Insights
Insights in Censys Attack Surface Management (ASM) organizes and presents key data points about your attack surface, like the state of your inventory's software and services, in an understandable and actionable format. The Insights search bar provides several pre-formatted prompts to help you investigate your inventory and learn how to build useful ASM queries.
Insights helps you stay on top of key security initiatives like software compliance and vulnerability management. It arms you with the information you need to answer questions about exposures and software in your attack surface and begin remediation workflows.
The Insights experience is available to all ASM users.
Insights is composed of three components: the Ports & Protocols dashboard, Software dashboard, and Insights search bar. Learn more about each below.
Ports & Protocols
The Ports & Protocols dashboard enables you to understand exactly which ports are open in your attack surface across the full 65,535-port range. This allows you to quickly determine whether there are any open ports that are misconfigured or non-compliant with your organization’s policy.
In addition to ports, the dashboard shows which protocols are present on your ports. ASM identifies whether these protocols are on standard ports, as defined by IANA. Nonstandard port and protocol combinations may indicate misconfigurations or malicious behavior. By closing these gaps, you can reduce your attack surface and, in turn, reduce the chances of a breach.
Learn more about how Censys scanning works and how it helps protect your organization here.
Filter the dashboard
Filter the entire dashboard using the standard and nonstandard toggle and the options available in the Severity, Associated Date, Tags or Protocols dropdown menus. Use the Min Port: and Max Port: fields to define a range of ports to focus on.
NoteUnknown protocols are categorized as running on nonstandard ports by default.
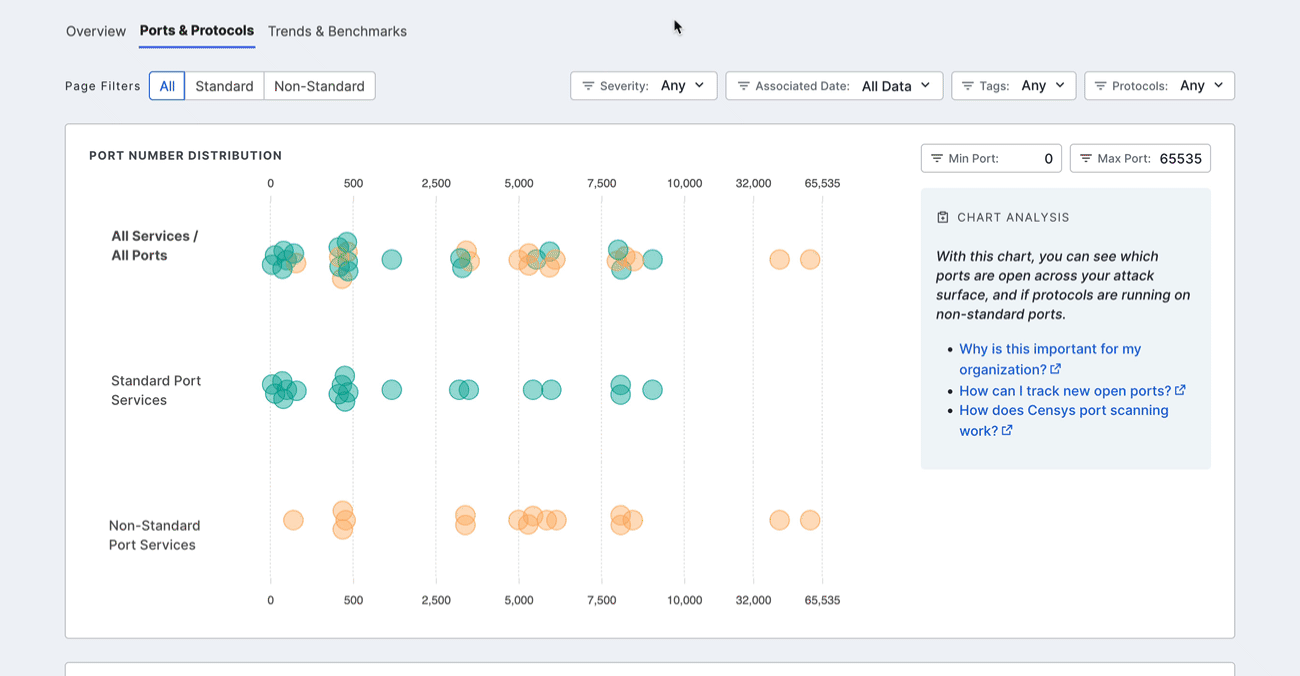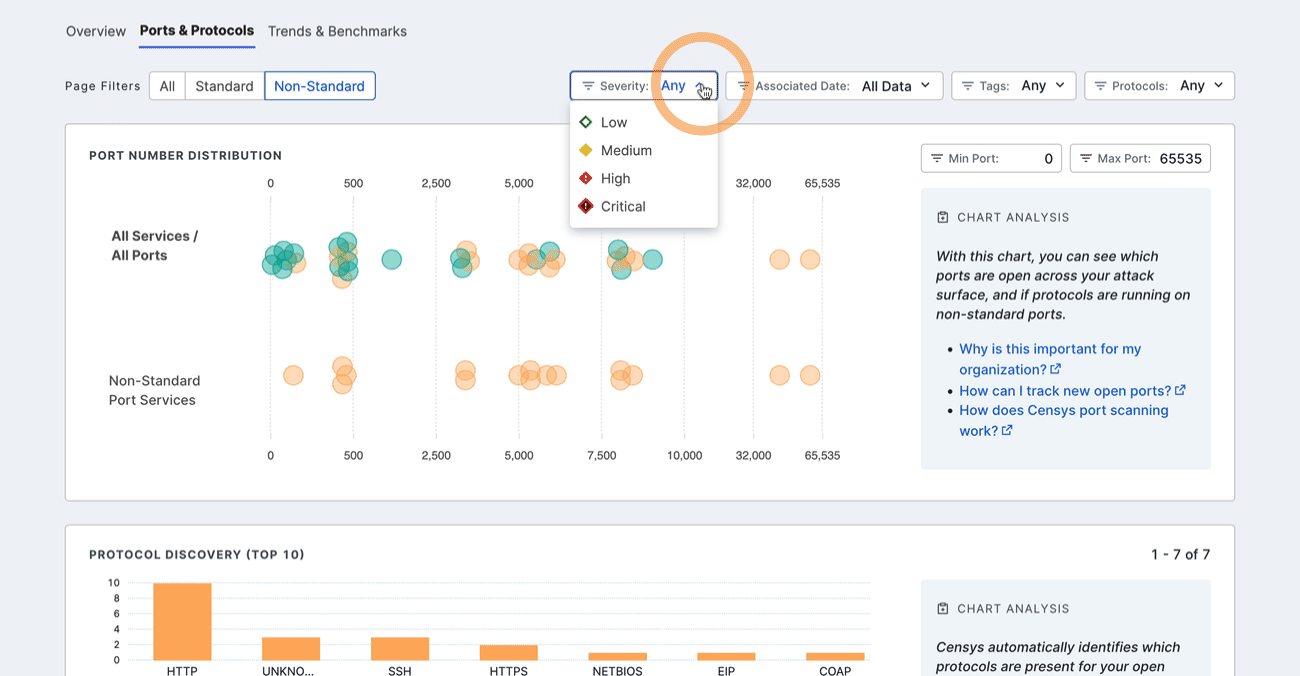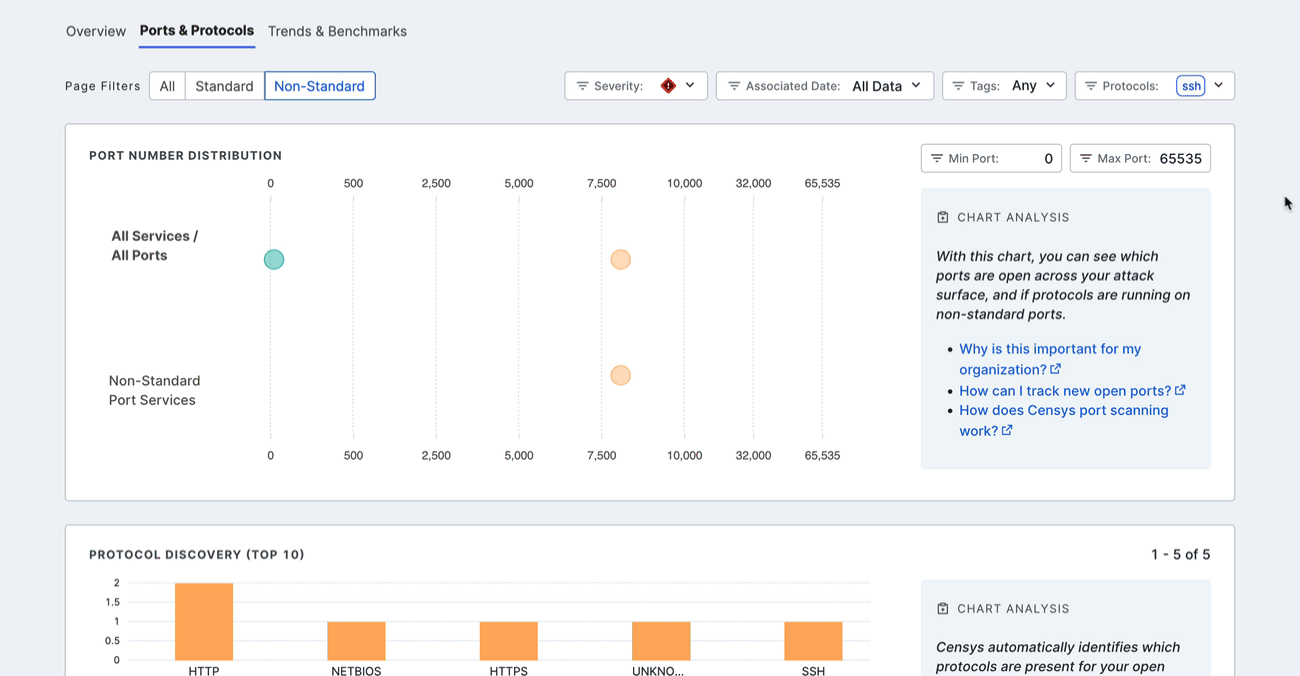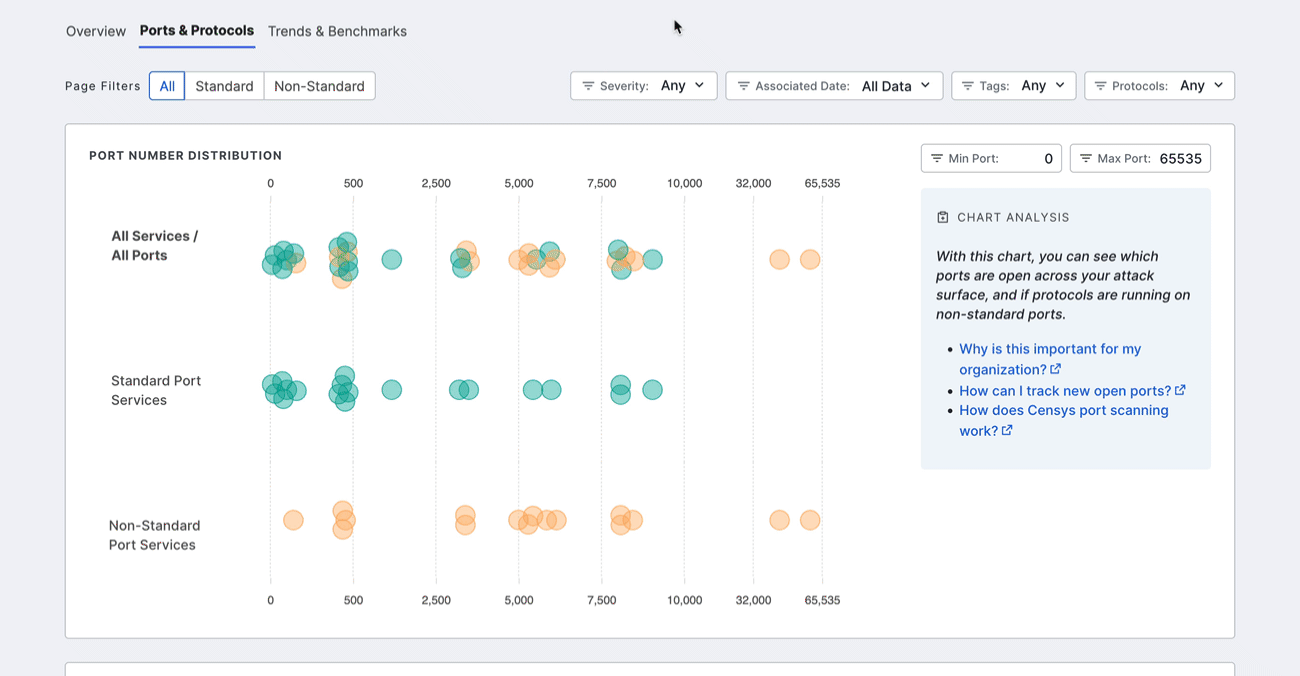
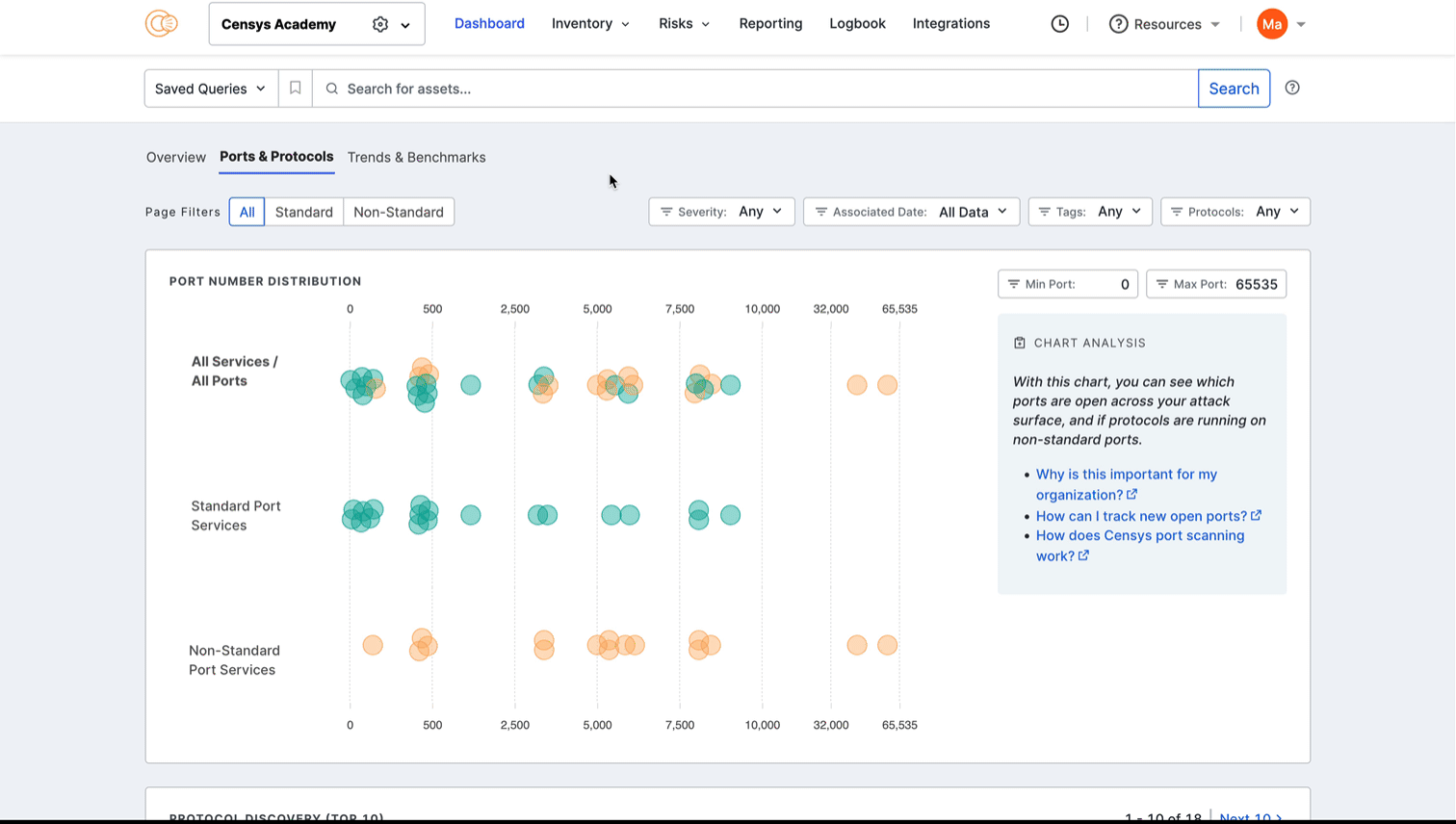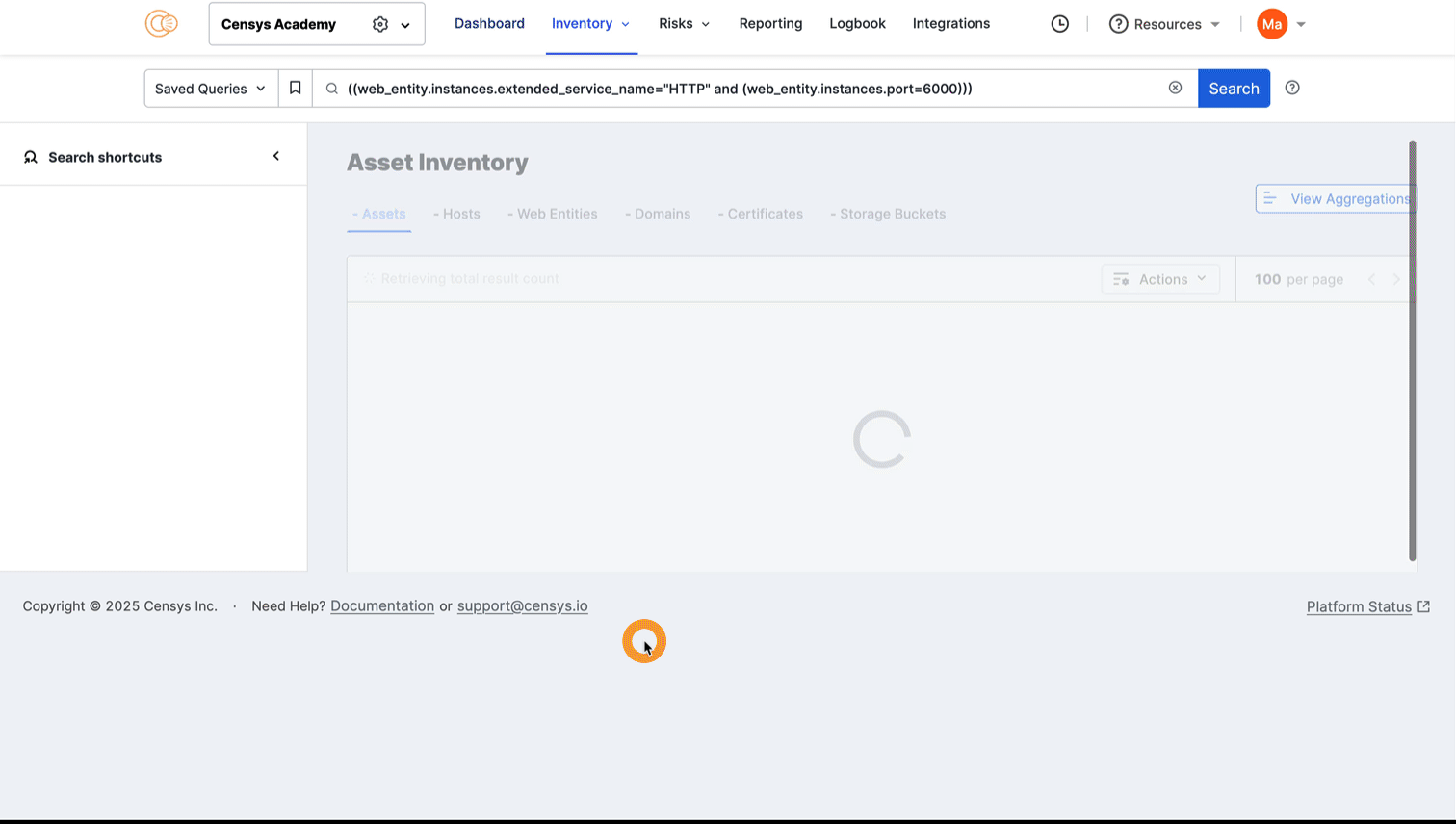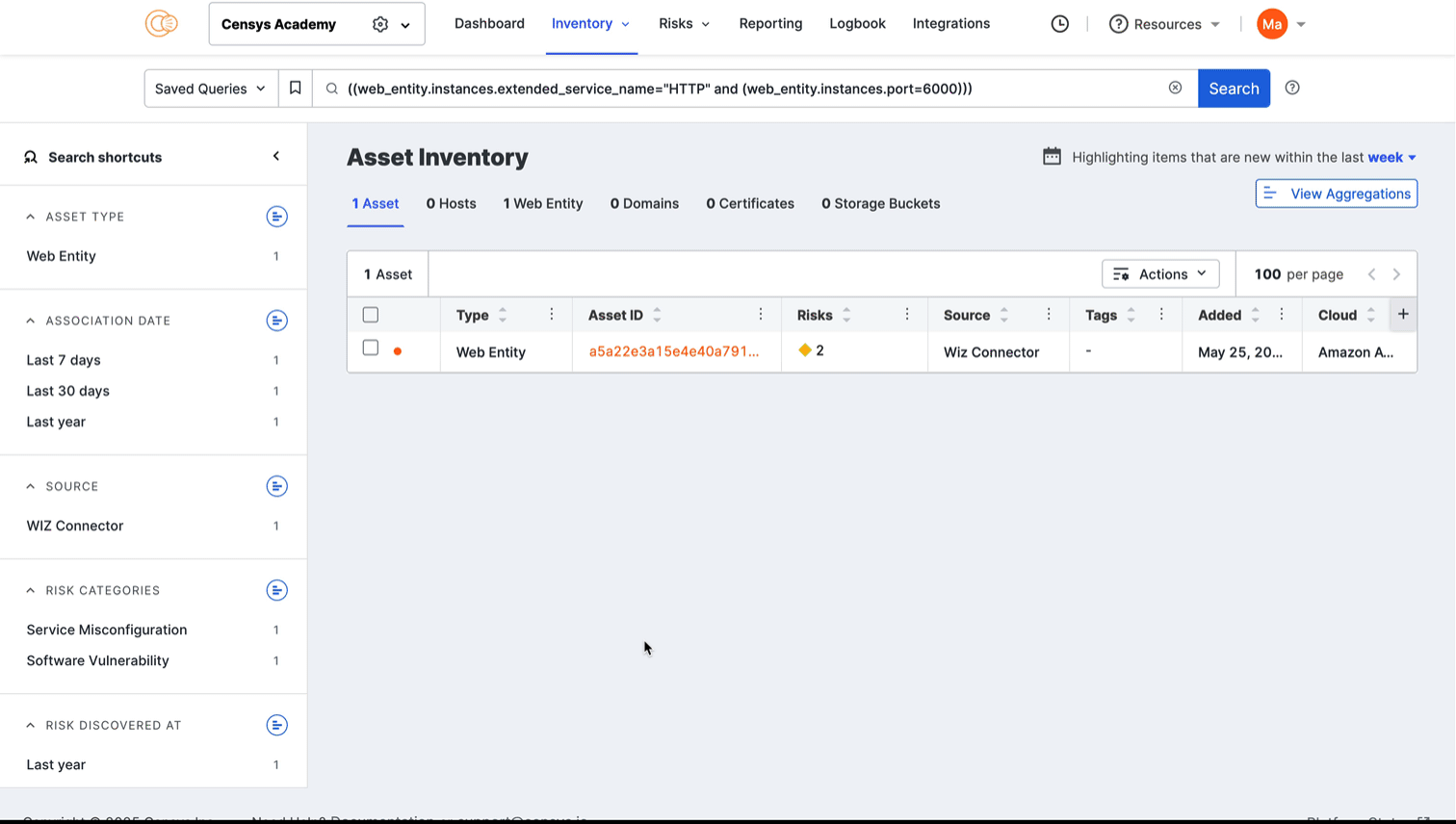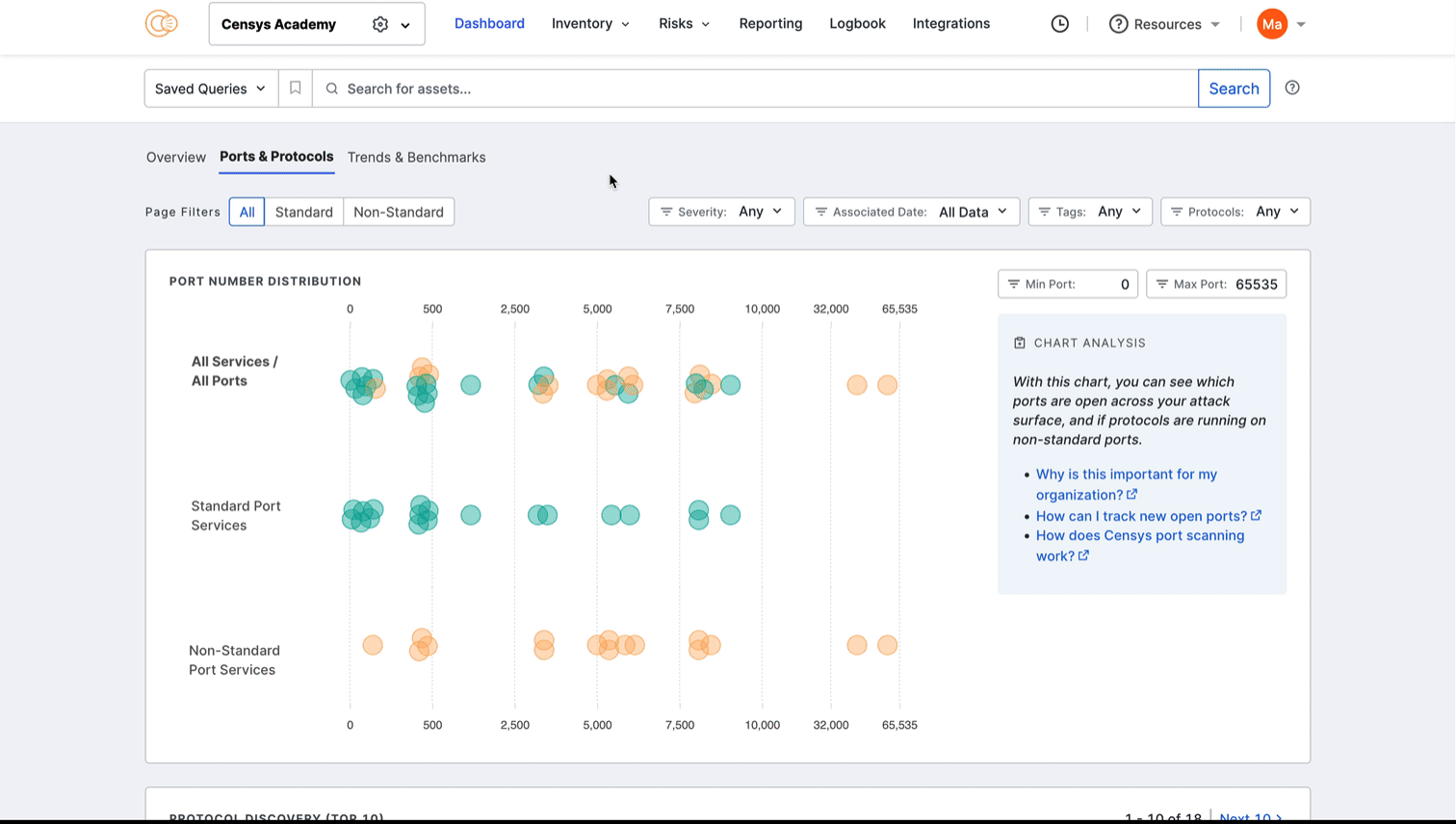
Port number distribution
The port distribution chart is a visualization of all open ports in your attack surface.
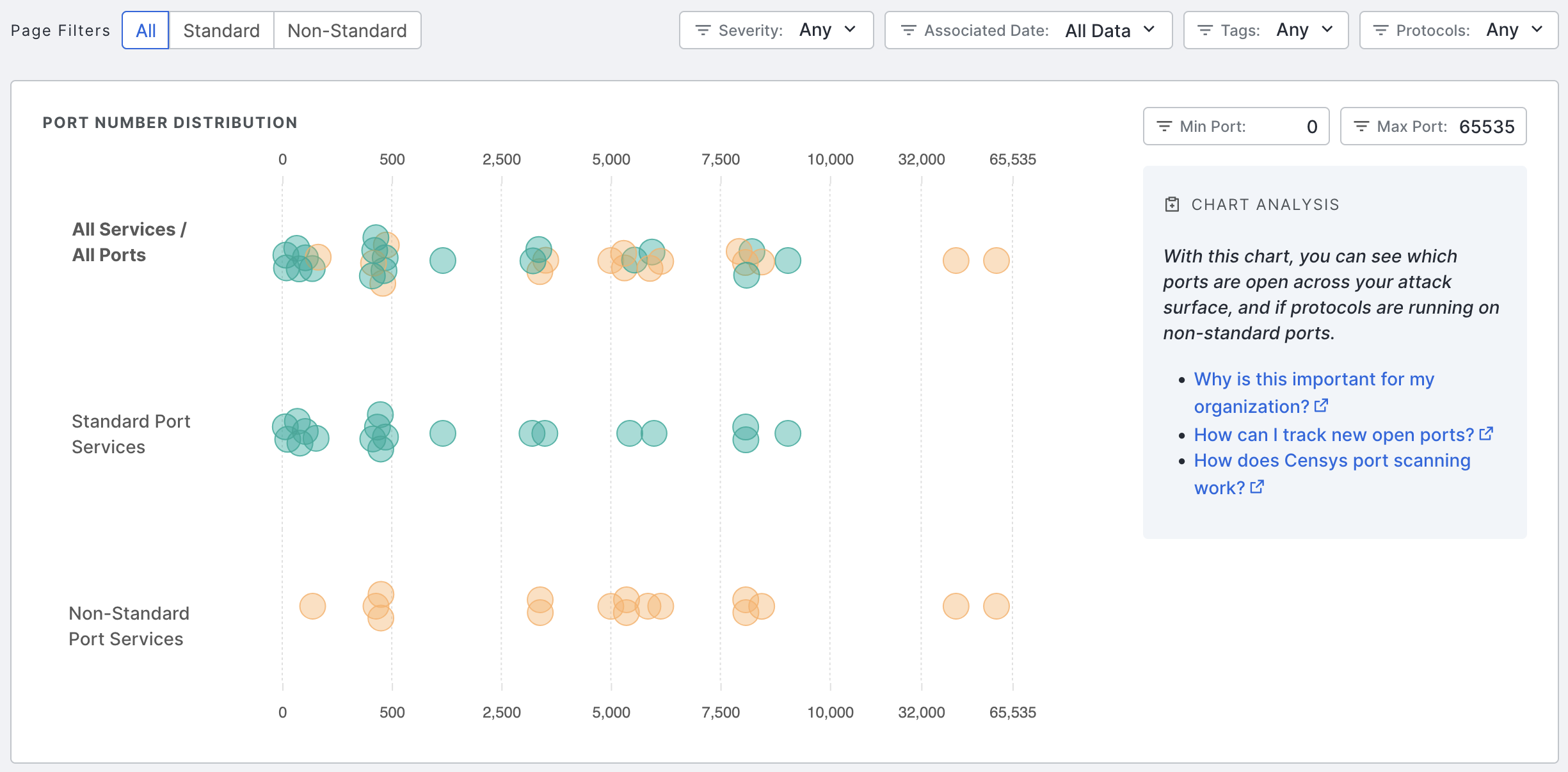
Hover over a dot to view its port number and protocol information. Click the dot to see all assets in your Inventory associated with the port and protocol pair. The query syntax used for this query is shown in the query bar. Set up regular alerting and tagging for these assets with Saved Query Automation.
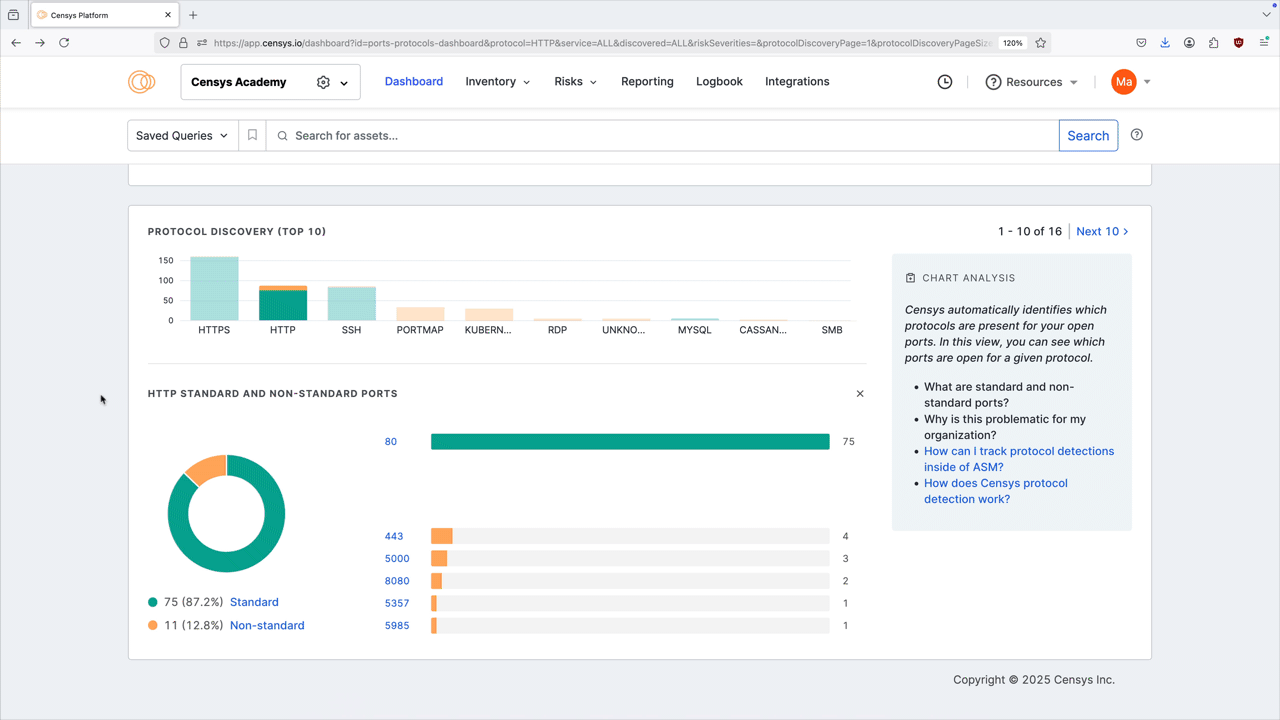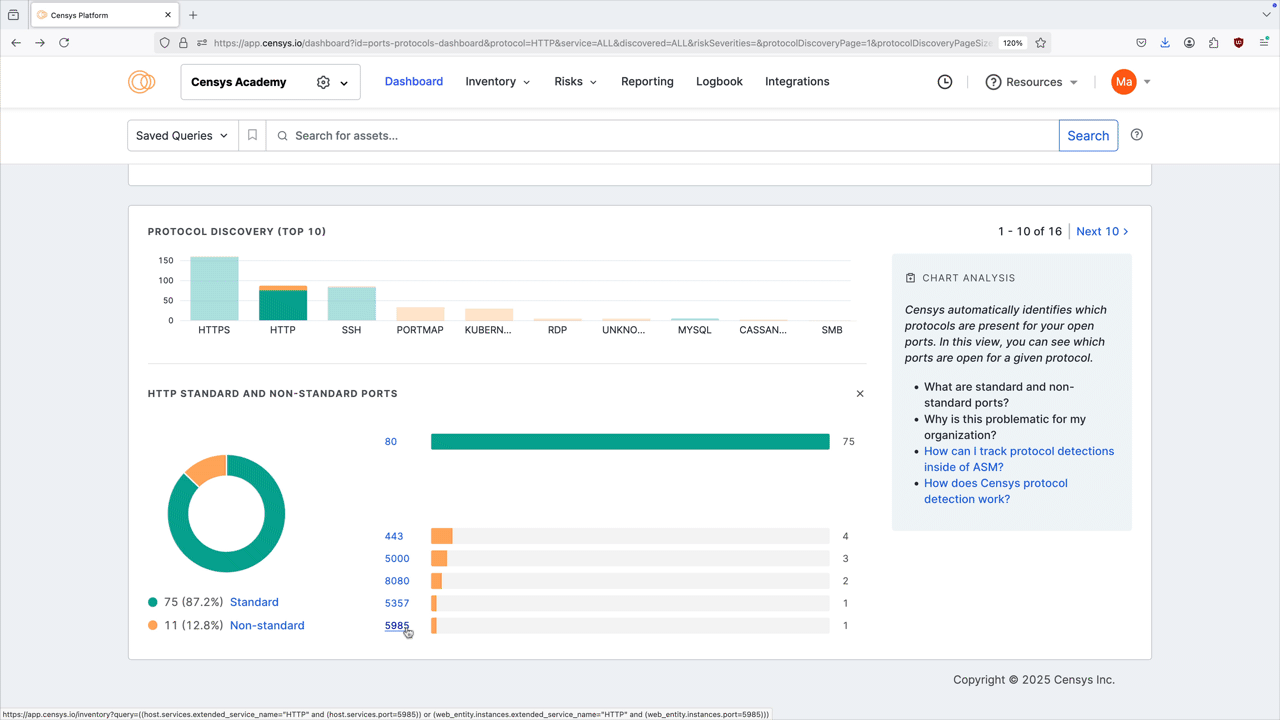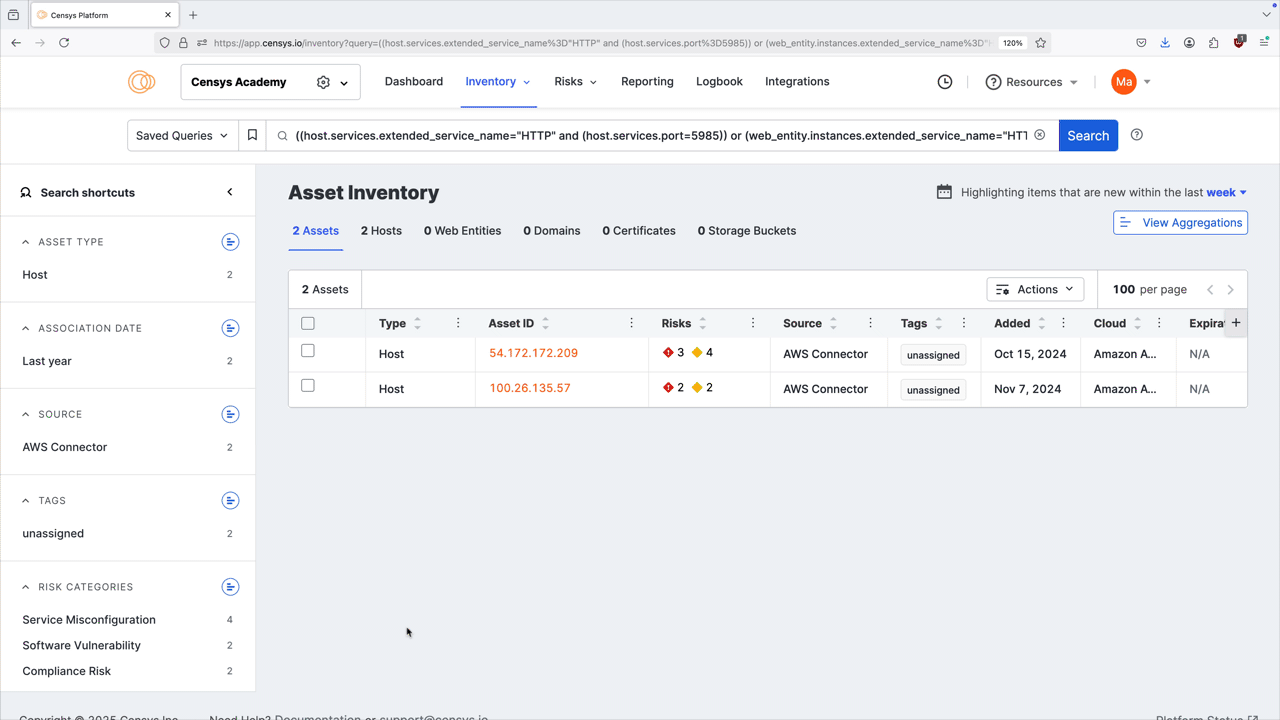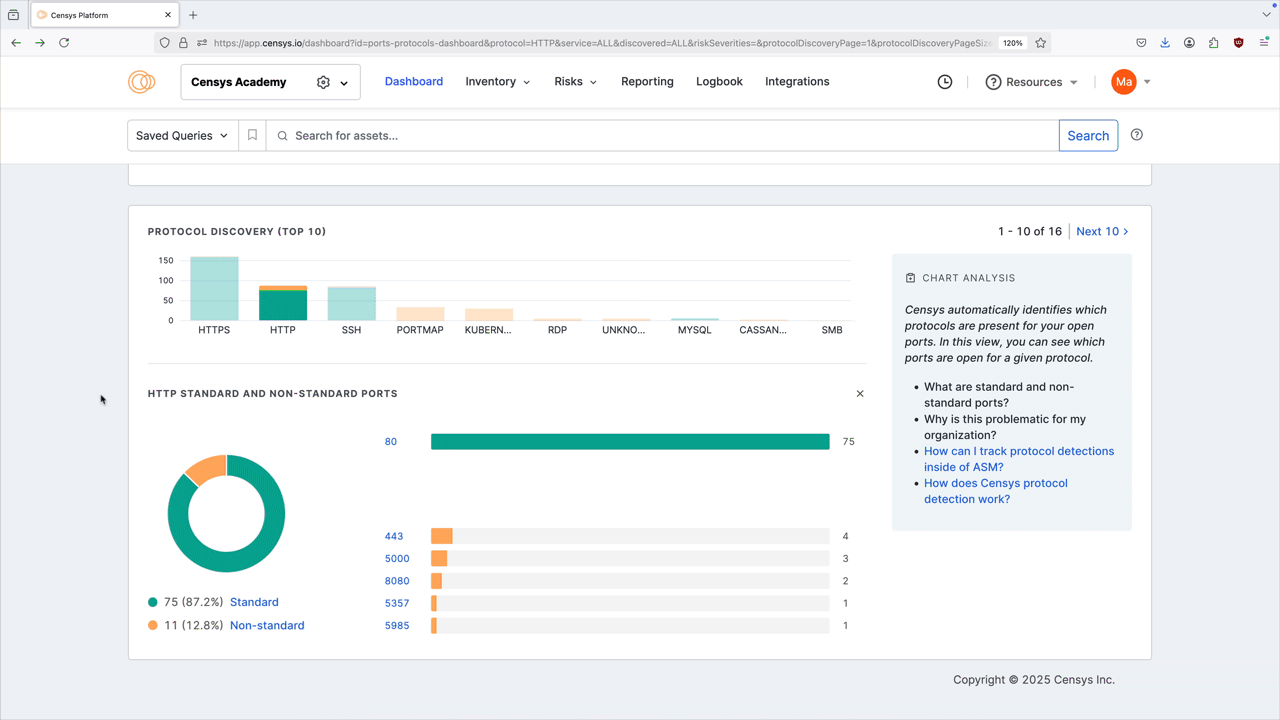
Protocol discovery
The protocol discovery chart shows the count of your services running various protocols. The green component of the bar represents services running on standard ports, while the orange component represents nonstandard ports. Use the Next 10 > and < Previous 10 links to page through your protocols.
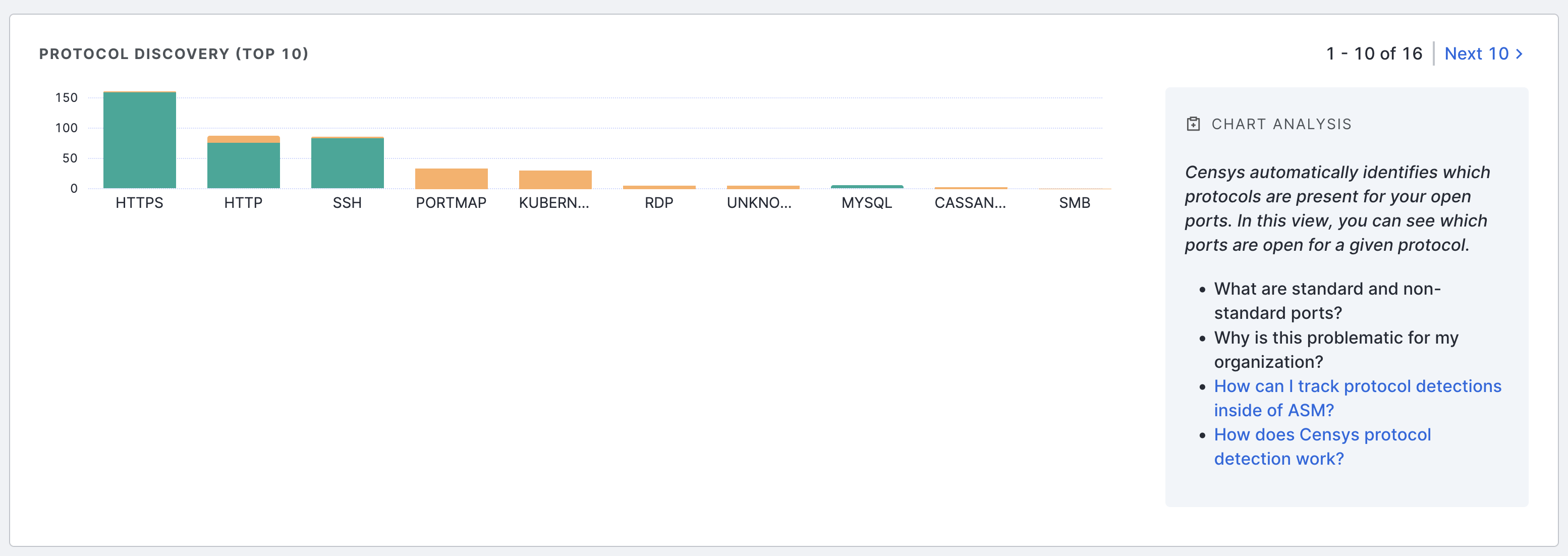
Select a protocol bar plot to see standard and nonstandard port information for that protocol. This will also filter the port number distribution chart above.
Click any of the linked port numbers to see all assets in your Inventory associated with that port and protocol pair. The query syntax used for this query is shown in the query bar. Use Saved Query Automation to set up regular alerting and tagging for these assets.
Ports & Protocol Breakdown
The Ports & Protocol breakdown table provides a list of the protocols present on ports in your inventory, and can be sorted by protocol, type, service count, risk count, and first seen date.
Use cases
- Compliance standards including NIST SP 800 and PCI 4.0 require the closure of unnecessary ports and protocols. Use the dashboard to identify assets to investigate and remediate to align with these standards.
- Use the Severity filter on the dashboard to quickly identify nonstandard ports being used by assets with risks. In general, a misconfigured port is worthy of investigation, while a misconfigured port with a risk should be immediately remediated.
- Attackers use nonstandard ports to evade detection, for example during C2 communication. If your environment has already been infiltrated, activity on a nonstandard port can indicate a compromise and will need to be remediated.
Software
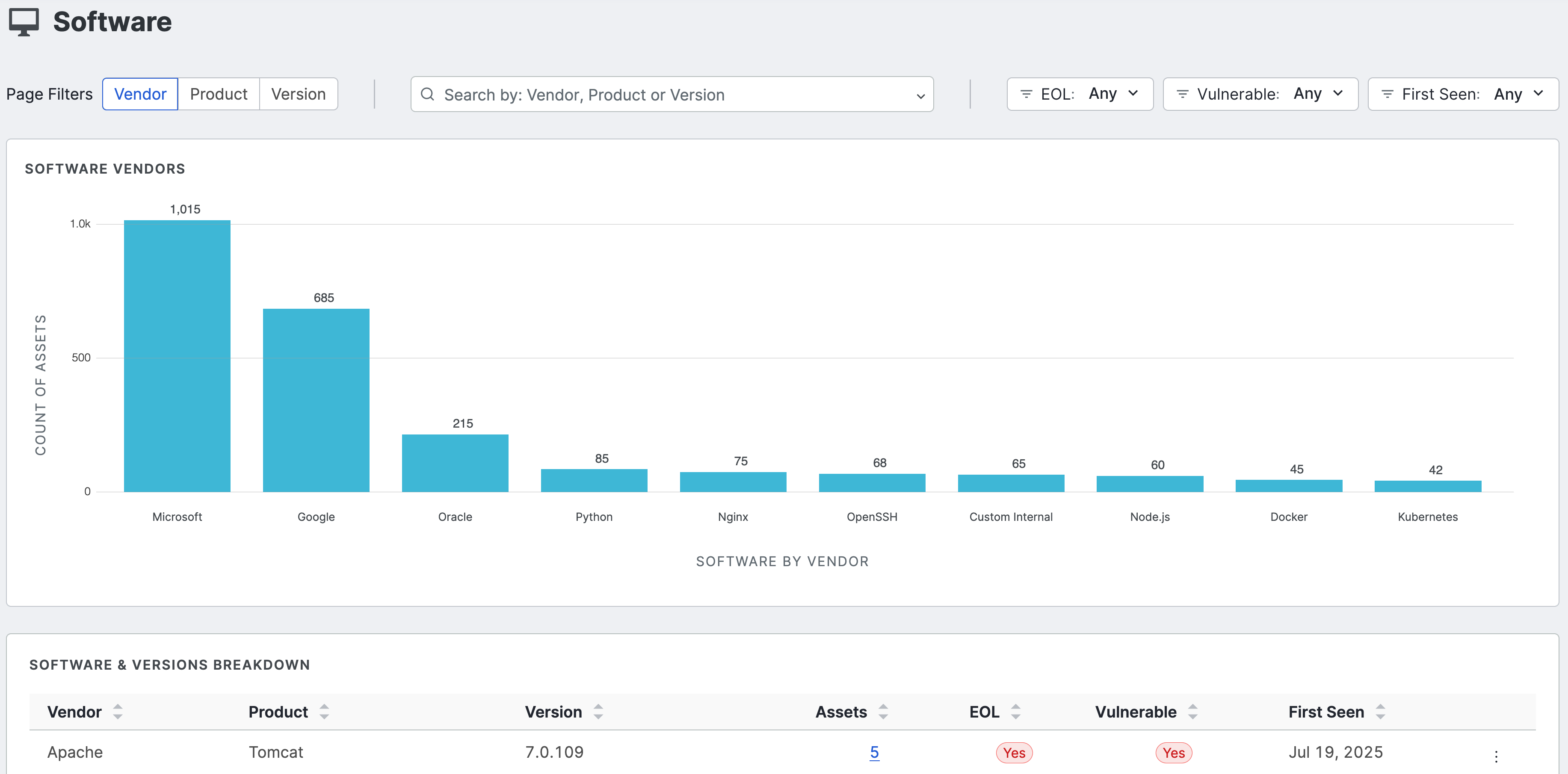
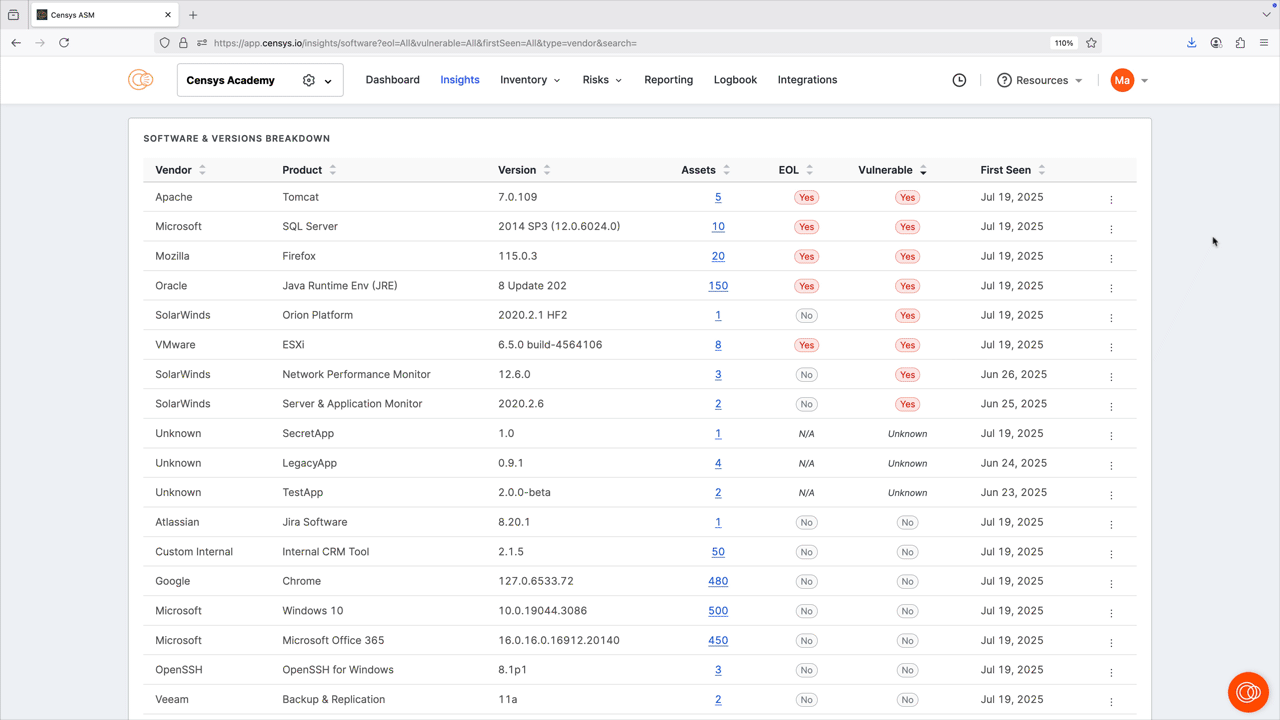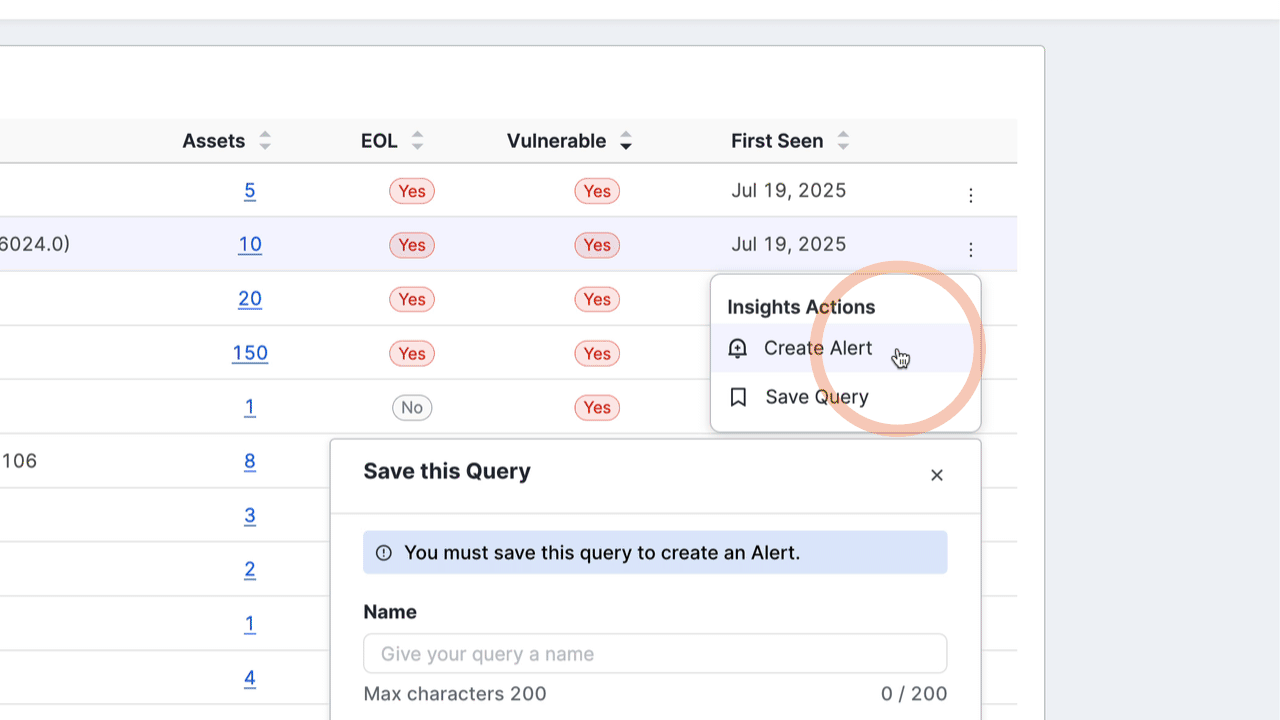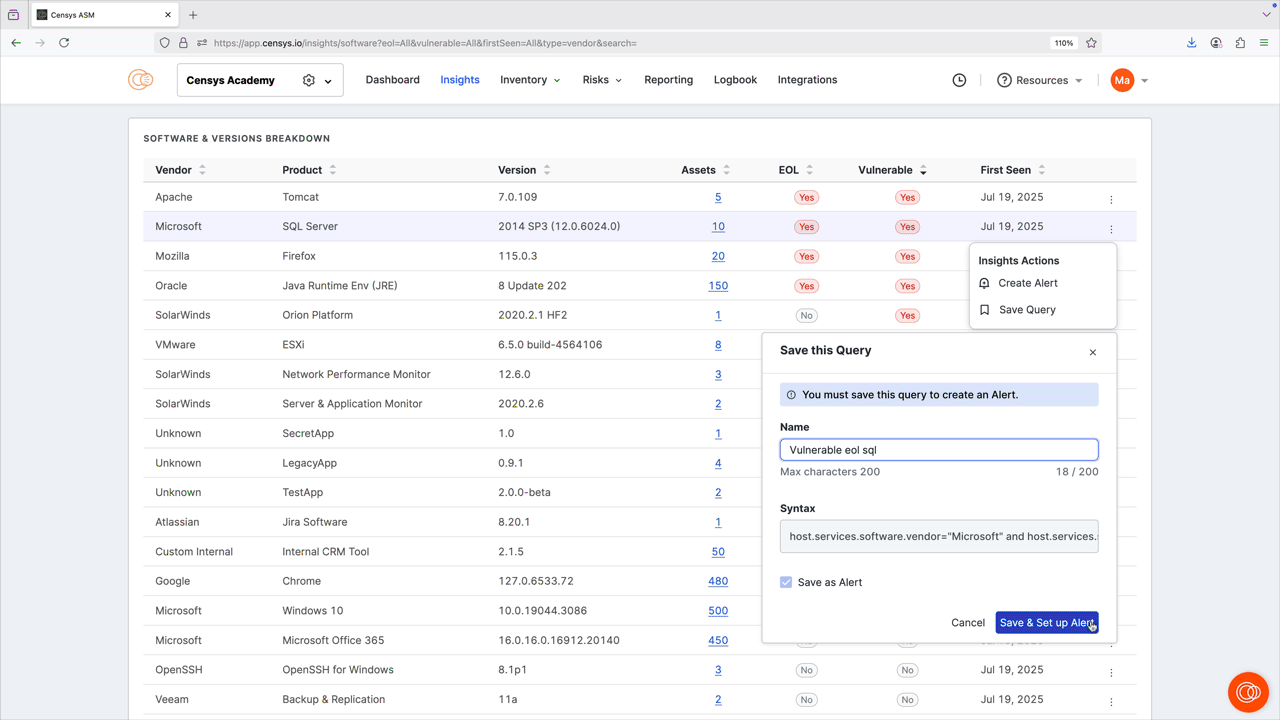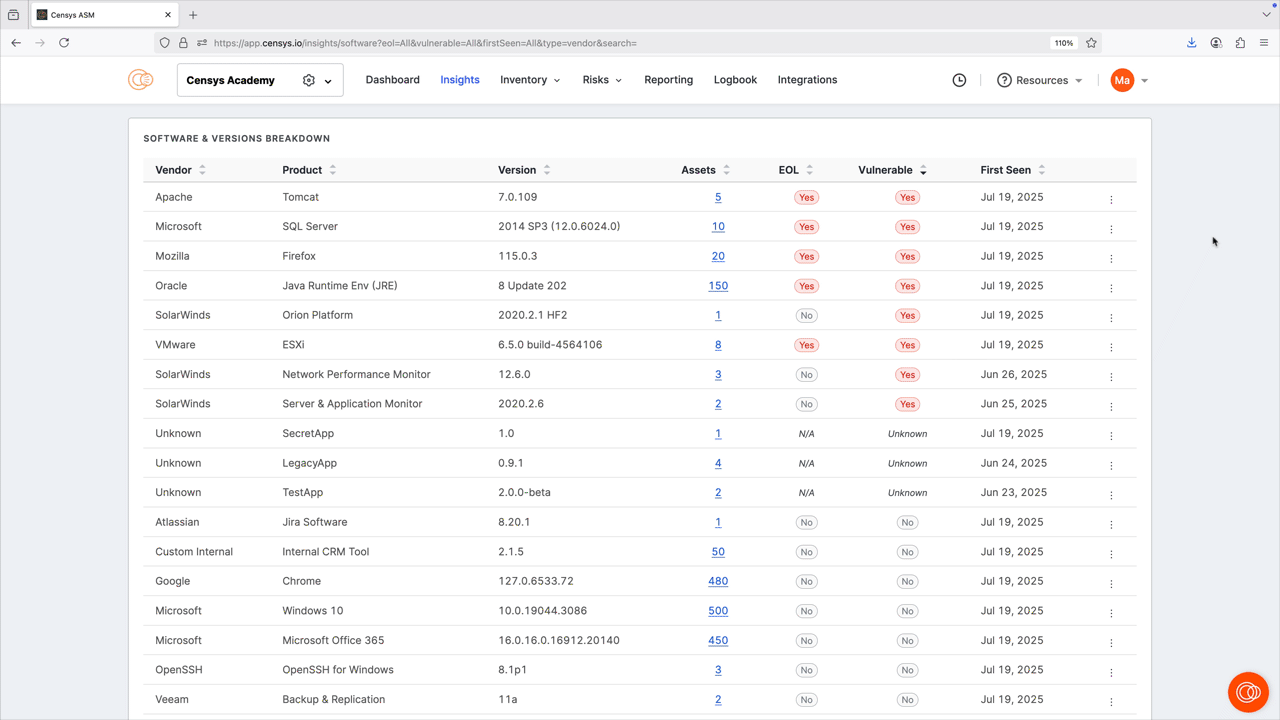
The software dashboard helps you understand the software vendors, products, and versions that are present and exposed in your attack surface.
You can filter and search by vendor, product, and version number. You can also filter by end-of-life (EOL) status, whether the detected software has any vulnerabilities, and when the software was first seen in your attack surface to help you prioritize remediation. Note that the filters you apply affect the entire dashboard view. Click any of the bar plots to see all results for that plot in your inventory; note the pre-built query used to find the results.
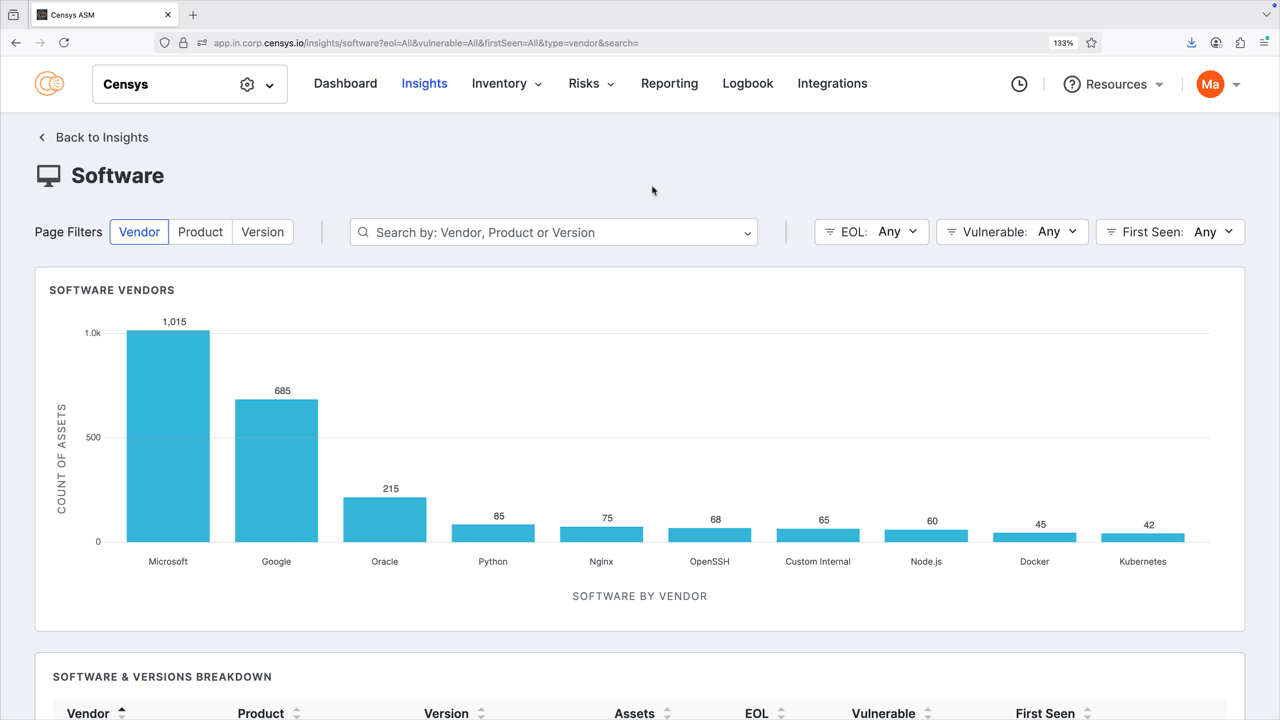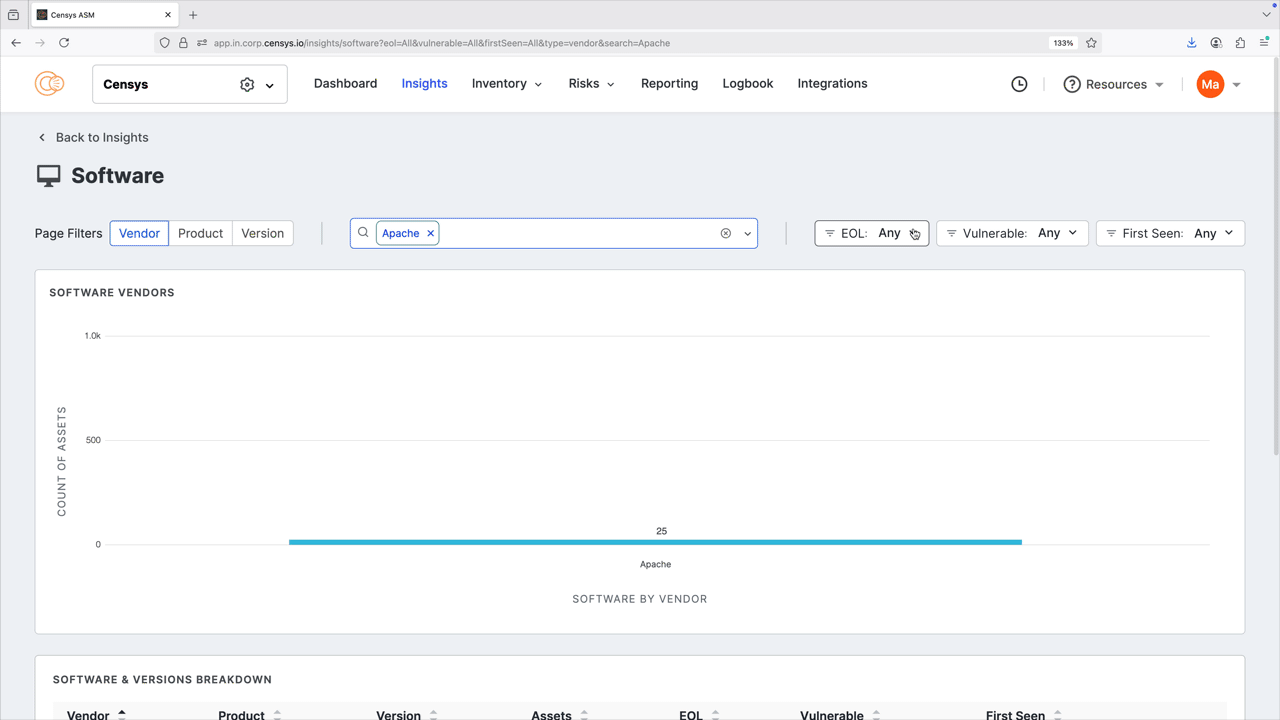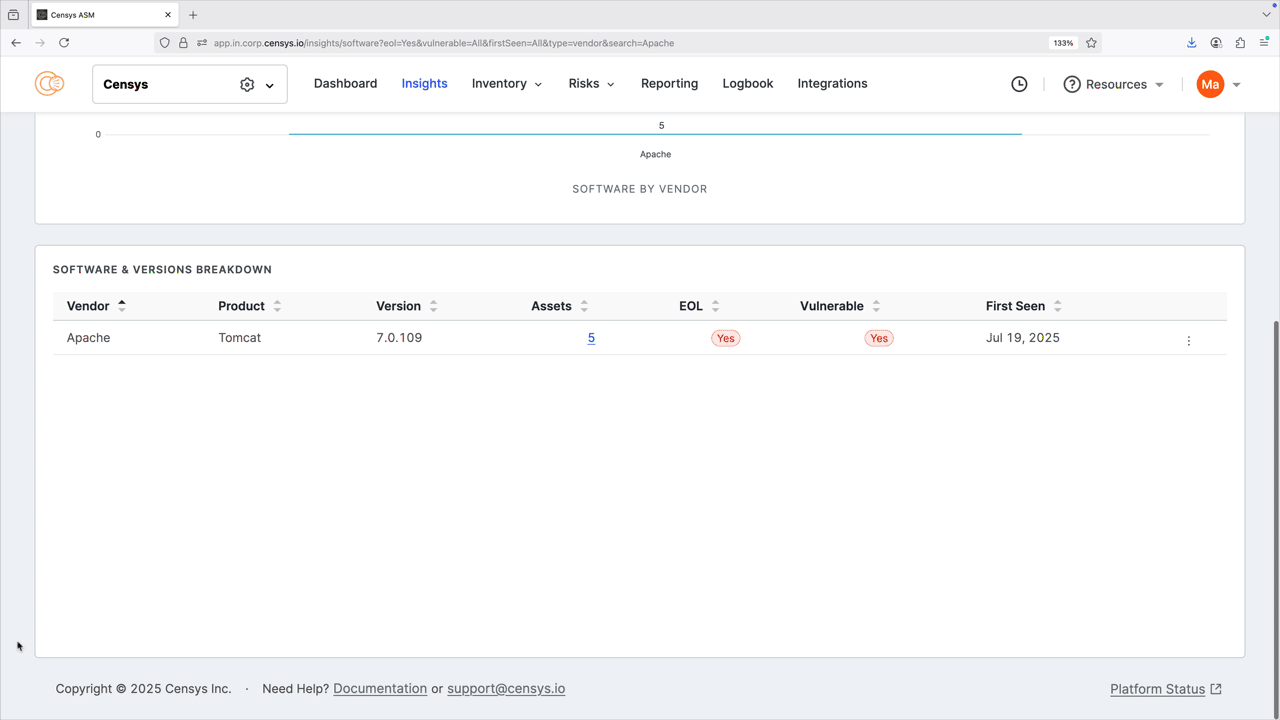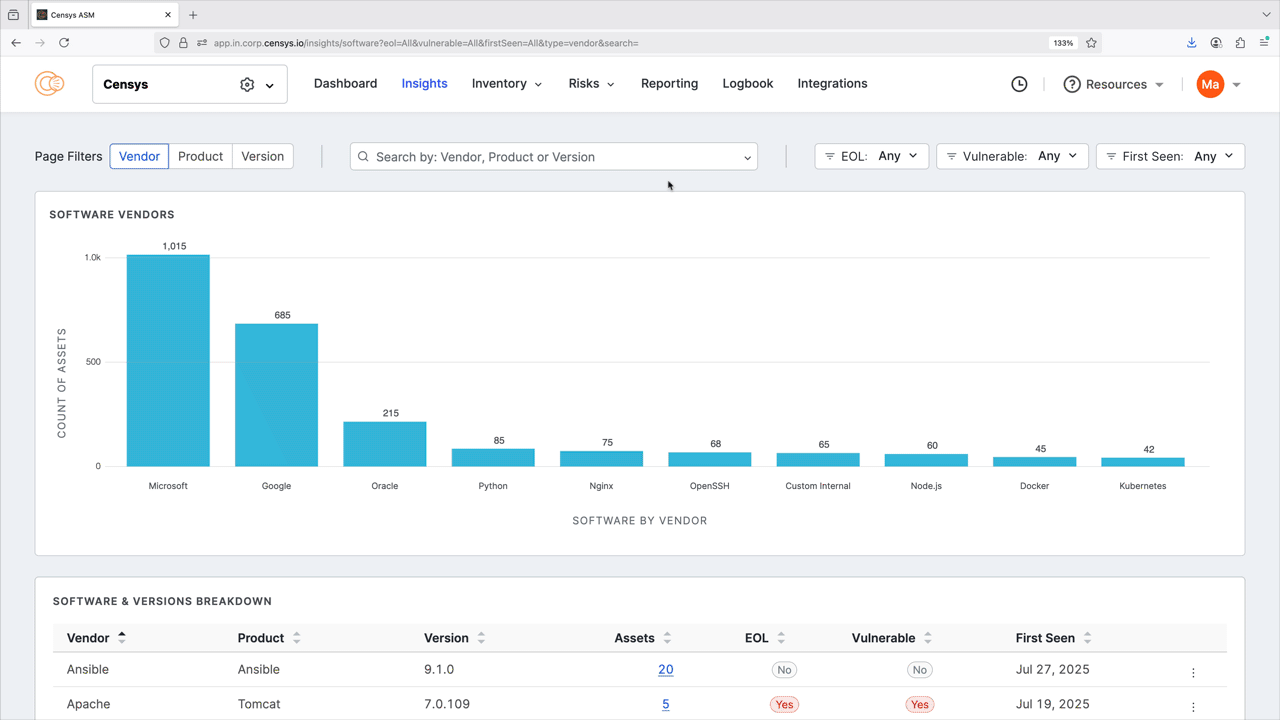
The software & versions breakdown report provides a detailed list of the software present in your inventory, and can be sorted by vendor, product, asset count, and more. Click the linked asset count values to see all results for the indicated software.
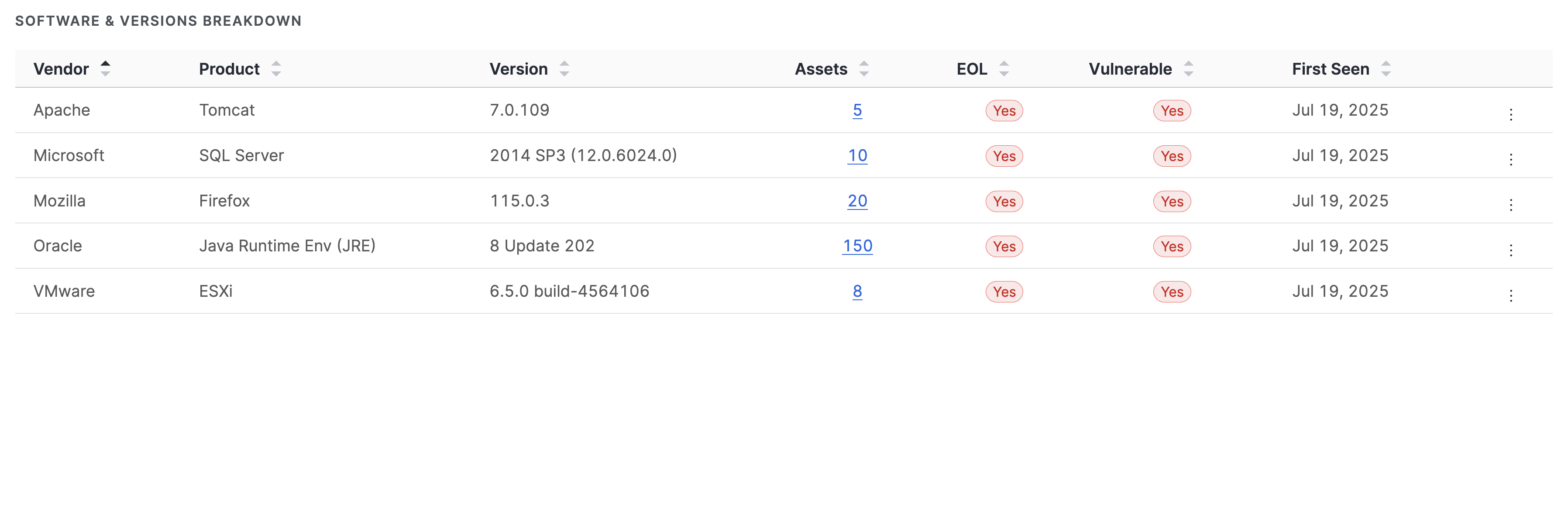
Create saved queries and alerts for software versions
From the software & versions breakdown report, you can quickly create alerts and saved queries for specific software versions. Use this to track versions of interest and receive notifications about additions to or removals from your inventory.
To create an alert or saved query:
- On the row for a software version, click the three-dot icon to open the Insights Actions menu.
- Select Save Query or Create Alert. Complete setup for your query or alert following the prompt.
End-of-life data collection
End-of-life data is collected from the endoflife.date feed. This source collects EOL information for over 400 products using web scraping for various support and product pages. This means that if endoflife.date loses access to a support page for a specific product, EOL data for that product may be interrupted. Learn more about endoflife.data EOL collection methodologies here.
Insights search bar
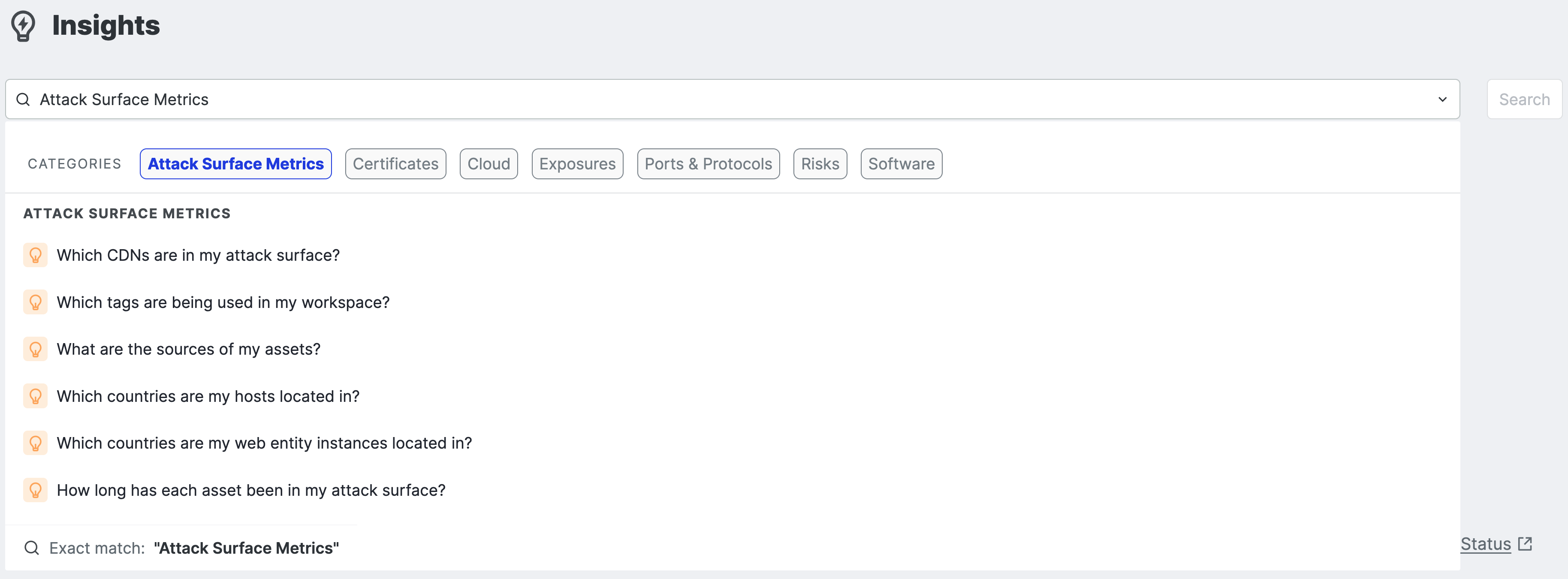
The search bar features several common attack surface questions presented in a natural language format. Use the prompts to explore your attack surface, find assets of interest, and learn about ASM data and how to effectively compose queries in the Censys Search Language.
Updated 8 days ago
