Platform Certificate Dataset
Certificates are an important part of internet traffic encryption. They can verify the identities of the services that are communicating to each other. Censys collects certificates in a repository for searching and viewing.
The Censys certificate dataset is the most exhaustive collection of X.509 documents in existence. It consists of over 15 billion records and records are added on a daily basis.
In the Censys Platform, certificates are indexed and identified by their "fingerprint," which is the SHA-256 digest of the entire raw certificate. You can use this information to directly navigate to a certificate record in the Platform web interface. It is also recorded in the cert.fingerprint_sha256 field on certificate records.
Each Censys certificate record contains:
- Data parsed from the certificate using ZCrypto, an open-source, Go-based, cryptographic library.
- Trust information from major root stores such as Apple, Google Chrome, Microsoft, and Mozilla NSS.
- Submission information from Certificate Transparency (CT) logs.
- Lint results describing non-conformance to the X.509 standard using the ZLint library.
- Data about Censys collection and observation during scan.
And much more.
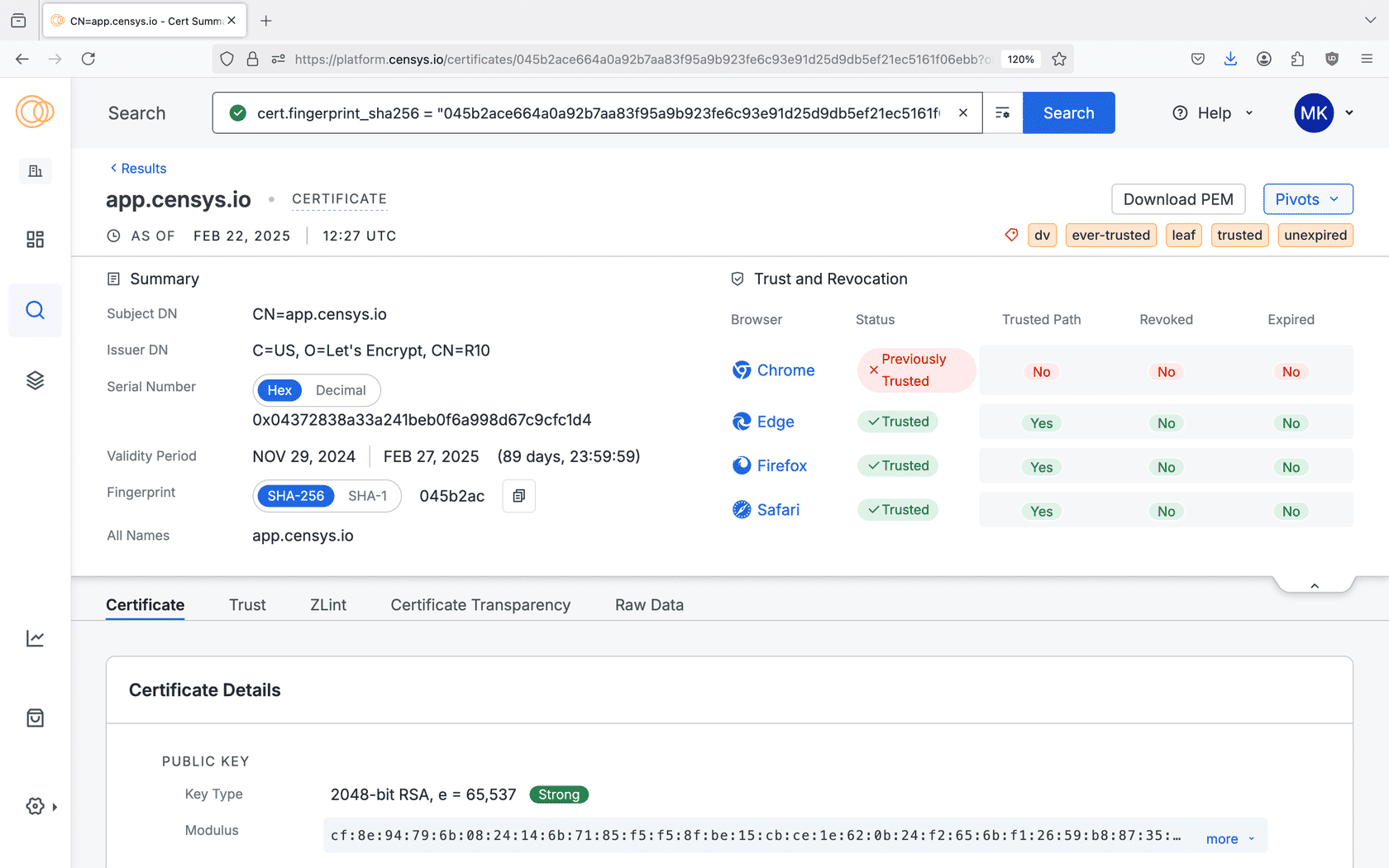
An example certificate record in the Censys Platform web interface.
Certificate collection
Certificates are collected using two methods:
- Syncing with a number of CT logs.
- A list of all CT logs monitored by Censys is available in the Platform web app.
- Observing a certificate presented as part of a TLS handshake during a Censys scan of the public internet over any protocol.
Certificate objects and fields
The contents of a certificate are immutable and cannot be changed after the certificate is generated.
Censys parses the contents of each certificate and provides them as searchable fields in an object called cert.parsed. These fields include, but are not limited to the following. A full list of certificate fields is available in the Platform web console.
- Issuer: Information about the certificate authority that issued the certificate.
- Subject: Information about the entity that was issued the certificate.
- Validity period: The dates from which and to which the certificate can be used.
- Subject alternate names: The additional names that may be used by a certificate.
- Signature algorithm: The algorithm used to sign the certificate.
- Signature value: Bit string containing the digital signature.
Other data about the certificate and the collection process also appear in a Censys certificate record, such as:
- Trust and validation: Information about the status of the certificate’s trust by modern web browsers.
- Certificate Transparency: Information about submissions to CT logs.
- ZLint: Whether the certificate’s attributes triggered any lints for non-conformance to the X.509 standard
- Seen in scan (
cert.ever_seen_in_scan): Whether the certificate has ever been seen during a Censys scan of the internet.- This is a one-way boolean--if true, it remains that way.
Certificate expiration and indexed fields
Certificates are converted to Lite Certificates in the Censys dataset upon expiration. Learn more about Lite Certificates here.
Example certificate record
The following is an example of a certificate record object obtained via the Platform API to show the general structure of these records.
{
"fingerprint_sha256": "ac626038ac117b26c07fe8d087286384748511c373fff248c48de46104e54fcb",
"fingerprint_sha1": "c2c0c7206b58c6f28c054714f01745c3da92e2f2",
"fingerprint_md5": "39d962add062dc8554e8fde0a39d7e20",
"tbs_fingerprint_sha256": "88fbd5f6c1150159d61f33505e25b5ef1e4f685af65bcf4318210a674cef7450",
"tbs_no_ct_fingerprint_sha256": "8d0bfacfd5cd5c027bb580933c13a17c3892098d0fbd5ddcf93f50e4b5a802b7",
"parsed": {
"version": 3,
"serial_number": "17542909292289844125069163059898343668",
"issuer_dn": "C=US, O=Google Trust Services, CN=WR2",
"issuer": {
"common_name": [
"WR2"
],
"country": [
"US"
],
"organization": [
"Google Trust Services"
]
},
"subject_dn": "CN=dns.google",
"subject": {
"common_name": [
"dns.google"
]
},
"subject_key_info": {
"key_algorithm": {
"name": "RSA",
"oid": "1.2.840.113549.1.1.1"
},
"rsa": {
"exponent": 65537,
"modulus": "e1af72ca77458ad7edf705c99d2647b678c467a9768e293d917d2cfdb26713349150a08bb1129bb3793aa5b08059be60dd92eeacd77e6178705a7f3275ace69d540fd67f3d0bdf43d020919d438adfe43655cbe45afe3754b095bdd082cf05ed6b0d81b54ca1a62c32dbb62e6d8651a6256de06a4d0596cd28f0a0da1c38be084643b5d240b8f9b68f582fdcd6219c187137357f1308d3f406d85caa4c0fd6169974077fc286f6126f81207e238cd39292d80ee17f00525951cd94a194efecb0aef60d97ee466547687c43a9c206bf21e6462e3de304cceca418fa1884342a3a6e2143d76191186b64a86e3127516a5eecd04def736910e4cba7c90884f79883",
"length": 2048
},
"fingerprint_sha256": "eff0a4c65367421fc2525f7d698727ecc5a5c973dde2d0d473e08e8f1688f03a"
},
"validity_period": {
"not_before": "2025-02-03T08:37:59Z",
"not_after": "2025-04-28T08:37:58Z",
"length_seconds": 7257599
},
"signature": {
"signature_algorithm": {
"name": "SHA256-RSA",
"oid": "1.2.840.113549.1.1.11"
},
"value": "26531ba7be65d999274daac60c8460e5855e99fbafa33ce819015cadede08d252a8d95e74252d6fc9e76144968f81ce2cb3eda9280ad5809b29f28aca691667f2403e59f671e62fc3efb3c83c961c93a8ca4dd0113e5679b9a3a6b9ec0b1d55d58ce1dd9d41809a03b6e5be043766a66b396087b7ce06b9cc14703b048f174a71256e5ffd6b9b7bd5582031e432758c655d6257151125f287e3600ae05fa63f5ed2299b9607c0c58342f0d5da3b673973f65f87e299e349c446806538f0524be7ee7b7b712055c34f6388817d1518c52cd2bcc0cf08644e9c2389f9e3e58eaf7b8b9058cc8e9d186245550fee5dfcc9c4f7f8556361d507b6aba29e1e58e0a99",
"valid": true
},
"extensions": {
"key_usage": {
"digital_signature": true,
"key_encipherment": true,
"value": 5
},
"basic_constraints": {},
"subject_alt_name": {
"dns_names": [
"dns.google",
"dns.google.com",
"*.dns.google.com",
"8888.google",
"dns64.dns.google"
],
"ip_addresses": [
"8.8.8.8",
"8.8.4.4",
"2001:4860:4860::8888",
"2001:4860:4860::8844",
"2001:4860:4860::6464",
"2001:4860:4860::64"
]
},
"crl_distribution_points": [
"http://c.pki.goog/wr2/9UVbN0w5E6Y.crl"
],
"authority_key_id": "de1b1eed7915d43e3724c321bbec34396d42b230",
"subject_key_id": "0f543b4dd062f6742b9812dfa510c665ad31fec9",
"extended_key_usage": {
"server_auth": true
},
"certificate_policies": [
{
"id": "2.23.140.1.2.1"
}
],
"authority_info_access": {
"ocsp_urls": [
"http://o.pki.goog/wr2"
],
"issuer_urls": [
"http://i.pki.goog/wr2.crt"
]
},
"signed_certificate_timestamps": [
{
"log_id": "cf1156eed52e7caff3875bd9692e9be91a71674ab017ecac01d25b77cecc3b08",
"timestamp": "2025-02-03T09:38:01Z",
"signature": {
"hash_algorithm": "SHA256",
"signature_algorithm": "ECDSA",
"signature": "304402203acb5a125104f36e4eb43c2ecd8002e7c00918ac0a890ec6b9acdb889d493e8f022053e55f79162a0ef9cdadf5b9cd4b0dab675d0e81379332e4b21af05dd407de9e"
}
},
{
"log_id": "134adf1ab5984209780c6fef4c7a91a416b72349ce58576adfaedaa7c2abe022",
"timestamp": "2025-02-03T09:38:01Z",
"signature": {
"hash_algorithm": "SHA256",
"signature_algorithm": "ECDSA",
"signature": "304502205ff3dd1cae1dffa9c3ba09b951d4aef43d0efe842c12d280c0d2f8f3f138e4a00221009bdb67fe1fc539638254507ebc7d41f0bf44f394a75a7d082c77e7a2efce1466"
}
}
]
},
"serial_number_hex": "0d32a434df5683b509748b3f1525e0f4",
"ja4x": "a373a9f83c6b_7022c563de38_2e3757343cb0"
},
"names": [
"*.dns.google.com",
"8.8.4.4",
"8.8.8.8",
"8888.google",
"dns.google",
"dns.google.com",
"dns64.dns.google"
],
"validation_level": "dv",
"validation": {
"nss": {
"is_valid": true,
"ever_valid": true,
"has_trusted_path": true,
"had_trusted_path": true,
"chains": [
{
"sha256fp": [
"e6fe22bf45e4f0d3b85c59e02c0f495418e1eb8d3210f788d48cd5e1cb547cd4",
"d947432abde7b7fa90fc2e6b59101b1280e0e1c7e4e40fa3c6887fff57a7f4cf"
]
},
{
"sha256fp": [
"e6fe22bf45e4f0d3b85c59e02c0f495418e1eb8d3210f788d48cd5e1cb547cd4",
"3ee0278df71fa3c125c4cd487f01d774694e6fc57e0cd94c24efd769133918e5",
"ebd41040e4bb3ec742c9e381d31ef2a41a48b6685c96e7cef3c1df6cd4331c99"
]
}
],
"parents": [
"e6fe22bf45e4f0d3b85c59e02c0f495418e1eb8d3210f788d48cd5e1cb547cd4"
],
"type": "leaf"
},
"microsoft": {
"is_valid": true,
"ever_valid": true,
"has_trusted_path": true,
"had_trusted_path": true,
"chains": [
{
"sha256fp": [
"e6fe22bf45e4f0d3b85c59e02c0f495418e1eb8d3210f788d48cd5e1cb547cd4",
"2a575471e31340bc21581cbd2cf13e158463203ece94bcf9d3cc196bf09a5472"
]
},
{
"sha256fp": [
"e6fe22bf45e4f0d3b85c59e02c0f495418e1eb8d3210f788d48cd5e1cb547cd4",
"d947432abde7b7fa90fc2e6b59101b1280e0e1c7e4e40fa3c6887fff57a7f4cf"
]
},
{
"sha256fp": [
"e6fe22bf45e4f0d3b85c59e02c0f495418e1eb8d3210f788d48cd5e1cb547cd4",
"3ee0278df71fa3c125c4cd487f01d774694e6fc57e0cd94c24efd769133918e5",
"ebd41040e4bb3ec742c9e381d31ef2a41a48b6685c96e7cef3c1df6cd4331c99"
]
}
],
"parents": [
"e6fe22bf45e4f0d3b85c59e02c0f495418e1eb8d3210f788d48cd5e1cb547cd4"
],
"type": "leaf"
},
"apple": {
"is_valid": true,
"ever_valid": true,
"has_trusted_path": true,
"had_trusted_path": true,
"chains": [
{
"sha256fp": [
"e6fe22bf45e4f0d3b85c59e02c0f495418e1eb8d3210f788d48cd5e1cb547cd4",
"d947432abde7b7fa90fc2e6b59101b1280e0e1c7e4e40fa3c6887fff57a7f4cf"
]
},
{
"sha256fp": [
"e6fe22bf45e4f0d3b85c59e02c0f495418e1eb8d3210f788d48cd5e1cb547cd4",
"3ee0278df71fa3c125c4cd487f01d774694e6fc57e0cd94c24efd769133918e5",
"ebd41040e4bb3ec742c9e381d31ef2a41a48b6685c96e7cef3c1df6cd4331c99"
]
}
],
"parents": [
"e6fe22bf45e4f0d3b85c59e02c0f495418e1eb8d3210f788d48cd5e1cb547cd4"
],
"type": "leaf"
},
"chrome": {
"ever_valid": true,
"had_trusted_path": true,
"parents": [
"e6fe22bf45e4f0d3b85c59e02c0f495418e1eb8d3210f788d48cd5e1cb547cd4"
],
"type": "leaf"
}
},
"revocation": {
"ocsp": {
"reason": "unspecified"
},
"crl": {
"reason": "unspecified"
}
},
"ct": {
"entries": {
"cloudflare_nimbus_2025": {
"index": 873149865,
"added_to_ct_at": "2025-02-18T16:51:33Z",
"ct_to_censys_at": "2025-02-18T17:39:09Z"
},
"comodo_dodo": {
"index": 207187936,
"added_to_ct_at": "2025-02-18T16:39:06Z",
"ct_to_censys_at": "2025-02-18T16:48:47Z"
},
"digicert_nessie_2025": {
"index": 650753700,
"added_to_ct_at": "2025-02-18T16:39:06Z",
"ct_to_censys_at": "2025-02-19T05:15:09Z"
},
"digicert_yeti_2025": {
"index": 1000061290,
"added_to_ct_at": "2025-02-18T16:39:06Z",
"ct_to_censys_at": "2025-02-19T05:25:58Z"
},
"google_argon_2025_h1": {
"index": 1001068177,
"added_to_ct_at": "2025-02-18T16:39:07Z",
"ct_to_censys_at": "2025-02-18T16:51:49Z"
},
"google_xenon_2025_h1": {
"index": 1430067497,
"added_to_ct_at": "2025-02-18T16:39:06Z",
"ct_to_censys_at": "2025-02-18T16:43:41Z"
},
"letsencrypt_ct_oak_2025_h1": {
"index": 668662087,
"added_to_ct_at": "2025-02-18T16:39:07Z",
"ct_to_censys_at": "2025-02-18T16:44:34Z"
},
"letsencrypt_ct_sycamore_2025_h1_b": {
"index": 1535366052,
"added_to_ct_at": "2025-02-18T16:39:06Z",
"ct_to_censys_at": "2025-02-18T16:45:07Z"
},
"letsencrypt_ct_twig_2025_h1_b": {
"index": 1774137785,
"added_to_ct_at": "2025-02-18T16:39:07Z",
"ct_to_censys_at": "2025-02-18T16:46:39Z"
},
"letsencrypt_ct_willow_2025_h1_b": {
"index": 1536361859,
"added_to_ct_at": "2025-02-18T16:39:07Z",
"ct_to_censys_at": "2025-02-18T16:41:40Z"
},
"sunlight_rome_2025_h1": {
"index": 1577786059,
"added_to_ct_at": "2025-02-18T16:39:06Z",
"ct_to_censys_at": "2025-02-18T16:51:40Z"
}
}
},
"ever_seen_in_scan": true,
"added_at": "2025-02-16T08:59:19Z",
"modified_at": "2025-02-21T10:36:05Z",
"validated_at": "2025-02-22T19:18:47Z",
"parse_status": "success",
"zlint": {
"version": 3,
"timestamp": "2025-02-16T08:59:19Z",
"notices_present": true,
"failed_lints": [
"n_subject_common_name_included"
]
},
"spki_subject_fingerprint_sha256": "6e17db6af474d4c5aaa65ae8a5bc1f74931b36eb55c1c4d9161e7d979735bd40",
"parent_spki_subject_fingerprint_sha256": "95b148afc4c249d314067527813d43973574f8e11a905040c881510026ae74f9"
},
"extensions": {}
}Certificate trust and validation
Trust chains are an important part of certificate usage. For a certificate to be trusted, the certificate must chain up, through a series of signing certificates, to a root certificate that is present in a major root trust store.
Censys indexes certificate trust information for each root store in a record called validation. The following fields are prepended by the applicable browser, for example the full path for the ever valid field described below for Chrome is cert.validation.chrome.ever_valid. The following information is contained within certificate validation fields:
- Valid (
*.is_valid): A boolean value for whether the certificate is trusted by the browser using the root store. - Ever valid (
*.ever_valid): A boolean value for whether an expired certificate was trusted by the browser before it expired. - Parents (
*.parents): A list of the fingerprints of the intermediary and root certificates in the chain. - Chain (
*.chains): A representation of the chain or chains of signing certificates up to the root. - Had trusted path (
*.had_trusted_path): A boolean value for whether the chain was trusted by the browser. - In revocation set (
*.in_revocation_set): Whether the certificate is included in the browser’s list of certificates whose trust has been revoked before their expiration.
Censys regularly validates unexpired certificates. Values of validation fields and related labels are accurate as of the cert.validated_at timestamp in the certificate record.
Updated about 1 month ago
