Role-based Access Control
The Censys Platform uses role-based access control (RBAC) to provide granular access control for users and resources. This document explains the various roles, their permissions, and how relationships to resources enhance functionality and security.
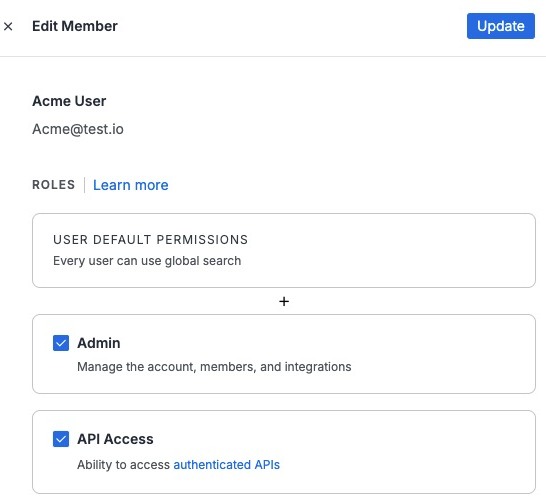
Assign and edit Member Roles
Follow the steps below to edit a member's role. This operation can be performed after the member accepts the invite.
NoteYou must be an admin to grant, edit, or revoke roles.
- In the left-side navigation panel, go to Settings > Account Management. Under Organization Profile, select Members.
- Click the three-dot menu to the right of the member.
- Click the edit icon.
- Apply appropriate roles and click Update.
Core roles and permissions
Admin
Admins have the highest level of permissions within an organization.
Capabilities
- Manage account settings, billing, and collection webhook integrations.
- Invite, edit, and remove users.
- Promote users to Admin roles.
- Grant the API Access role to members, allowing them to access authenticated APIs.
- Configure and manage SSO configurations.
- Create, update, and delete integrations.
- Grant Members access to integrations.
Admins cannot delete or modify another member's Personal Access Token for API access.
Member
Default role for all users, with basic access permissions.
Capabilities
- Access integrations if granted appropriate permissions.
- Edit their personal account settings. If a member is granted API Access Role, they can generate, modify, or delete their API key (Personal Access Token).
Key features and functionality
Default relationships
- Viewer Access to Global Search: All users can access Global Search by default.
Advanced capabilities
Integration management
Admins can perform the following actions for integrations:
- View, edit, or delete collections webhooks.
API Access role
Admins can assign members the API Access role. This role allows the member to access the Censys Platform API. Members with this role must create a Personal Access Token to make API calls. To learn more, see our API documentation.
API key management
- Members can generate multiple Personal Access Tokens.
- Members can generate, edit, and delete their Personal Access Tokens.
- Future roadmap includes token-specific scopes for enhanced security and limited permissions.
Additional features
Audit and logging
- Admins can view logs of user actions, including role changes, ensuring accountability.
Best practices
- Assign roles thoughtfully: Limit the Admin role to trusted users. Use Member Manager for delegated user management.
- Use relationships: Leverage Viewer and Editor roles to control access without over-assigning permissions.
- Review access regularly: Audit user access and role assignments to ensure security and compliance.
- Secure integrations: Assign integration-related permissions only to those who manage connected workflows.
Updated about 2 months ago
