JARM
JARM is a method for fingerprinting TLS configurations on hosts to help identify TLS-enabled services.

Use cases for JARM
Threat Hunters can use JARM to:
- Search for C2 infrastructure of malicious actors who use a specially crafted TLS configuration.
Attack surface managers can use JARM to:
- Identify anomalies in TLS configurations in their organization’s network.
- Verify upgrades in TLS configurations.
JARM fingerprint components
The 62-character JARM fingerprint is itself a concatenation of two fingerprints.
- First 30 bytes: The output of a hybrid fuzzy hash of the service’s TLS version and cryptographic cipher usage.
- Second 32 bytes: A SHA-256 digest of the service’s TLS extension usage.
Searchable JARM fields
Censys Search provides four JARM-related fields for querying at the root level of a service object.
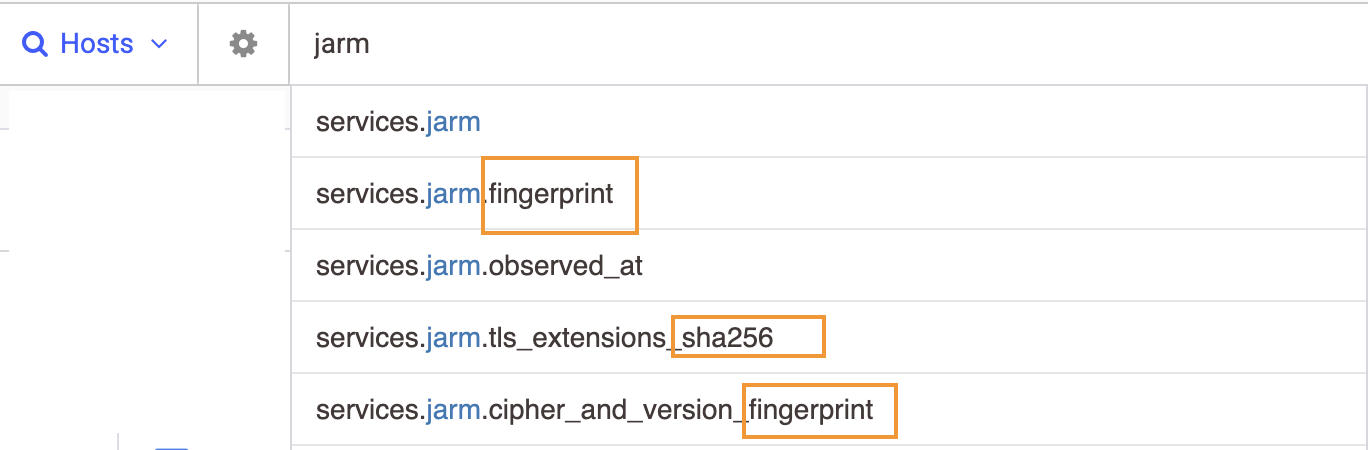
Use the services.jarm.fingerprint to search with a full 62-byte JARM fingerprint, or use one of the two-component fingerprints to search with the first 30 bytes or second 32 bytes.
Use the jarm.observed_at field to restrict your searches to fingerprints obtained within the time frame you feel is fresh enough. The maximum age for JARM fingerprints is 15 days.
| Field | Type | Description |
|---|---|---|
services.jarm.fingerprint | Text | The 62-byte JARM fingerprint of the service. |
services.jarm.cipher_and_version_fingerprint | Text | The first 30 bytes of the JARM fingerprint, which encodes the service’s TLS version and cipher suite configuration. |
services.jarm.tls_extensions_sha256 | Text | The second 32 bytes of the JARM fingerprint is a digest of the service’s TLS extension usage. |
services.jarm.observed_at | Text | The RFC 3339-formatted timestamp indicates when Censys fingerprinted the service. |
API events related to JARM
The Legacy Search API event service_enriched indicates that data not obtained during one of the traditional service scans (such as JARM) was added to a service.
See our API documentation for more information about the details of this event.
Implement JARM
Creating a full JARM fingerprint requires ten separate connections to a TLS-encrypted service.
Censys strives to be a good citizen of the Internet while maintaining the highest quality and accuracy in the host dataset. Censys is careful to collect TLS data without negatively impacting servers worldwide.
Considering this, Censys does not attempt JARM fingerprints of any services on "super hosts" (for example, hosts with more than 99 services).
If a JARM fingerprint is older than 15 days, it is removed from the service data until it can be respectfully re-fingerprinted. Likewise, if Censys detects a change in a service's name—its primary identifier—the JARM fingerprint is also removed, as the likelihood of an identical JARM fingerprint on a new service is very low.
Updated 11 months ago
