Software
In Censys Attack Surface Management (ASM), you can search for software that needs to be updated or contains a vulnerability in your organization’s Internet-accessible hosts.
Three sources for software are pulled from scan results:
- A fingerprint (for example, a Censys mapping to Common Platform Enumeration (CPE) formatted software names)
- The HTTP x-powered-by field in an HTTP header
- The HTTP server header field in an HTTP field. This information is provided in a source field in our APIs and in the Source column on the Software list page.
Censys Attack Surface Management matches more than 1,433 software fingerprints to software. As additional fingerprints are created, the latter two methods will eventually be deprecated.
NoteASM only identifies end-of-life (EOL) versions for fingerprinted software.
View software
-
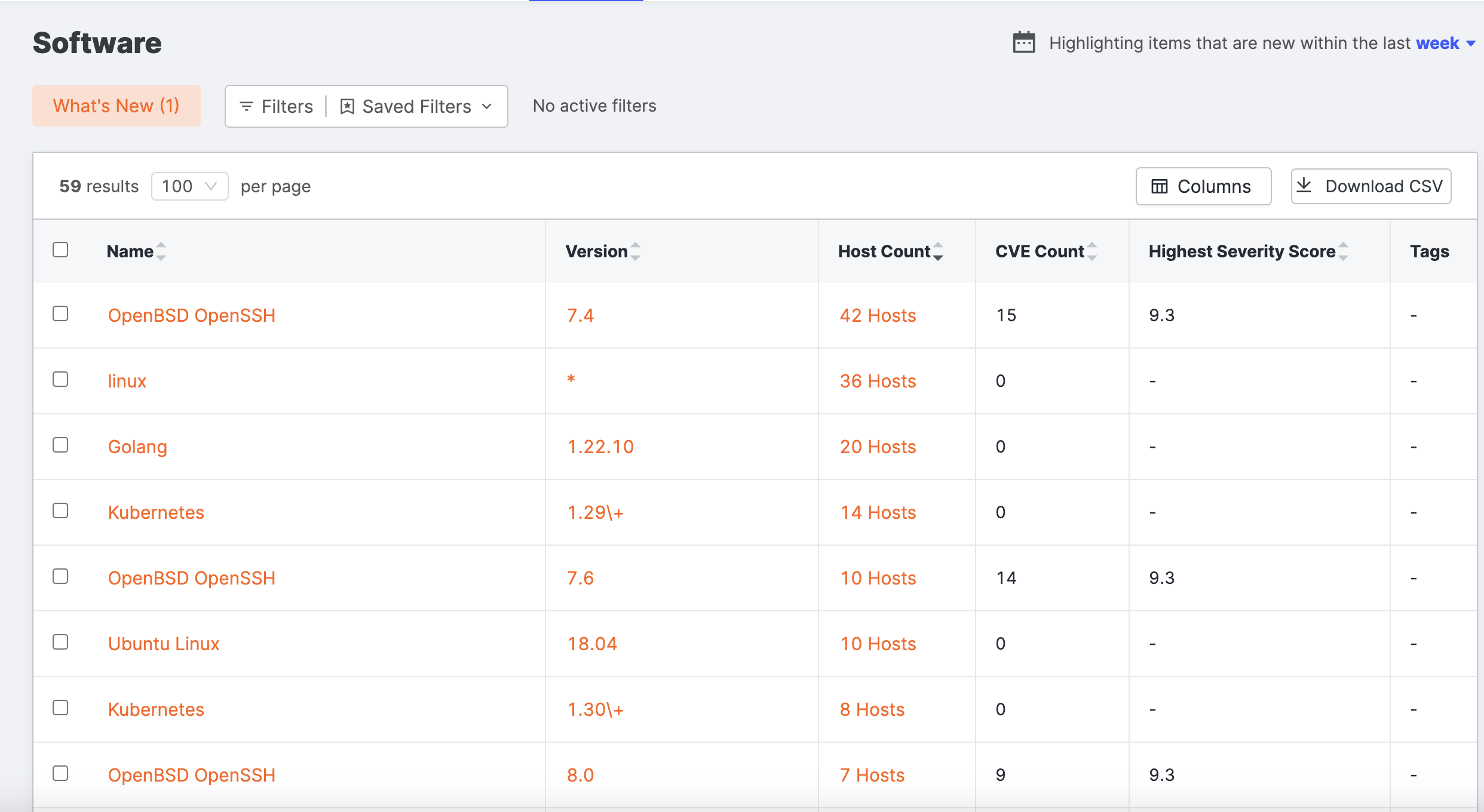
Go to the ASM web console and click Inventory > Software.
-
Sort the columns to find what you want to focus on.
- Name: The name of the software.
- Version: The version of the software reported by one or more of your hosts. The software name + version is tied to a vulnerability (known as a CVE-ID) from the Common Vulnerabilities and Exposures (CVE) dictionary. In accordance with the CPE format, an asterisk (*) appears in the column when the version is unknown. The same name can appear in the list more than 1 time because the versions are different.
- Host Count: The number of your hosts that are reporting this software version.
- CVE Count: The number of CVE-IDs associated with this software version.
- Highest Severity Score: The severity score of the most critical CVE ID tied to the software. Severity scores range from 0-10. A higher score is more critical.
- Tags: Any tags applied to the software version.
-
Click the link in the Host Count column to view all the hosts with a specific software severity issue.
-
Click Asset ID to view specific details about the asset. This information can help you learn more about this host, such as where it is and what the issues are.
NoteWhen Censys uses the term severity score in relation to CVEs, it is referring to the National Vulnerabilities Database’s Common Vulnerabilities Scoring System (CVSS) Version 2, an industry standard.
Add or remove columns
You can view additional columns with more information about your software by clicking Columns above the table.
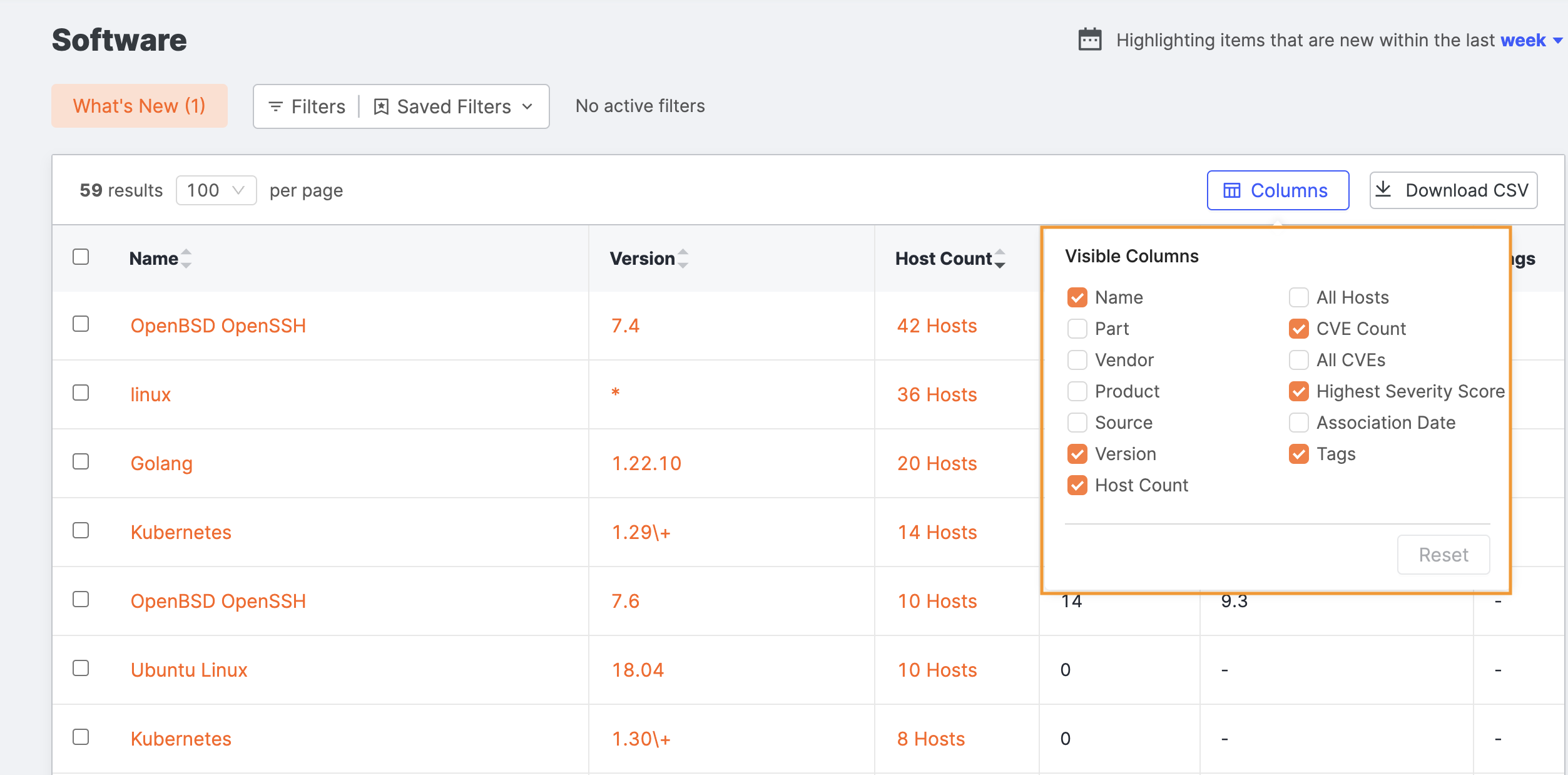
Select or clear the columns to create your view. Additional column options include:
- Part: A type enumeration. Values include:
- Application
- Hardware
- Operating System
- Vendor: The name of the organization providing the software.
- Product: The name of the system, package, or component. Product and vendor are sometimes identical.
- Source: A Censys-specific field indicating the identification of the software. Values include:
- Fingerprint: A Censys mapping of software indicated during protocol-specific scans to CPE-formatted software URIs.
- Server: A string pulled from the HTTP server header that had no fingerprint match.
- X-Powered-by: A string pulled from the HTTP x-powered-by header that had no fingerprint match.
- All Hosts: A list of the IP addresses of the hosts running the software version.
- All CVEs: A list of all of the CVE IDs associated with the software version.
- Association Date: The date that the software version was first seen on one of your hosts.
Download software data
After you create a view, you can export the software catalog as a comma-separated value (CSV) file for use in other products and workflows.
-
Set up the view with the information you want to download.
-
Click Download CSV in the right corner. The filename is
{timestamp}_{customerName}_SoftwareExport.csv
Updated 11 months ago
