SAML Authentication
This document describes how to configure Security Assertion Markup Language (SAML) authentication for the Censys Platform. After you successfully configure SAML for the Platform, you must complete the configuration for your identity provider (IdP). Censys provides the information you need for your IdP.
SAML for single sign-on (SSO) allows you to use an IdP to manage authentication for organization members.
Prerequisites and notes
- Organizational Admins can create, edit, and delete SAML configurations.
- Organizations must be on the Enterprise tier to use SAML.
- Organizations can have a maximum of 10 SAML configurations.
- Each configuration can have a maximum of 10 domains.
Configure SAML authentication in Censys
-
Go to My Account > Authentication.
-
Click Set up configuration.
-
(Optional) Name your SAML configuration in the Configuration Name field.

-
(Optional) Enable Sign Authentication Requests. This setting defaults to disabled.
NoteSome IdPs require this - you can enable this to increase security. If enabled, Censys digitally signs the SAML authentication request before sending it to the IdP.
-
In the Identity Provider Information section, you can enter your IdP's Metadata URL and click Populate to automatically populate the required IdP information. You can manually enter this information to the right.
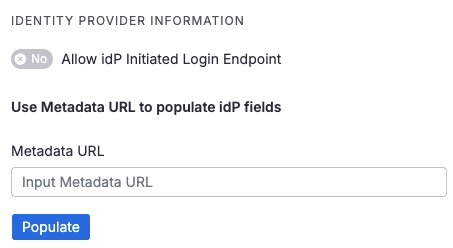
-
(Optional) Enable Allow IdP-Initiated Login Endpoint. This setting defaults to disabled. Enable this to allow users to log in directly from the IdP portal.
-
Click Save Configuration.
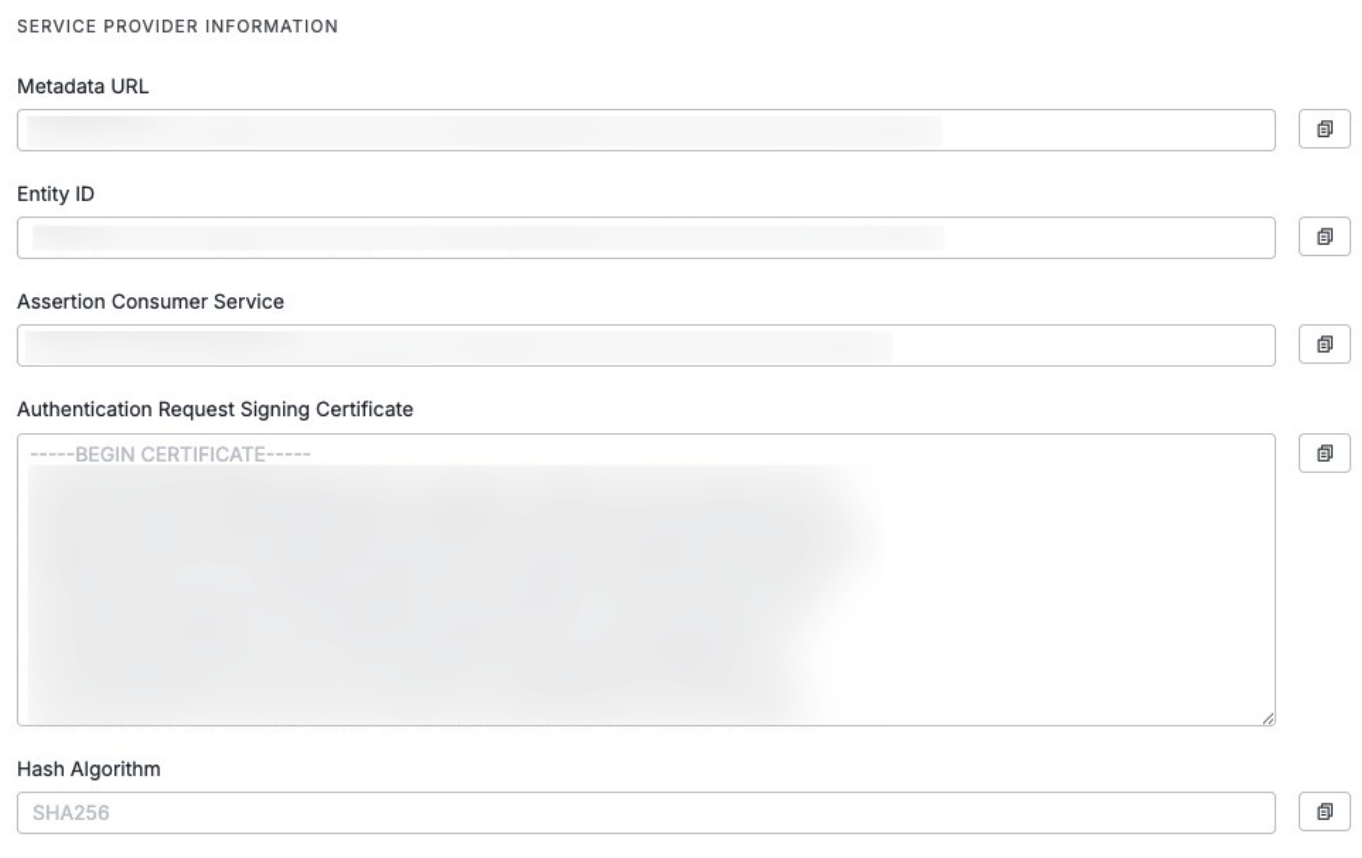
Service provider information
Service Provider Information contains the details your IdP needs to complete the SAML configuration. Click the icon to the right to copy the value.
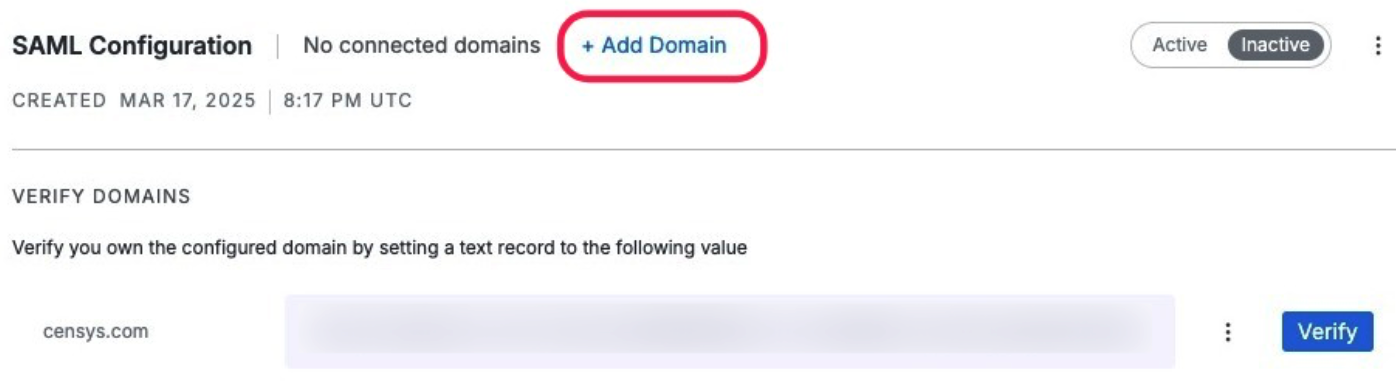
Add domain
After you complete the SAML configuration for Censys, you now must add and verify your domain.
NoteCensys periodically verifies that the TXT record is still present in your domain’s DNS. This ensures that your organization maintains control of the domain.
-
Click Add Domain.
-
Enter your domain in the Domain Name field and click Input.
-
The field then populates with the Censys Domain Verification name.
-
Add the Censys Domain Verification as a TXT record in your domain’s DNS settings. This TXT record is used to verify that you control the domain.
-
Click Verify to the right of the value. If you submitted a valid domain, Verified is displayed.

TipIf you receive an error, verify that you entered the correct value into your DNS settings and try again.
Next steps
Now that you configured SAML for Censys, use the information provided in the Service Provider Information section to complete the configuration in your IdP.
Attributes
Censys expects the following attributes from the IdP:
Censys User Profile Attributes | Accepted IdP Attributes |
|---|---|
| |
given or first name |
|
last name |
|
organization (optional) |
|
Activate SAML
After you successfully configure SAML in your IdP, you can activate your SAML configurations in Censys. Organizations can have multiple active SAML configurations with multiple domains.
Follow the steps below to activate a SAML Configuration:
-
Go to My Account > Authentication.
-
Locate the SAML config you want to activate and toggle the Active/Inactive boolean.
-
The SAML configuration is now Active.
Post-activation behavior
- When a user logs in, they use the SAML configuration that supports the domain they are logging in from.
- After SAML is activated, all users whose email addresses match a verified domain are redirected to the configured (IdP) during log in.
Set up non-SAML admin
Organizations can set up a non-SAML admin user (a user on a domain not configured for SAML) to avoid getting locked out of the account while testing.
To avoid getting locked out while testing SAML:
- Set up a backup admin account using an email address on a domain not configured for SAML.
- This non-SAML admin account allows you to bypass SAML login if configuration issues occur.
If you are unable to create a backup admin account, you can open an incognito/in-private browser and log in to test the login.
Multiple configurations and domains
You can set up multiple SAML configurations for an organization, but only one SAML configuration can be active for a given domain. Additionally, a SAML configuration can also have multiple domains.
You cannot split users with the same email domain across two different SAML configurations, you can have different SAML configurations for different email domains.
For example, if you want to set up SAML for users across the example domains alpha.io, beta.io, and gamma.io, you could do any of the following:
- Set up one SAML configuration for all three domains.
- Set up three different SAML configurations (one for each domain).
- A combination of the options described above.
Updated about 1 month ago
