Hosts
Hosts are a foundational concept in Internet security and the Censys Attack Surface Management (ASM) platform.
Formal definition: A network host is a computer or other device connected to a computer network. It may act as a server, offering information resources, services, and applications to users or other hosts on the network. Hosts are assigned at least one network address.
Informal Censys definition: A computer or device that’s connected to the Internet, located at and identified by an IP address.
Hosts list
Go to the ASM web console and click Inventory > Hosts.
The Hosts list page shows all of your organization’s hosts, which are indexed by Asset ID.
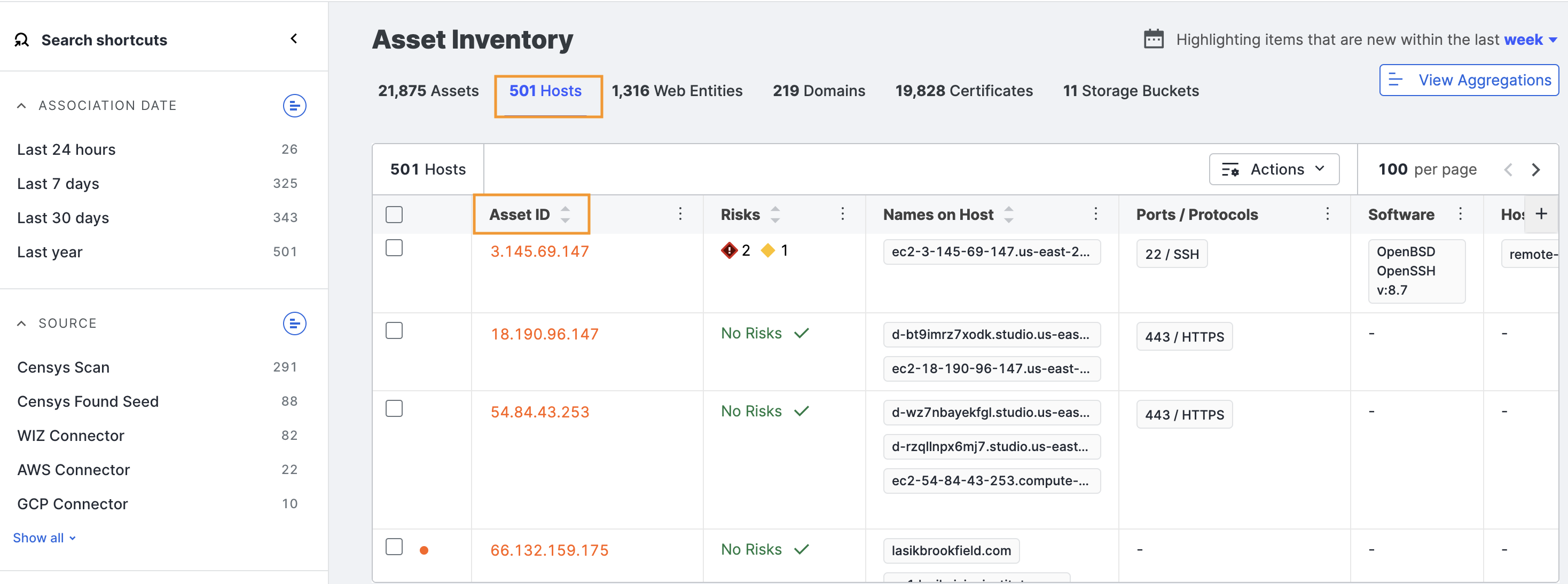
Other columns in this view include:
- Risks: A count of any risks detected on an asset, categorized by their severity.
- Name(s) on Host: The domain and subdomain names associated with the host, obtained through DNS lookups.
- Ports/Protocols: The numeric identifiers for the open ports on the host and the application-layer protocols being used by those ports.
- Software: The names and versions of applications running on the host, as reported by the services running on it.
- Host Labels: Descriptive tags or identifiers assigned to a host to categorize it based on specific criteria. Examples include
remote-access,database,login-page,network-administration, andfile-sharing. - Country: The geographic location (country) associated with the host.
- Tags: Custom labels or categories applied to an asset by the user or organization for easier identification and filtering.
- Added: The date when an asset was associated with your organization.
- Cloud: The name of the hosting provider or cloud service where the asset is hosted, such as AWS, Azure, or GCP.
- Account ID: A unique identifier for the cloud account associated with the asset.
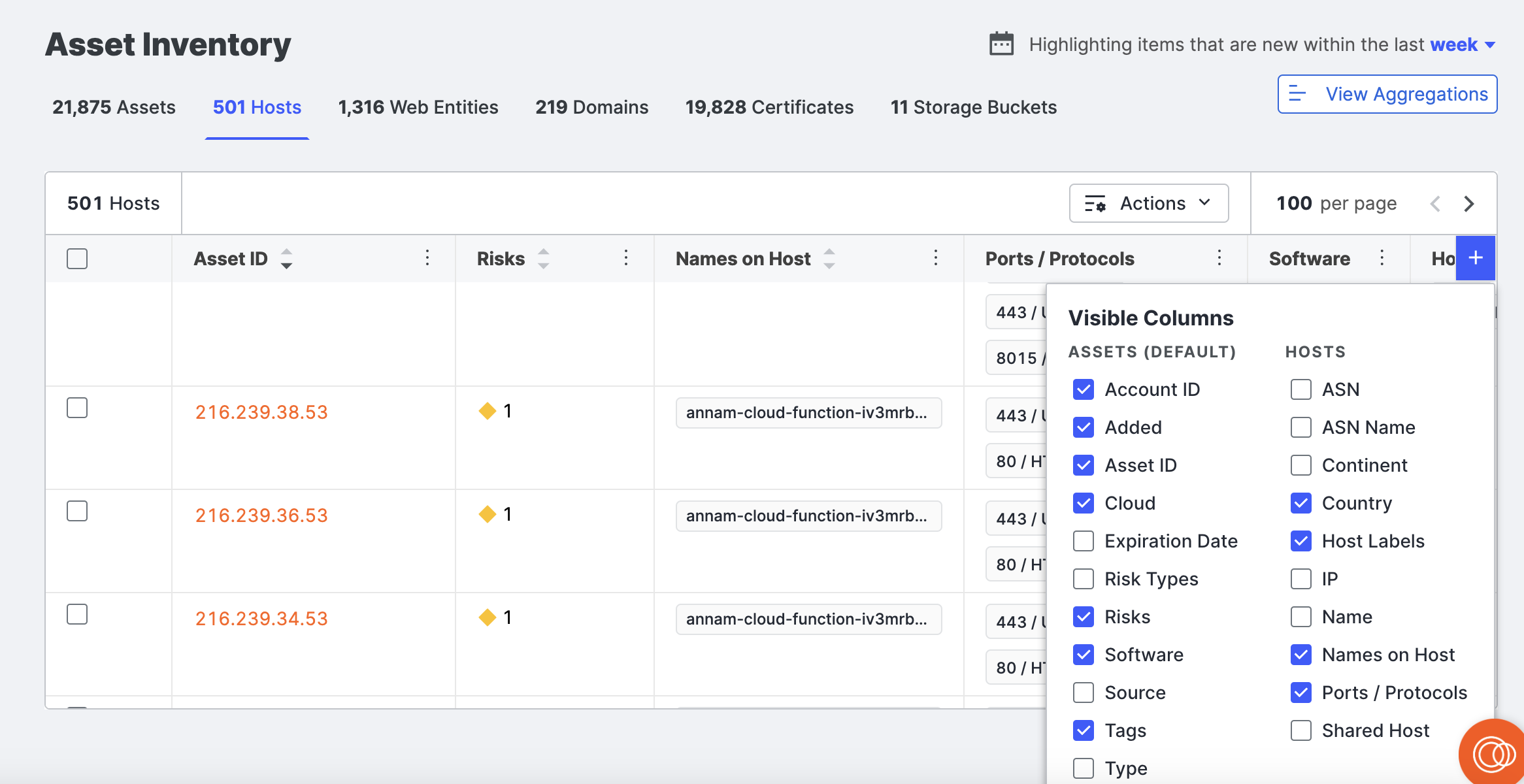
Column selection
Click the plus icon ( ) above the table to open additional columns with more information about your hosts.
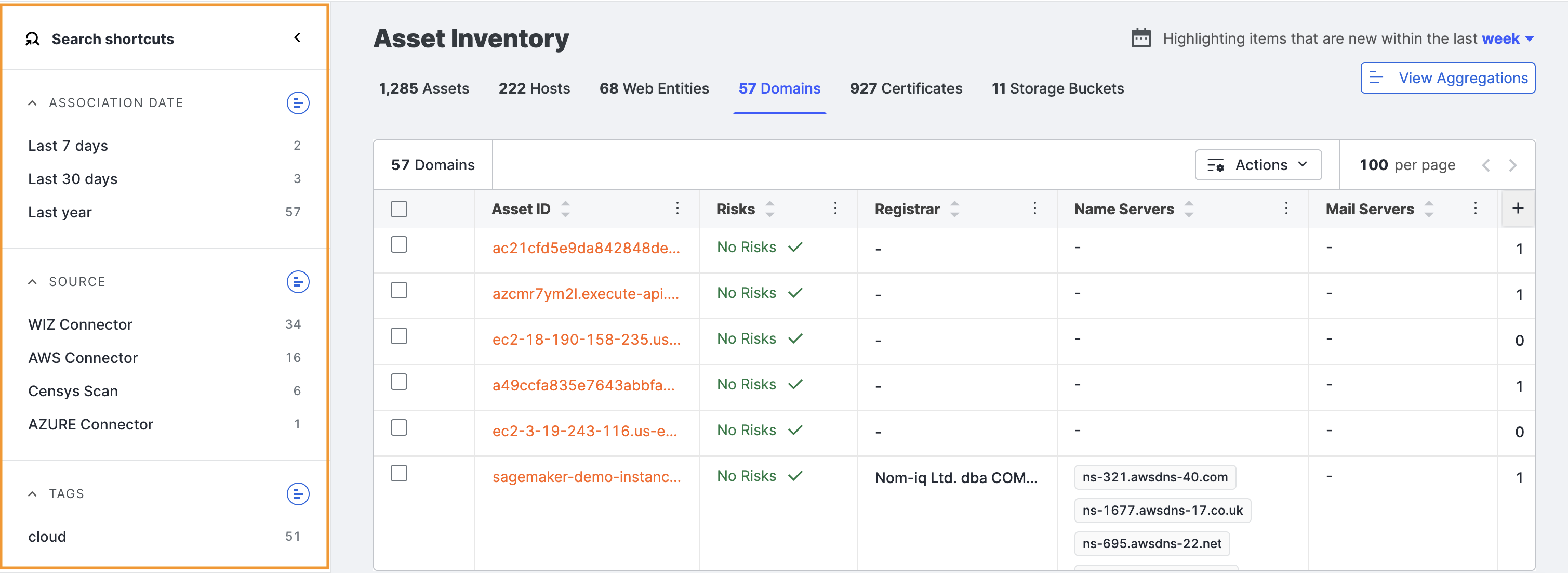
Search shortcuts
This section provides quick access to common asset attributes. By clicking on specific field values, you can easily refine searches. This will build your query, which can then be saved.
Download hosts data
You can download the hosts list as a comma-separated value (CSV) for use in other products and workflows.
Click Actions > Download CSV.
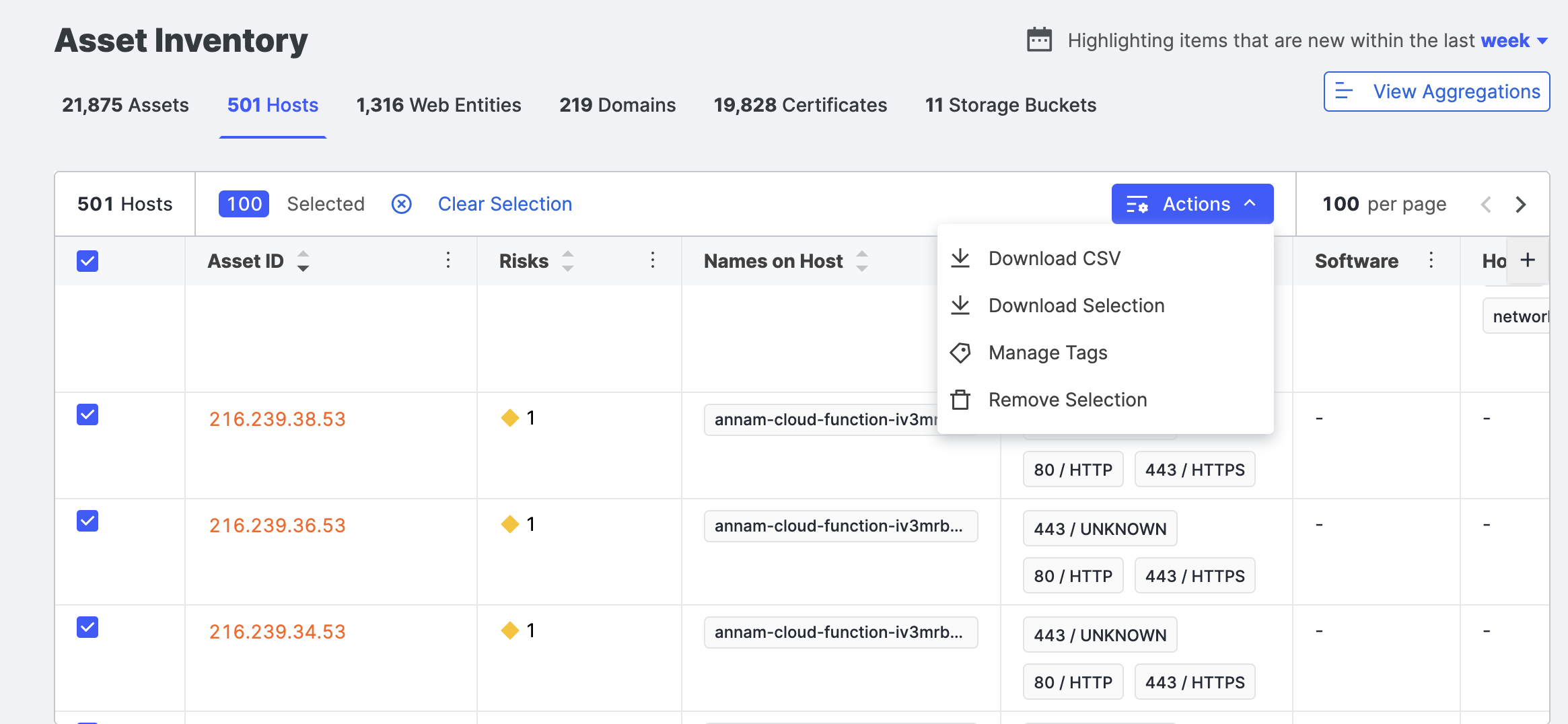
The default filename is {timestamp}_{customerName}_HostByIpExport.csv. The columns in the CSV file reflect the columns shown in the table when exported.
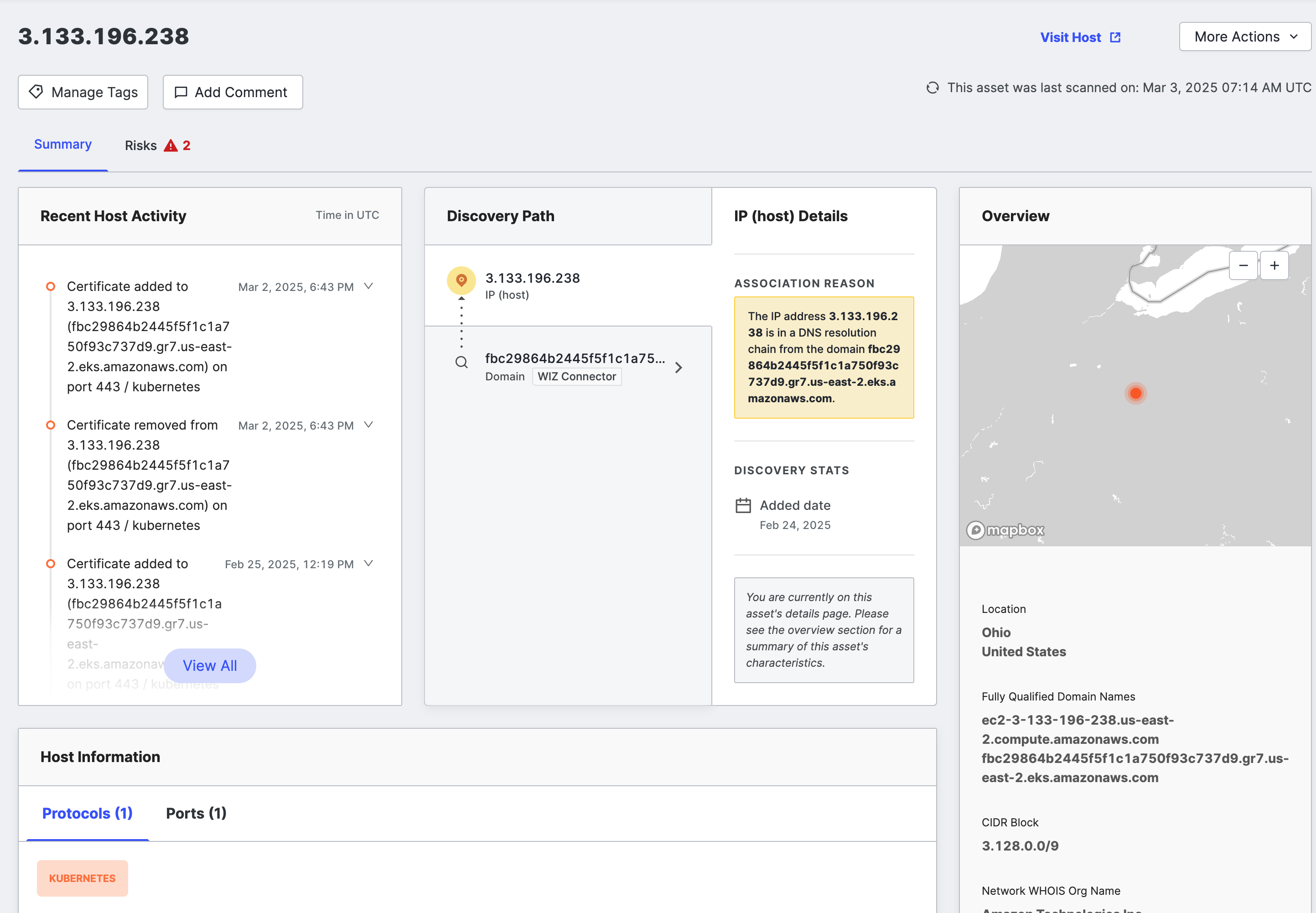
Host details
Click the linked Asset ID to see a hosts detail page with additional information.
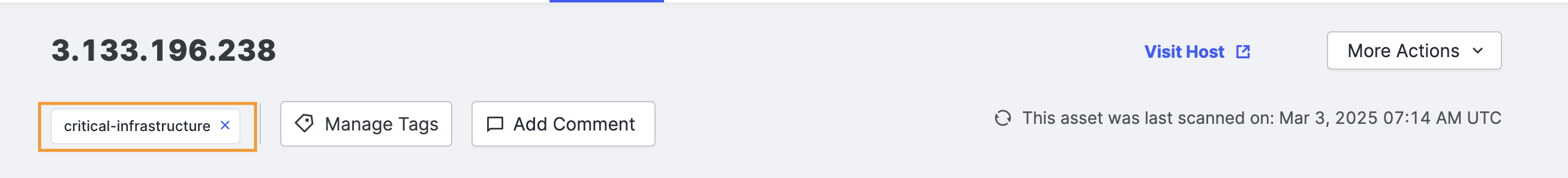
Manage Tags
The page title is the host’s Asset ID. Any tags applied to the host are shown underneath, and an option removes them.
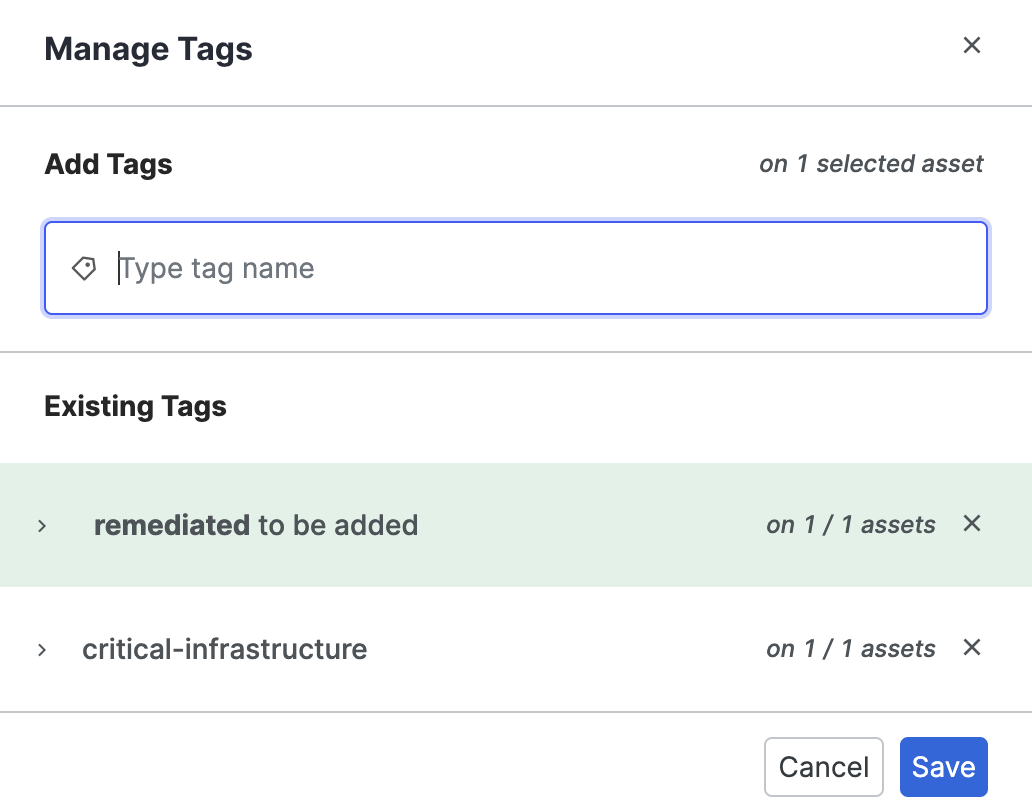
Click Manage Tags to add a new tag or edit a current one. In the dialog box, type the name of the new tag, or select from existing tags in the list.
Summary tab
The Summary tab shows recent activity related to this host, taken from the logbook. This activity includes events such as new open ports, certificates the host presented during any TLS handshakes with Censys, and software and vulnerability events.
Click Load More at the bottom to expand the card and view all events related to this host since Censys added it to your organization.
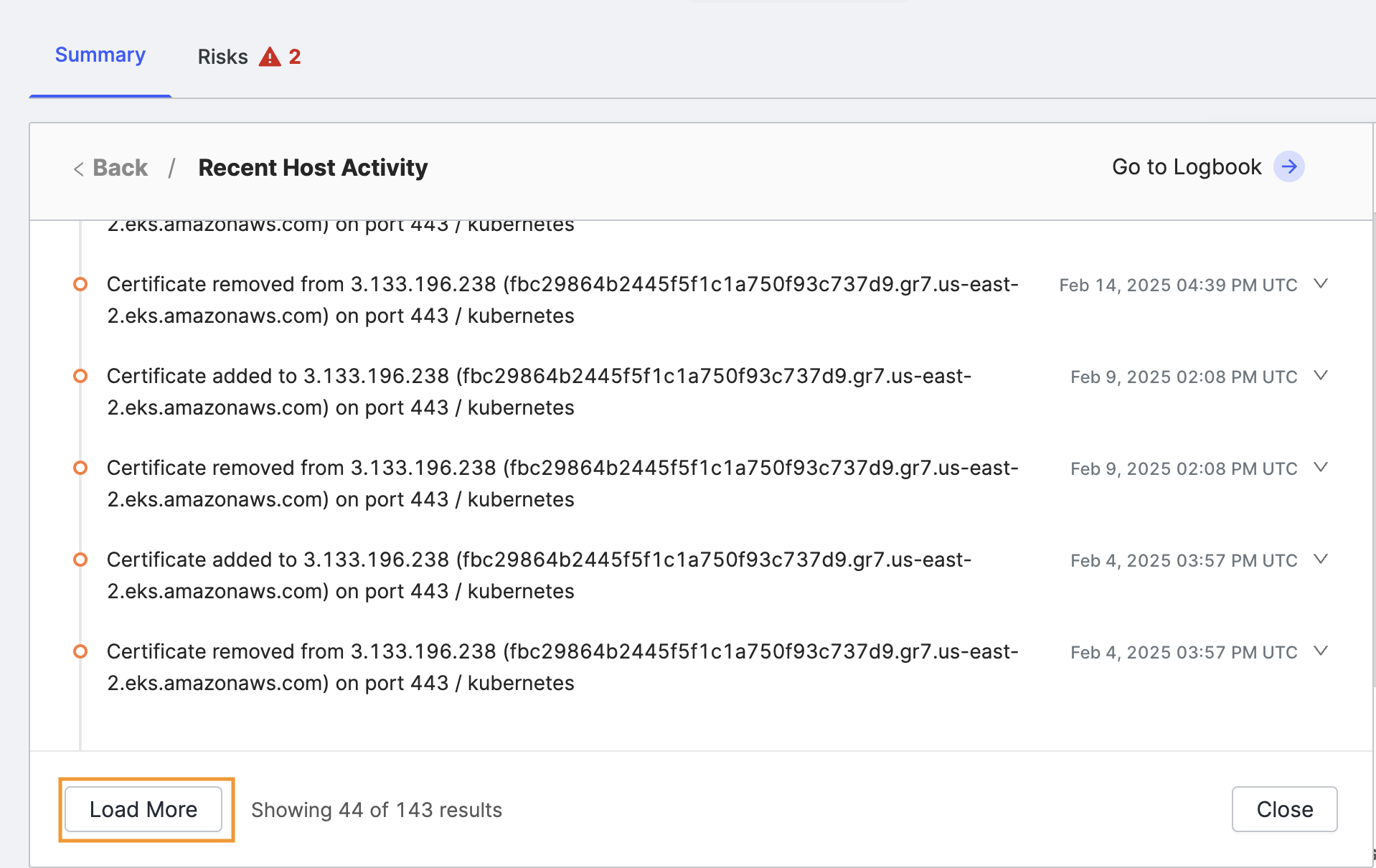
If you want to filter the events further, excluding or including only certain types, click Go to Logbook at the top right corner of the card. This will take you to the Logbook page, where those refinement options are available.
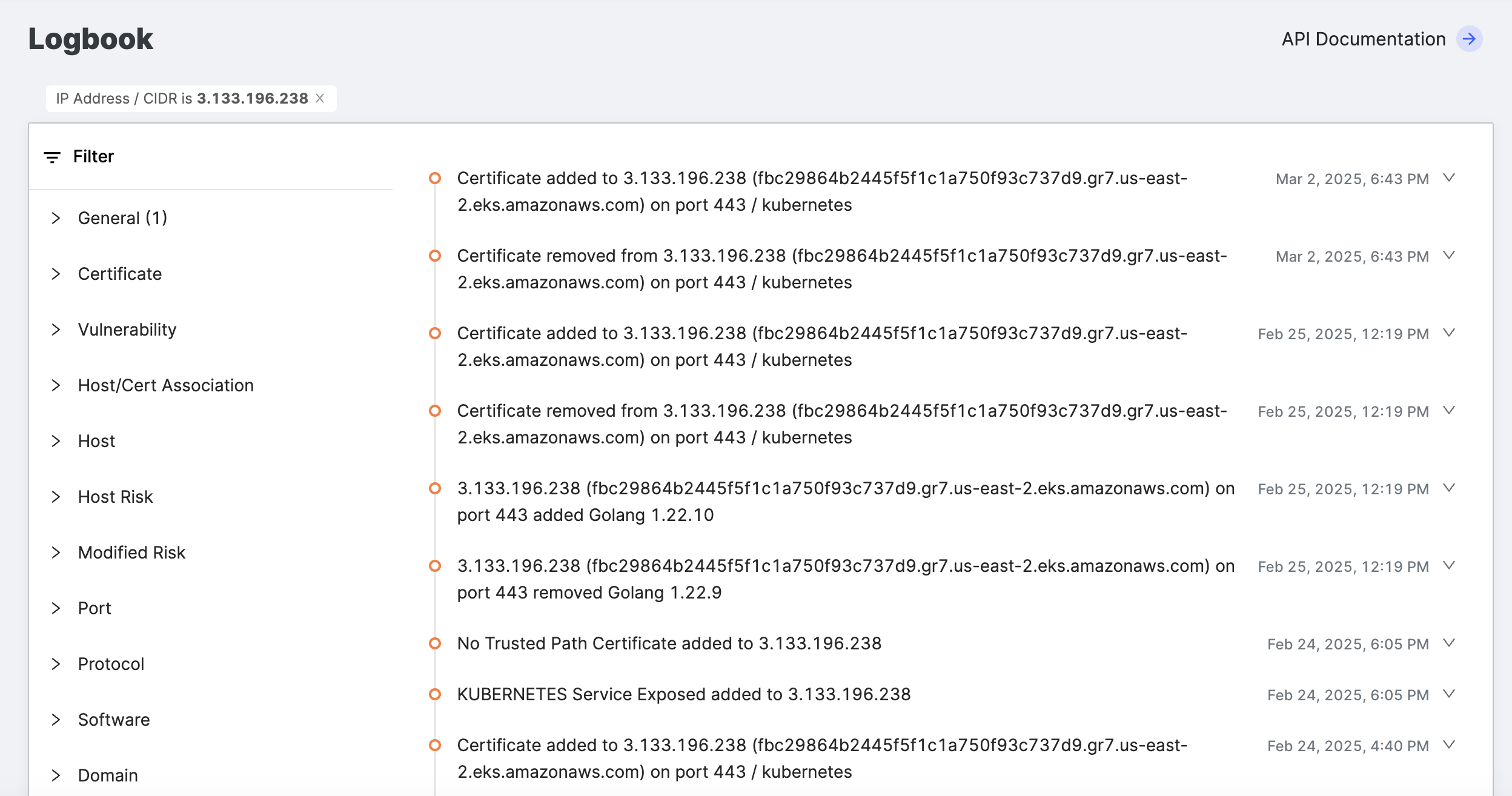
The Logbook page shows the IP address filter already set for the selected host.
For more information on the events that can appear in the recent activity card, see the logbook article.
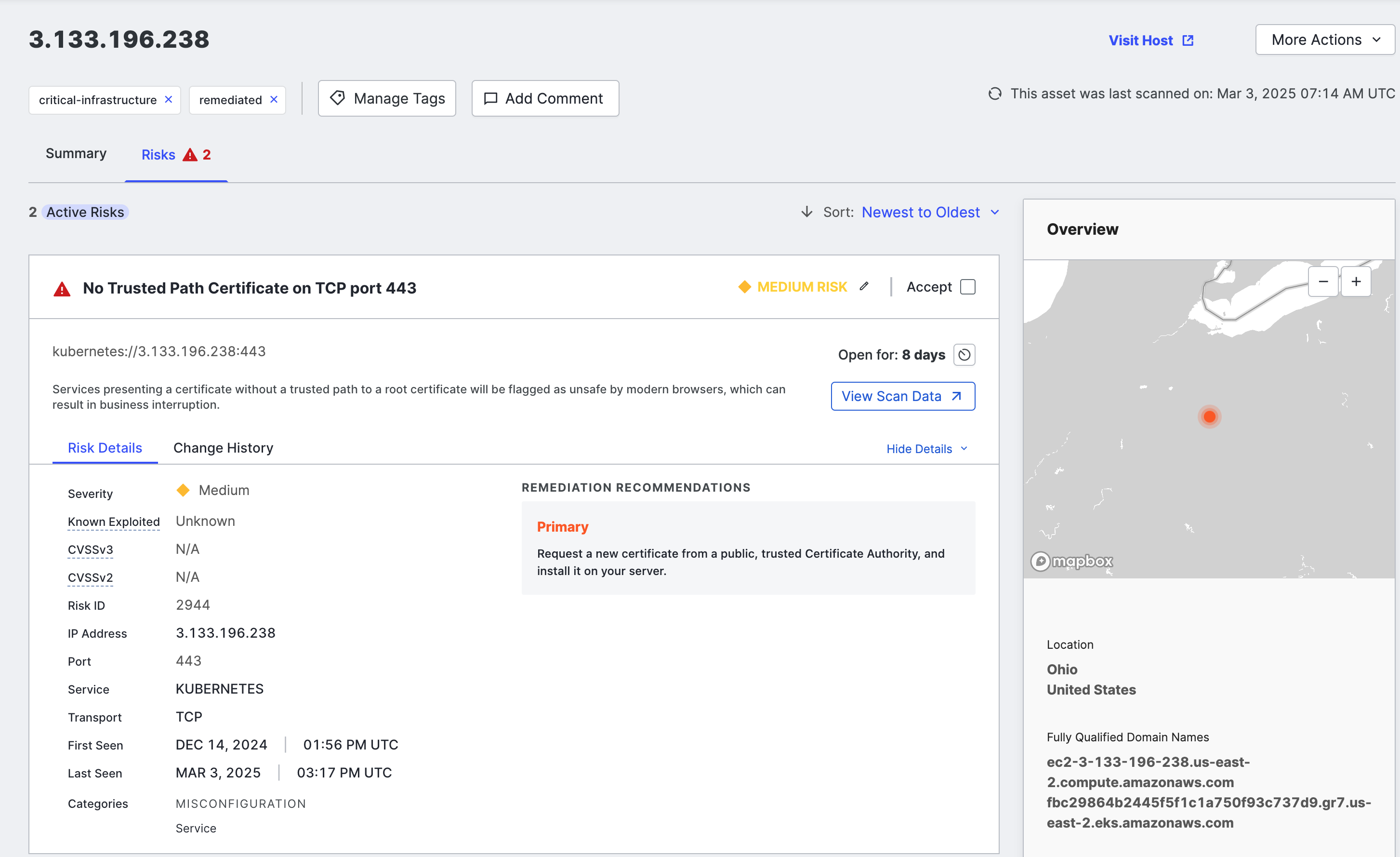
Risks tab
If there are risks on the host, a red warning icon next to the Risks tab near the top of the page identifies them. Click the tab to see the list of identified risks, details, and remediation recommendations.
The list is ordered by detection date, with the newest on top. However, you can sort by severity by using the menu above the list on the right.
Discovery Path
The Discovery Path card shows a list of assets whose connections to this host were used to determine with confidence that this host belongs to your organization.
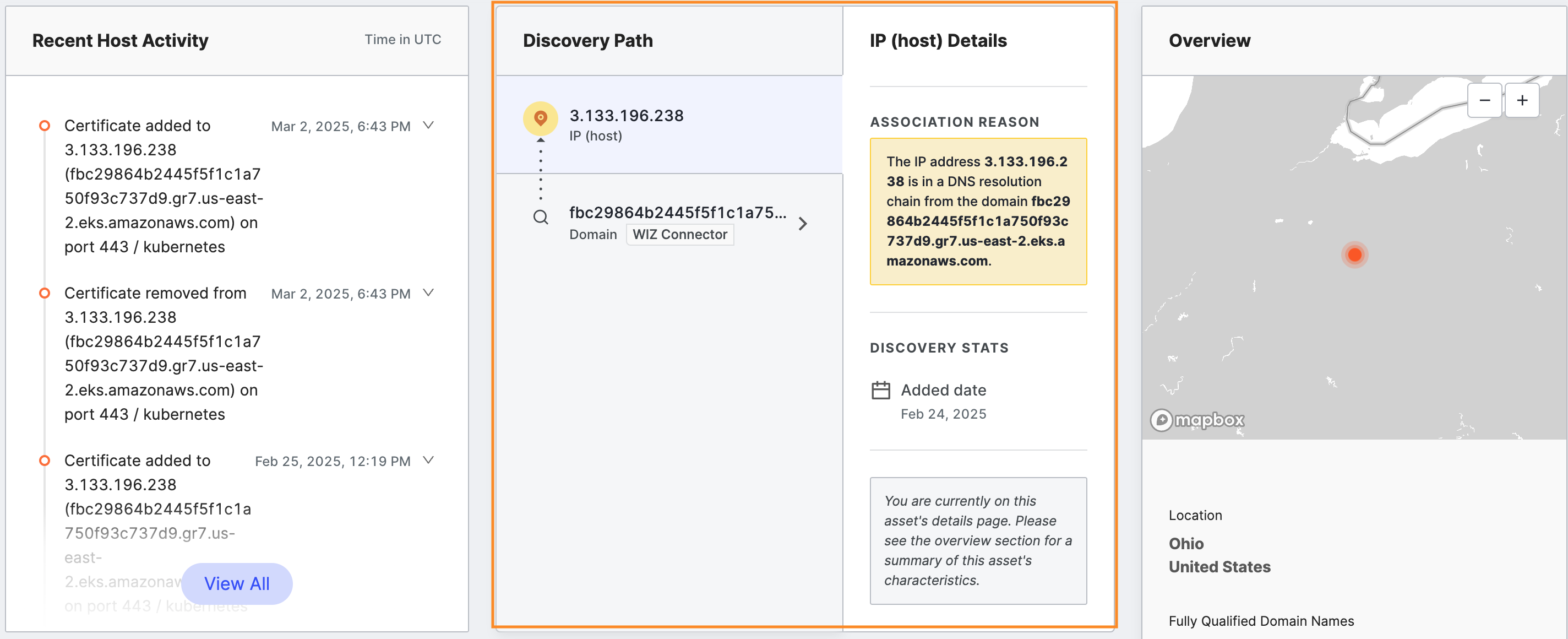
After investigating, if you decide that you do not want Censys to track this host for you, click More Actions > Remove at the top right of the page. This removes the asset and puts it on an excluded asset list so it does not reappear in subsequent Censys attributions.
Overview
The Overview area on the far right of the page enriches the host information gained from the scan with other contextual data.
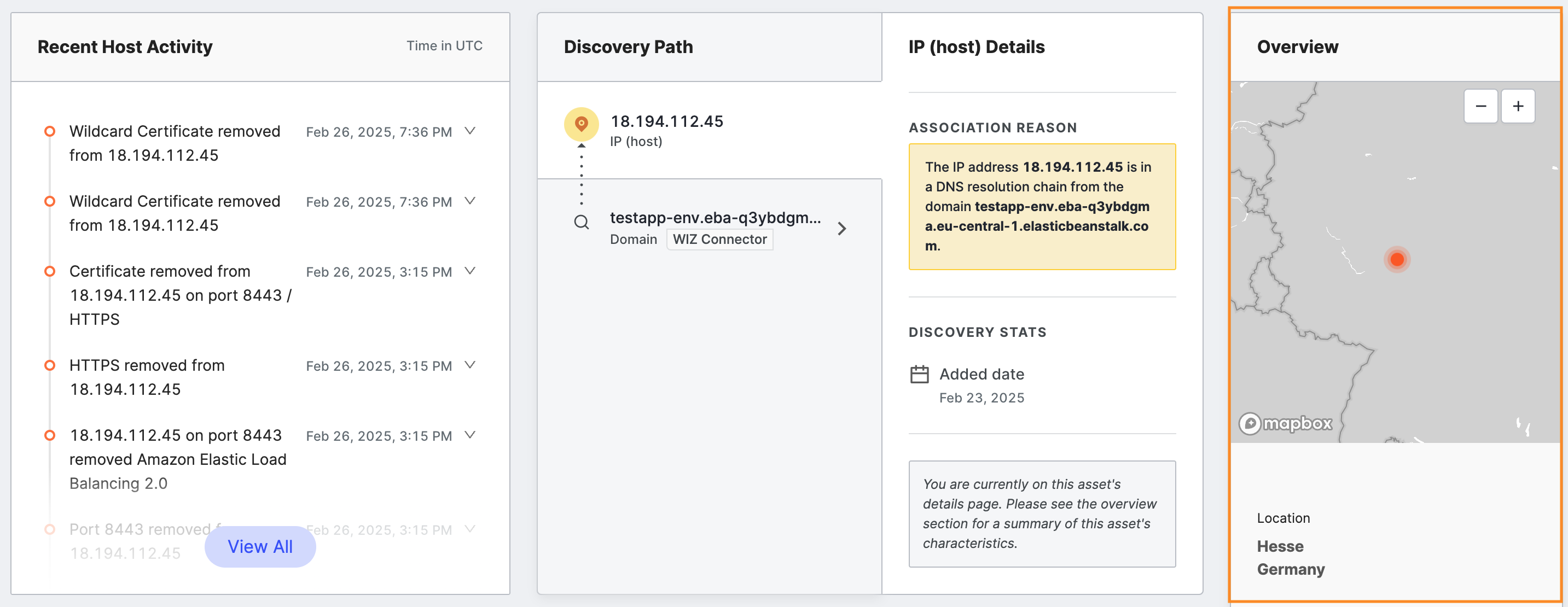
- Location: The country, and state or province shown on a map at the top.
- Fully Qualified Domain Names: Name obtained by reverse and forward DNS.
- Network WHOIS Org Name: The organization name associated with the netblock.
- Cloud: The cloud provider where the IP is hosted.
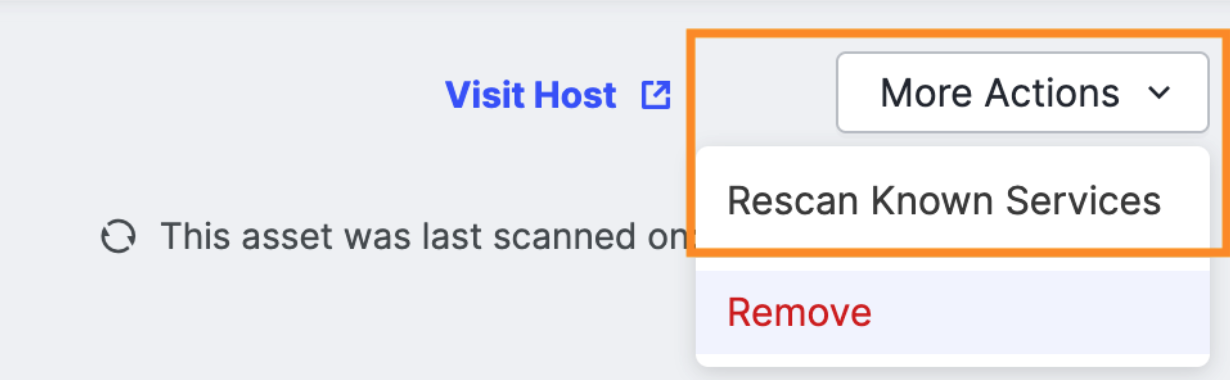
Rescan known services
Access Levels: Enterprise
After addressing vulnerabilities or misconfigurations—such as updating software versions, closing unnecessary ports, or removing outdated services—you can use the rescan feature to verify that these changes are reflected externally immediately. This ensures that remediation actions have effectively mitigated the identified risks.
The rescan also provides immediate feedback. Unlike scheduled scans that occur at set intervals, on-demand rescans offer immediate insights into the current state of services. This is vital for promptly validating remediation efforts.
To rescan services on a host, on its host details page, click More Actions > Rescan Known Services on the top right of the screen.
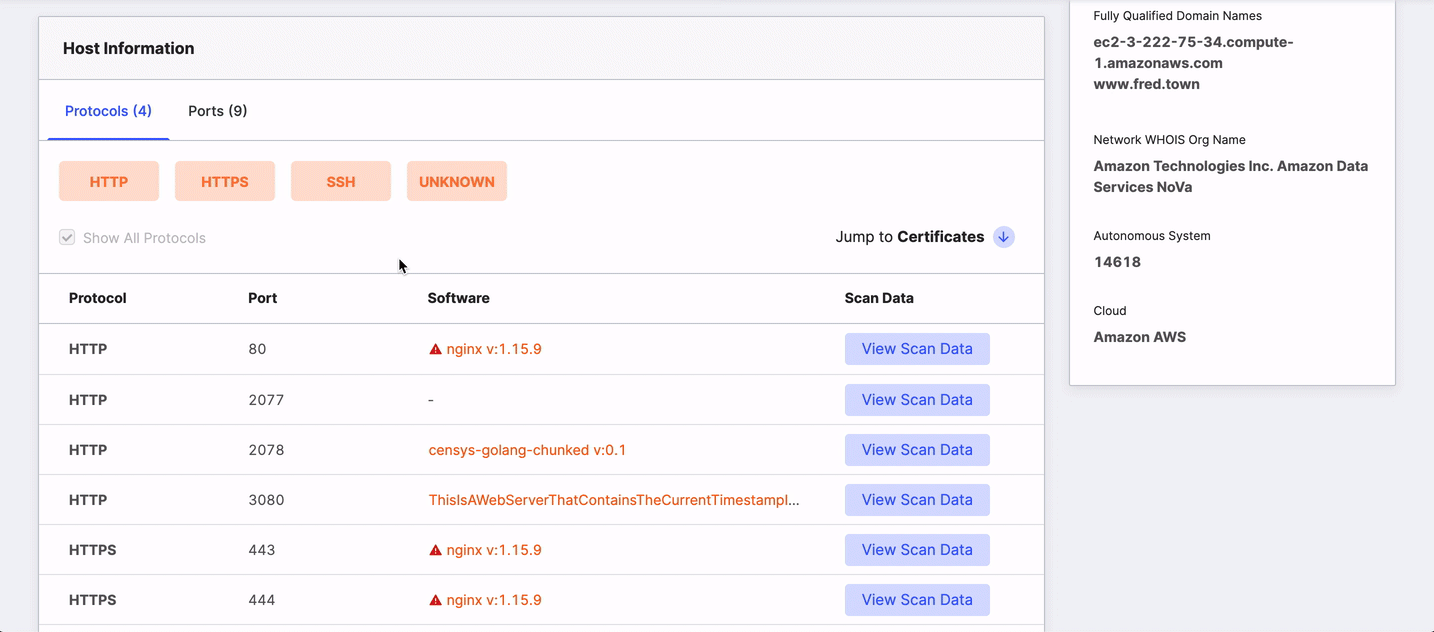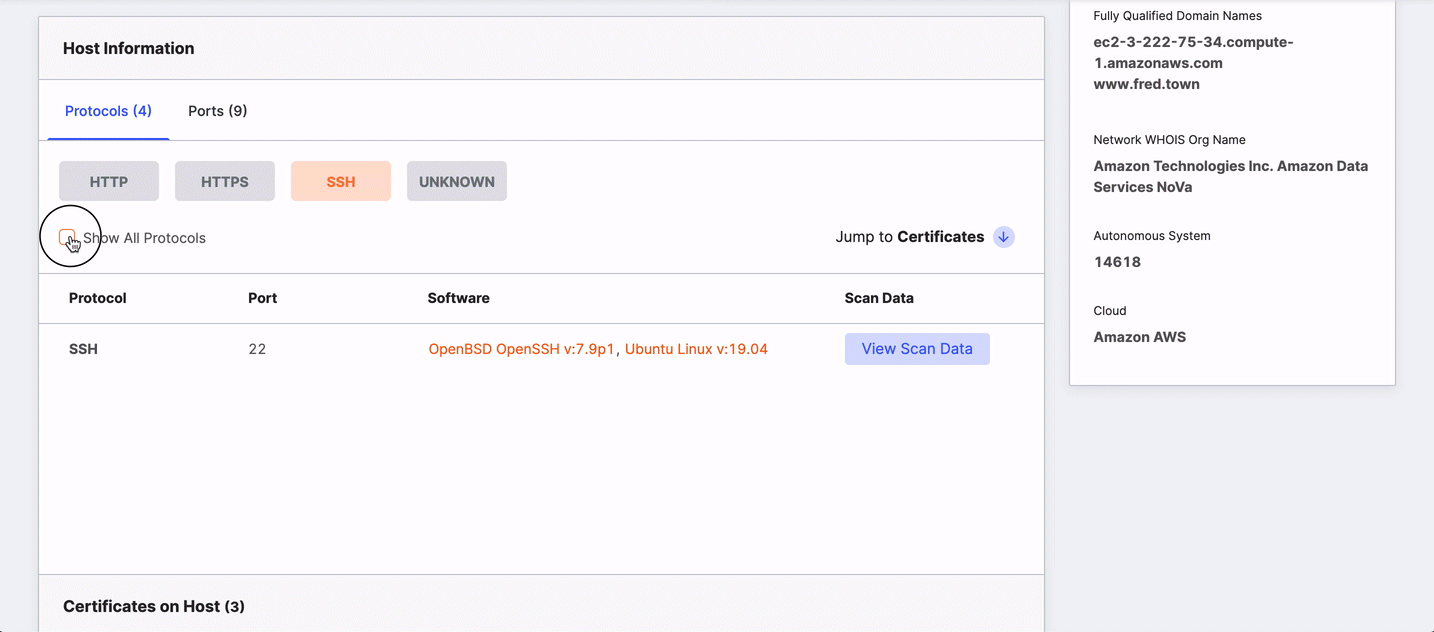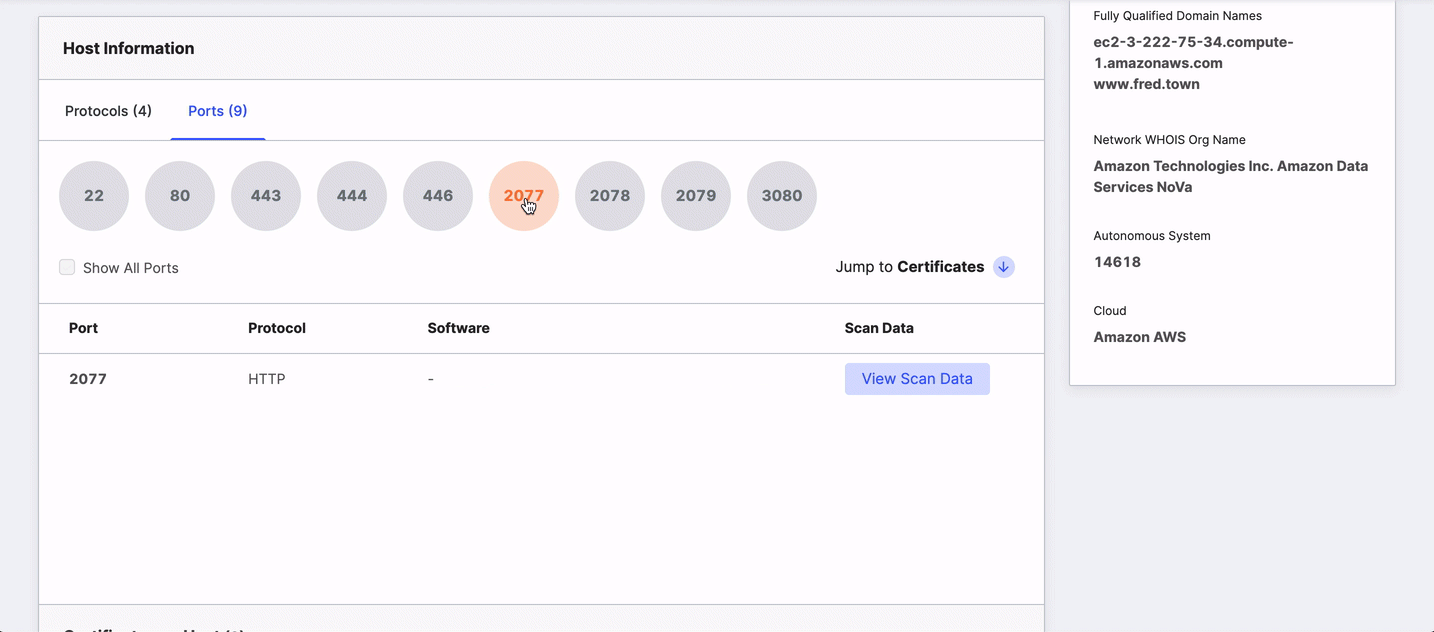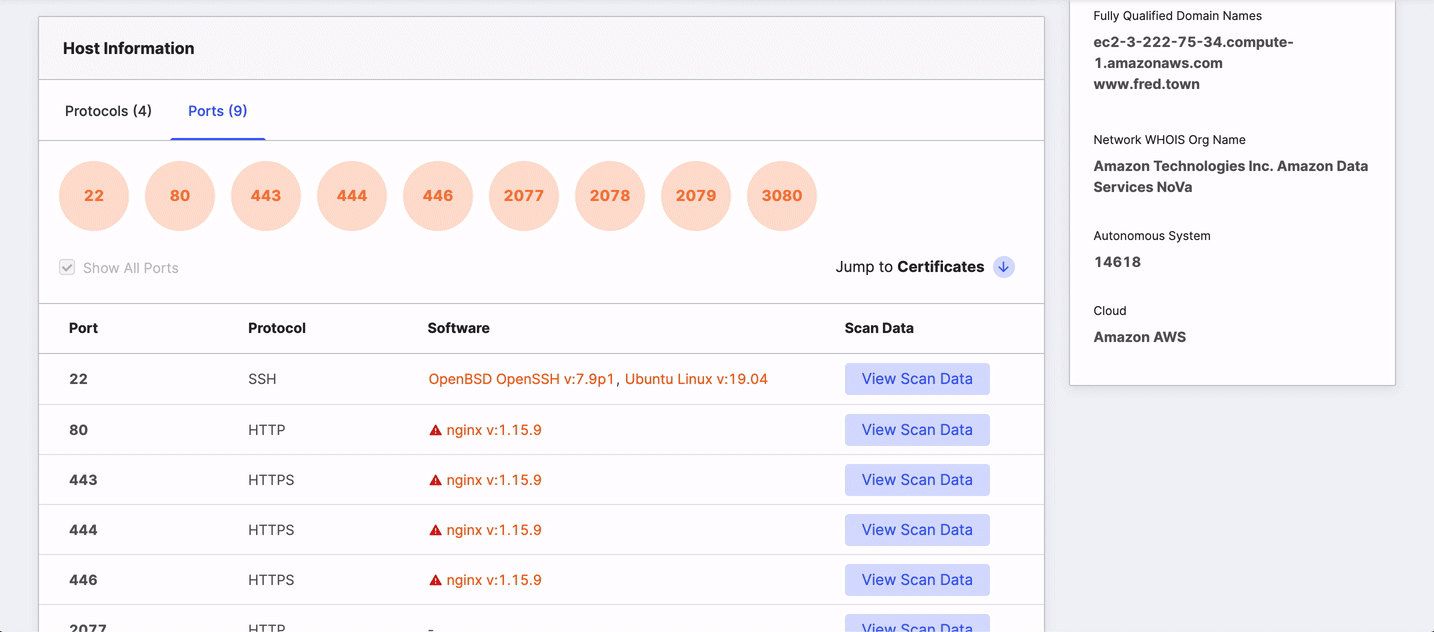
Protocols and ports
This area shows every protocol the host is using on its open ports and additional details to help you identify and secure the services there. The table's default view lists protocols, but you can view the chart by port by clicking the Ports tab.
The table shows all ports and protocols by default. Clicking a port or protocol hides others. To return to an all-ports/protocol view, select the Show All checkbox.
The columns in the table provide detailed information about the service that Censys detected running on a particular port and include:
- Protocol: The application-layer protocol that the service uses to communicate with clients.
- Port: The port number used to receive and send application-related communications.
- Software: The name and version of the software running on the port, if known.
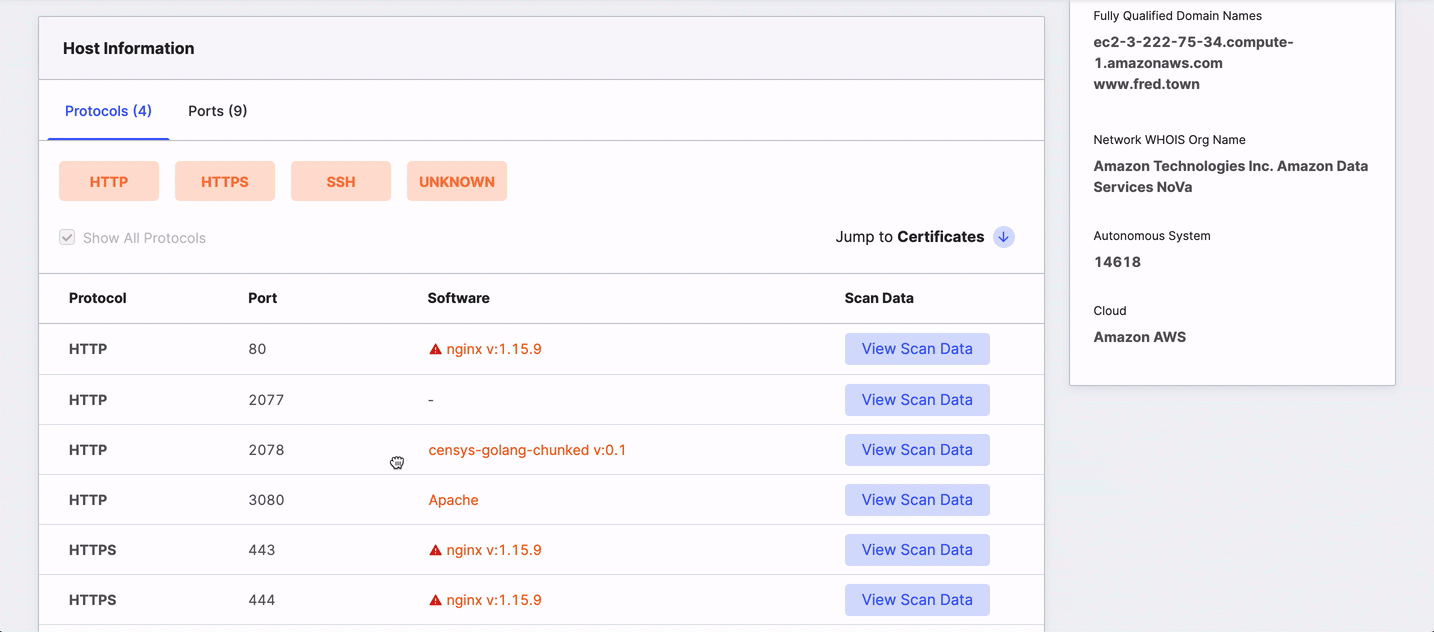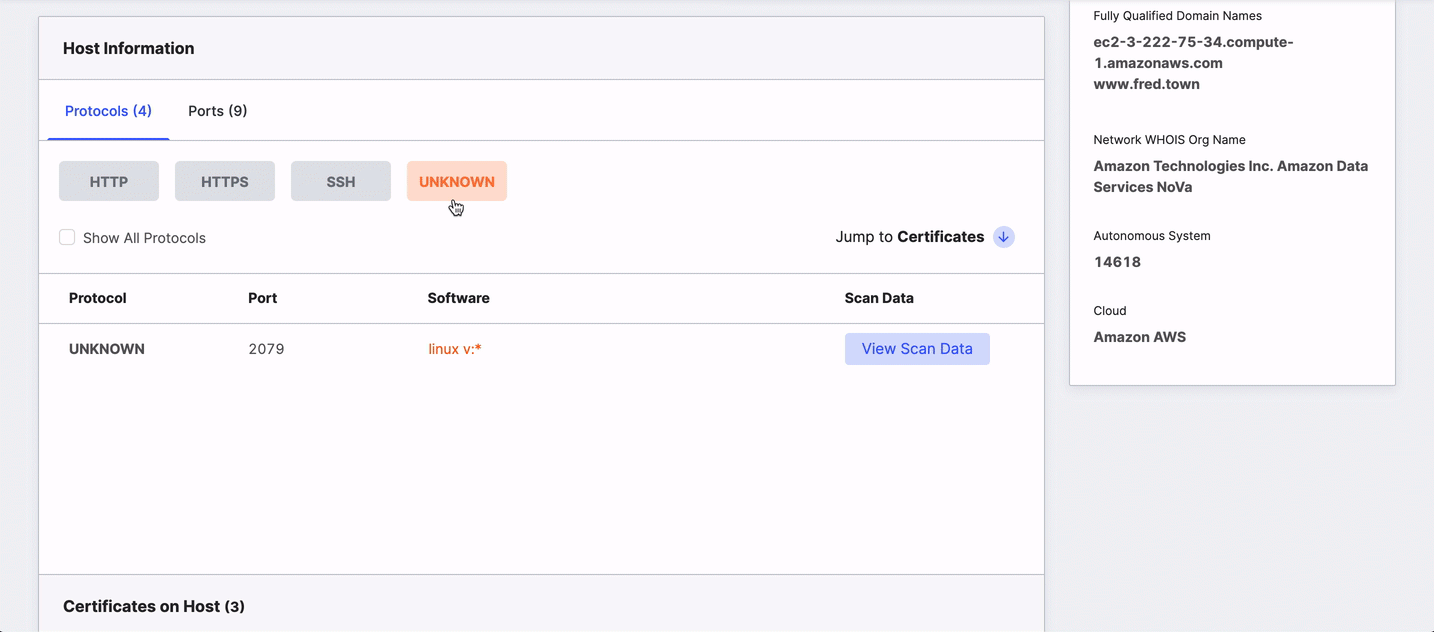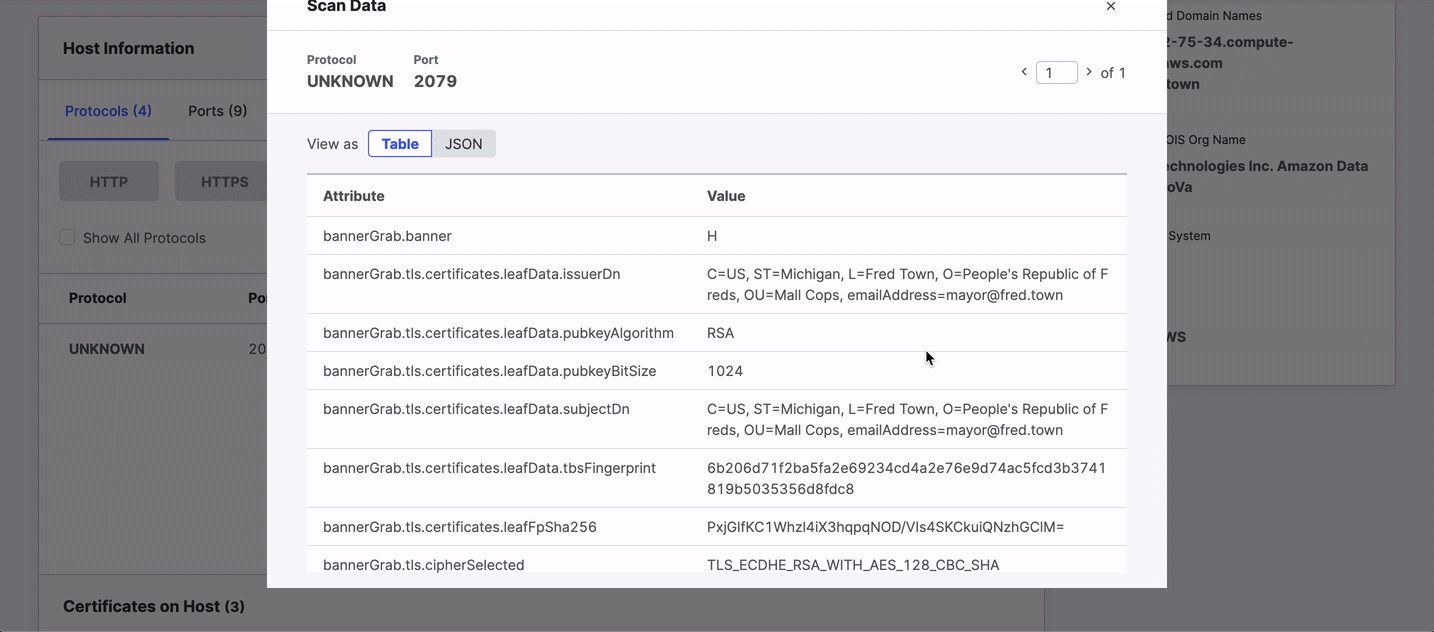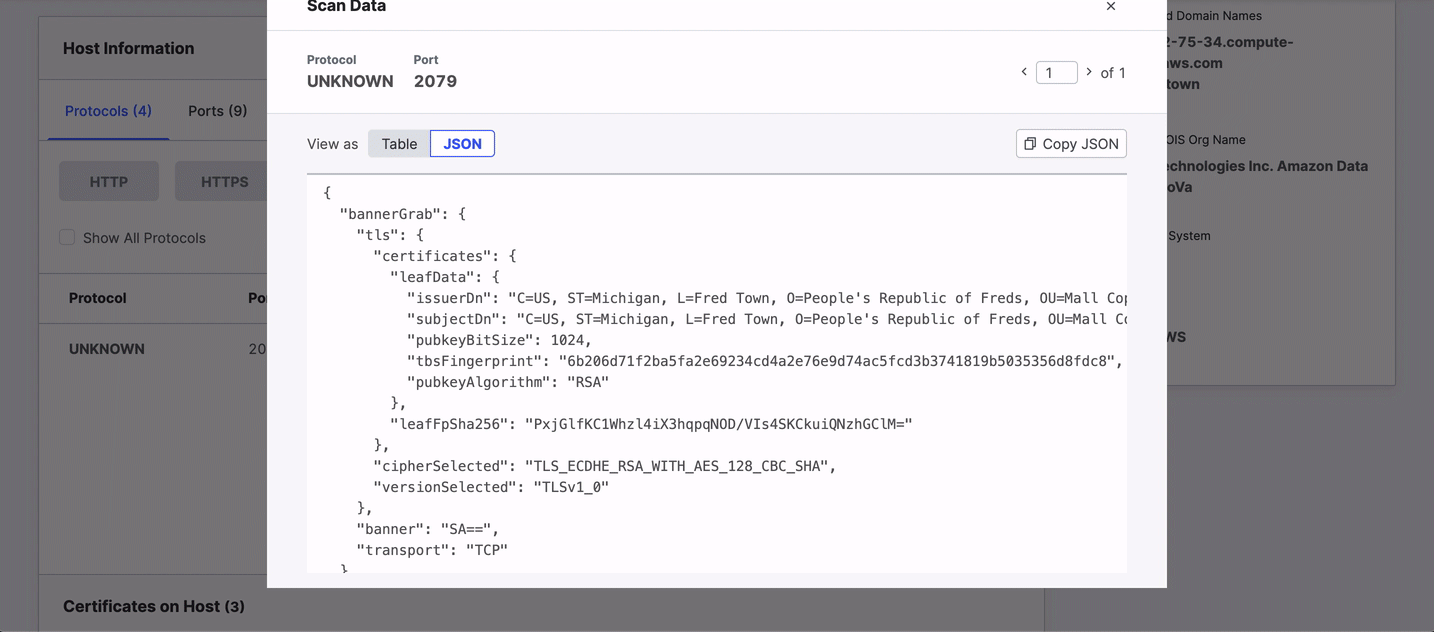
- Scan Data: Structured data for the port and protocol pair obtained during the scan.
Click View Scan Data on the right side of the row to view structured data in a table or as JSON.
Certificates on Host
The next section of the area shows Transport Layer Security (TLS) certificates presented by this host when scanned.
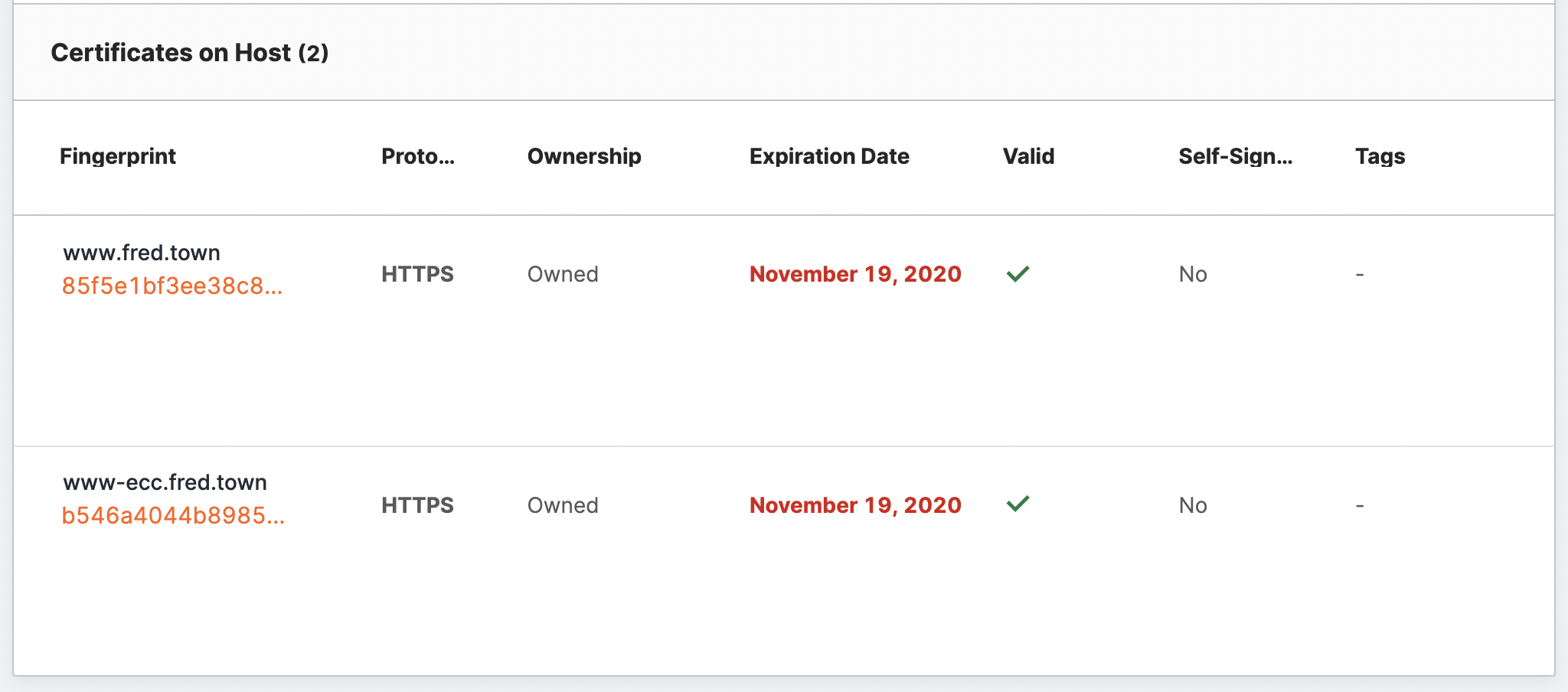
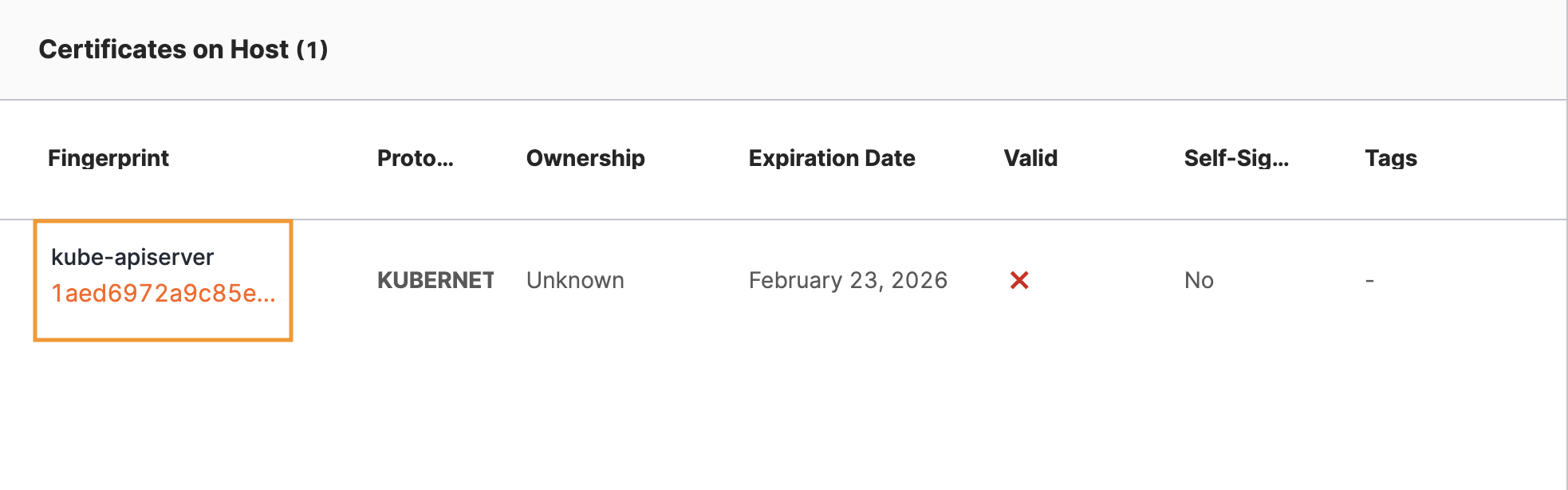
The default view of the table is listed by certificate fingerprint with the common name listed above. Other columns in the table provide high-level certificate information, such as:
- Port/Protocol: The port or protocol that the host presented the certificate on. This column changes with the selection above.
- Ownership: A category indicating whether Censys considers the certificate to be yours or a third party’s.
- Expiration Date: The date on which the certificate expires and can no longer be trusted by browsers if it is live on a site.
- Valid: A Censys indicator of trustworthiness based on the certificate’s features, including trust anchors, formatting, signatures, validity dates, and more.
- Self-Signed: Whether or not the certificate is self-signed. Self-signed certificates can indicate an internal or development certificate not intended to be exposed to the public Internet.
- Tags: Any tags assigned to this cert.
TipNot seeing a certificate you expected? Check for redirects to domains serving as authentication systems, which prevent ASM from seeing the cert.
To learn more about a certificate, click the linked Fingerprint ID. This opens the recent Certificate Activity page.
Updated 2 months ago
