Understand and Investigate Your Attack Surface
Censys uses its industry-leading, Internet-wide data sets and research-backed knowledge about asset relationships to present a comprehensive public inventory that belongs to your organization.
The Censys Attack Surface Management (ASM) attribution process begins with seed data, which are assets owned and managed by your organization. When the evidence for a relationship between a parent node (a member of the tree) and a potential child node crosses a defined confidence threshold, branches to new assets are created.
The discovery path can serve as a starting point and guide for your own investigation as you discover and monitor your attack surface.
Seeds
Many seeds come from public Internet artifact repositories such as WHOIS and DNS. These are often traditional asset types such as:
- Autonomous Systems
- Netblocks
- Domain names
Your organization can also seed the platform with more ephemeral assets from public Cloud Server Provider accounts using a Censys Cloud Connector to add asset types such as:
- Storage buckets
- Dynamic cloud IP addresses
- Subdomains
Discovery Path layout
Each asset type can be discovered and attributed from a variety of parent types. Paths can vary in length from one, which means the asset is a seed.
In the ASM web app, Censys shows a discovery path from your seed data to each asset that is attributed to your organization. A discovery path is present on every asset details page that shows you the path Censys Attack Surface Management took to the asset you’re viewing.
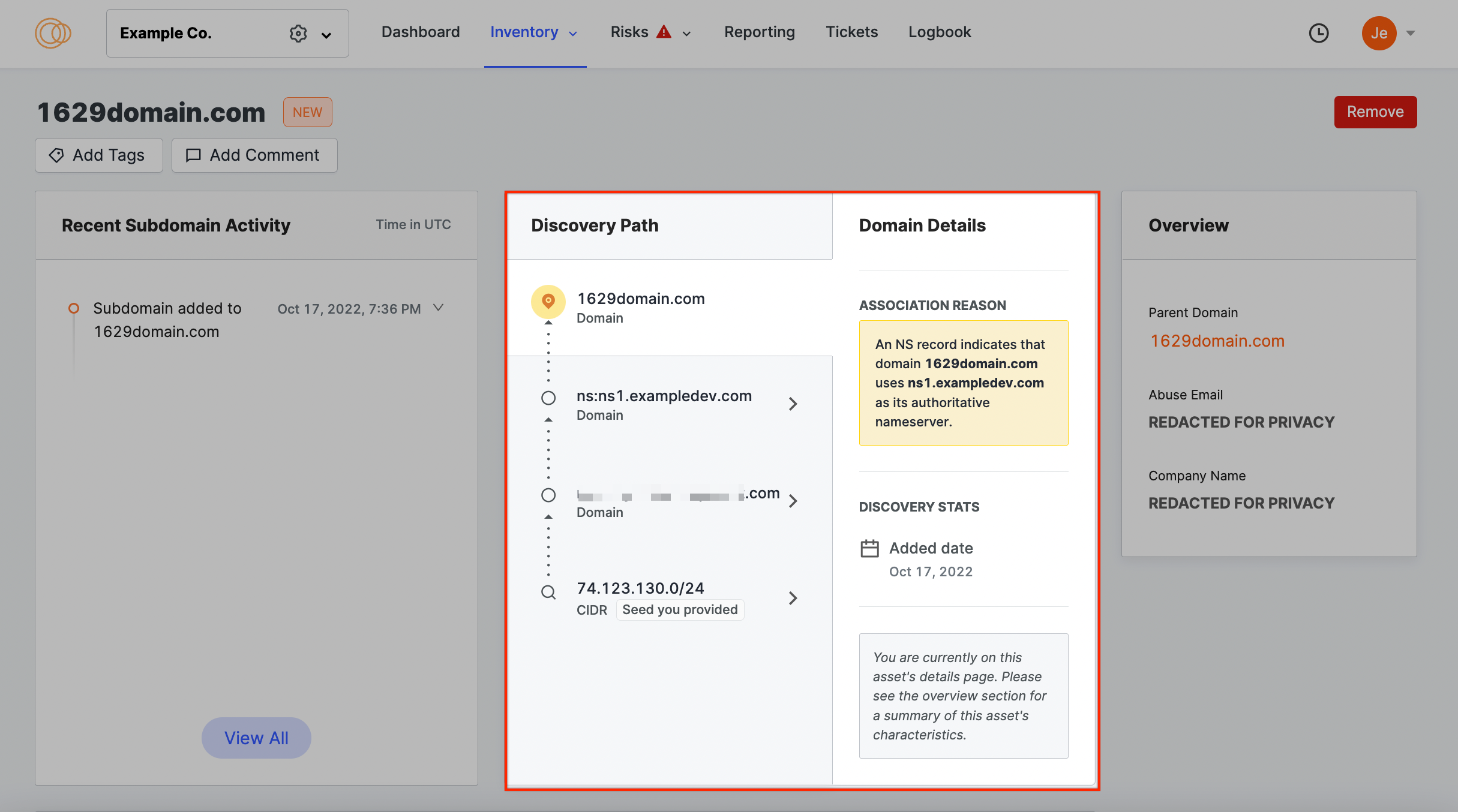
The relationships between parent nodes and child nodes are listed below, grouped by the type of asset that is added.
Host Discovery Paths
The paths that end in a host can be short or long. If your organization is large enough to have allocated sections of IPv4 address space (for example, netblocks or ASes), these hosts are almost permanently attributed to you, and discovery paths are rather short.
In other cases, hosts are attributed via DNS records or because they are presenting assets (such as certificates) attributed to you.
-
ASN → IP network
The set of sequential IPv4 addresses (indicated by the prefix) is within an Autonomous System belonging to your organization.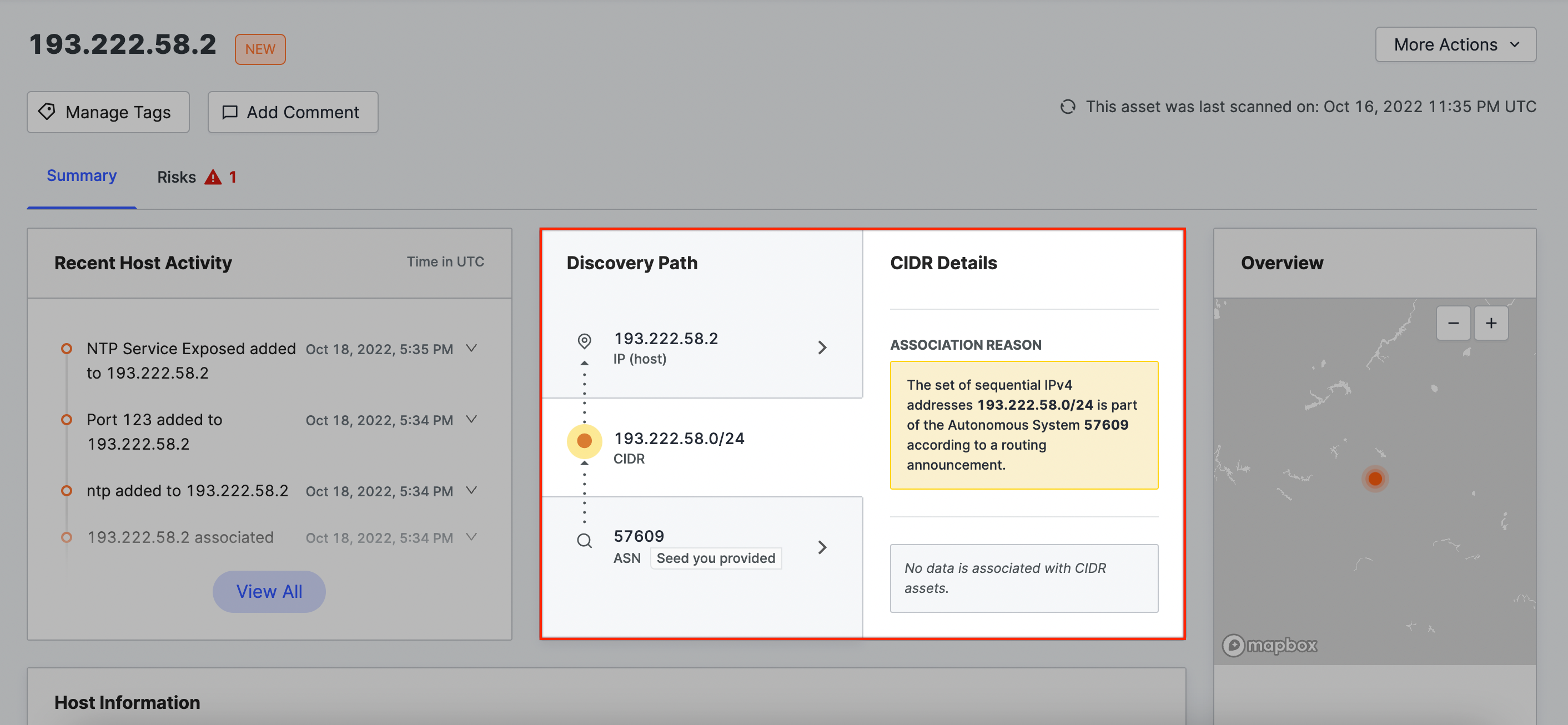
-
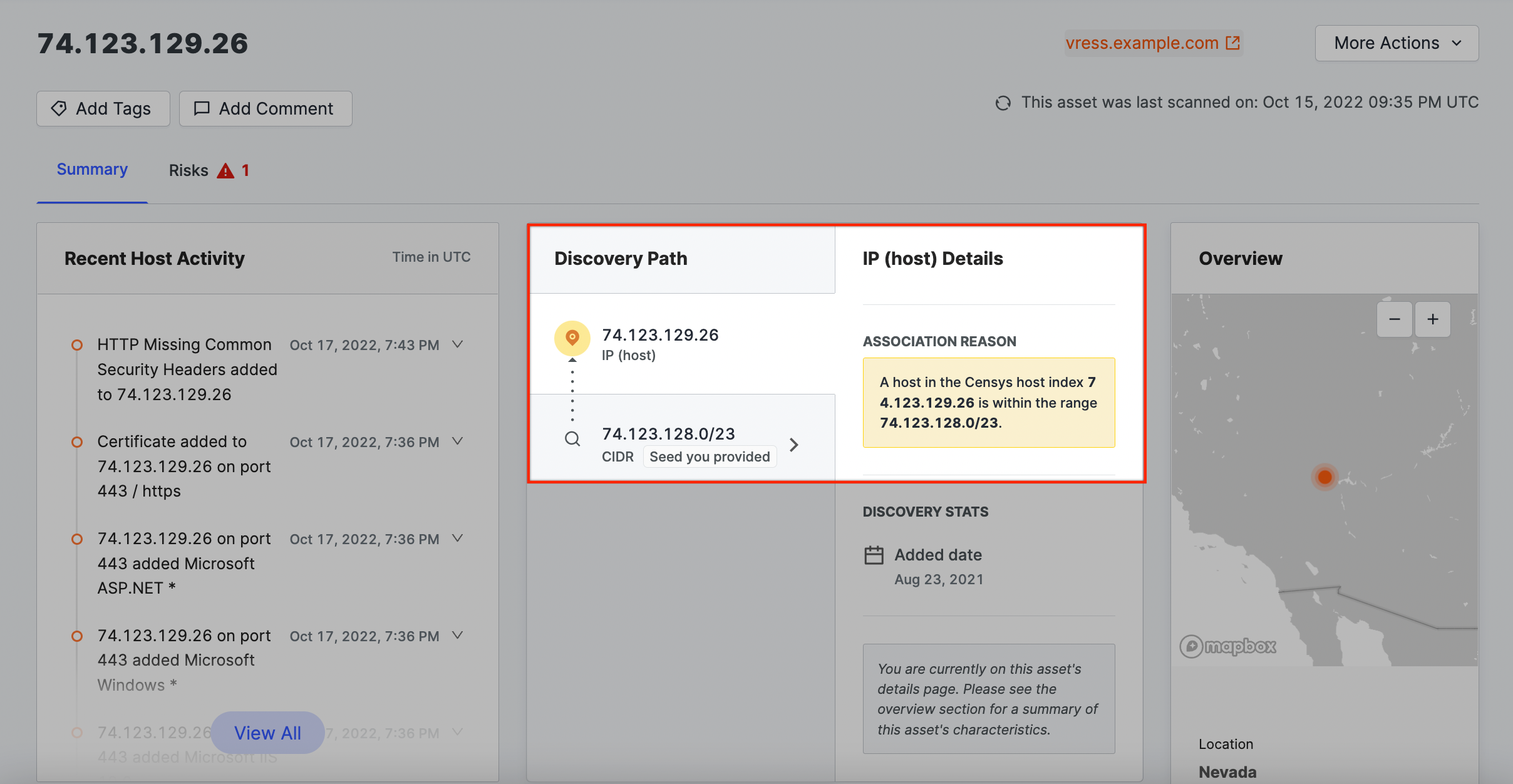
IP network → IP address
The IPv4 address is within an IP range belonging to your organization.
-
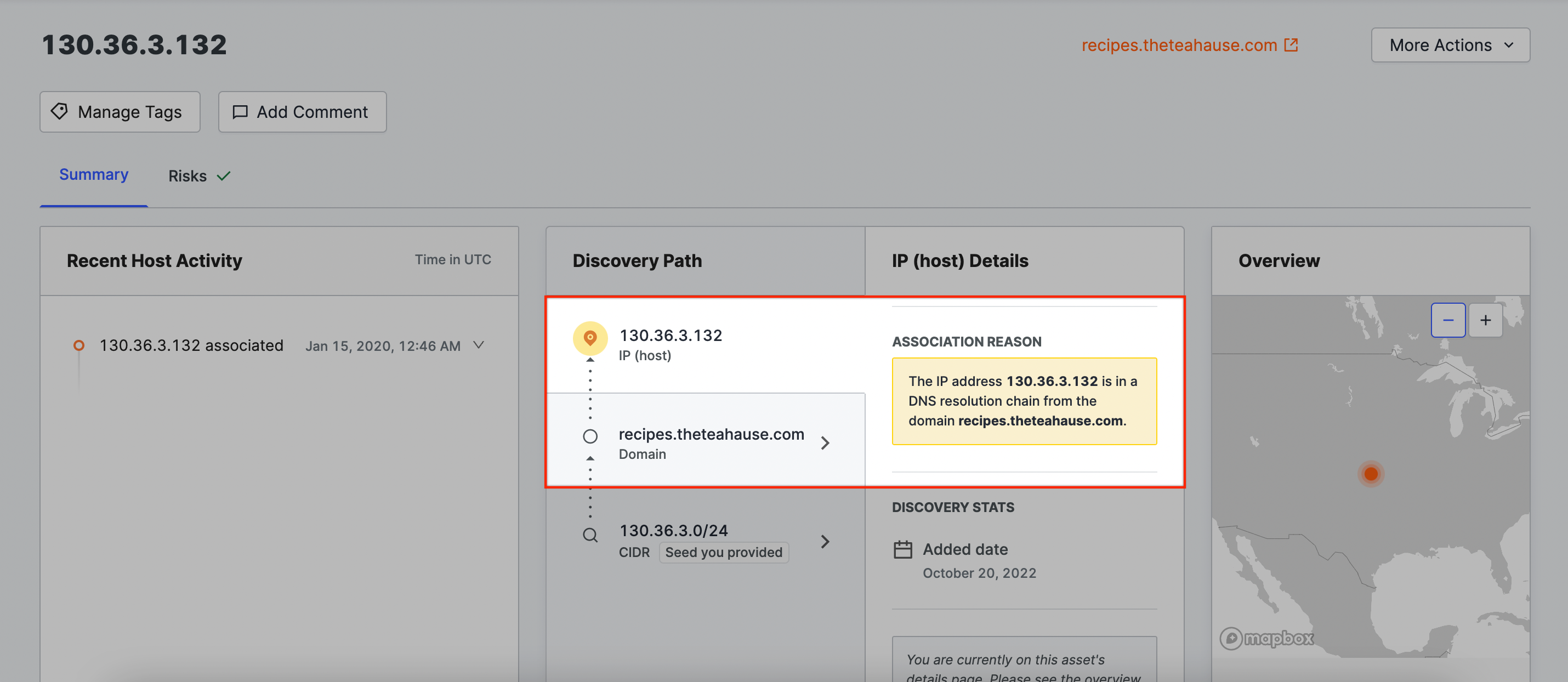
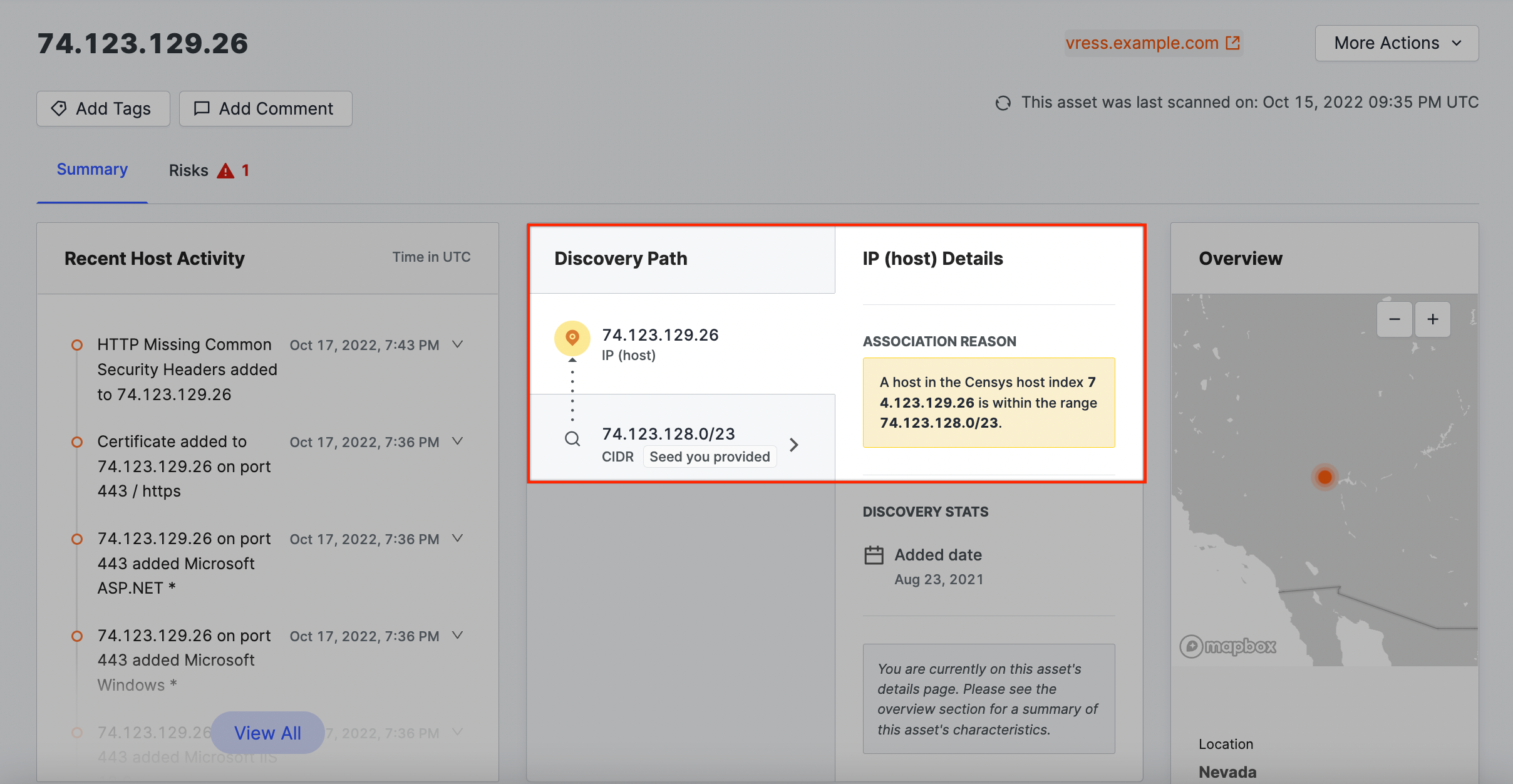
Domain name → IP address
The IP address is present in a DNS A Record with a domain name belonging to your organization.
-
Certificate → IP address
The host presented a certificate belonging to your organization when a Censys scanner initiated a TLS handshake.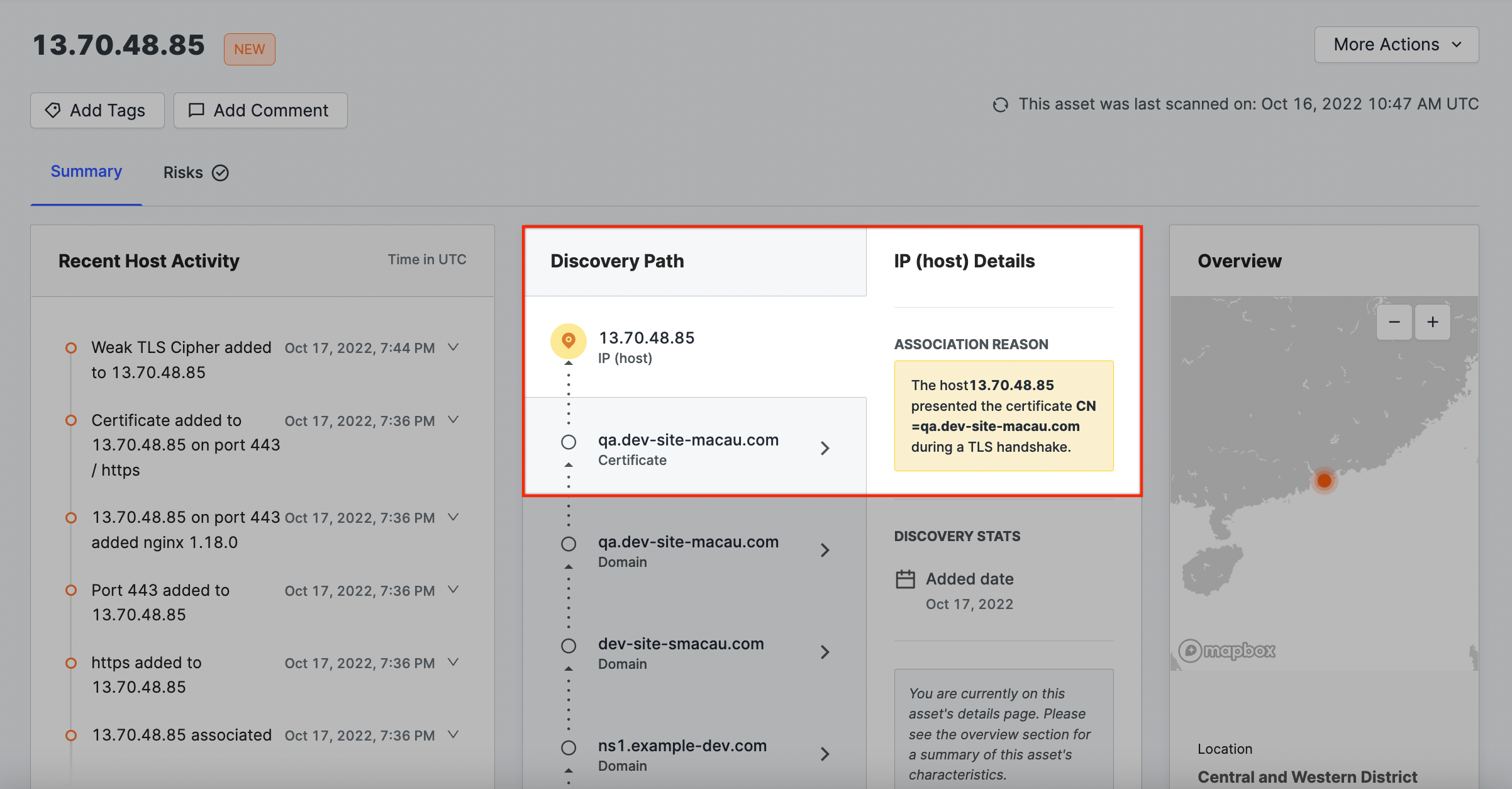
Certificate Discovery Paths
Certificates are not seeds. They are always found because of the names they contain or because of the hosts that present them.
-
Domain name → Certificate
The certificate’s name section contains the domain name belonging to your organization.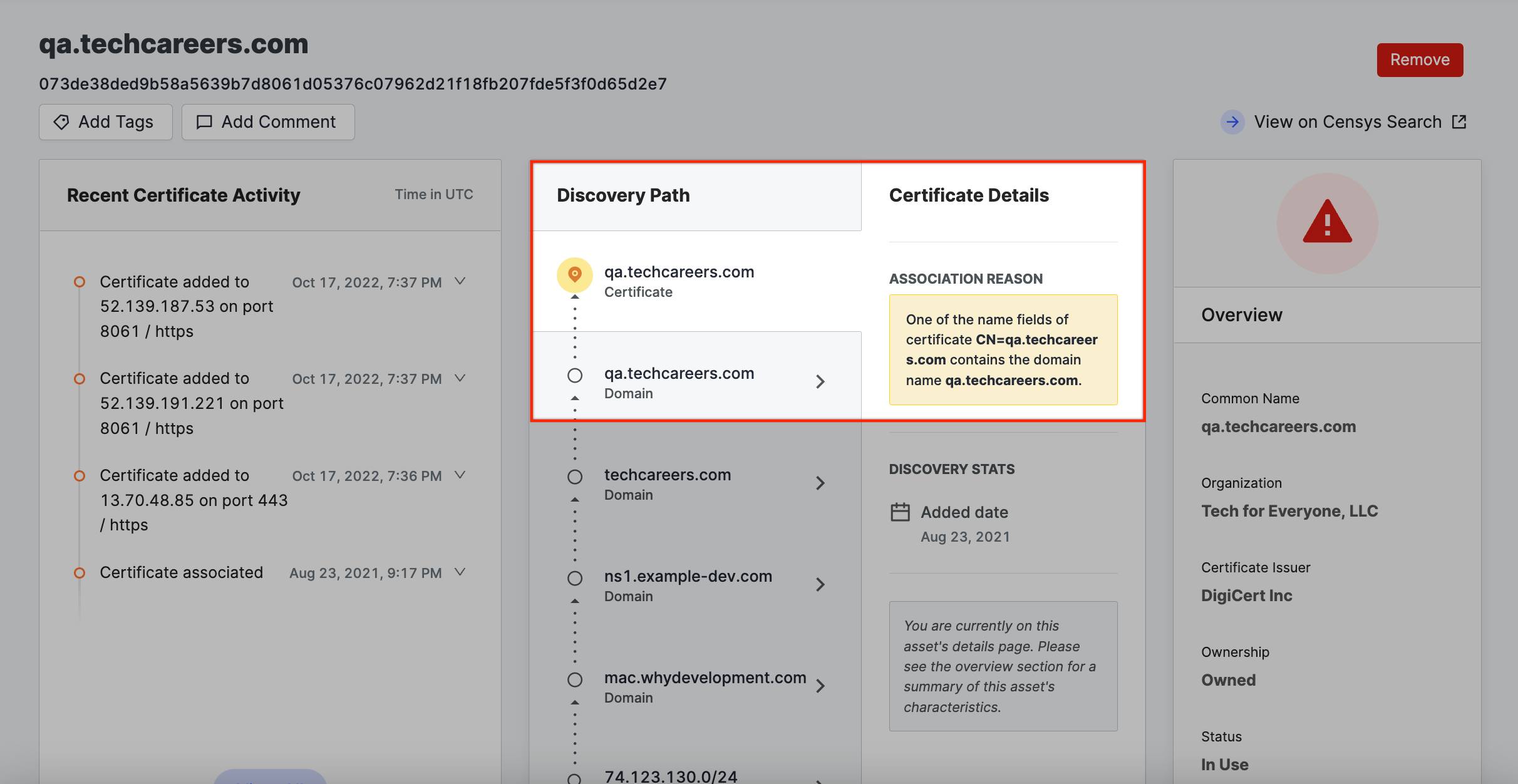
-
IP address → Certificate
The certificate was presented by a host in your attack surface when a Censys scanner initiated a TLS handshake.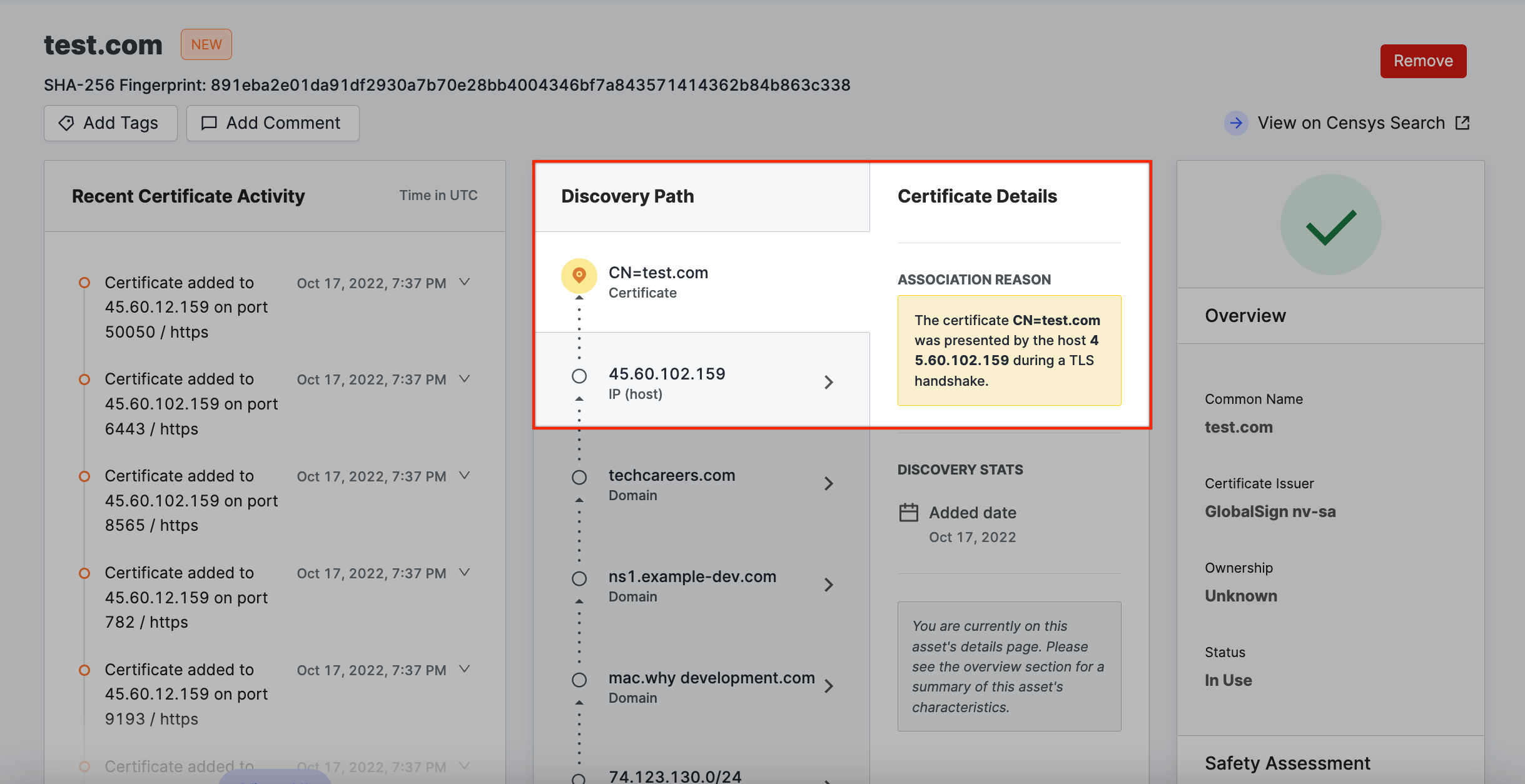
NoteIf your organization doesn't own all of the names listed on a certificate, an ownership field indicates unknown, and the certificate is not used to discover additional assets.
Domain Discovery Paths
While the natural hierarchy of the Domain Name System often connects domain and subdomain paths, the familial relationship of name servers can also prominently feature in these paths.
-
Domain name (A) → Domain name (B)
Domain name B is a subdomain of domain name A, which belongs to your organization.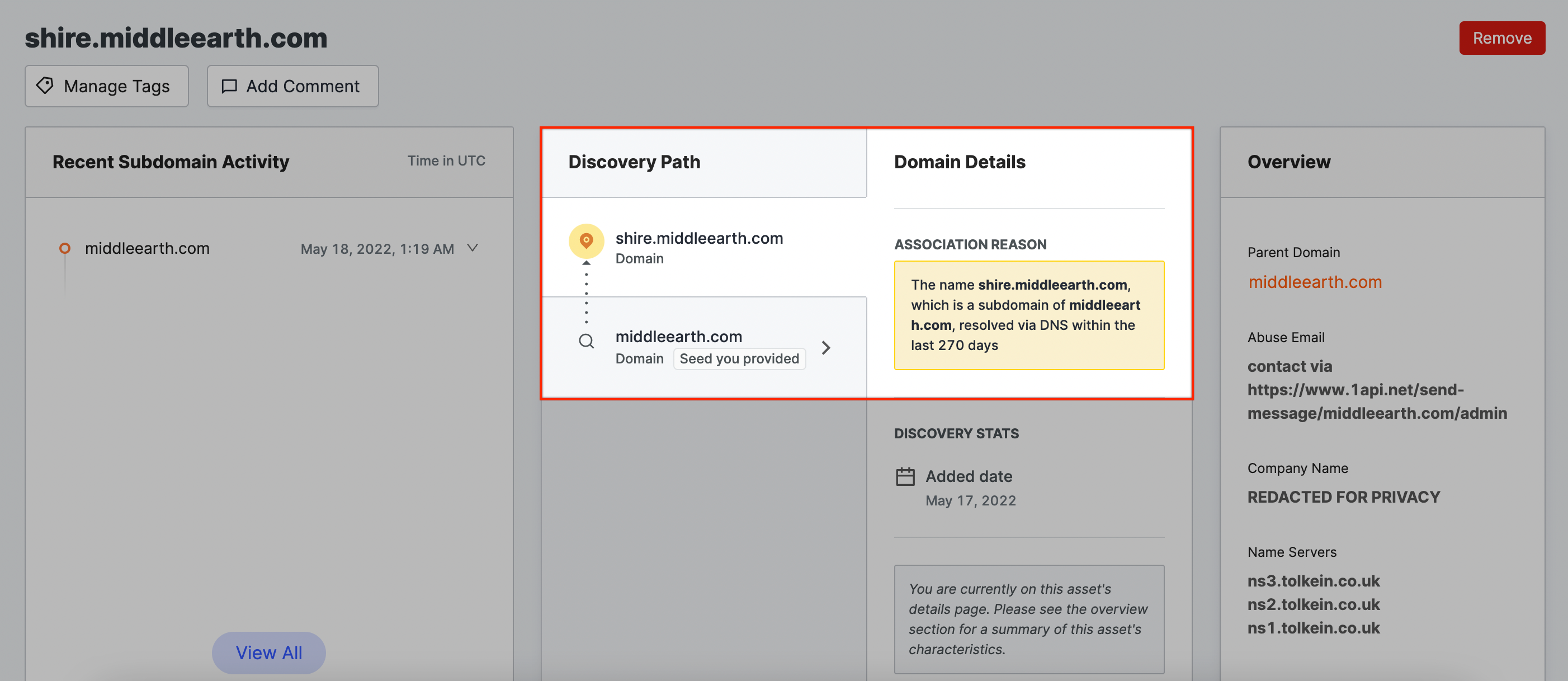
-
IP netblock → Domain name
The domain name was seen to resolve to an IP address in an IP Block belonging to your organization in the past 270 days.
-
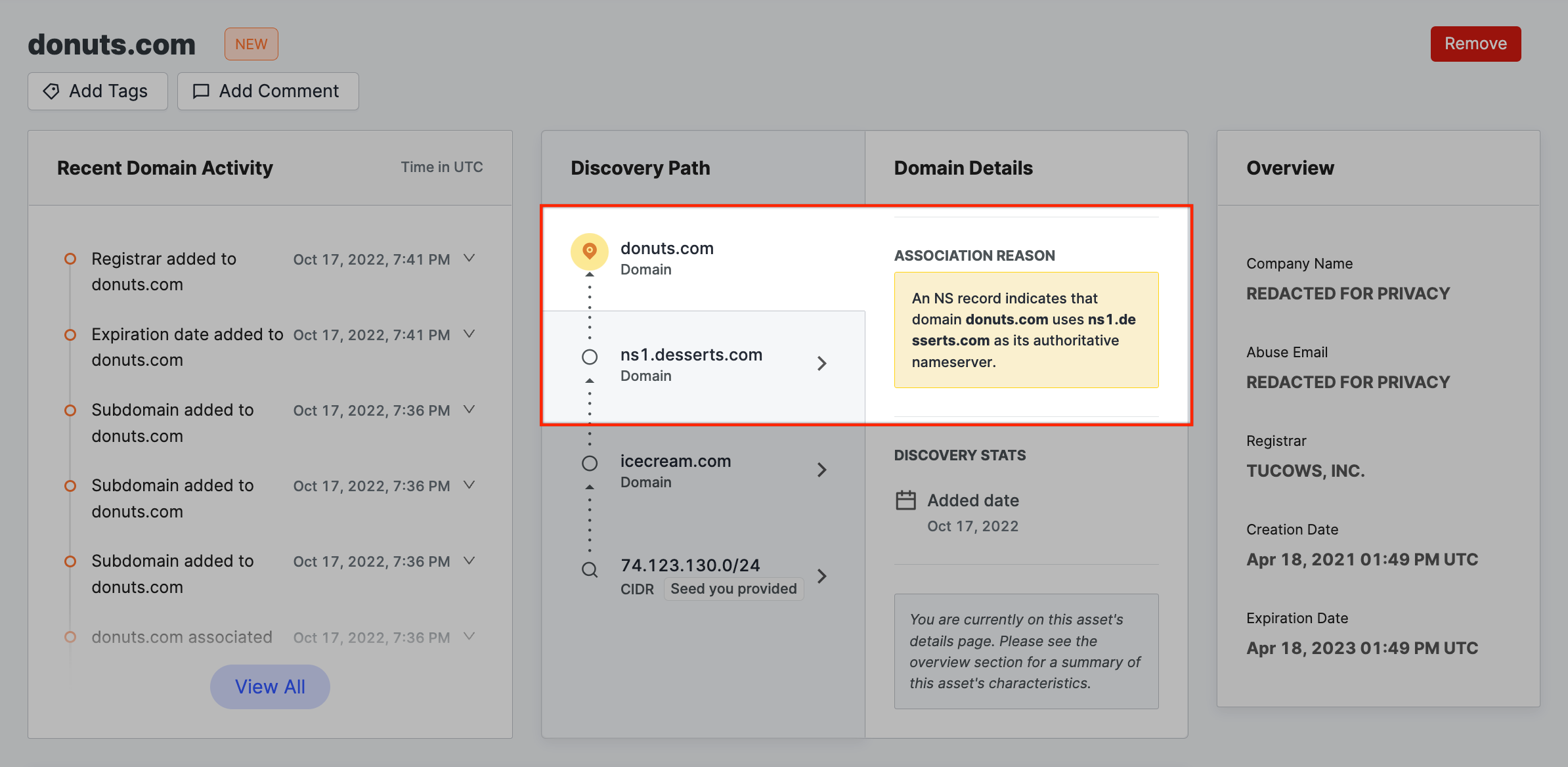
Domain → Name Server
In the past 270 days, a (non-shared) name server with your organization's domain has appeared in an NS record.
-
Name server → Domain name
A domain’s NS record shows that it has used a name server belonging to your organization for the past 270 days.
Correcting incorrectly attributed assets
If you see an IP address, TLS certificate, or domain name that you are certain does not belong to you, you can exclude it from your inventory.
Updated 28 days ago
