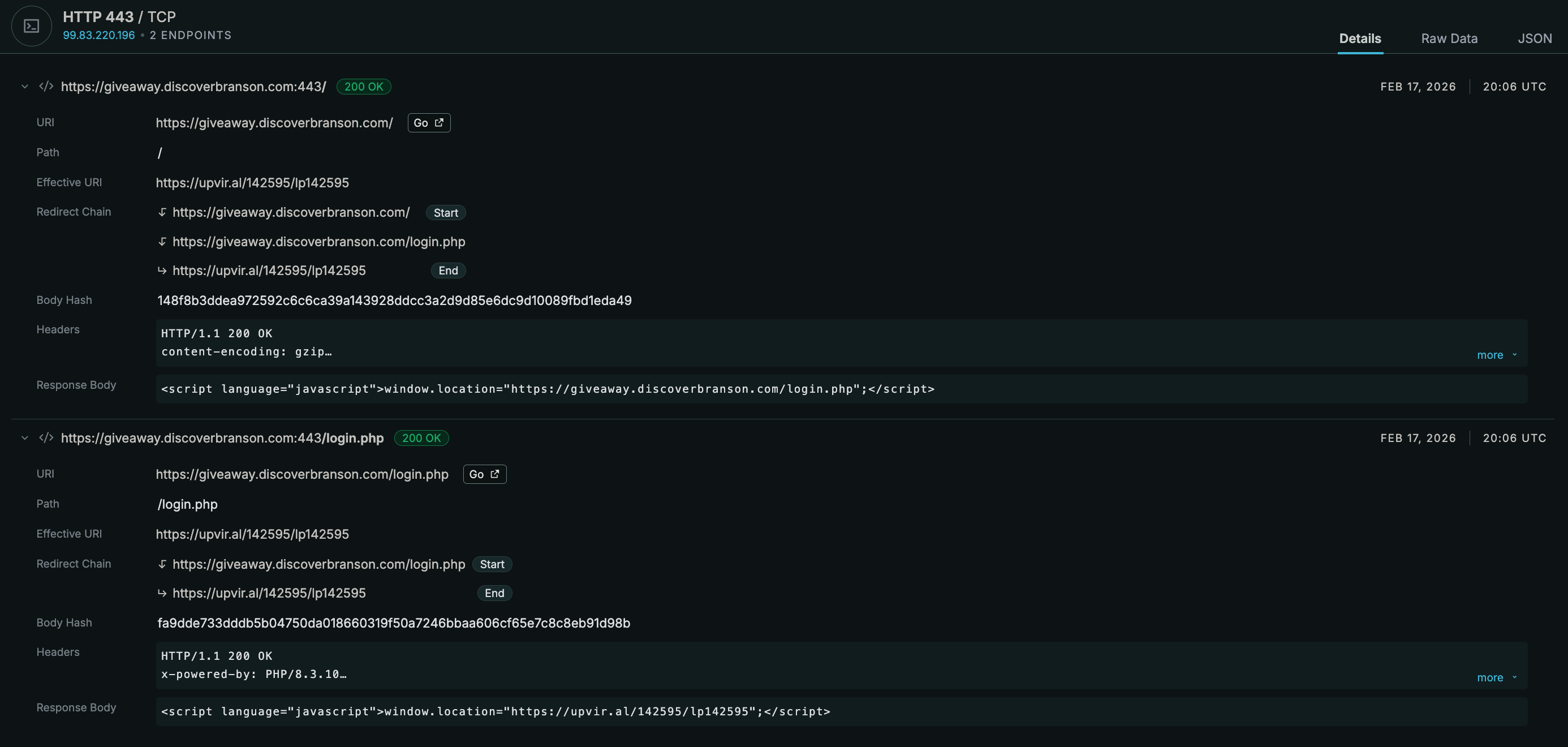
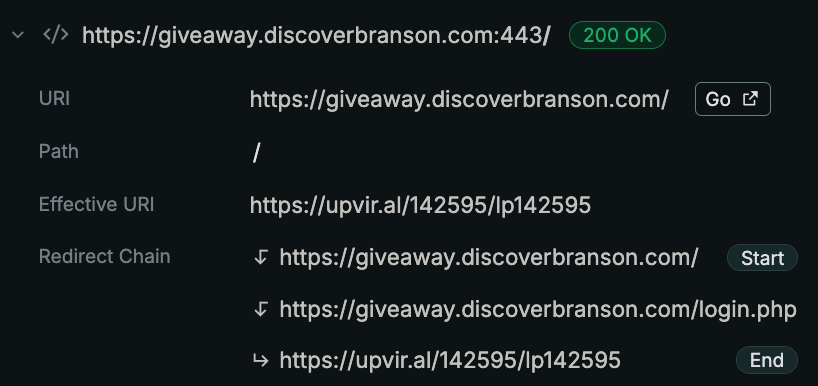
Summary
- The Censys Platform web UI has been updated to make the search bar the focus on the home page and improve navigation. See below for more details.
- Use the new Search History page in the Platform web UI to review your search activity over the past seven days.
- Added a protocol scanner for Gemini, an application-layer internet communication protocol for accessing remote documents.
- New fingerprints for TiVo DVRs, Gitea instances, Gogs instances, and a new ASM risk for exposed Ollama applications.
- One new Rapid Response advisory for Cisco Catalyst SD-WAN Controller and Manager Authentication Bypass [CVE-2026-20127].
Platform UI updates
The Censys Platform web UI has been updated to make the search bar the focus on the home page and improve navigation.
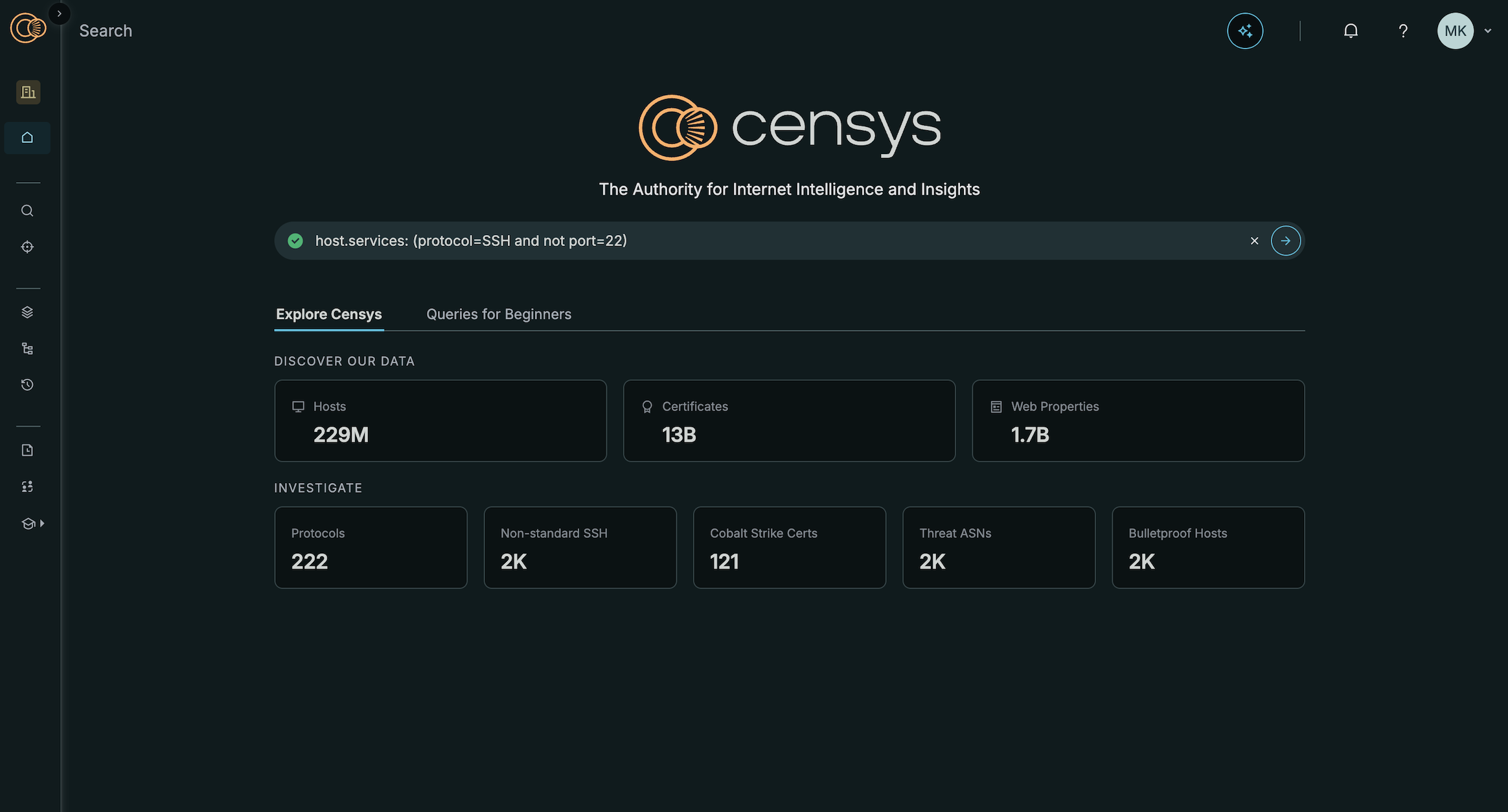
Left-side navigation panel
- The organization you are currently logged into is displayed in the top of the left-side nav bar. Switch to your Free account or another organization and access your organizational and personal settings from the organization drop-down.
- Open the account selector menu, select your account or organization, and click the credits section to go to the Credit Management page.
- Access to search and the dashboards for the Threat Hunting and Critical Infrastructure modules is now located in the Intelligence section of the left-side nav bar.
- The My Work section contains your collections, a link to the Investigation Manager, and your search history.
- The Resources section includes links to the Release Notes feed, the Censys Community. Additional resources like the Censys Academy and Data Definitions are nested under Learn in this section.
Alerts and Notifications
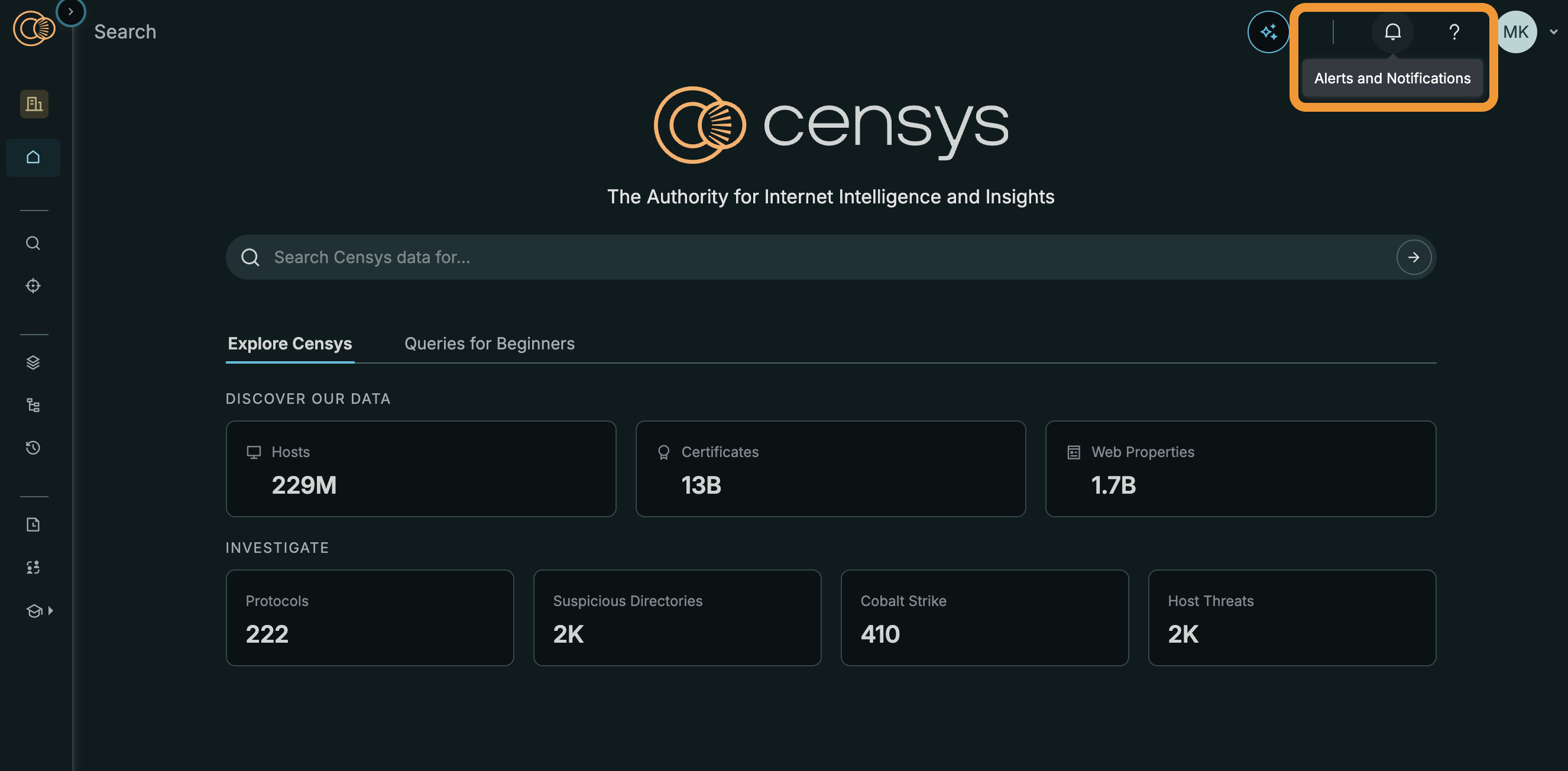
- Access webhook configuration by clicking the bell icon for Alerts and Notifications in the top-right corner.
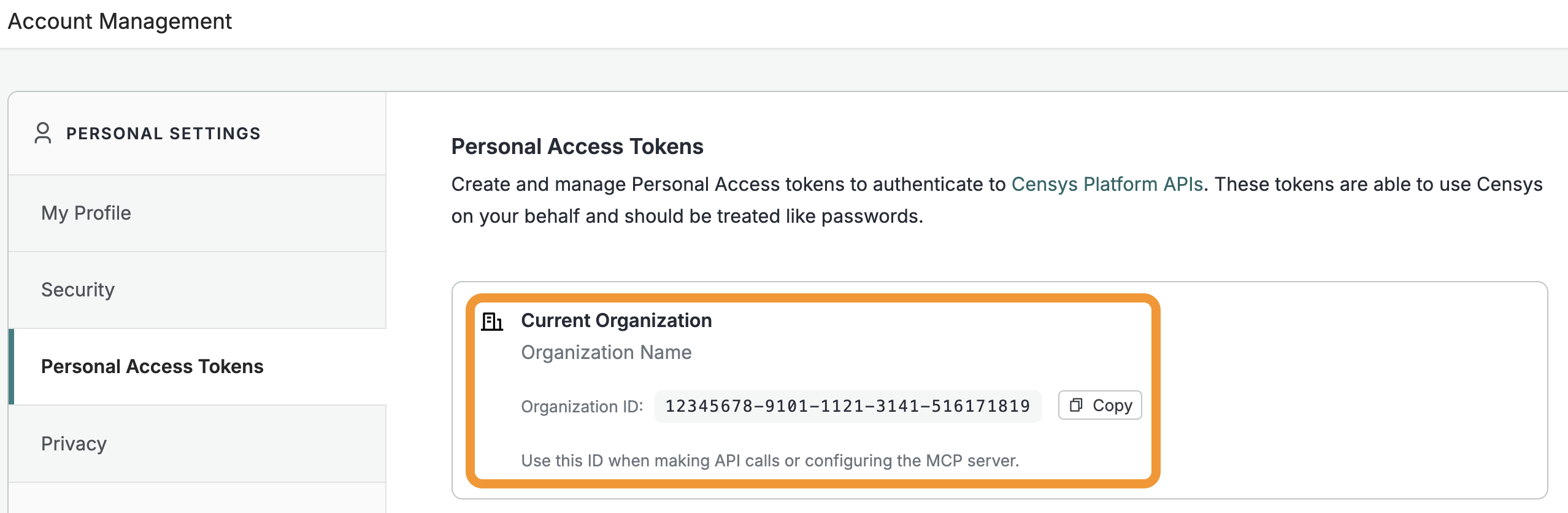
Personal Access Tokens, account management, and more
- Create and manage Personal Access Tokens (PATs), manage your account, and switch between light and dark mode using the profile menu in the top right corner.
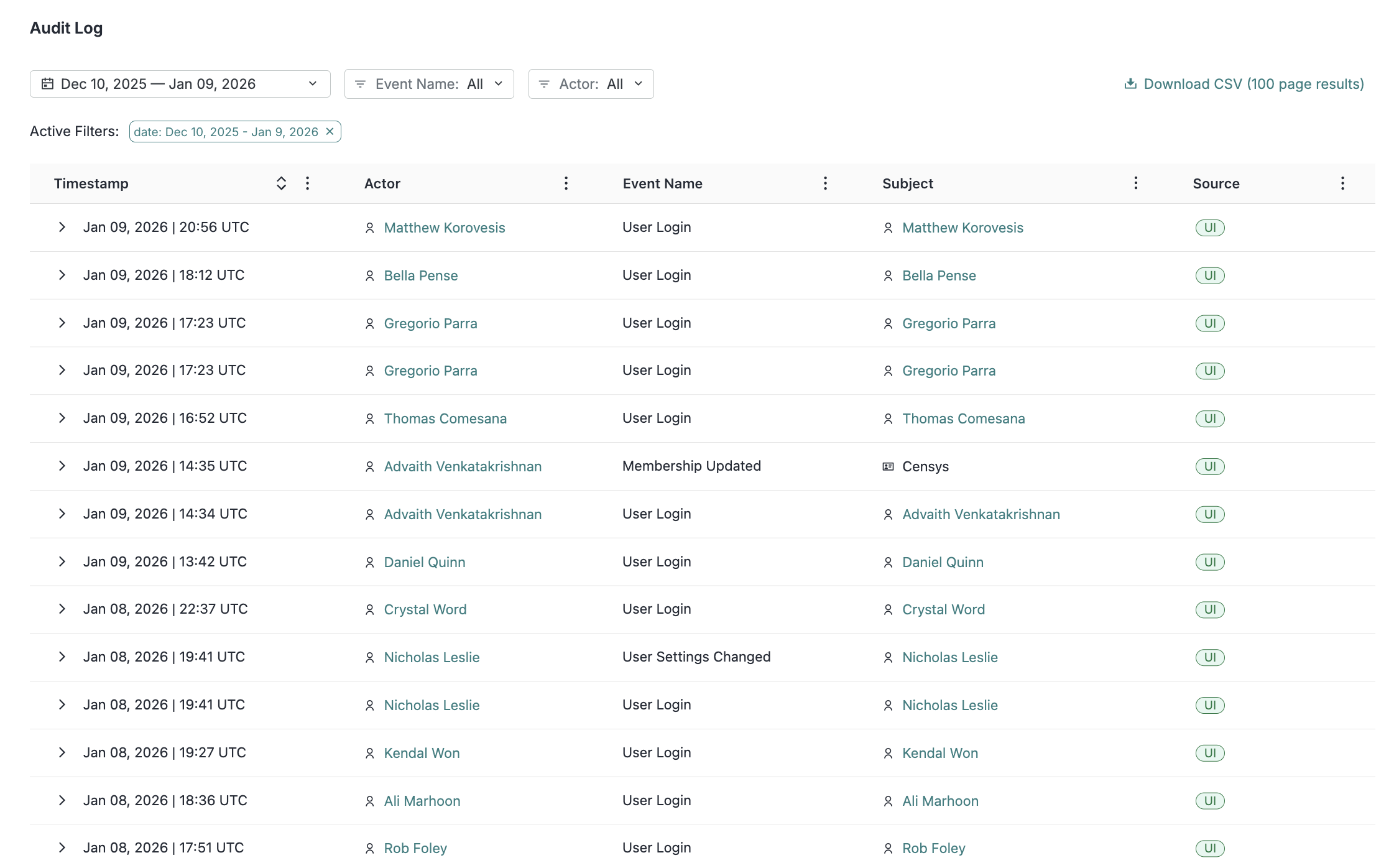
Platform Search History page
- The new Search History page in the Platform web console records all of the searches you ran in the Platform UI over the previous 7 days.
New protocols and application scanners
Added support for the following protocol.
| Protocol/application | Query | Data availability |
|---|---|---|
GEMINI | Platform query | Visible and searchable to all user tiers. |
New fingerprints
Added the following fingerprints.
Note that new ASM risk fingerprints may be disabled by default in your workspace. Reference your risk type configuration in the ASM web console to review new risk types.
Type | Name | Description | Query |
|---|---|---|---|
risk | Exposed Ollama Application | An exposed Ollama server. This application allows users to run and manage large language models (LLMs) locally. Exposing this service to the public internet can allow unauthorized access to AI models and computational resources. | ASM query: |
hardware | TiVo DVR | This is a TiVo digital video recorder (DVR). | Platform query |
software | Gitea | Gitea is a self-hosted Git service. | Platform query |
software | Gogs | Gogs is a self-hosted Git service. | Platform query |
Rapid Response
The Censys Rapid Response team published information about and queries for the following issue.
-
February 27 Advisory: Cisco Catalyst SD-WAN Controller and Manager Authentication Bypass [CVE-2026-20127]
- The following queries can be used to identify exposed SD-WAN Manager instances.