Platform JARM Fingerprints and Context Hashes
JARM is a method for fingerprinting TLS configurations on hosts to help identify TLS-enabled services. In the Censys Platform datasets, JARM fingerprints and other useful data fields are available in the *.jarm object for host services and web properties.
In addition to JARM fingerprints, the Platform datasets contain other context fingerprints and hashes using JA3 and JA4. This data is contained in objects and fields like *.tls.ja3s, *.tls.ja4s, cert.parsed.ja4x, and host.services.ja4tscan. Reference the data definitions page for a comprehensive list.
JARM fingerprints and context hashes are available to organizations with access to the Threat Hunting module as well as some Enterprise organizations that transitioned from Legacy Search to the Platform.
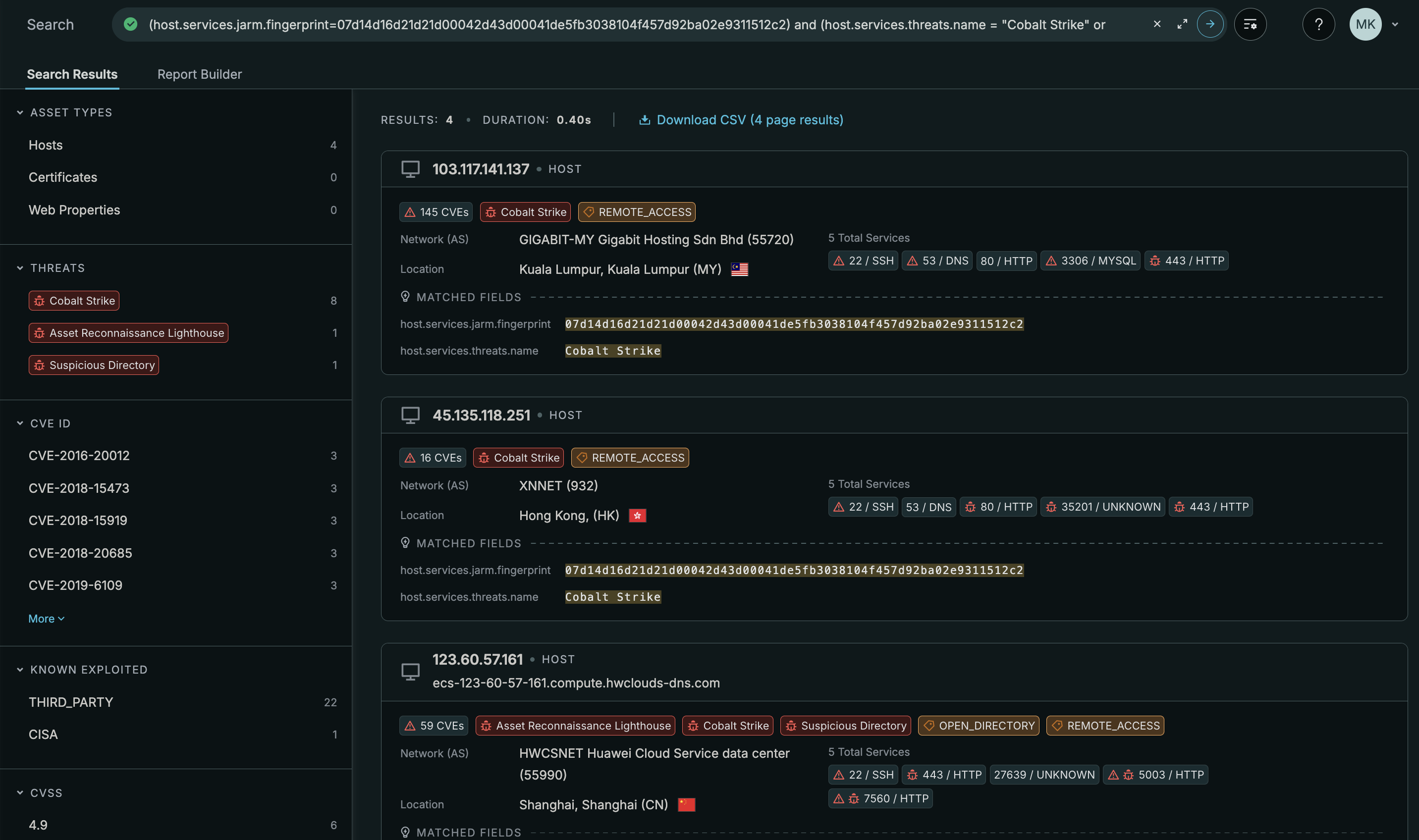
Example search results for a query that show four hosts running Cobalt Strike using the same JARM fingerprint.
Use cases for JARM and other context hashes
Threat hunters can use JARM to search for C2 infrastructure associated with malicious actors that use a specially crafted TLS configuration. JARM, JA3, and JA4 fingerprints are default pivot fields used with CensEye.
Attack surface managers can use JARM to identify anomalies in TLS configurations in their organization’s network and verify upgrades in TLS configurations.
JARM fingerprint components
The 62-byte JARM fingerprint is a concatenation of two fingerprints.
- First 30 bytes: The output of a hybrid fuzzy hash of the service's TLS version and cryptographic cipher usage.
- Second 32 bytes: A SHA-256 digest of the service's TLS extension usage.
Searchable JARM fields
The Platform provides several JARM-related fields for querying at the root level of a host service or web property object.
Use *.jarm.fingerprint to search with a full 62-byte JARM fingerprint, or use one of the two-component fingerprints to search with the first 30 bytes or second 32 bytes.
Use the *.jarm.observed_at field to restrict your searches to fingerprints obtained within the time frame you feel is fresh enough. The maximum age for JARM fingerprints is 15 days.
The table below highlights some useful JARM fields and their descriptions.
| Field | Type | Description |
|---|---|---|
*.jarm.fingerprint | Text | The 62-byte JARM fingerprint of the service. |
*.jarm.cipher_and_version_fingerprint | Text | The first 30 bytes of the JARM fingerprint, which encodes the service’s TLS version and cipher suite configuration. |
*.jarm.tls_extensions_sha256 | Text | The second 32 bytes of the JARM fingerprint is a digest of the service’s TLS extension usage. |
*.jarm.observed_at | Text | The RFC 3339-formatted timestamp indicates when Censys fingerprinted the service. |
Example queries
The following queries provide some examples of how you can use context hash information in queries, from searching for specific fingerprints to finding hosts with specific characteristics based on their JA4T fingerprint.
Query description | Query syntax |
|---|---|
Web properties with a specific JARM fingerprint | |
Hosts with services with a specific JA4S fingerprint | |
Hosts with a very small MSS | |
Hosts that have more than 16 TCP options set | |
Hosts with window sizes between 51 and 100 | |
Censys implementation of JARM
Creating a full JARM fingerprint requires ten separate connections to a TLS-encrypted service.
Censys strives to be a good citizen of the Internet while maintaining the highest quality and accuracy in the host dataset. Censys is careful to collect TLS data without negatively impacting servers worldwide.
Considering this, Censys does not attempt JARM fingerprints of any services on "super hosts" (for example, hosts with more than 99 services).
If a JARM fingerprint is older than 15 days, it is removed from the service data until it can be respectfully re-fingerprinted. Likewise, if Censys detects a change in a service's name—its primary identifier—the JARM fingerprint is also removed, as the likelihood of an identical JARM fingerprint on a new service is very low.
Updated 15 days ago
