Certificate History
The certificate timeline provides a visual history of when a certificate was present on hosts. This visualization gives you historical context that simplifies the discovery of patterns, trends, and anomalies that could signal malicious behavior.
Certificates can act as strong indicators of compromise (IOCs) because threat actors often reuse a certificate across multiple assets over time. If a certificate is used by a threat actor, they will likely use it again. While a certificate may be used by only a few hosts or web properties, uncovering the assets that previously presented it helps to identify related infrastructure, build better queries, and track the evolution of attack infrastructure over time.
You can pivot directly from the timeline to investigate the historical configurations of hosts, providing a faster and deeper understanding of adversary behavior.
In the Platform UI, the Timeline tab is located below summary information on certificate record pages.
This animation shows how to use the certificate timeline to find a host that has historically presented a certificate.
NoteIt may take up to 24 hours after a host service has been observed for it to appear in the certificate timeline.
Host history for a certificate can also be obtained via API.
You can identify certificates of interest by pivoting within the Platform UI using the process described below.
Find a certificate of interest on a host or web property
-
Go to a host or a web property with certificate information on a service or web endpoint.
-
On the service summary card, click the value next to Fingerprint. You can also find this value in the raw data in
host.services.cert.fingerprint_sha256andweb.cert.fingerprint_sha256.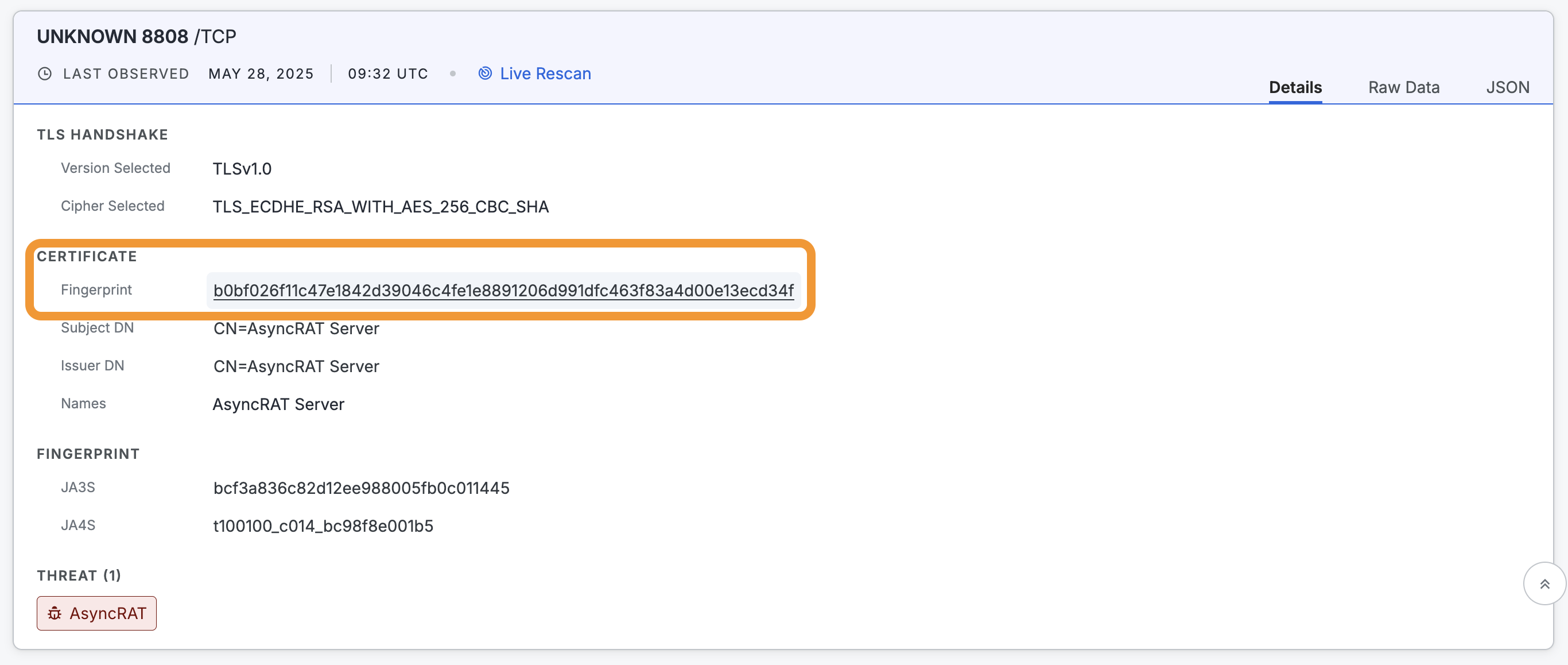
-
On the Certificate Details page, click the Timeline tab.
-
The Timeline tab displays the history of this certificate within a defined time range. Each line of the bar chart represents a host or web property that presented this certificate. In the screenshot below, the certificate is present on numerous hosts beginning on Apr 23.
Sort the timeline by different dimensions to refine your search results including date range, port, and protocol.
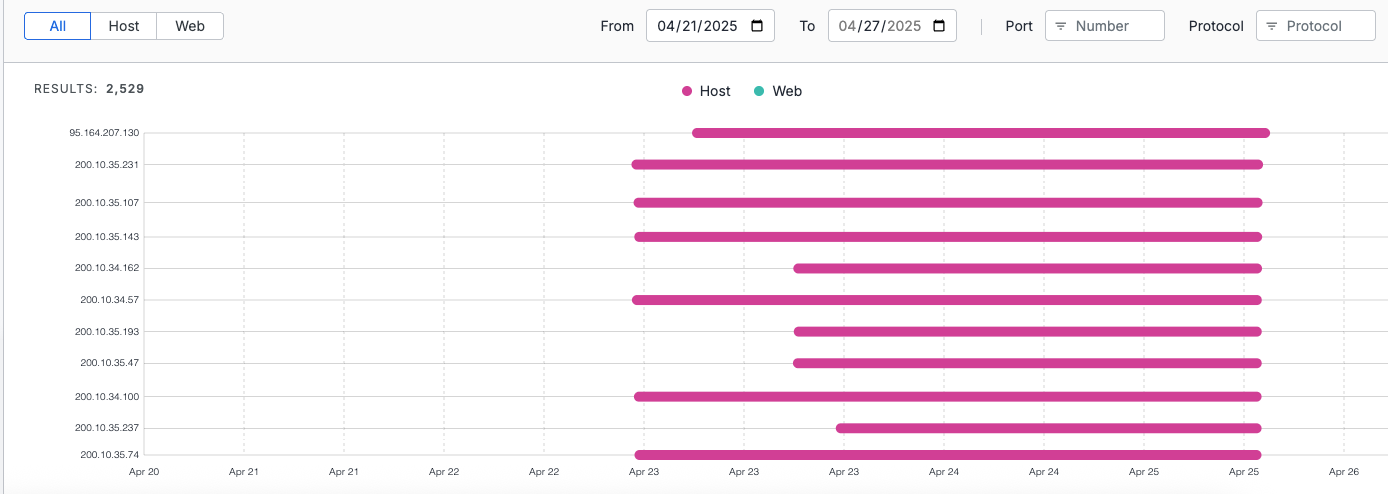
-
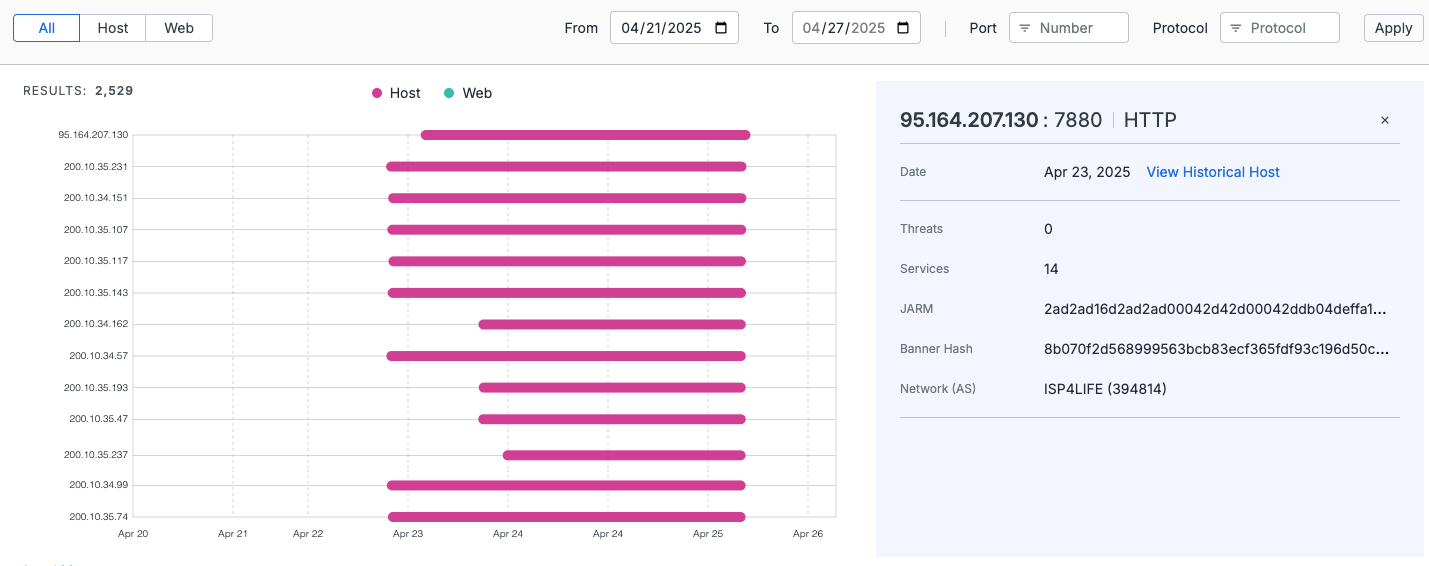
Click a bar plot for an asset to view additional information about that asset at that specific point in time.
In the example below, when the host was presented this certificate, it showed no detected threats, 14 services, the JARM fingerprint, and banner hash that were observed on the host.
Updated about 1 month ago
