Transition Guide for Enterprise Customers
The purpose of this document is to assist current Censys Legacy Search Enterprise customers with their transition to a Core or Enterprise plan on the Censys Platform.
Migration timeline
The Censys team will reach out to you about your migration timeline.
Key migration tasks
1. Use the Quick Start Guide
You can familiarize yourself with the Platform using a Free account. The Quick Start Guide can help you get up and running with the Platform.
2. Update SAML authentication
If you use SAML SSO to handle authentication to Legacy Search, you need to set it up again for use with the Platform. Documentation is available here and the Censys team will help you handle the configuration. For additional assistance, reach out to [email protected].
3. Convert your queries to Censys Query Language
The Platform uses a new domain-specific language, Censys Query Language (CenQL). You can quickly convert your Legacy Search queries to the new syntax using the built-in Query Converter in the Platform web console or the query converter API endpoint.
In the Platform web console, the query validator next to the search bar informs you about errors in your query syntax, helping you quickly build valid and focused queries.
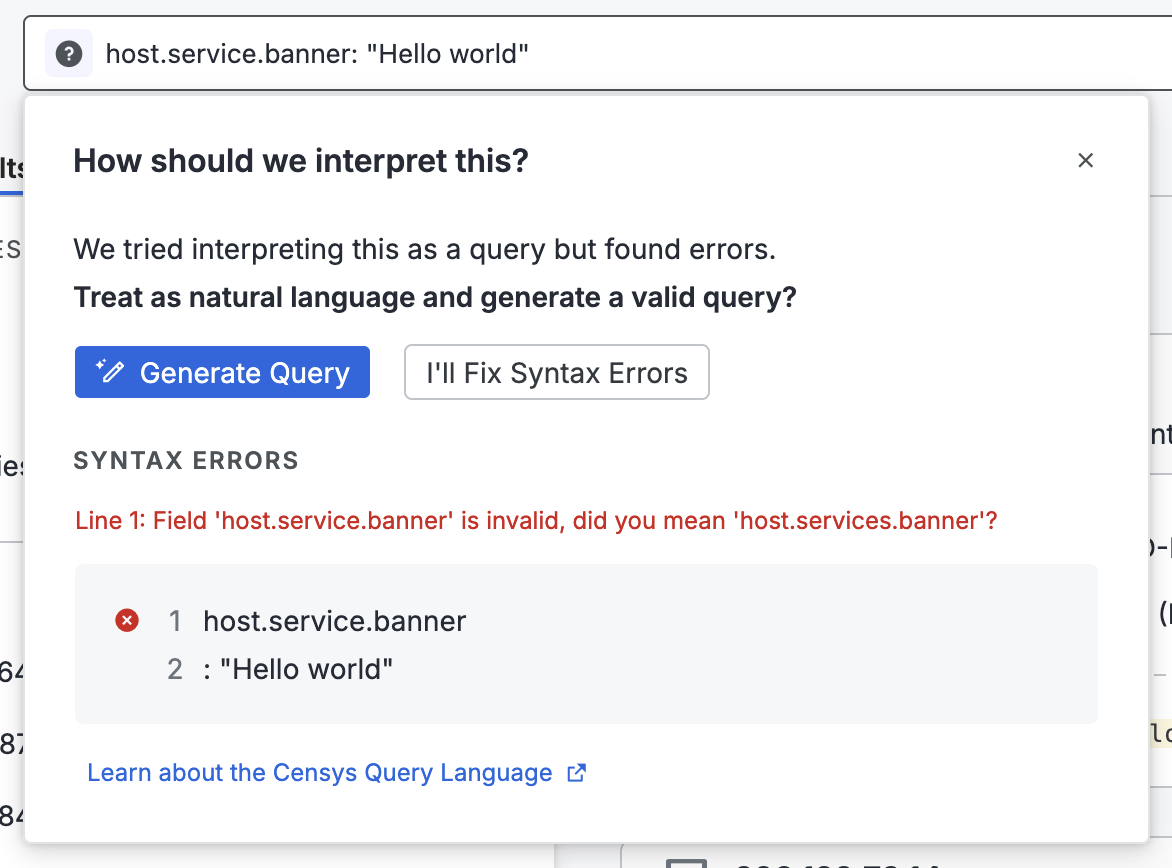
The Censys team can also help you convert queries into CenQL. Send a message to [email protected] for assistance with query conversion.
4. Transition to Platform APIs and SDKs
The Platform features new API endpoints. You can see complete details about API syntax, parameters, and test the new APIs in the API Reference Guide.
To ensure a smooth API transition, note the following:
- You must use the new base URL:
https://api.platform.censys.io/v3/- Global data endpoints use
https://api.platform.censys.io/v3/global/ - Collections endpoints use
https://api.platform.censys.io/v3/collections/
- Global data endpoints use
- Your API requests must use a valid Personal Access Token and bearer token (organization ID). Learn how to generate a Personal Access Token and obtain your organization ID.
- Users must have the API Access role in order to use the API.
The following Platform SDKs are available. Note that these are distinct from the Legacy Search SDKs:
New features in the Platform
The Platform provides a number of new capabilities and enhancements.
Unlimited UI actions for Core and Enterprise plans
Customers who transition to the Core or Enterprise plan can perform an unlimited number of queries, asset lookups, and actions in the Platform web UI.
Censys Credits replace queries for API usage
API usage in the Platform is measured using Censys Credits instead of queries. There are three main differences between the new Platform API access model and the previous licensing models used for Legacy Search.
- The credit-based licensing model allows customers to purchase and consume credits for various Platform API features, ensuring scalability.
- As your needs grow, you can easily purchase additional credits.
- Purchased credits are typically valid for 12 months.
All plans will have a variable number of credits included in their package and you can purchase additional credits at any time. For Core and Enterprise customers, 1 credit is equivalent to 1 query in Legacy Search. To learn more, reference the documentation on Censys Credits.
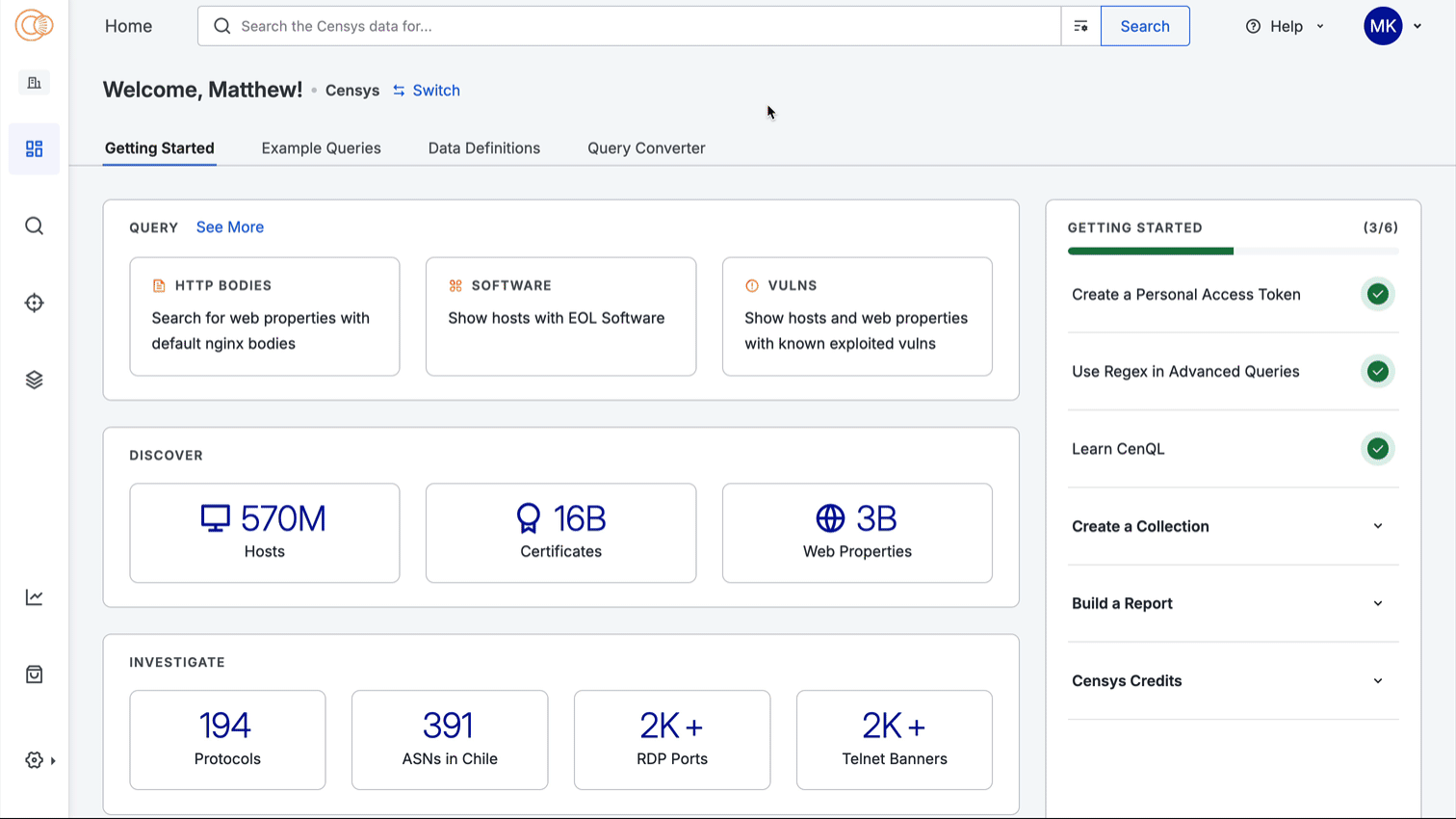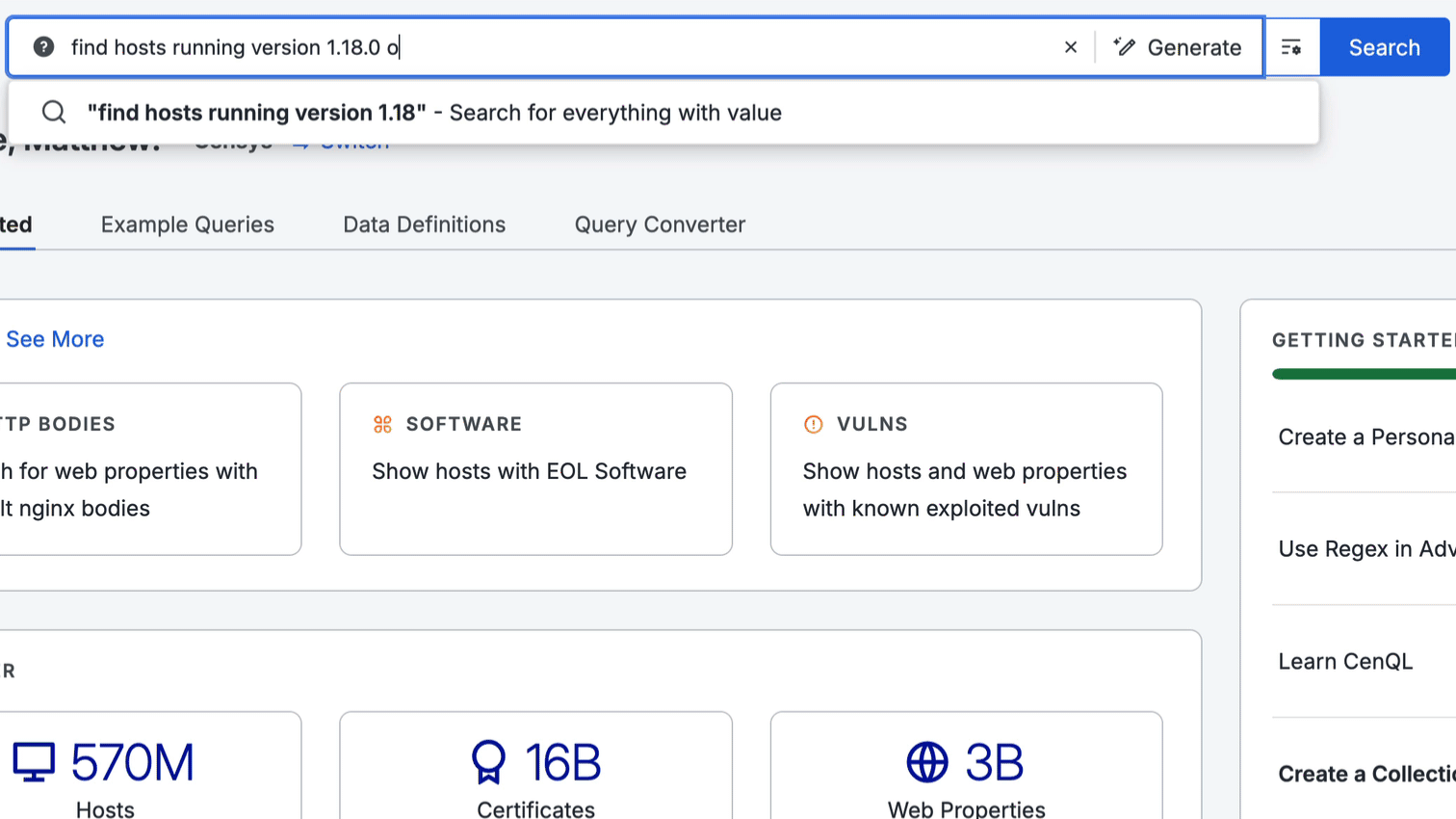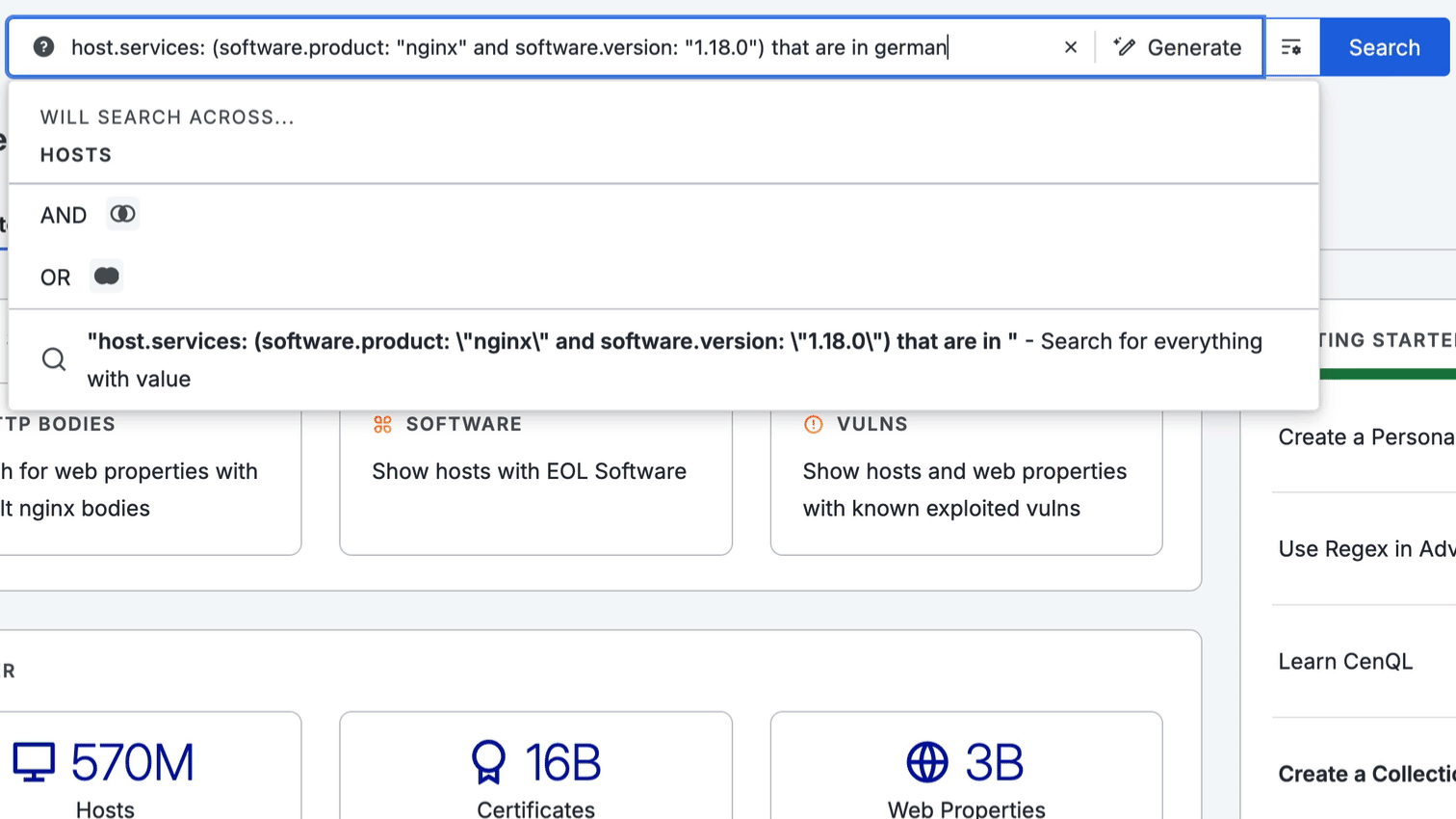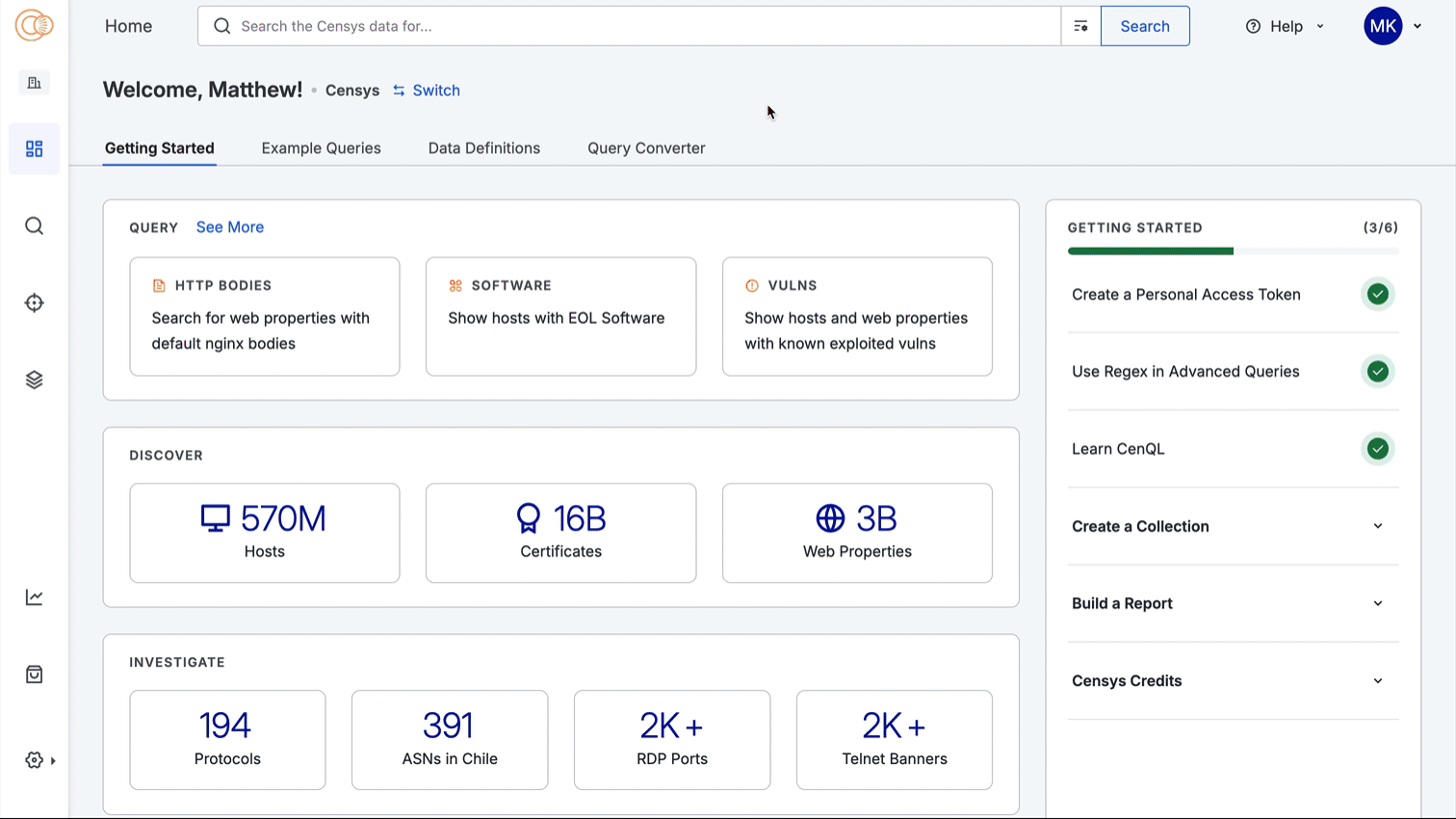
Censys Query Assistant AI tool
You can use the Censys Query Assistant in the search bar to build queries using natural language input. For example, input “find hosts running version 1.18.0 of nginx” and click the Generate button to output the CenQL query host.services: (software.product: "nginx" and software.version: "1.18.0"). You can also add natural language input to existing queries using this workflow.
Dataset differences
Censys introduced a new data model for describing hosts, certificates, and web properties on the internet in the Platform. This new data model is different from the one available in Legacy Search and features many improvements and additions. Queries and workflows that were used in Legacy Search need to be modified to return similar results in the Censys Platform.
Some of the most prominent changes include:
- A new domain-specific language and syntax, Censys Query Language (CenQL), for querying the Censys Platform datasets, as described above.
- Virtual hosts are now represented by web properties (see below) to describe and organize data for internet assets that respond to name-based scans.
- Additional context about web asset software, hardware, operating system, threats, and more to provide actionable information on what exactly mapped services and devices are, how they are configured, whether they are vulnerable, whether they are malicious, and where they live.
host,cert, orwebhave been prepended to all parsed data fields. These values indicate whether the field is present on a host, certificate, or web property asset.- Many values related to software or hardware that were previously present in the
labelfield in Legacy Search can now be found instead insoftware,software.components,hardware, andhardware.componentsdata for hosts and web properties.
To learn more about schema changes, see Dataset Differences: Censys Platform vs. Legacy Search.
New web property dataset
The Legacy Search dataset includes hosts and virtual hosts. In Legacy Search, hosts are identified by an IP address. Virtual hosts are identified by a name and an IP address.
Virtual hosts are not present in the Platform dataset. Instead, internet assets that respond to hostname-based scans are classified as web properties.
In the Platform, web properties are identified by a hostname and a port. Hostnames can be name-based records (such as app.censys.io) or IP-based records (such as 104.18.10.85). Example names of web property records include the following:
app.censys.io: 443104.18.10.85: 8880
Web properties provide a more accurate, up-to-date, and comprehensive view of name-based assets than virtual hosts. Classifying and presenting web assets as web properties enables Censys data to:
- Better identify and showcase name-based assets, linking domain names and related services directly to their underlying infrastructure.
- Support data from multiple HTTP endpoints.
- Make searching for name-based assets feel like using a web browser.
- Dramatically improve the freshness of web data. Web properties are refreshed approximately every three weeks.
- Provide deeper visibility into application scans and the true footprint of internet assets, enhancing precision in asset discovery and threat monitoring.
Learn more about web properties.
Monitor infrastructure with Collections
Track changes to infrastructure in near-real-time using Collections. Collections monitor the results of a saved query and can send alerts to downstream applications via webhook. This built-in tracking and alerting functionality saves you time that would otherwise be spent coding custom tools.
Data access entitlements
Platform Enterprise users have access to full protocol data information and advanced internet visibility provided by deep application scanners. This allows you to search and view protocols, services, web applications, and view at least one month of host history.
Enterprise search results include all CPE-based fields and provide access to unlimited paginated results. Raw and JSON data can be viewed and downloaded.
A complete list of all data fields available is provided on the Data Definitions page in the Platform web console.
Threat-related data, including data that was previously associated with the C2 label in Legacy Search datasets, is accessible to Enterprise organizations that have purchased the Threat Hunting module. More information on the Threat Hunting module is provided below.
Industrial control system (ICS) data will be available to Enterprise customers at an additional cost.
Tags and comments
Tags and comments for assets are not currently present in the Platform. They are planned for a future release.
Threat Hunting module
The Censys Platform introduces the new Threat Hunting module designed to help security teams proactively detect, investigate, and respond to adversary infrastructure.
New features such as Live Discovery, CensEye, enriched threat context, and certificate history provide deeper visibility and investigative power. Integrated fingerprint and endpoint scanners enhance detection of command-and-control activity, while improvements to the results view and reporting tools make threat data more actionable. Together, these capabilities enable faster pivots, smarter correlations, and more effective threat response—all within a single, unified platform experience.
The Threat Hunting module is available to Enterprise customers at an additional cost.
Threat Context: Enriched threat object intelligence
Threat Context surfaces enriched information about command-and-control (C2) infrastructure, including TTPs, adversary profiles, and related threat indicators. Users with access to the Threat Hunting module can search and pivot across all threat data within the Platform, giving security teams more insight to assess and prioritize threats.
CensEye: Infrastructure pattern detection
CensEye helps analysts discover similar hosts and web properties based on key:value patterns. This allows threat hunters to pivot more effectively from known indicators and expand adversary infrastructure mapping. CensEye results are embedded directly in host and web property pages, automatically ranked by frequency and relevance.
Certificate and host history: Infrastructure correlation over time
Users can now explore historical relationships between certificates, hosts, and web properties via a dedicated timeline view. This supports deeper investigation of long-running campaigns, infrastructure reuse, and certificate-sharing behaviors. This data is accessible both via the UI and through public APIs.
Live Rescan: Real-time infrastructure validation
The Live Rescan feature allows users to re-scan known services on a host to validate whether a threat still exists or if changes have occurred. This is critical for verifying remediation or detecting newly introduced malicious services. Built on the ArctorService, each rescan is timestamped to support timeline investigations and fast pivots. Rescans consume credits, are subject to per-asset rate limits, and leverage a dedicated queue to enable rapid execution.
Fingerprint and endpoint scanners: Active C2 detection
The platform now supports active scanning of HTTP endpoints to detect known or emerging C2 infrastructure using customizable CenQL predicates. Scans can be tuned with custom headers, parameters, and request bodies. The results feed into structured threat objects for further investigation, alerting, and detection workflows.
Improved results view: Actionable visual intelligence
The search results interface now includes threat-specific metadata, filters for threat types and open directory filenames, and visual chip icons for quick identification. A new information panel surfaces threat object details, helping teams assess risk and relevance at a glance without leaving the results page.
Explore View: Threat actor catalog
A new centralized "All Threats" view provides an interactive catalog of Censys-tracked threat actors, malware families, botnets, and C2 groups. Each card includes a short summary and links to related infrastructure. Users can query by region, IP range, or keyword to quickly surface relevant threats.
Updated 9 days ago
