Certificates
Certificates are crucial for securing your organization's internet-facing services. With Censys Attack Surface Management, you can efficiently track and manage all certificates associated with your organization. Unidentified services and devices outside your known inventory can introduce security risks.
Use Censys Search in Attack Surface Management to uncover rogue assets beyond your IP ranges, detect unexpected configurations, and identify unauthorized certificates. This will ensure a more secure and comprehensive view of your attack surface.
Certificates list
Go to the ASM web console and click Inventory > Certificates.
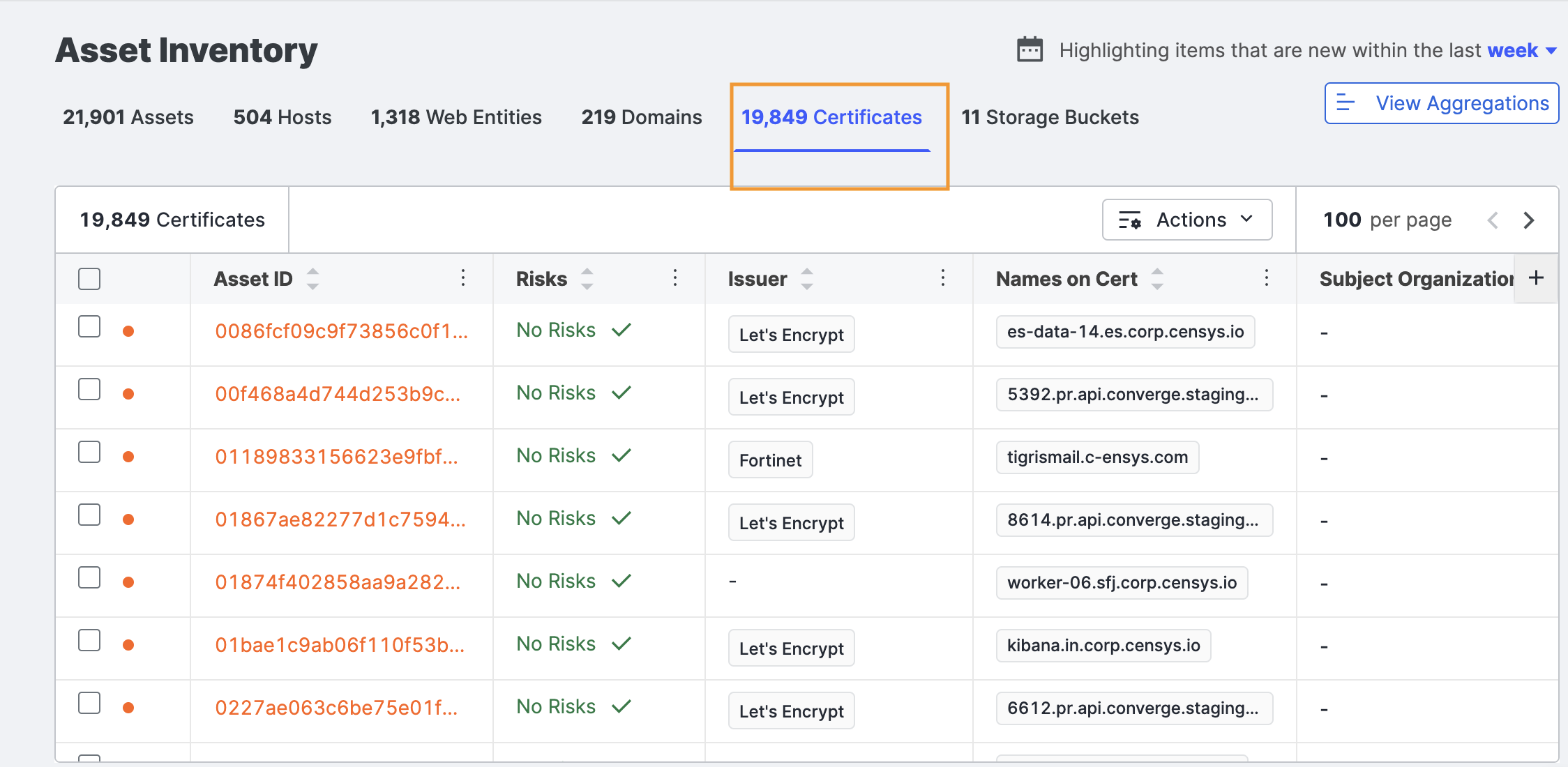
This displays all of the Transport Layer Security (TLS) certificates connected to your organization, including default certs that your hosts may present. The certificates included here are found from Censys Internet scans, as well as from certificate transparency logs. You may discover some certificates you didn’t know existed.
The table contains a catalog of all certificates indexed by SHA-256 fingerprint. By default, the list is filtered to show certificates in use, which means a host presented them during the Censys scan of the Internet.
Other columns in the view of the table include:
- Asset ID: The natural identifier of an asset.
- Risks: Highlights potential security issues related to certificates, such as expired or weakly encrypted certificates, self-signed certificates that could indicate misconfigurations, and certificates issued by untrusted authorities.
- Issuer: The certificate authority that issued the certificate.
- Names on Cert: Any names for which the certificate can verify the identity.
- Subject Organization: The name of the organization to which the certificate was issued, if available.
Column selection
Click the plus icon ( ) above the table to open additional columns with more information about your certificates. Select or clear the columns to create your view.
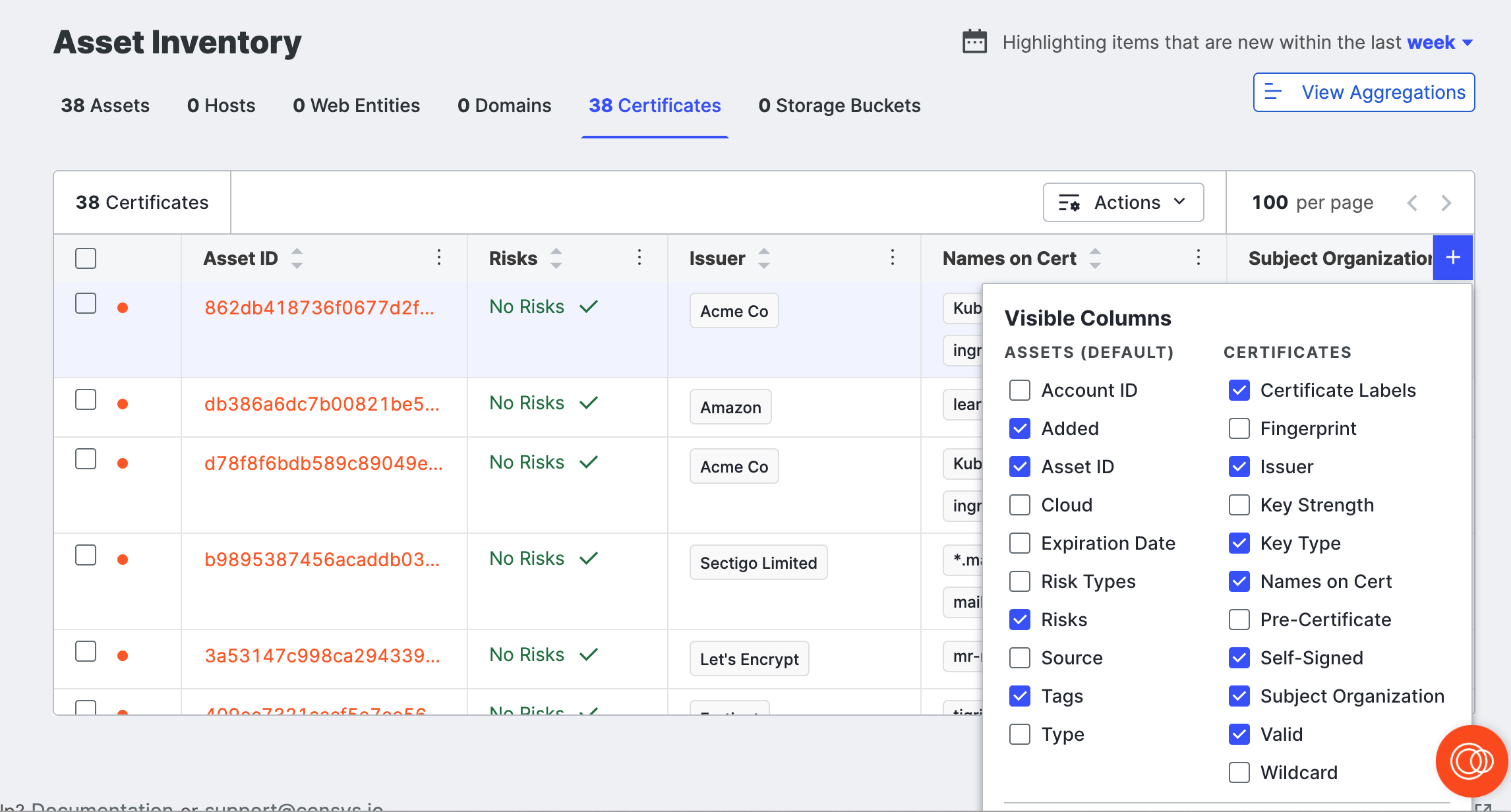
Additional column options include:
- Association Date: The date when the certificate was added to your attack surface.
- Browser Trust: A list of browsers that trust the certificate chain. If empty, none of the four major browsers trust the certificate.
- Tags: Tags applied to the certificate.
- Ownership Status: Whether Censys believes this cert is associated to you (Owned) or not (Unknown).
- Self-Signed: Whether or not the certificate is self-signed (whether the issuer is the same as the subject).
- Self-signed certificates can indicate an internal or development service that is not intended to be exposed to the public Internet.
- Valid: A Censys indicator of trustworthiness based on the certificate’s features, including trust anchors, formatting, signatures, validity dates, and more.
- Key Type: The encryption algorithm of the public key.
Sort columns
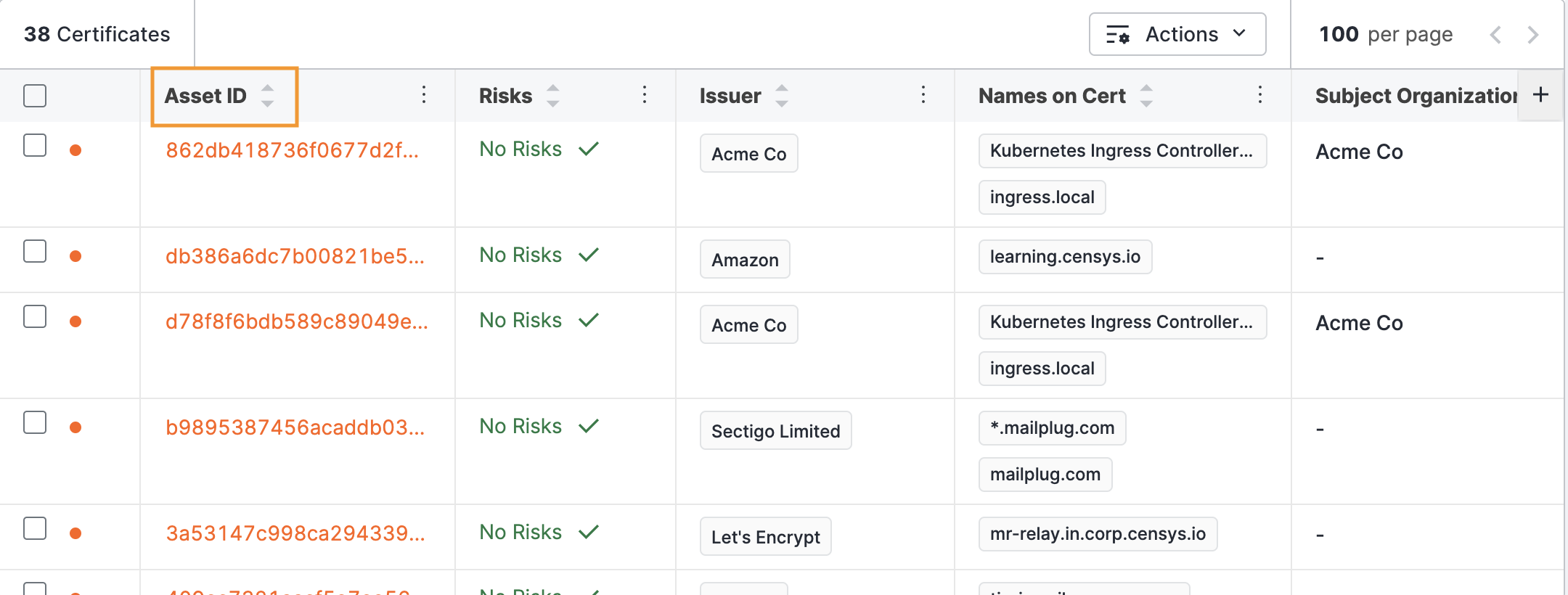
The default sorting for the table is ascending (A-Z) for the Asset ID column. Use the arrows on the other columns to sort the table by those attributes.
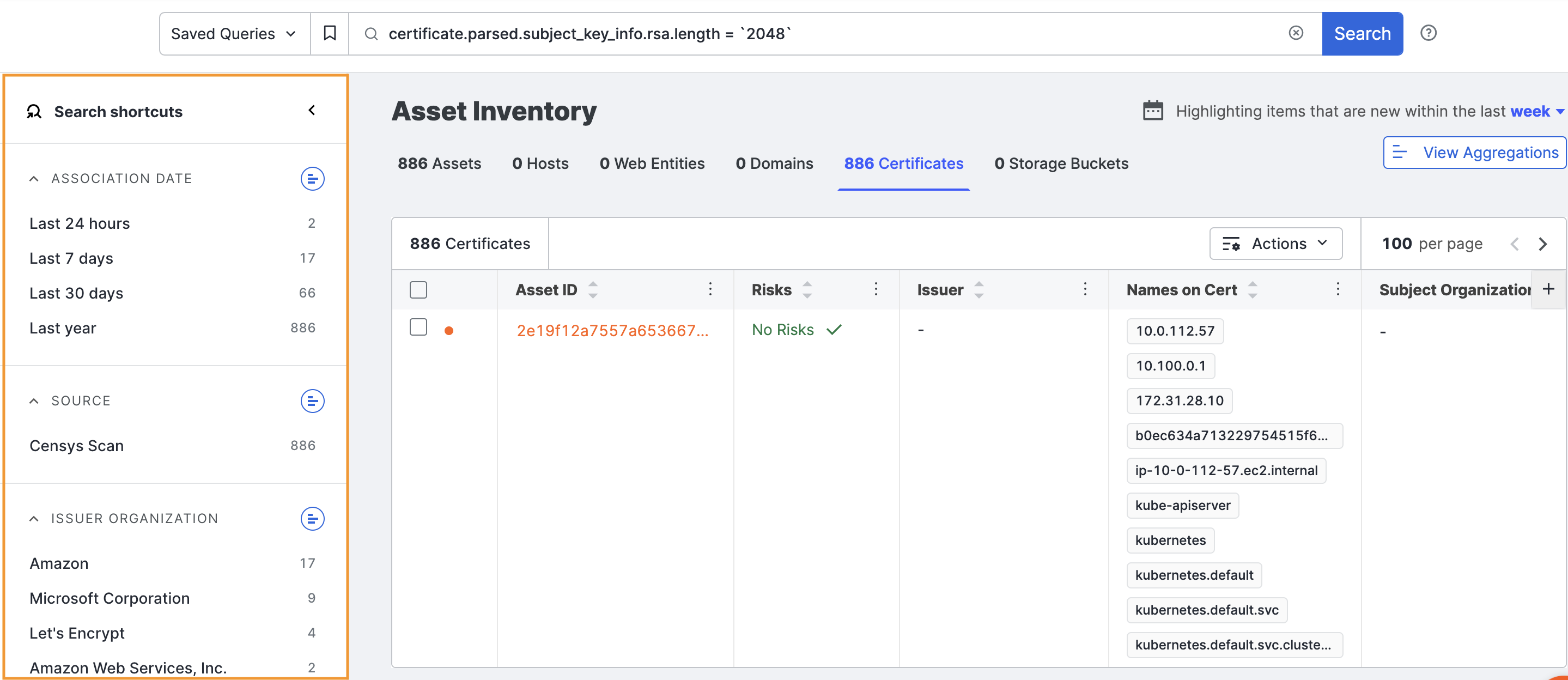
Search shortcuts
Shortcuts include:
- Association Date: The date when the certificate was added to your attack surface.
- Issuer Organization: The certificate authority that issued the certificate.
- Self-Signed: Whether the certificate was issued by the same organization using it or not.
- Key Strength: The length and complexity of the cryptographic key used in the certificate, which impacts security. Shorter keys may be vulnerable to attacks.
- Validity: Indicates whether the certificate is currently valid, expired, or approaching expiration.
- Expired: Expired certificates that are live on a host may be causing service interruptions for your customers.
-
Expires within 7 days: Prioritize replacing these certs to ensure no interruption in service to your customers.
-
Expires within 30 days: Prepare for these expirations by readying new certificates soon.
-
Expires within 60 days: Prepare for these expirations by readying new certificates.
-
Download certificate data
You can download the certificate list as a comma-separated value (CSV) for use in other products and workflows.
-
Click Actions > Download CSV. The default filename is
CertificateExport.csv.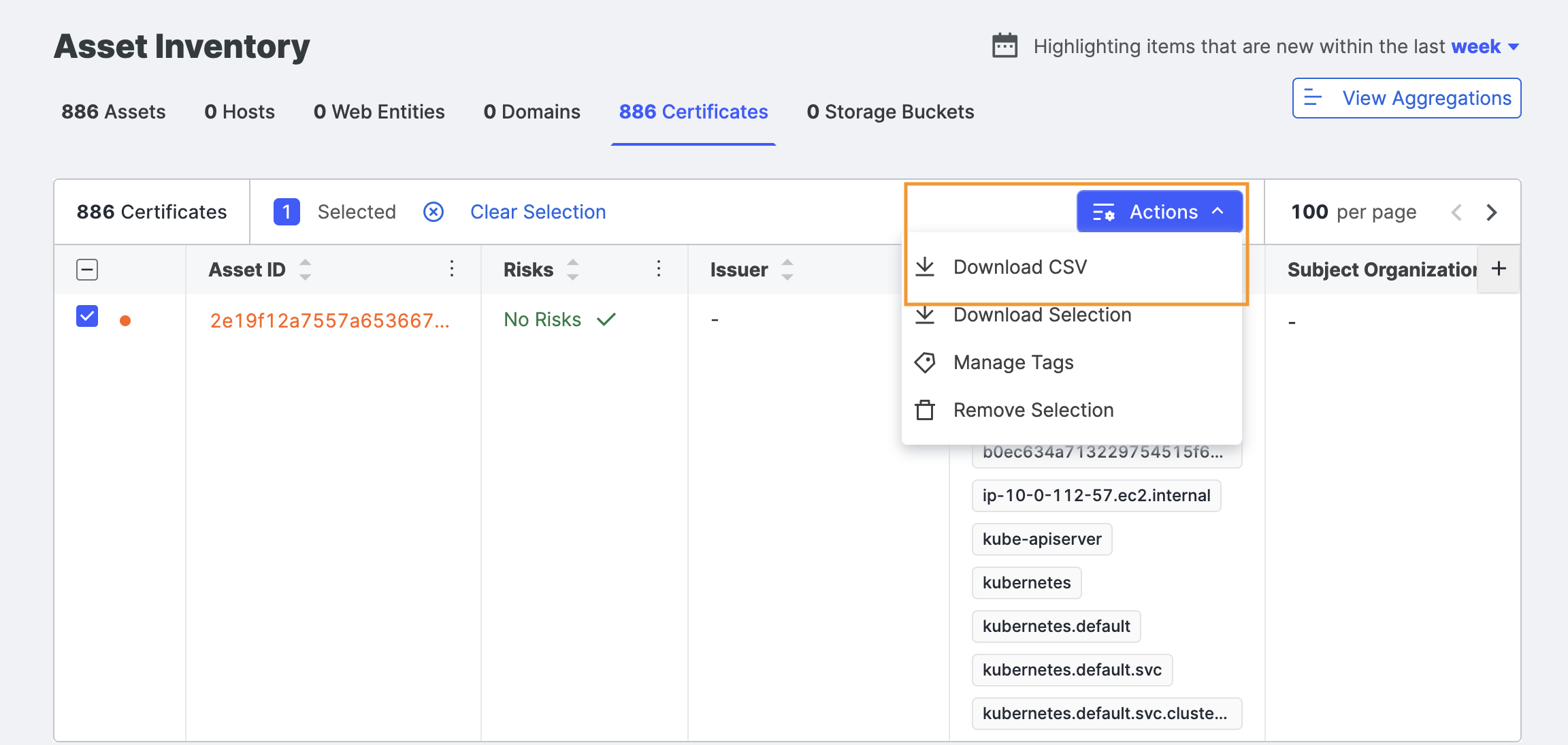
Certificate details
Click the Asset ID to see a certificate detail page with additional information. The page's primary title is the certificate’s common name, and the secondary title is the SHA-256 fingerprint.
Manage Tags
Tags are labels you and your team create to apply to assets in your attack surface. Any tags applied to the certificate are shown underneath, and an option removes them.
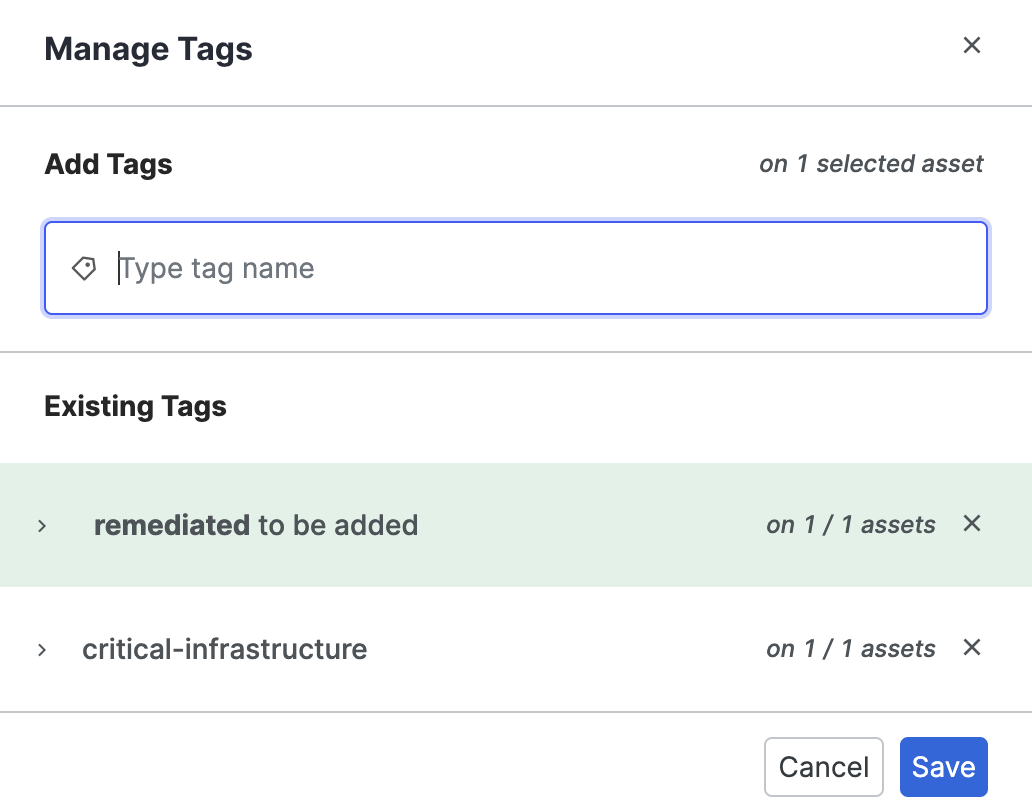
Click Manage Tags to add a new tag or edit a current one. In the dialog box, type the name of the new tag, or select from existing tags in the list.
Recent certificate activity
The first area on the page shows recent activity related to this certificate, taken from the logbook. Activity includes events such as adding the certificate to your organization and connecting it with your hosts.
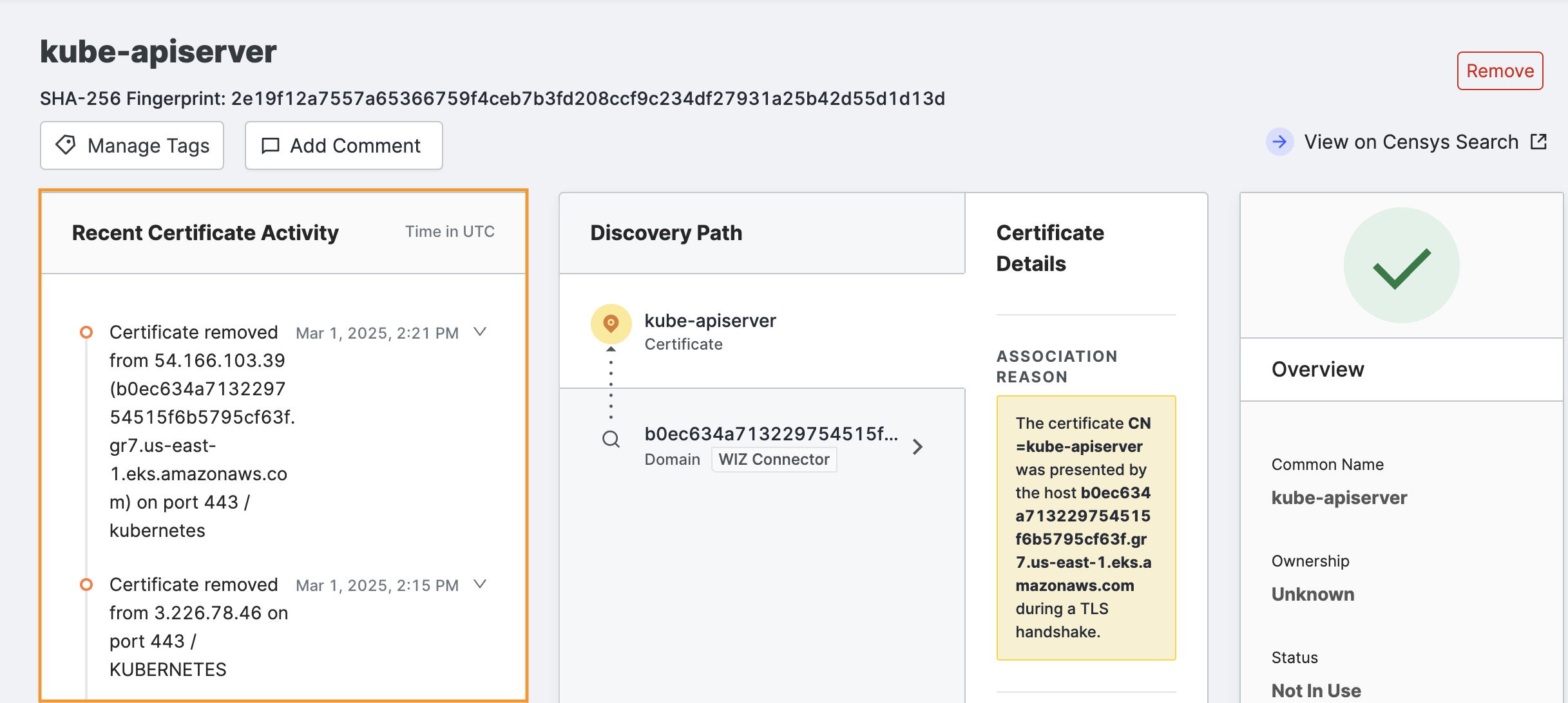
Click View All to see all events related to this certificate after Censys added it to your organization.
If you want to filter the events further, click Go to the Logbook where you can access those refinement options where those refinement options are available.
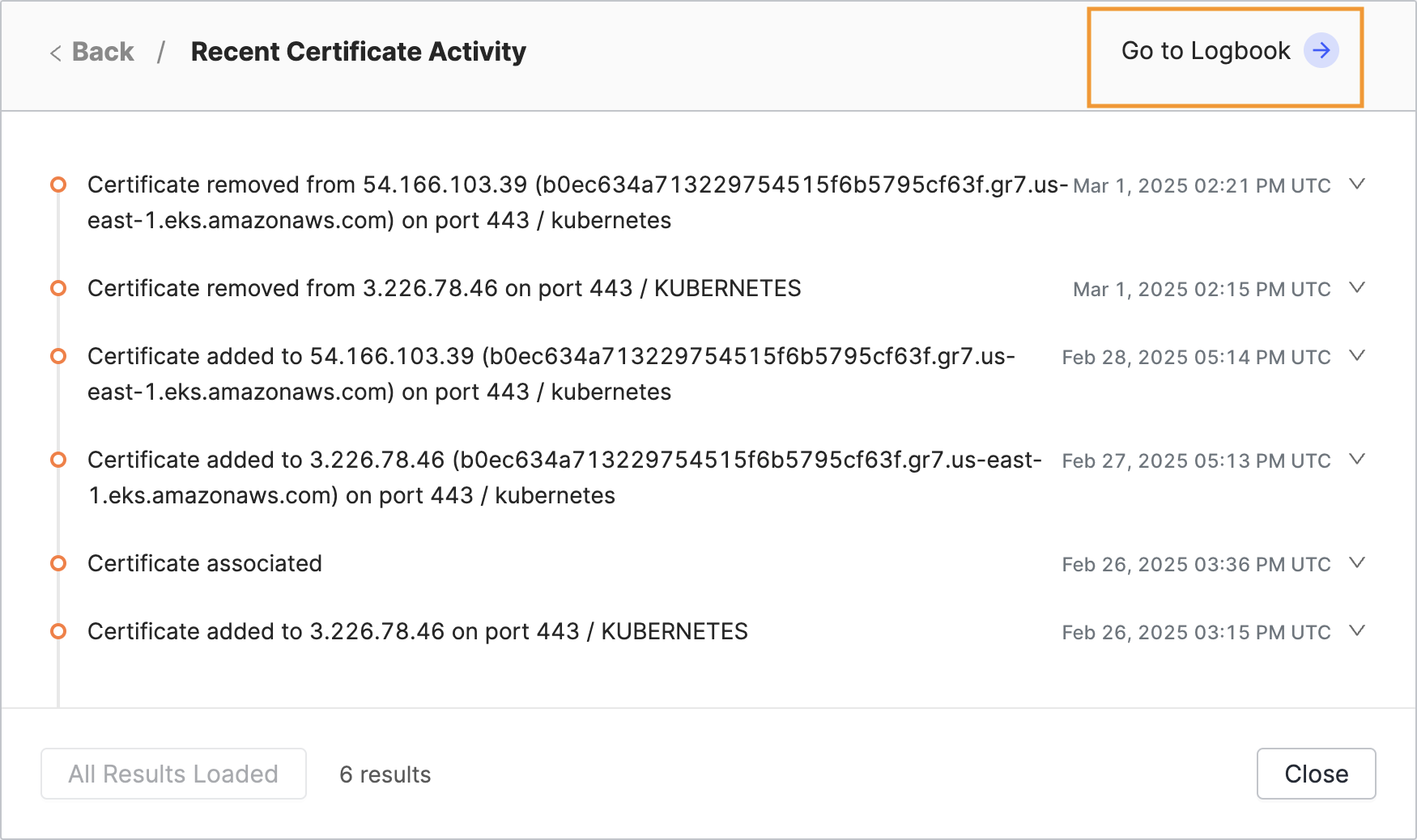
The Logbook page shows the SHA-256 fingerprint filter already set for the certificate.
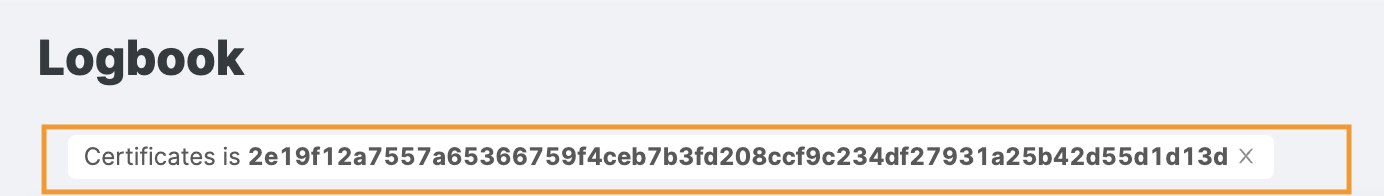
Discovery path
The next area shows a list of assets whose connections to this certificate were used to determine with confidence that they belong to your organization.
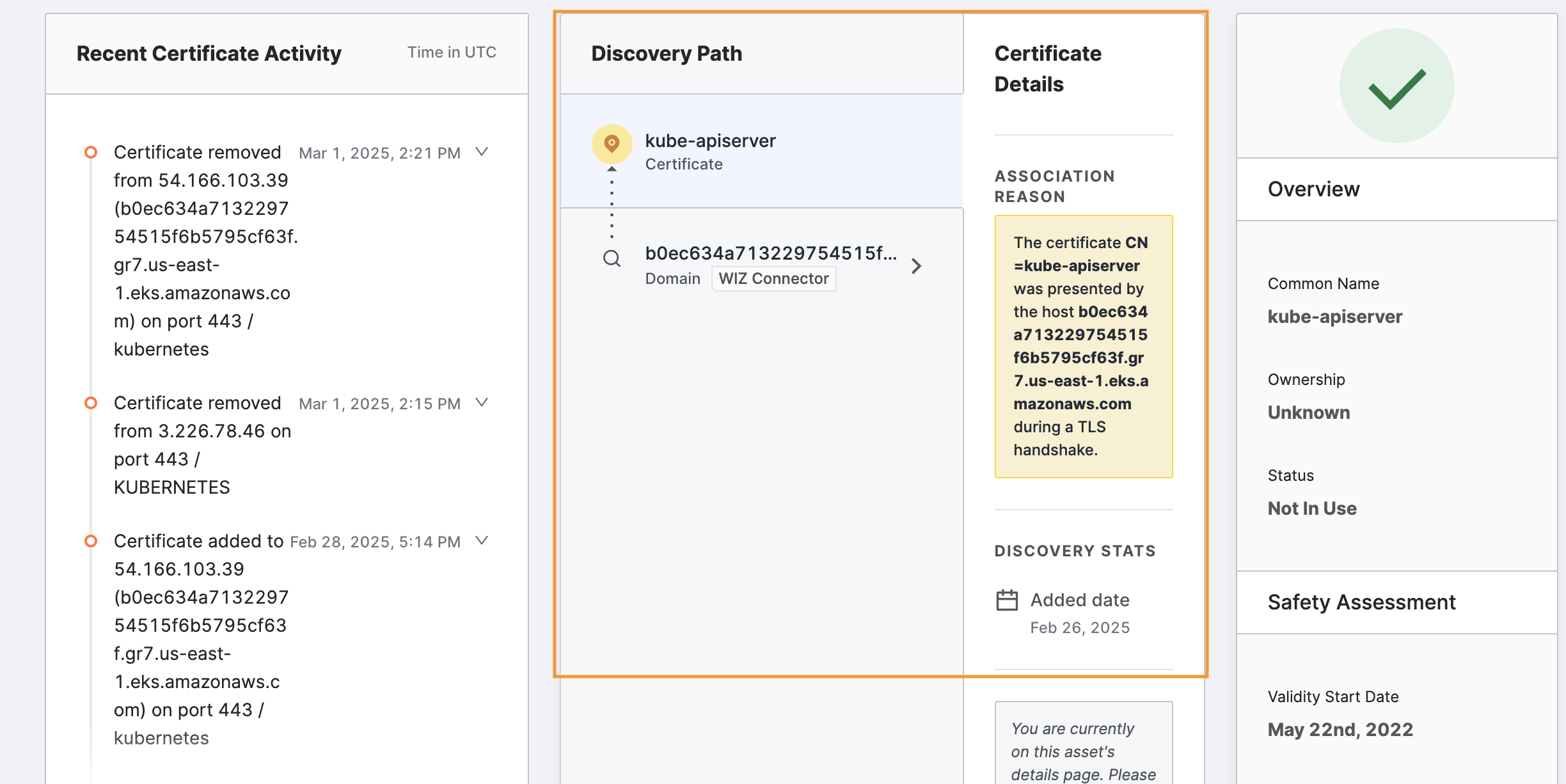
After investigating, if you decide that you do not want Censys Attack Surface Management to track this certificate for you, click Remove at the top right of the page.
This action removes the asset and adds it to an excluded asset list so that it will not reappear in subsequent Censys Attack Surface Management updates.
Overview
The Overview area on the far right of the page provides the most important certificate identification information and is a visual indicator of any problems with the cert.
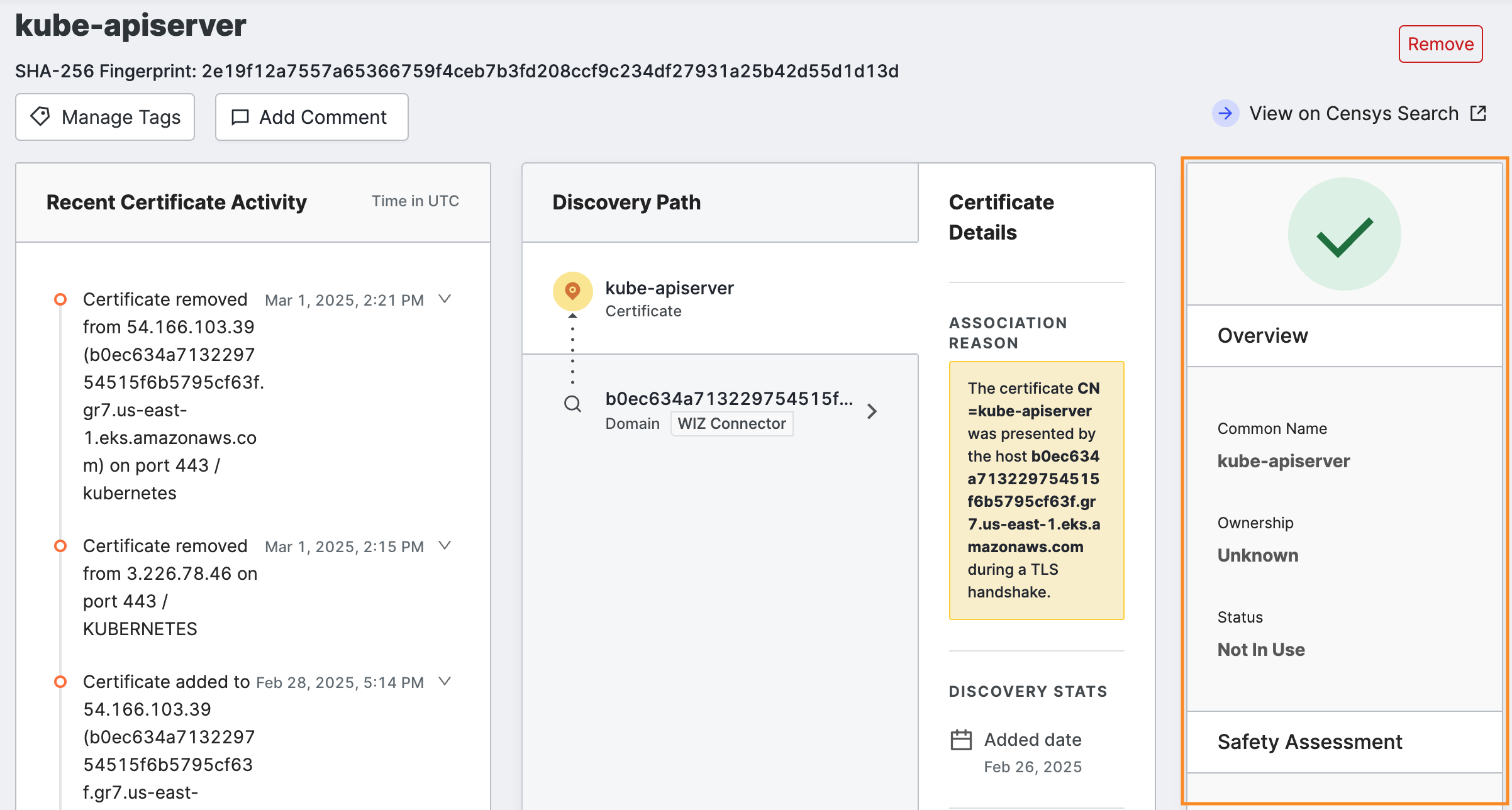
Information in this section includes:
- Common Name: The nominal fully qualified domain name of the certificate.
- Ownership: A categorization providing a Censys interpretation of whether this cert is associated to you (Owned) or not (Unknown).
- Status: Whether or not the certificate is currently in use on a host.
Safety assessment
The lower area on the right provides a report on the factors that determine whether there are any risks associated with using this certificate, as indicated by the icon at the top of the panel.
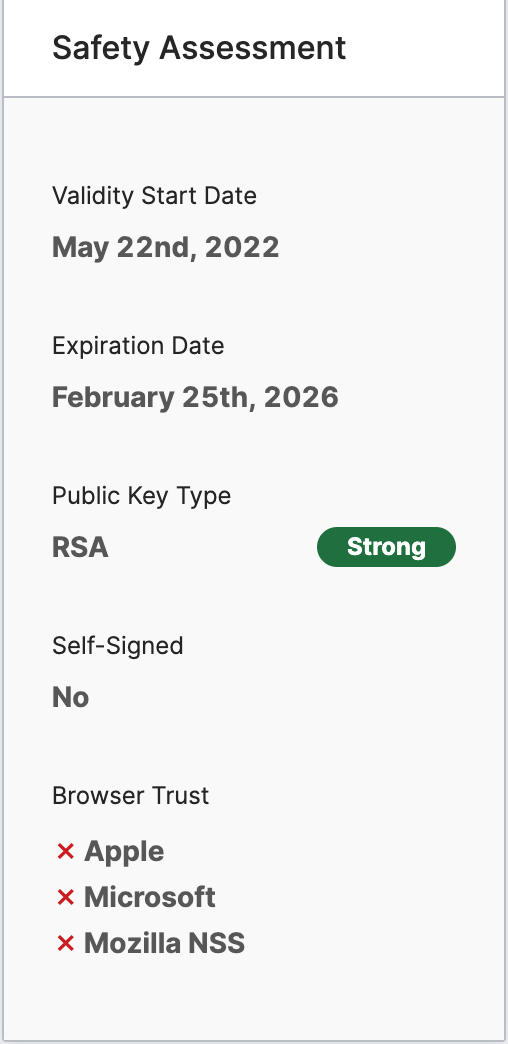
- Validity Start Date: The date on which the certificate can be used to verify the identity of the service(s) for which it has been issued.
- Public Key Type: The type of encryption algorithm used for the certificate’s public key.
- Self-Signed: Whether the issuer is the same as the subject.
- Browser Trust: Whether each of the four major browser-owning companies (Apple, Microsoft, Google, Mozilla NSS) endorse the chain of trust used by this certificate.
Certificate Information
This area provides detailed information from within the certificate, as well as information about its connections to other assets in your attack surface.
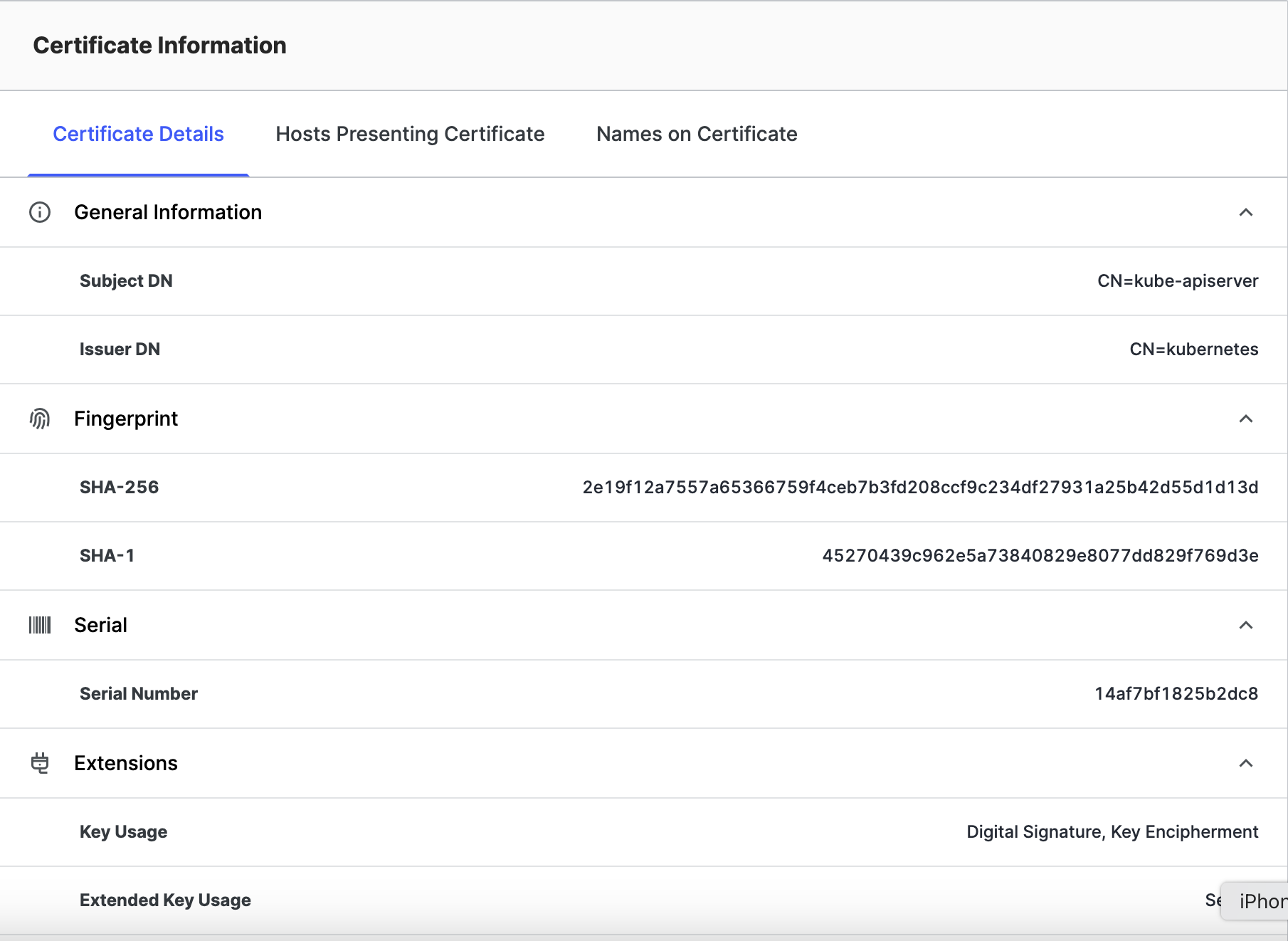
Certificate Details
- General Information
- Subject DN: Information about the identities that the certificate is valid for consisting of a number of key-value pairs called Relative Distinguished Names (RDNs). Common RDNs found in this field:
- C: Country Name
- CN: Common Name
- L: Locality
- O: Organization
- OU: Organizational Unit
- S: State Or Province Name
- Issuer DN: Information about the identity of the certificate issuer in key-value pairs called Relative Distinguished Names (RDNs). See above for common attributes.
- Subject DN: Information about the identities that the certificate is valid for consisting of a number of key-value pairs called Relative Distinguished Names (RDNs). Common RDNs found in this field:
- Fingerprint
- SHA-256: A hash of a body resulting in a unique identifier represented as a 64-digit hexadecimal string.
- SHA-1: A hash of a body resulting in an identifier represented as a 40-digit hexadecimal string.
- Serial
- Serial Number: A certificate identifier unique to the certificate issuer. Used for indexing revocation lists.
- Extensions
- Key Usage: The purpose(s) for which the public key may be used. Common Key Usage Purposes:
- Digital Signature
- Key Encipherment
- Extended Key Usage: Other purpose(s) for which the public key may be used, in addition to or in place of the basic purposes already indicated in the key usage extension. Common Extended Key Usage Purposes:
- Server Authentication
- Client Authentication
- Any
- Key Usage: The purpose(s) for which the public key may be used. Common Key Usage Purposes:
- Signature
- Signature Algorithm: The encryption algorithm for signing certificates with the algorithm OID in parentheses.
- Certificate Visibility:
- Added to Censys: This section lists any Certificate Transparency Logs that the cert has been entered in, with the date that they were added.
- Last Updated: This metadata field shows the last time Censys updated information about this certificate, not including its presentation by a host during TLS handshakes.
Hosts Presenting Certificate
This list of IP addresses is hosts that are presenting this certificate during a TLS handshake.
Names on Certificates
This list of names is taken from the CN (Common Name) and Subject Alternative Names (SAN) fields in the certificate and indicates the named services that this certificate can be used to verify.
Updated 10 months ago
