Ports & Protocols
In Censys Attack Surface Management (ASM), the Ports & Protocols dashboard enables you to understand exactly which ports are open in your attack surface across the full 65,535-port range. This allows you to quickly determine whether there are any open ports that are misconfigured or non-compliant with your organization’s policy.
In addition to ports, the dashboard shows which protocols are present on your ports. ASM identifies whether these protocols are on standard ports, as defined by IANA. Nonstandard port and protocol combinations may indicate misconfigurations or malicious behavior. By closing these gaps, you can reduce your attack surface and, in turn, reduce the chances of a breach.
Learn more about how Censys scanning works and how it helps protect your organization here.
View and filter the dashboard
In the ASM web UI, on the main dashboard page, click Ports & Protocols.
Filter the entire dashboard using the standard and nonstandard toggle and the options available in the Severity, Associated Date, Tags or Protocols dropdown menus. Use the Min Port: and Max Port: fields to define a range of ports to focus on.
NoteUnknown protocols are categorized as running on nonstandard ports by default.
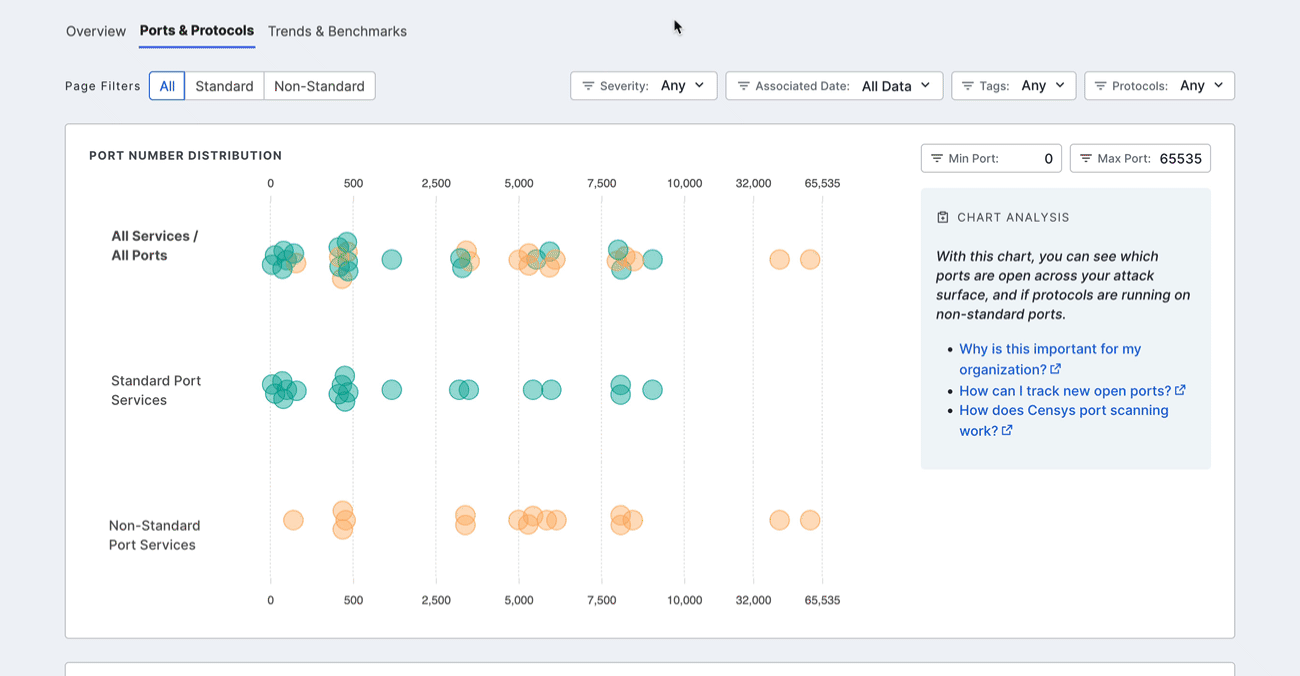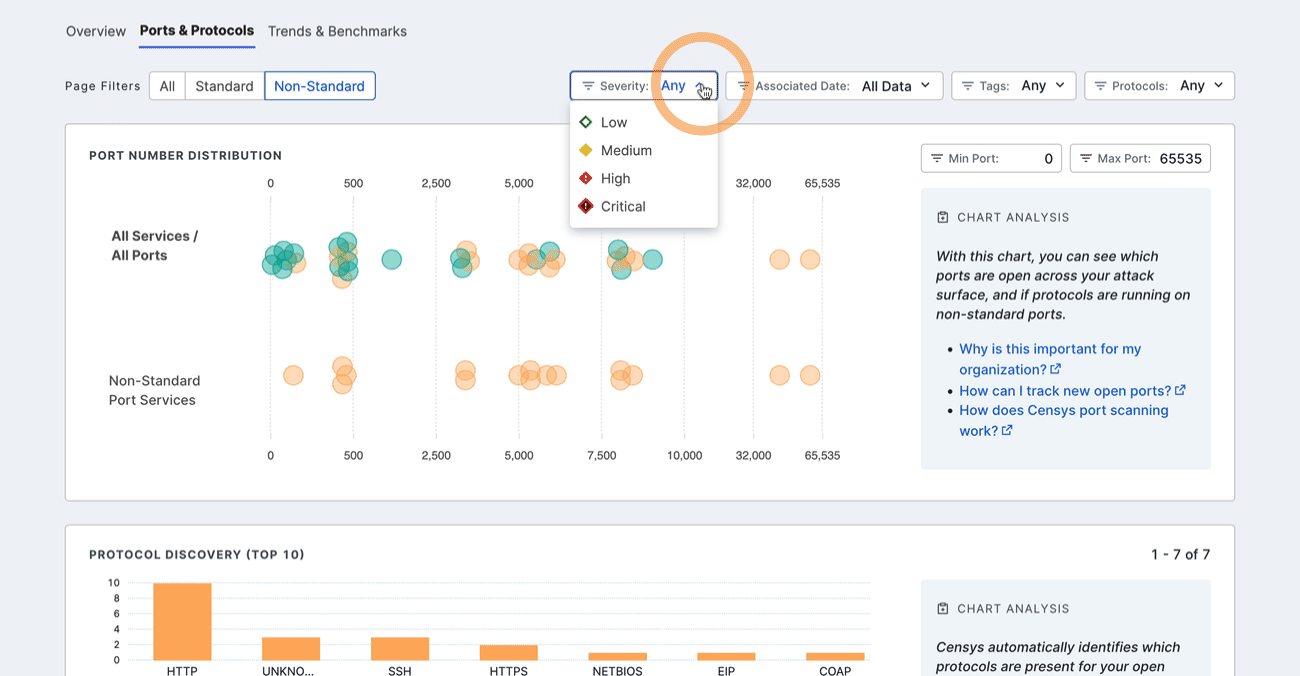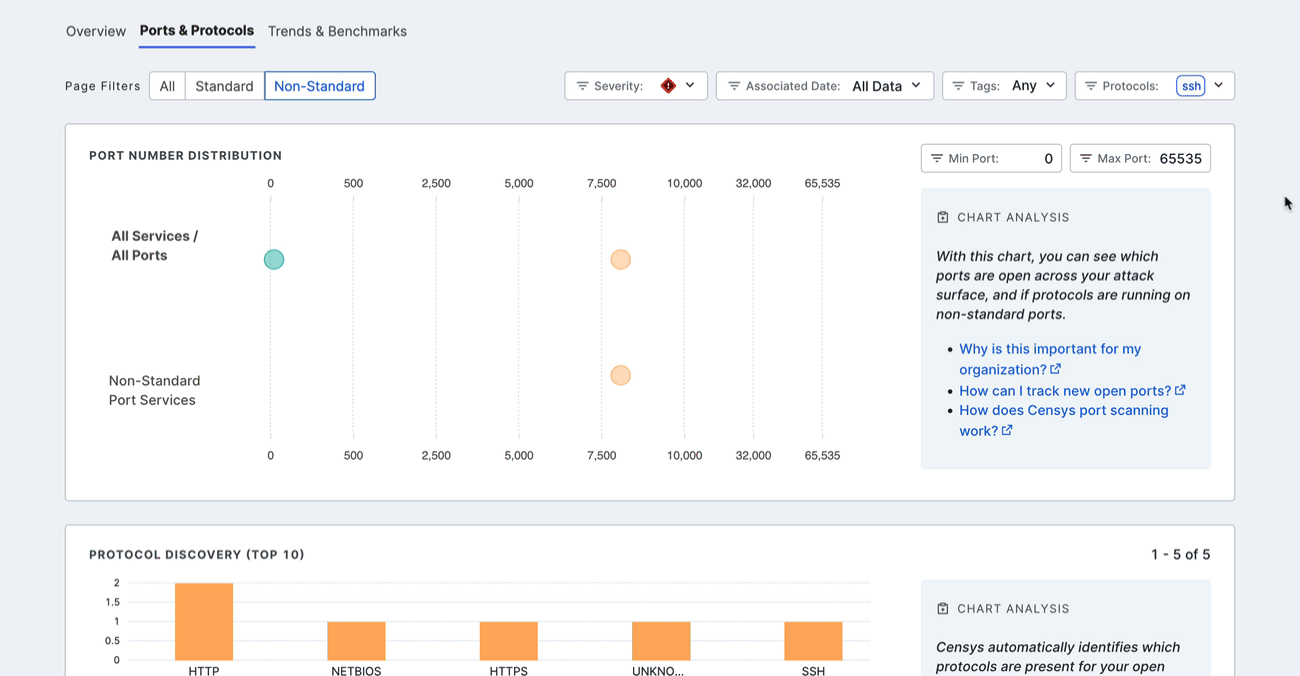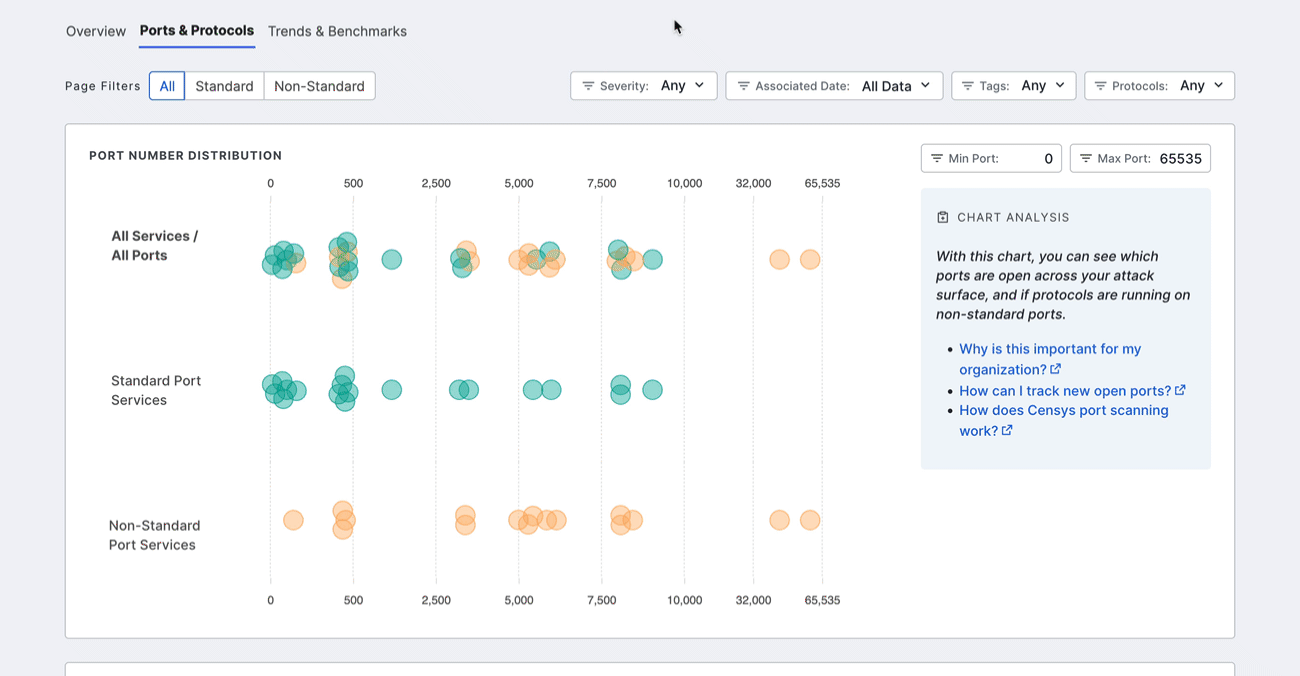
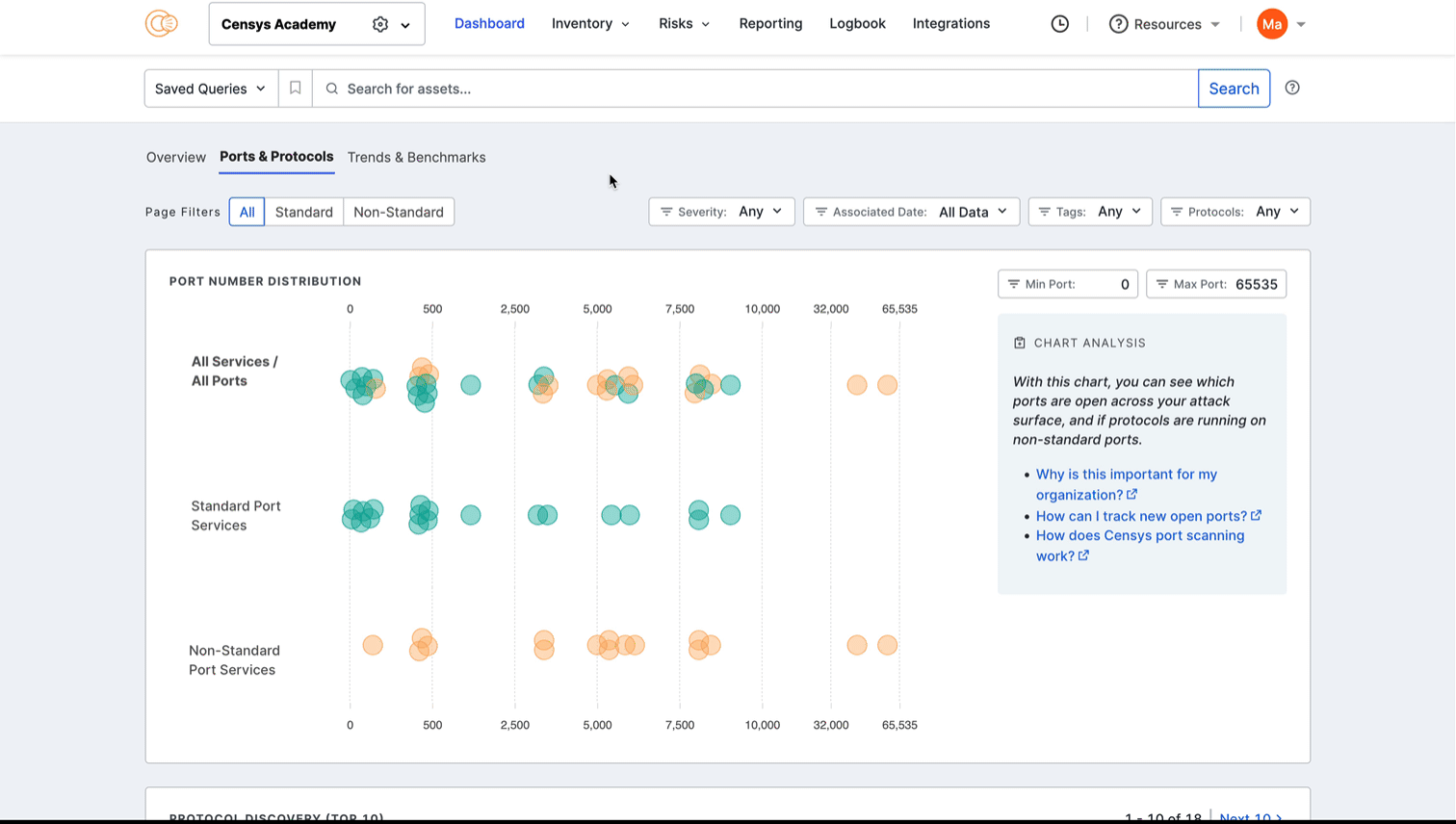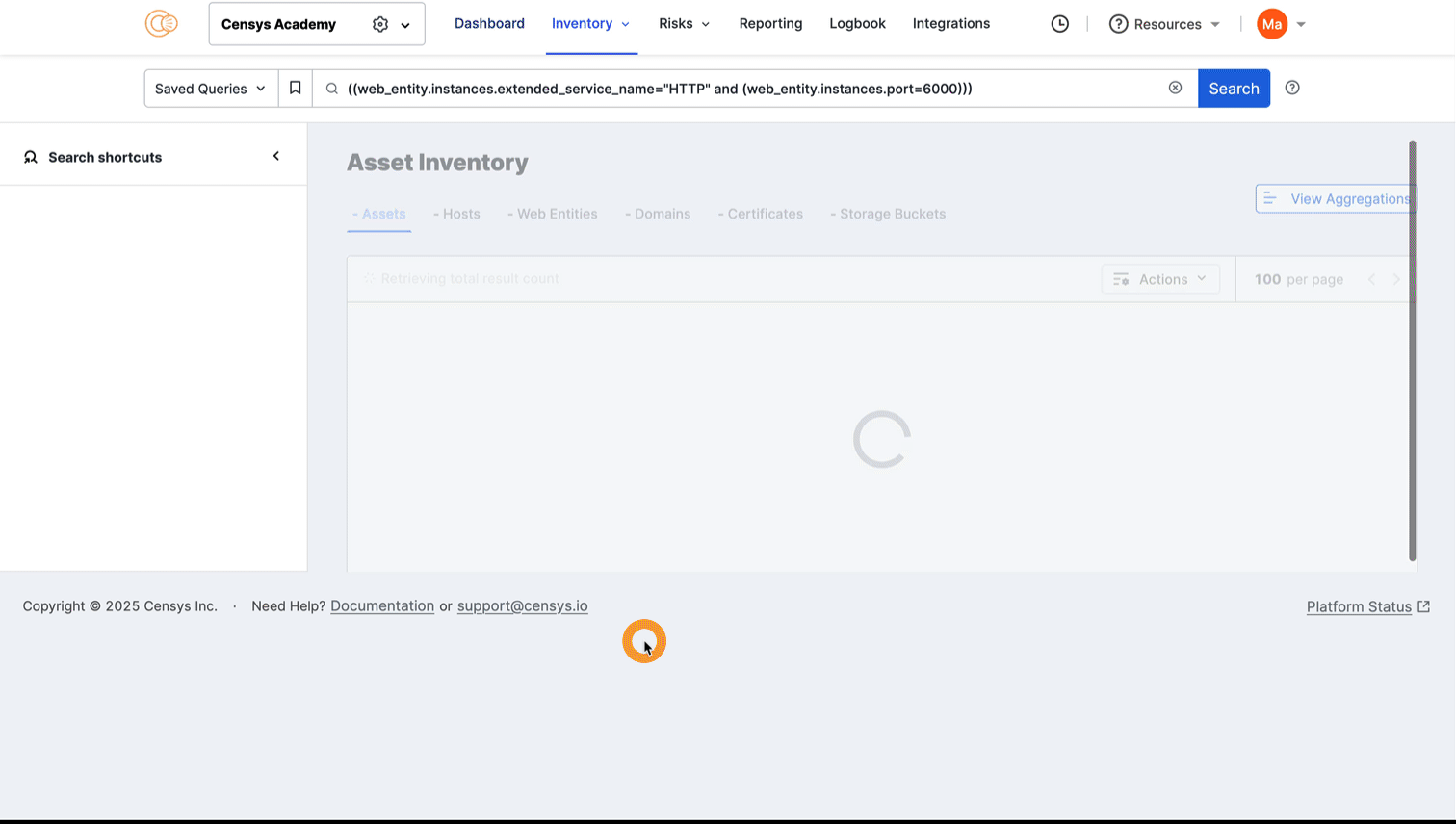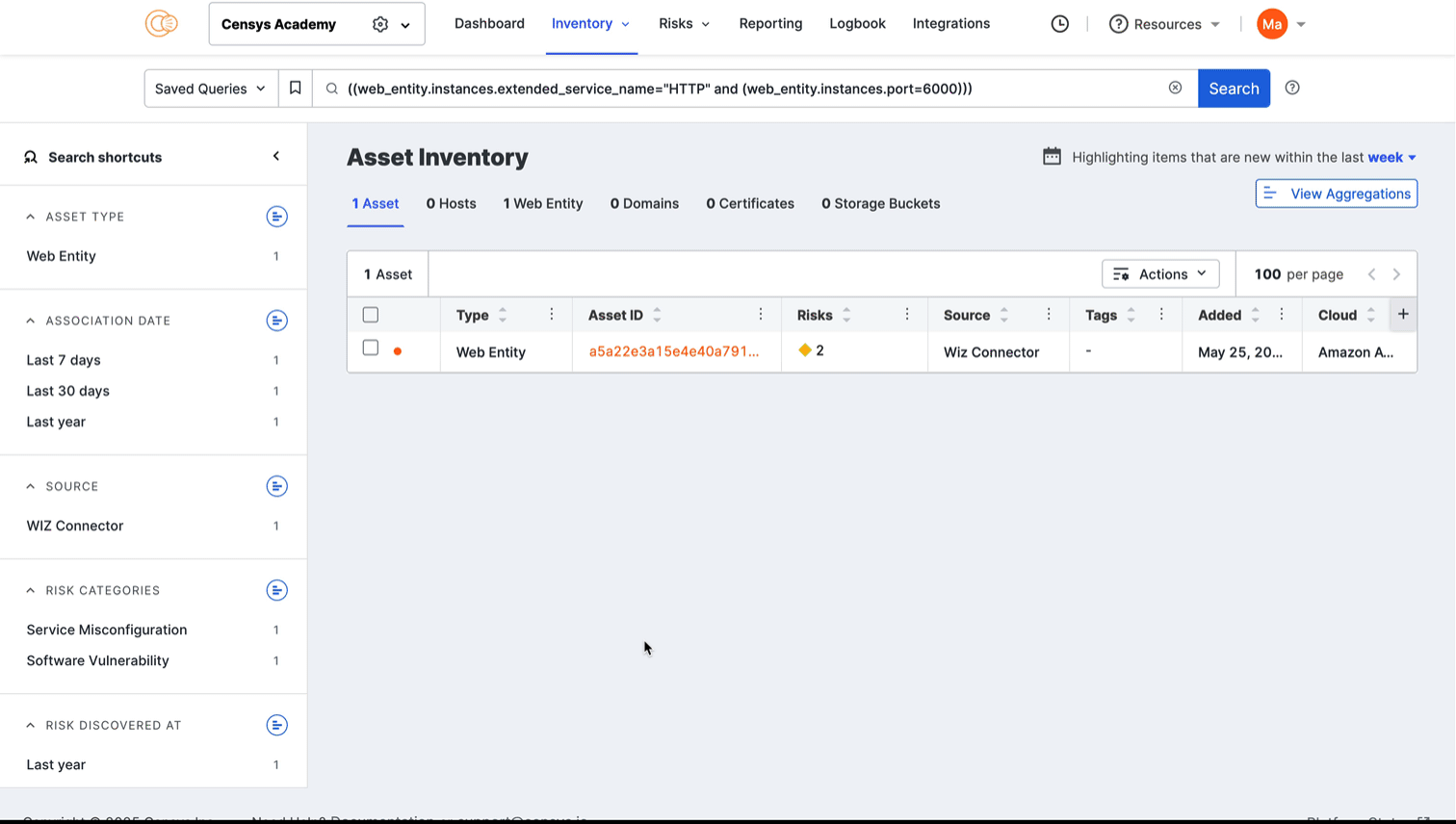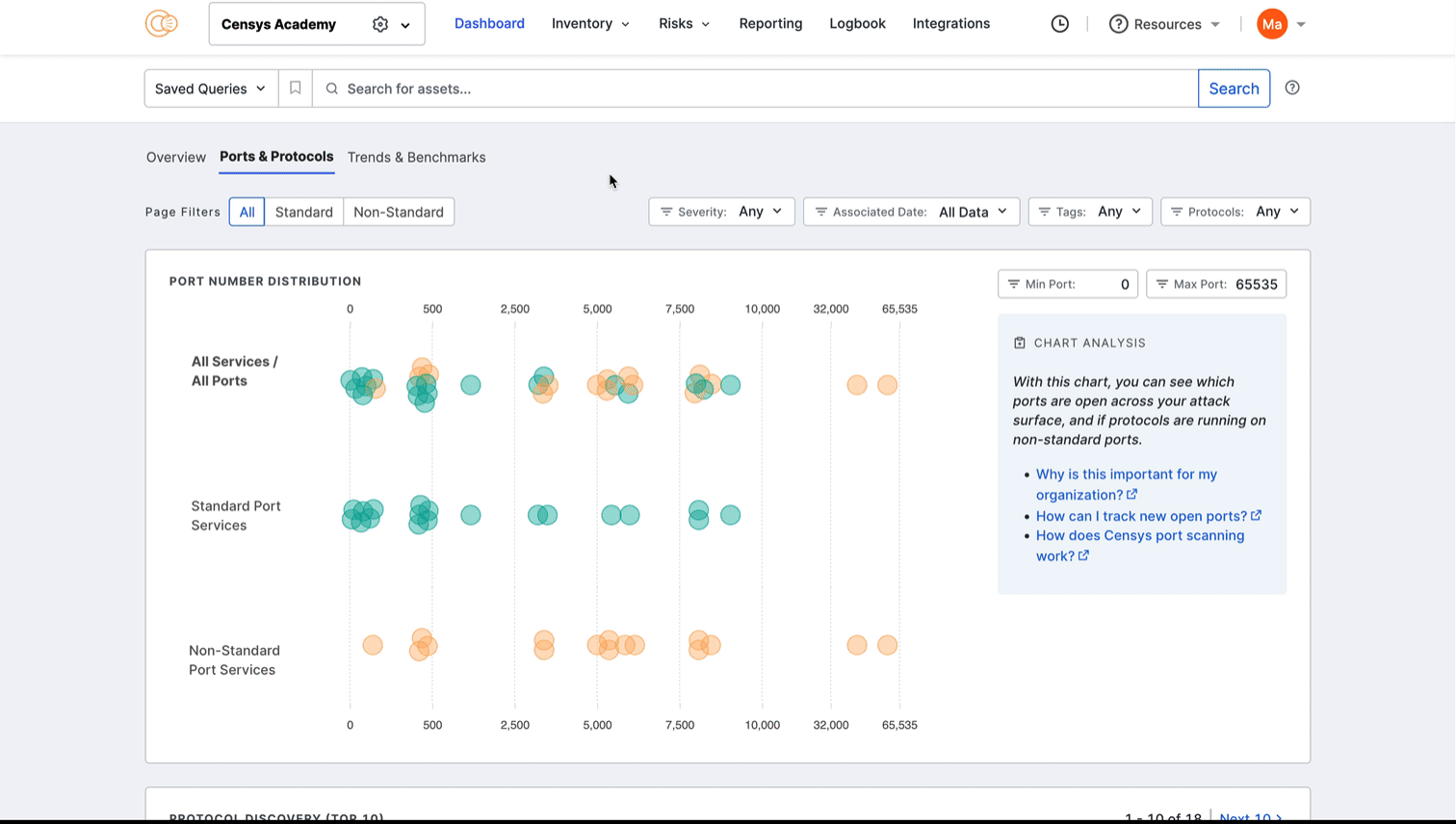
Port number distribution
The port distribution chart is a visualization of all open ports in your attack surface.
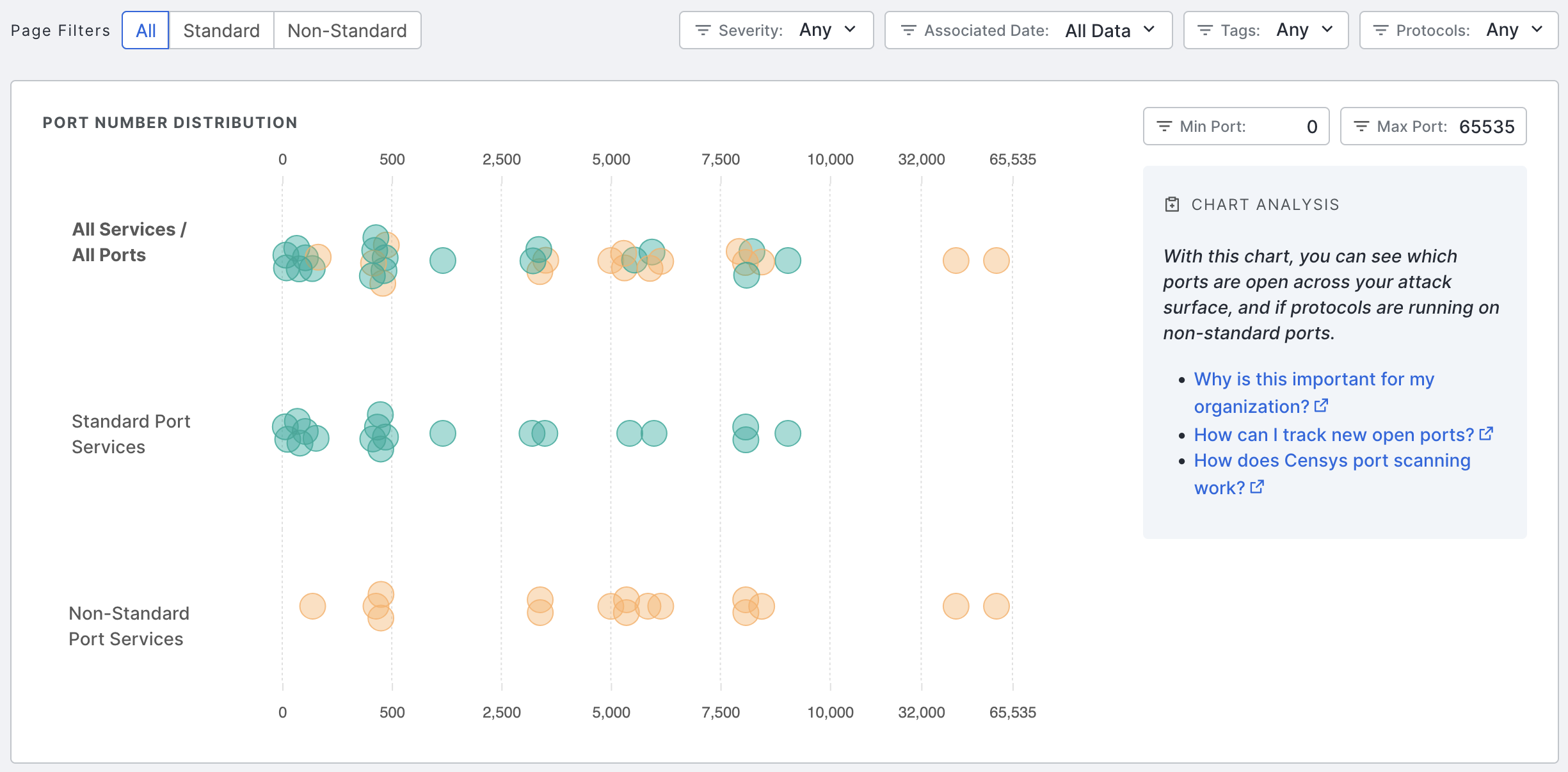
Hover over a dot to view its port number and protocol information. Click the dot to see all assets in your Inventory associated with the port and protocol pair. The query syntax used for this query is shown in the query bar. Set up regular alerting and tagging for these assets with Saved Query Automation.
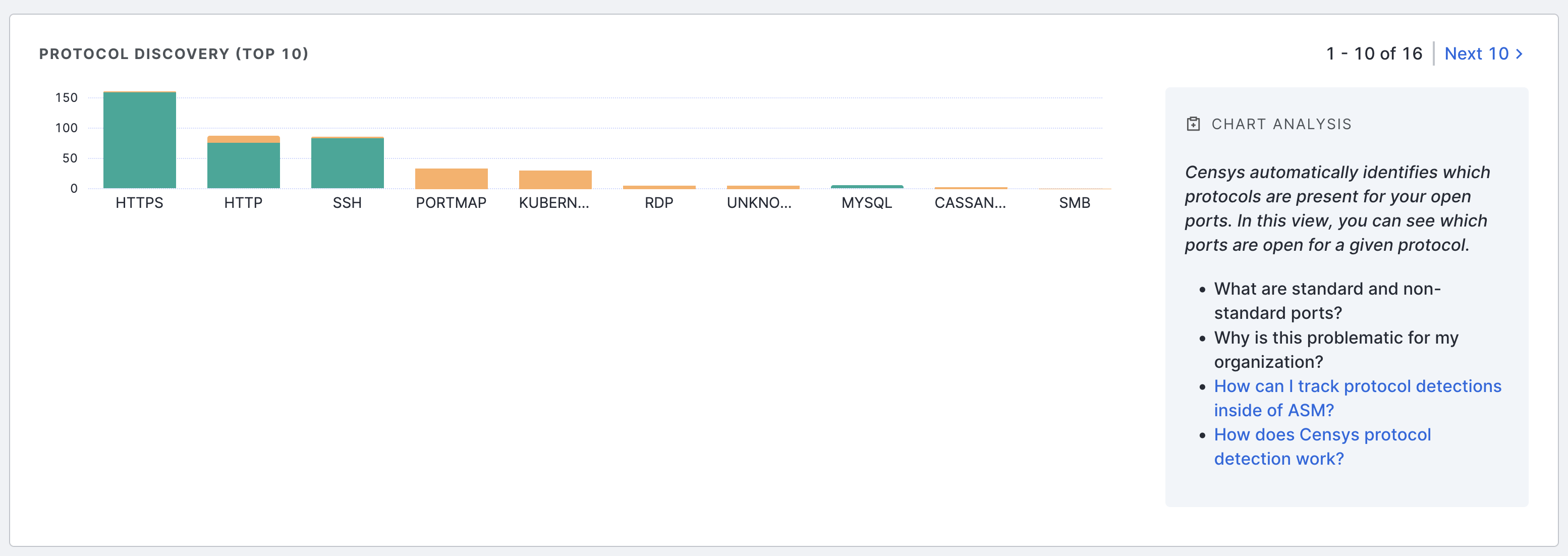
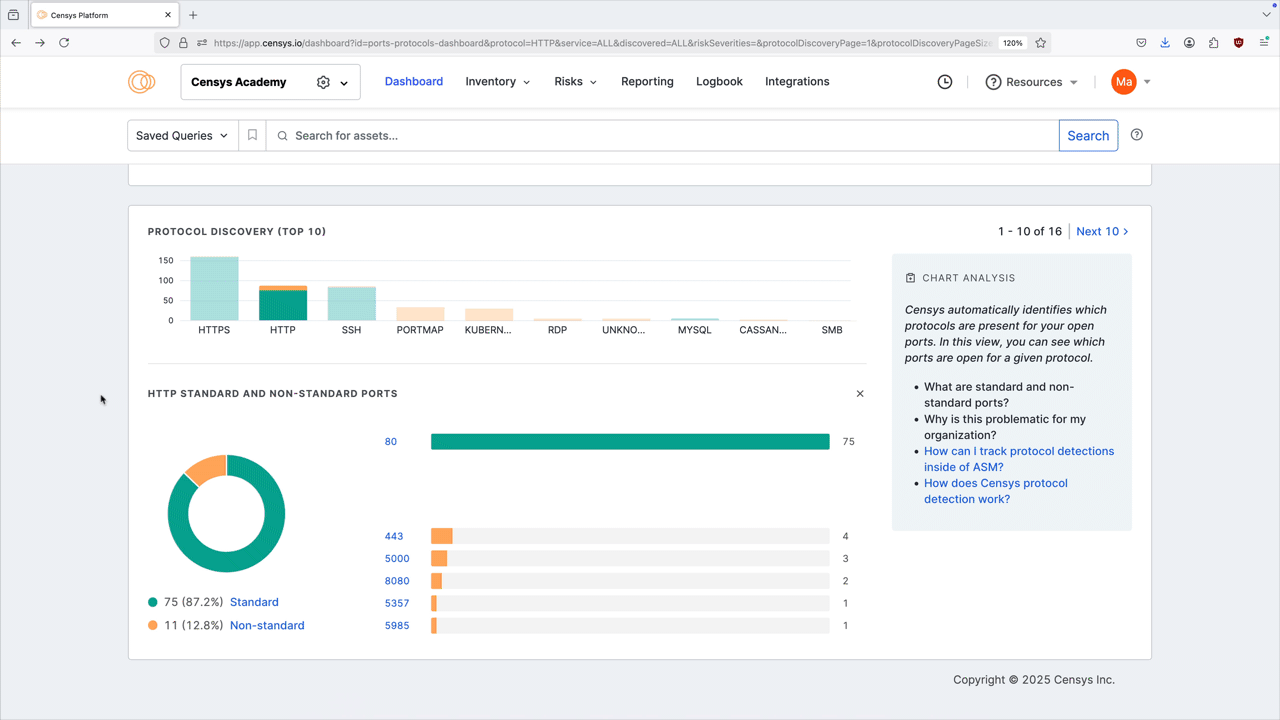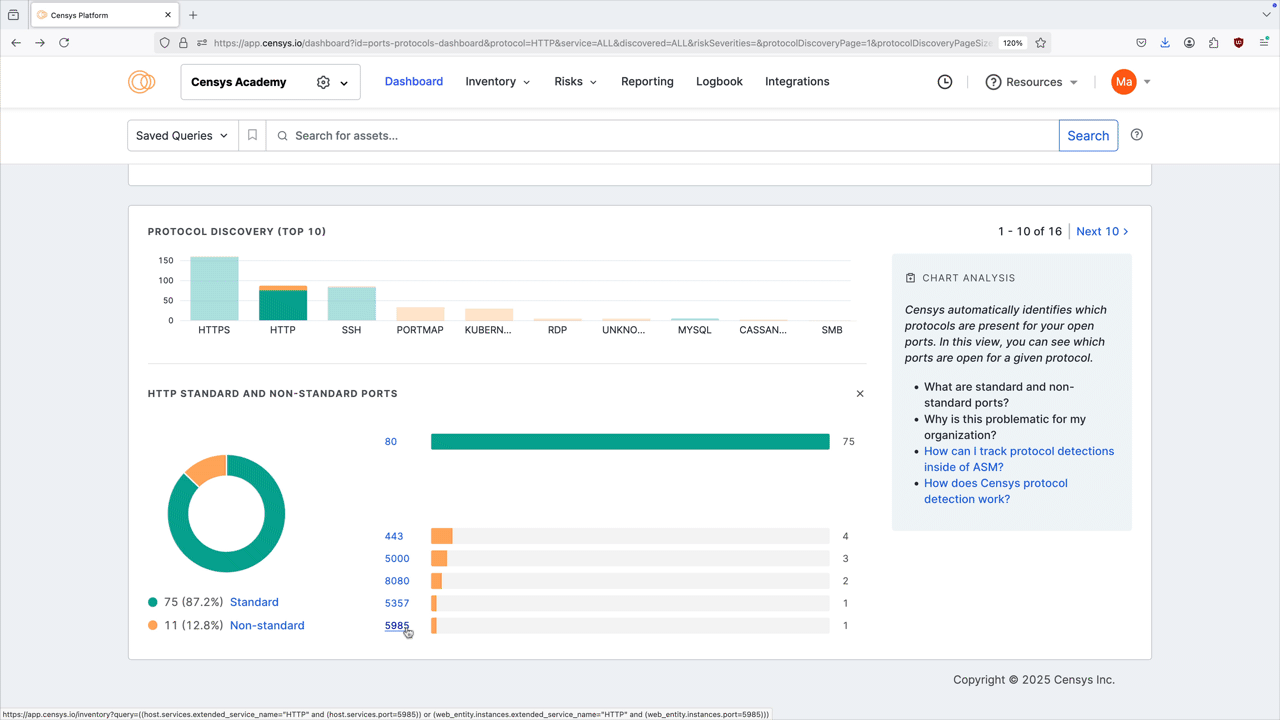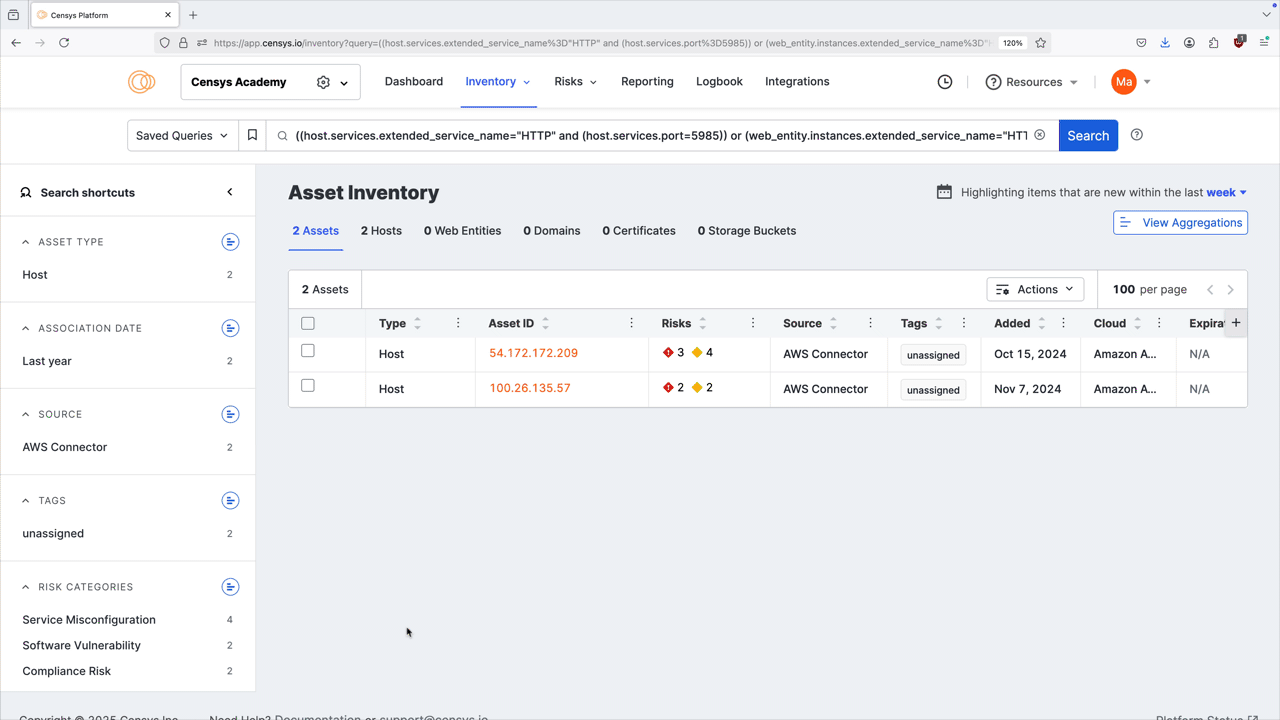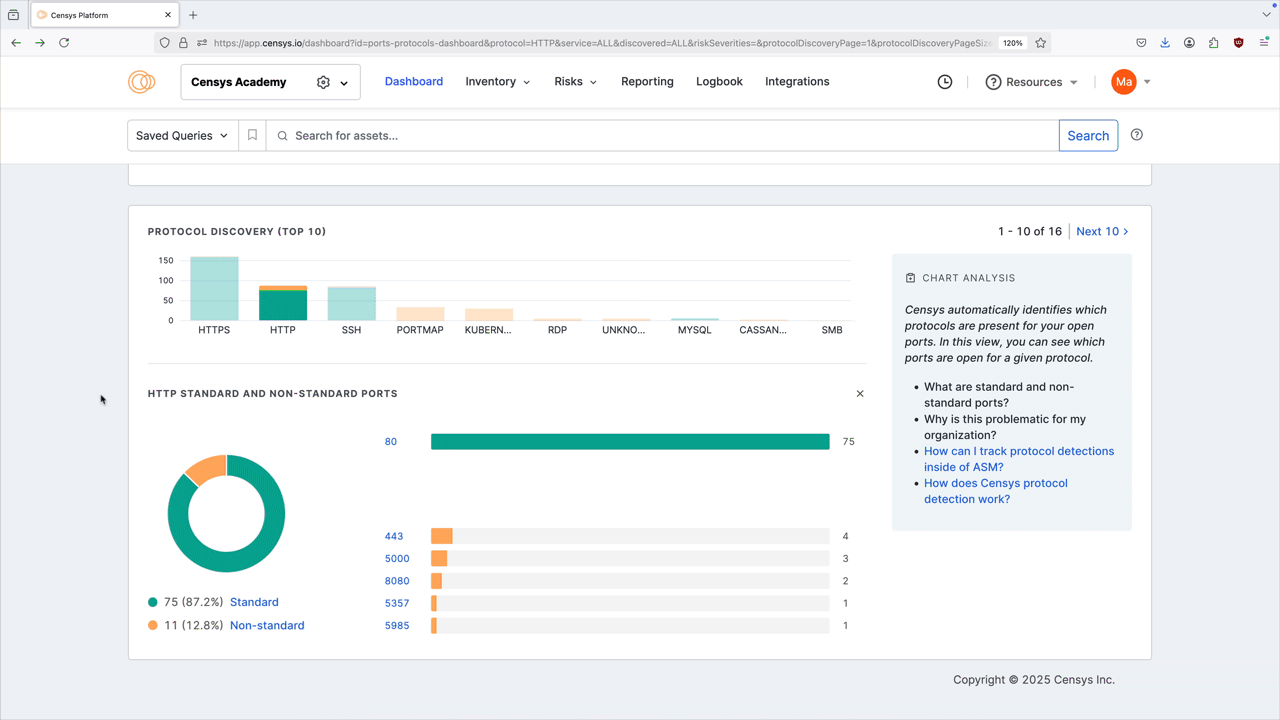
Protocol discovery
The protocol discovery chart shows the count of your services running various protocols. The green component of the bar represents services running on standard ports, while the orange component represents nonstandard ports. Use the Next 10 > and < Previous 10 links to page through your protocols.
Select a protocol bar plot to see standard and nonstandard port information for that protocol. This will also filter the port number distribution chart above.
Click any of the linked port numbers to see all assets in your Inventory associated with that port and protocol pair. The query syntax used for this query is shown in the query bar. Use Saved Query Automation to set up regular alerting and tagging for these assets.
Use cases
- Compliance standards including NIST SP 800 and PCI 4.0 require the closure of unnecessary ports and protocols. Use the dashboard to identify assets to investigate and remediate to align with these standards.
- Use the Severity filter on the dashboard to quickly identify nonstandard ports being used by assets with risks. In general, a misconfigured port is worthy of investigation, while a misconfigured port with a risk should be immediately remediated.
- Attackers use nonstandard ports to evade detection, for example during C2 communication. If your environment has already been infiltrated, activity on a nonstandard port can indicate a compromise and will need to be remediated.
Updated about 1 month ago
