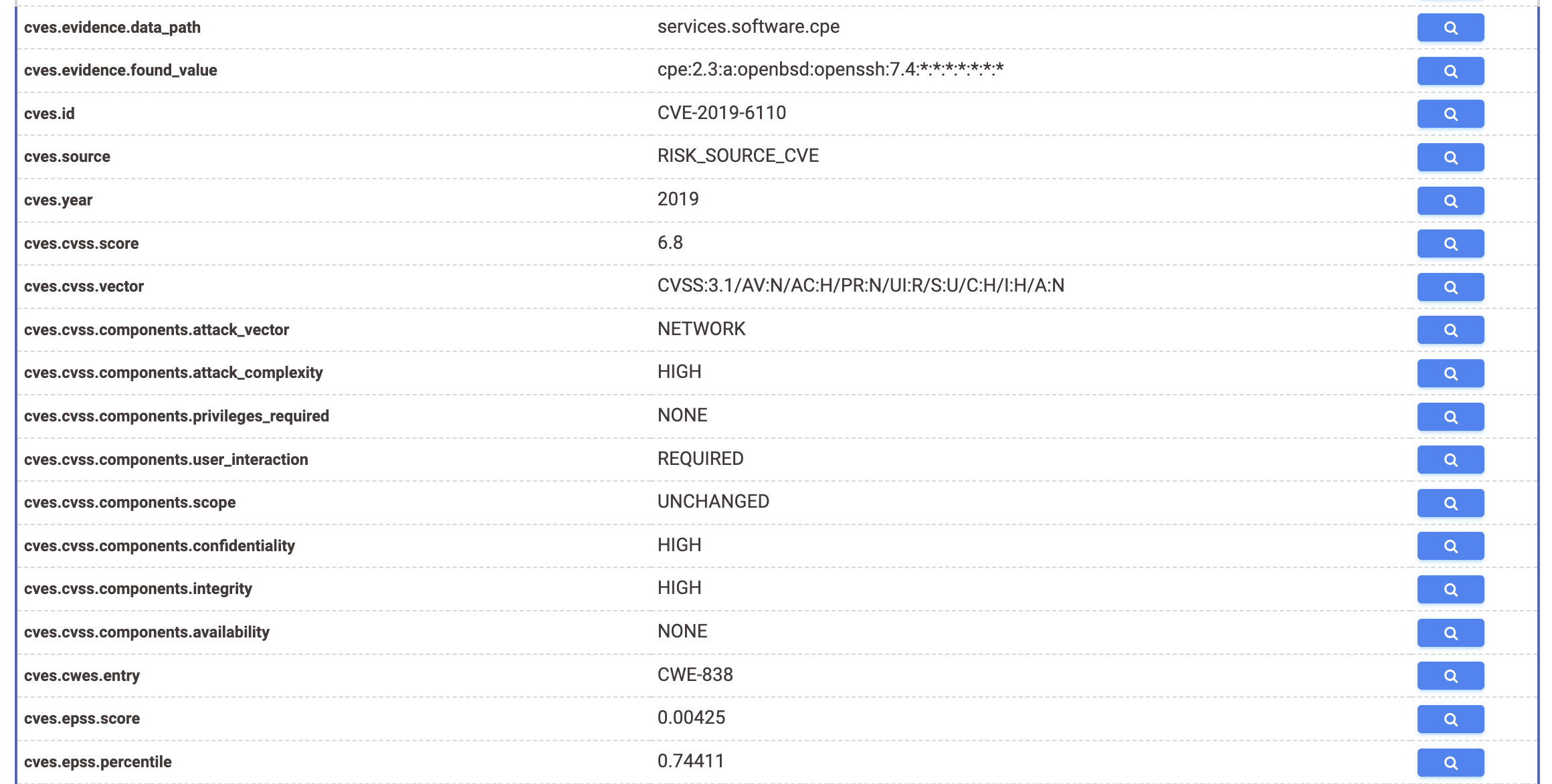
View all raw CVE data for a host
-
Click Raw Data > Table on the right side of the host's summary page and scroll down to the CVE section.
Use and view CVE data via API
The API allows you to retrieve CVE data using the fields provided on the host data definitions page.
CVE query examples
Use the following queries to search CVE data:
| Query description | Query syntax |
|---|---|
| Critical CVEs that are KEVs | cves.cvss.score: [9 to *] and cves.kev: * |
| KEVs from a specific year | cves.kev: * and cves.year: 2024 |
| Easily exploitable CVEs | cves.cvss.components.attack_complexity="LOW" |
| CVE identifiers | cves.id="CVE-2019-14540" |
| Critical CVEs that an unauthenticated attacker can easily exploit | cves.cvss.score: [9 TO 10] and cves.cvss.components.privileges_required="NONE" and cves.cvss.components.attack_complexity="LOW" |
Updated 12 months ago
