Open Directory Data and Threats
The Threat Hunting module in the Censys Platform provides contextual metadata about assets with open directories. This information can be explored in an intuitive interactive UI, raw data in the Platform web console, and retrieved via API. Open directories that meet certain criteria are tagged as Suspicious Directory threats.
The Suspicious Directory threat highlights assets that contain web-accessible directories containing security tools, penetration testing utilities, webshells, or other potentially malicious files. These directories often expose sensitive tools and scripts that could be used for unauthorized access or malicious activities. Use this threat information to find hosts and web services with suspicious files before they are leveraged in attacks.
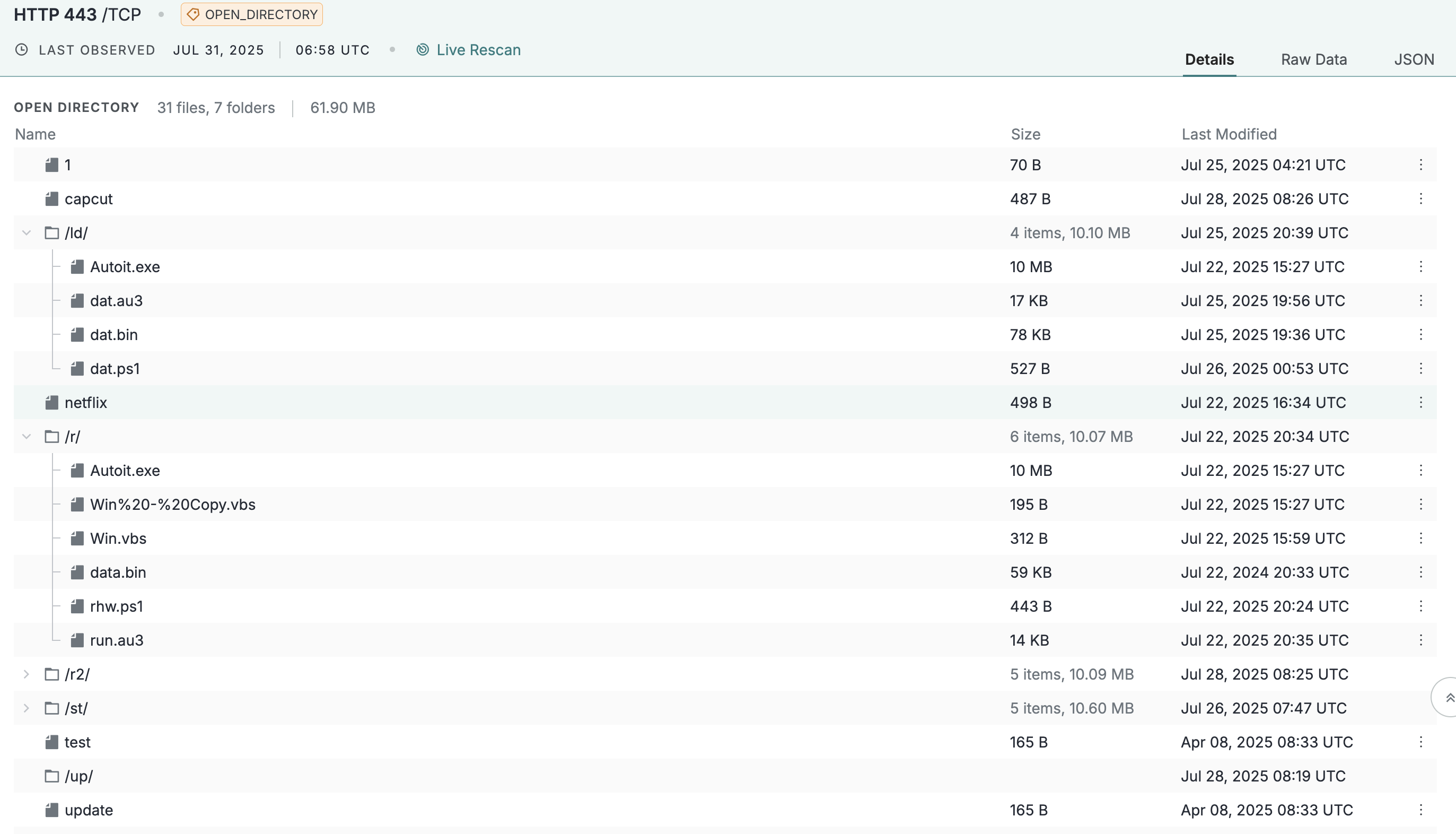
An example open directory on a host service in the Censys Platform console.
The OPEN_DIRECTORY data label is available to all Platform users. However, open directory metadata, the open directory UI, and the Suspicious Directory threat are only available to users with access to the Threat Hunting module.
Open directory metadata
The following data objects and fields are available for open directories scanned by Censys. This information is available for all directories scanned by Censys, not just ones that are marked suspicious.
| Data field | Description |
|---|---|
open_directory | The data object containing open directory information. |
open_directory.files | The data object containing nested information for each file or subdirectory detected in a directory. |
open_directory.files.path | The path at which a file or subdirectory is located. |
open_directory.files.size | The size of the file in bytes. This data may not be available for all files. |
open_directory.files.type | The type of resource detected. Can be directory or file. |
open_directory.files.extension | The file extension, such as .exe, .php., .json,.png, and so on. |
open_directory.files.last_modified | The time at which the file or subdirectory was last modified. |
open_directory.files.name | The name of the file or subdirectory. |
open_directory.recursive | Whether directories in the top level listing are also open directory listings. |
How to use open directory data
The scan data obtained from open directories lets you identify, monitor, and fingerprint resources across the global internet. For example, if you're tracking suspicious Python files you can execute a search to find open directories with .py file extensions and run a report broken down by file name to investigate specific file names.
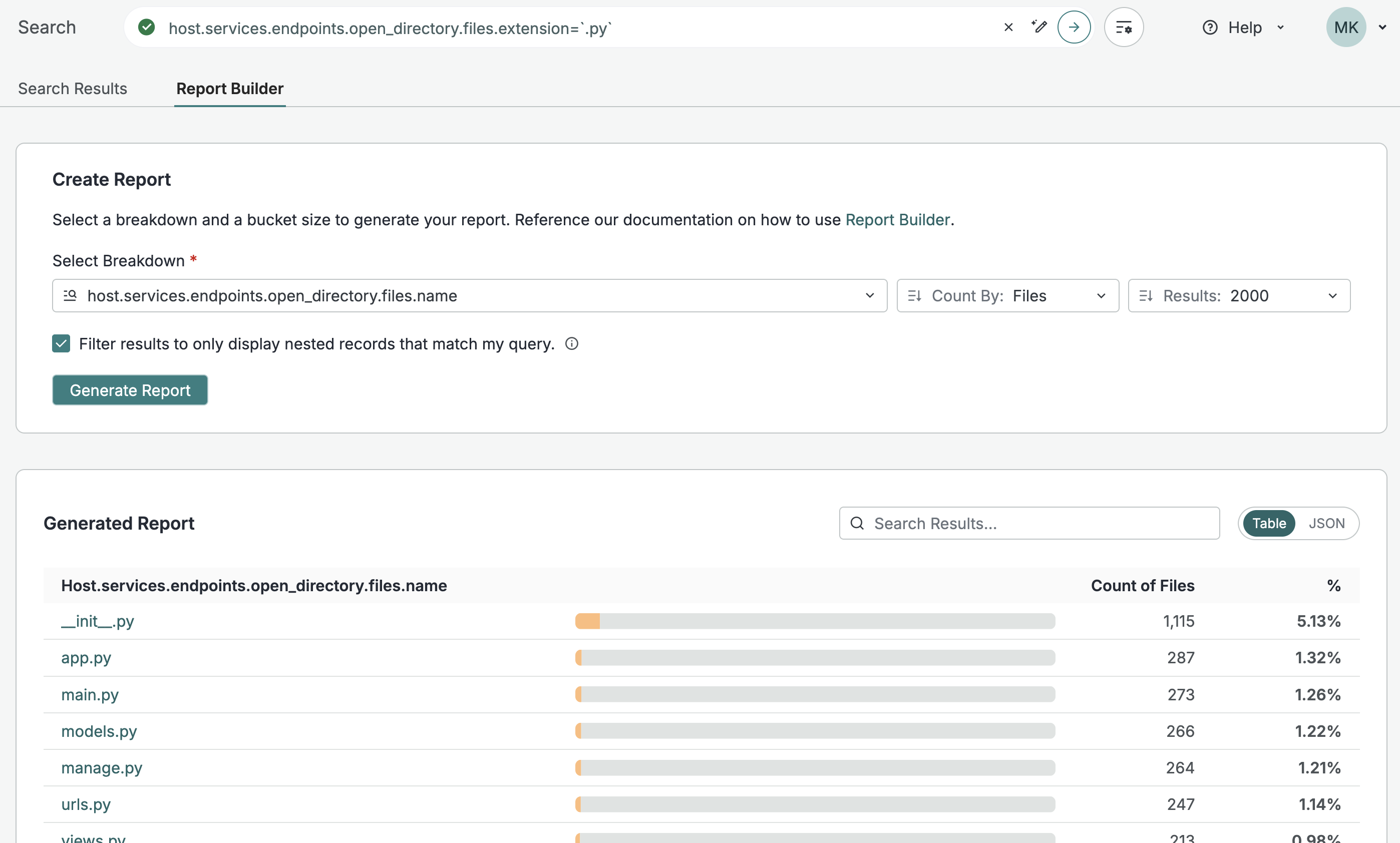
You can also use the following example queries that leverage open directory data as a starting point for your research.
Query description and link | Query syntax |
|---|---|
| Open directories with PowerShell files in the contents |
|
| Open directories with files that reference "leaked" |
|
| Open directories with hidden files | |
| Suspicious open directories with files that were modified in the past 6 hours |
|
Directory visual explorer
The open directory visual explorer provides an easy-to-parse interactive representation of an open directory's structure and files. Use it to quickly understand directory information at a glance, including file names, sizes, last modified dates, and directory structure.
Click the three-dot menu next to a file name to open a pivot menu to search for files with the same name, name and size, or extension.
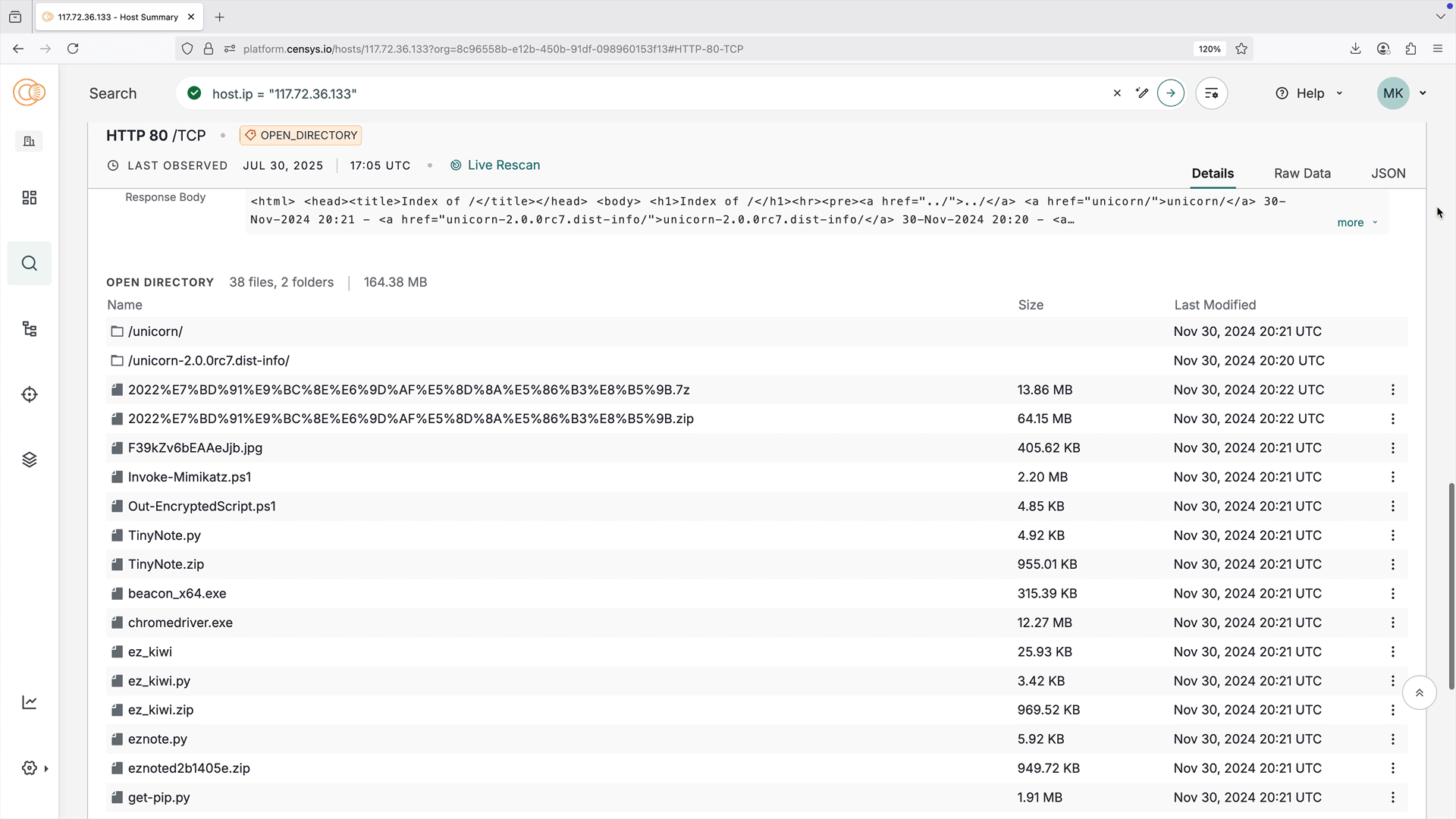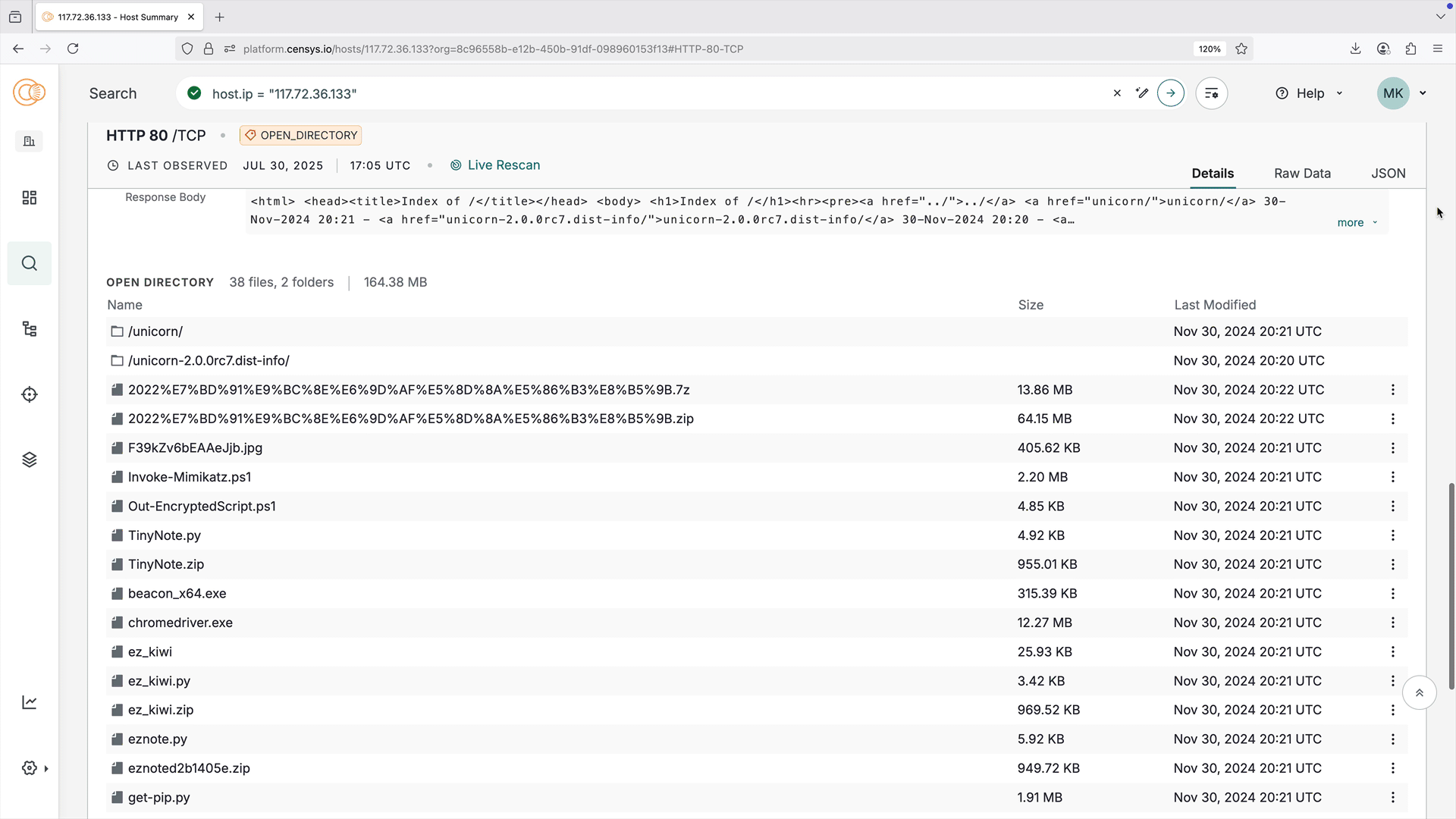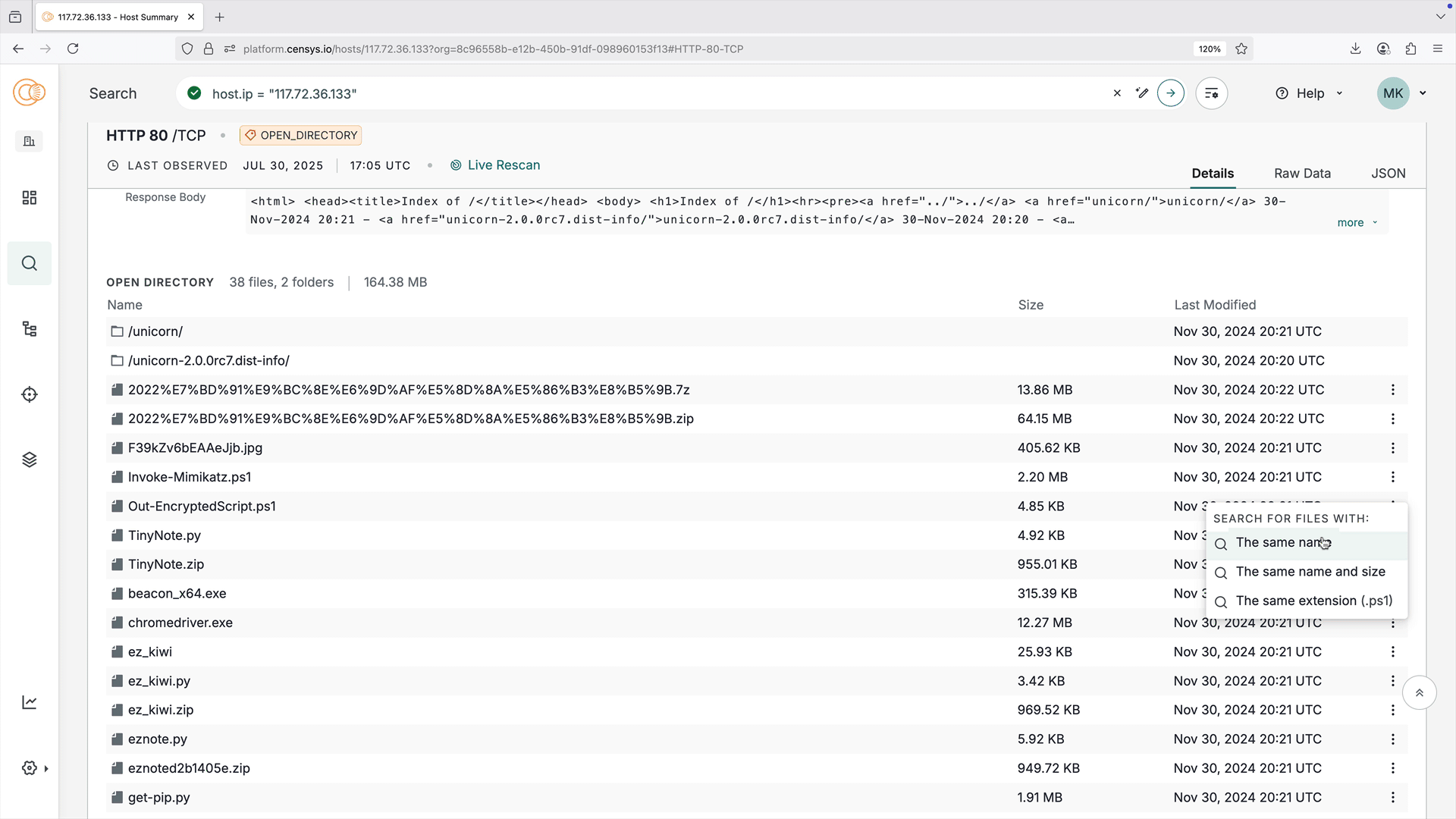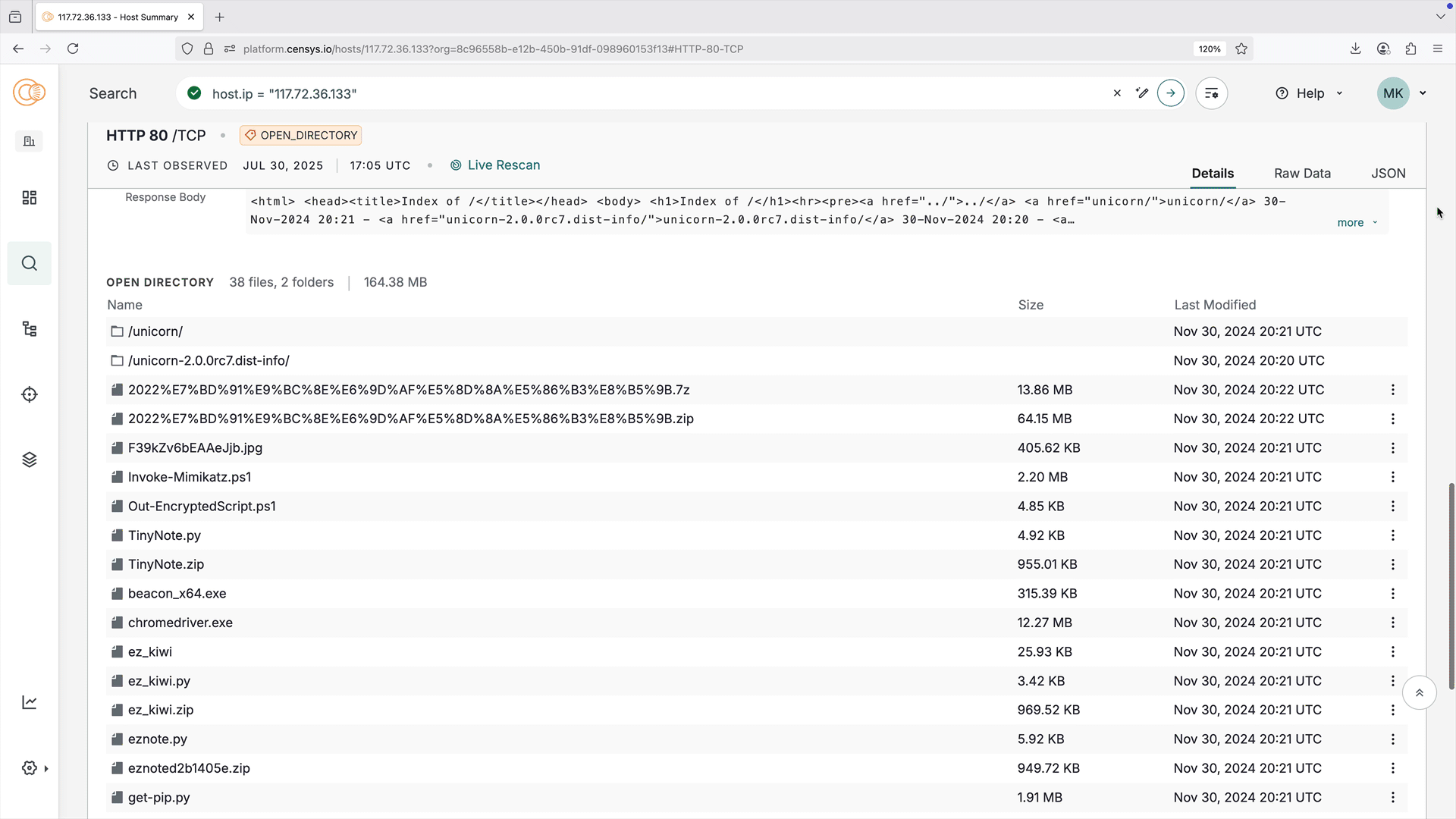
The visual explorer is shown on host service and web property endpoint cards that an open directory has been found on. All data shown in the visual explorer is available in the raw data for the open directory service or endpoint.
Additional open directory data information
Open directory data is subject to the following limitations, which are subject to change:
- A maximum of 100 files or subdirectories are available for each directory.
- A maximum depth of 10 subdirectories is available for each directory.
Updated about 1 month ago
