ASM Activity Logbook
ASM tracks and reports when changes take place in your attack surface in the following categories:
Categories
- Certificate
- Host
- Port
- Domain
- Name server
- Storage bucket
- Vulnerability (CVE)
- Host risk
- Protocol
- Domain risk
- Domain register
- Host/certificate association
- Modified risk
- Software
- Mail exchange server
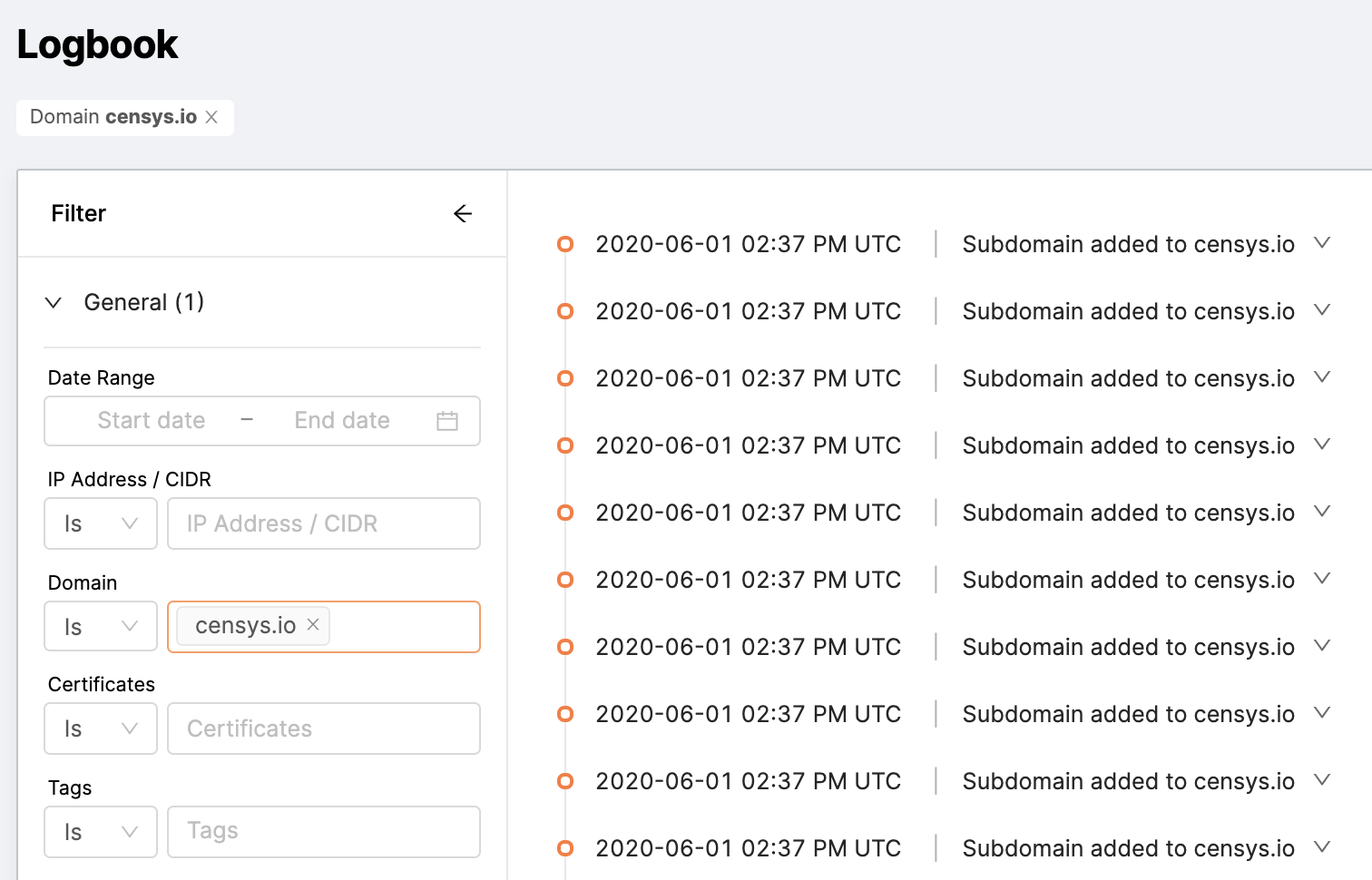
- Subdomain
The Logbook is a changelog of activity related to your assets. The log is sorted by timestamp, with the most recent events on top.
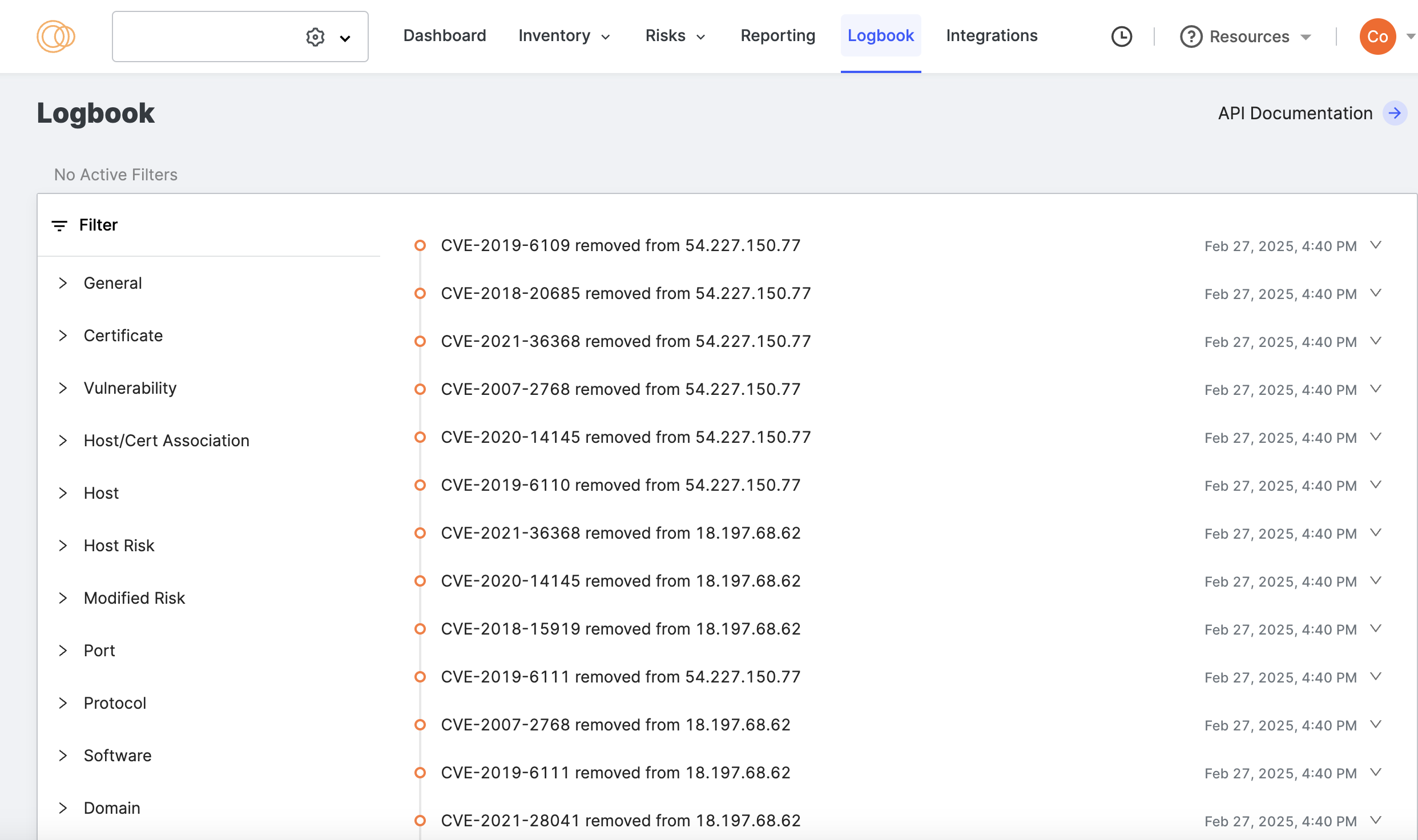
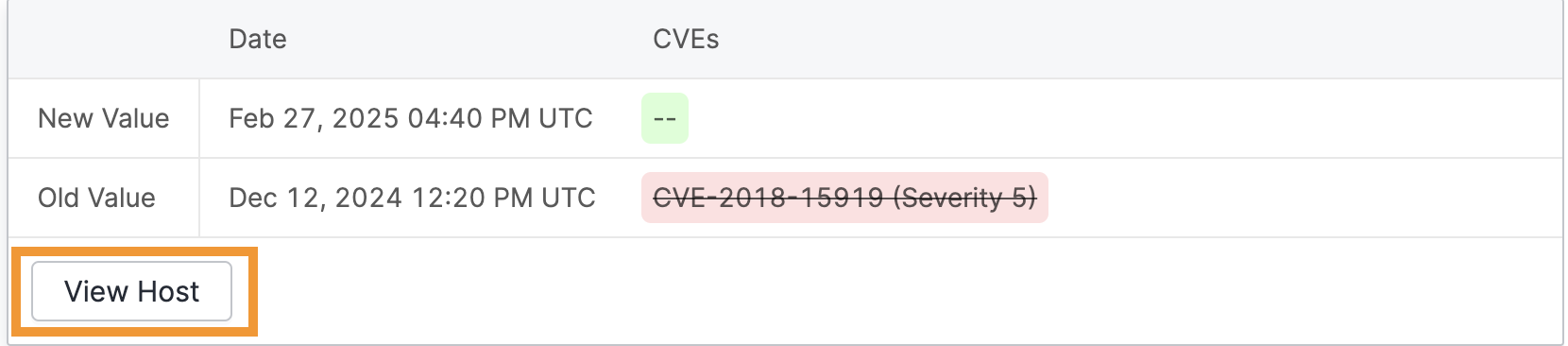
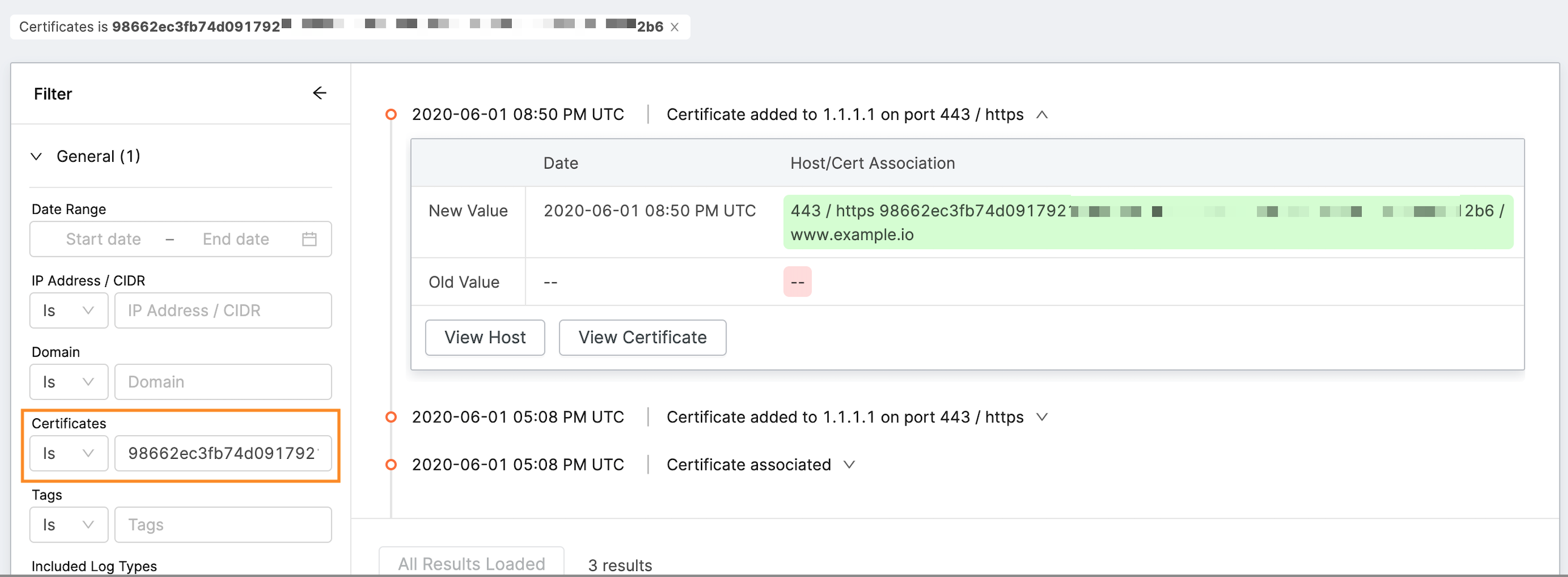
You can expand any row to see more information about the event, including a diff of the entity. Buttons linking to the asset(s) let you navigate to those pages for further investigation.
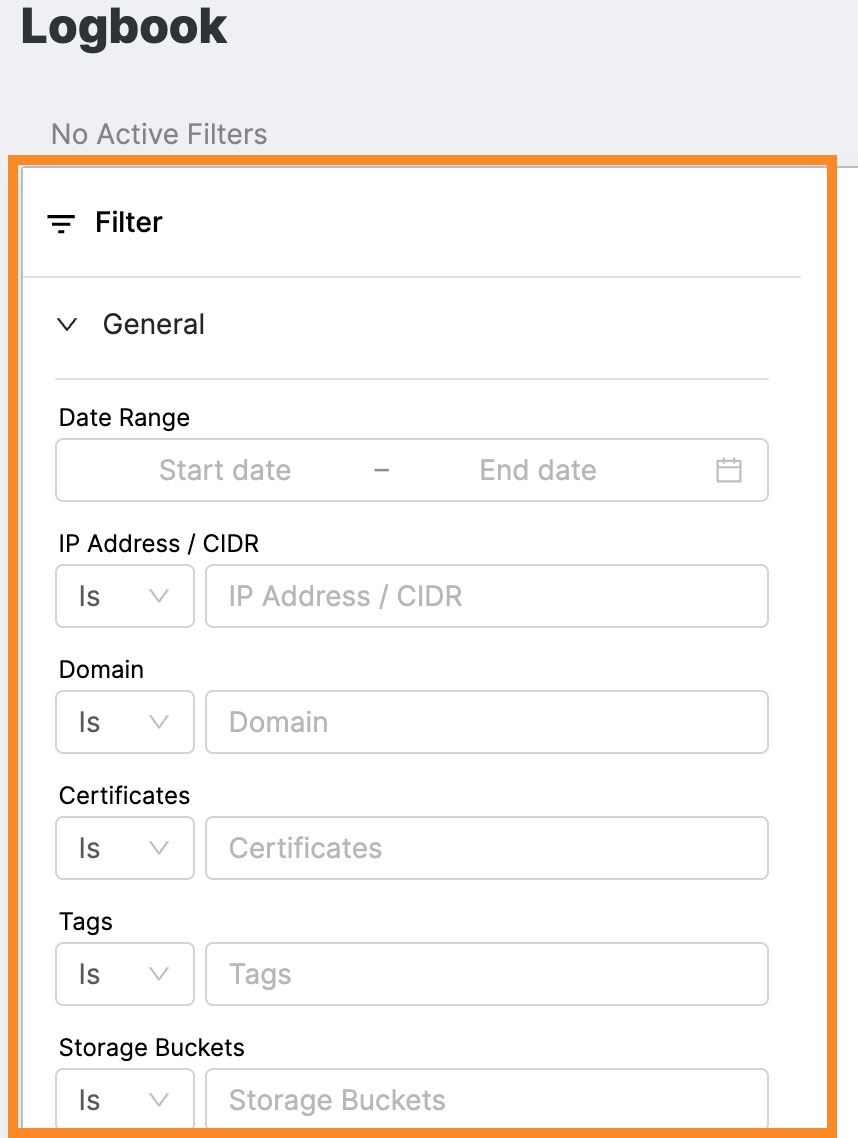
Filters
Apply filters to see events that meet specific criteria.
General
General filters allow you to narrow the scope of Logbook events in the list by including or excluding events that share characteristics or top-level asset identifiers.
-
Date Range: A time period during which event(s) occurred. By default, all events from all time are shown. Timestamps for logbook events reflect when the event was entered into the logbook. Read the definition of the event carefully to understand how the timestamp applies.
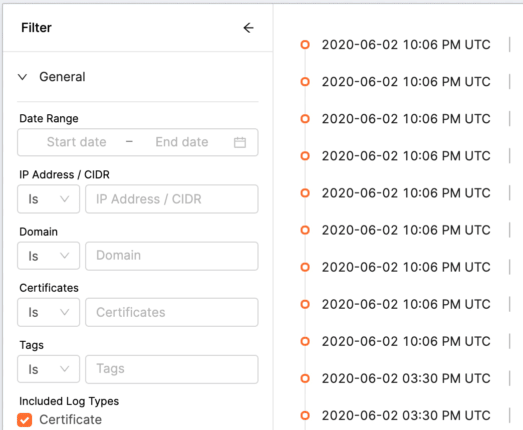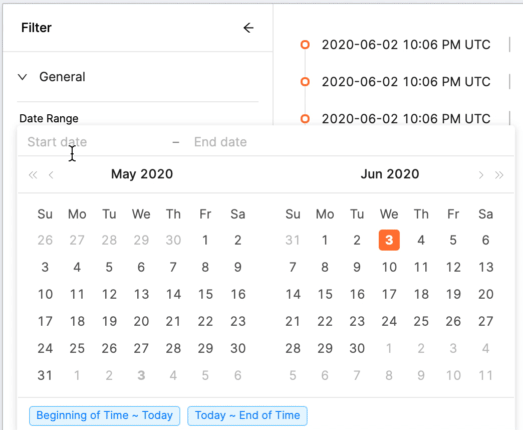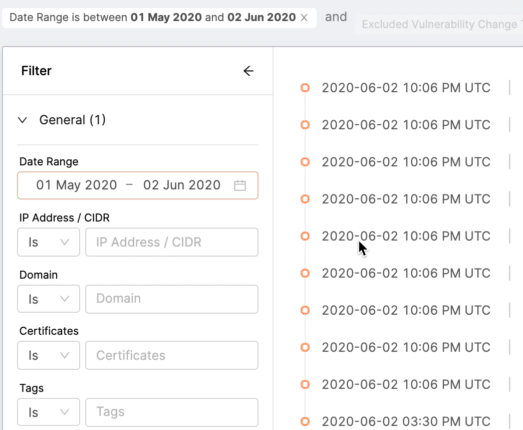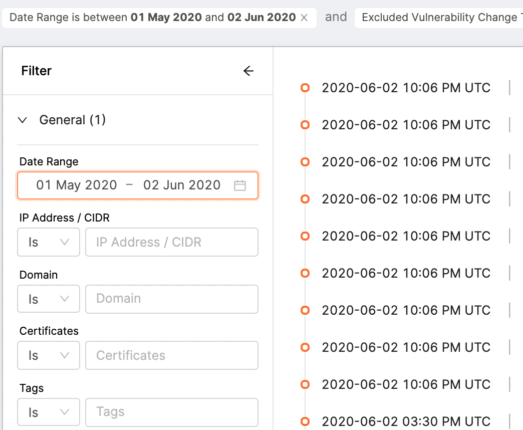
-
IP Address/CIDR (Classless Inter-Domain Routing): An IP address or block of IP addresses in your attack surface.
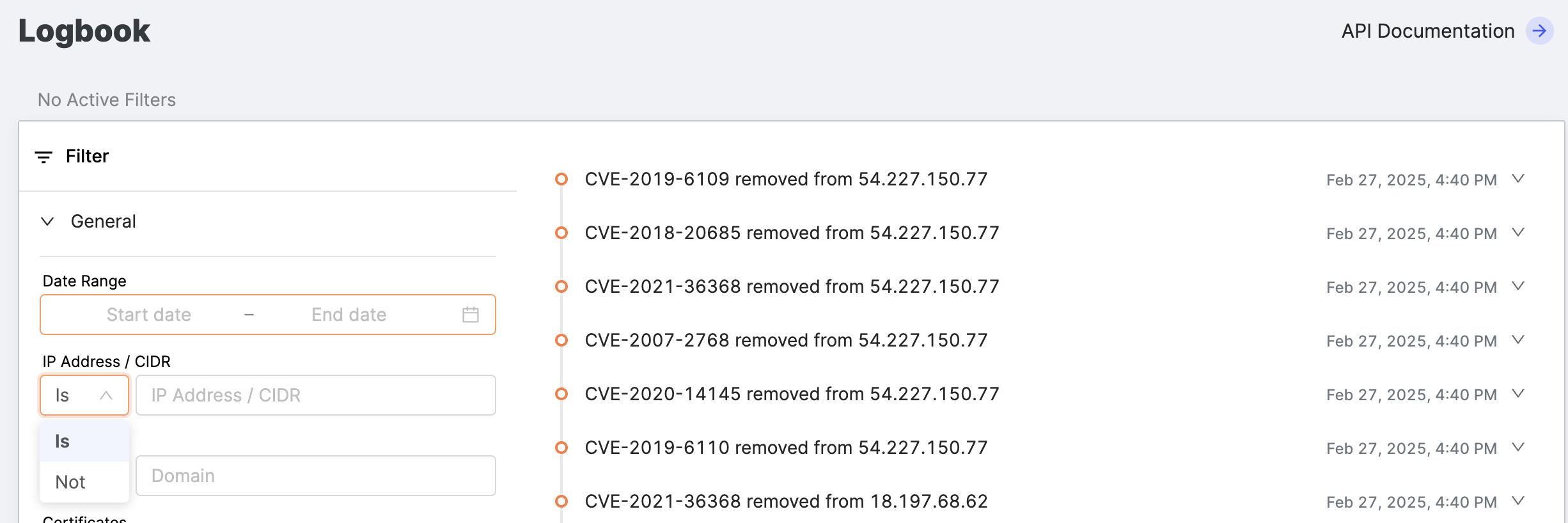
-
Domain: An apex domain you own.
-
Certificate: The SHA-256 fingerprint of a TLS certificate you own.
-
Tags: Any tags applied to this asset.
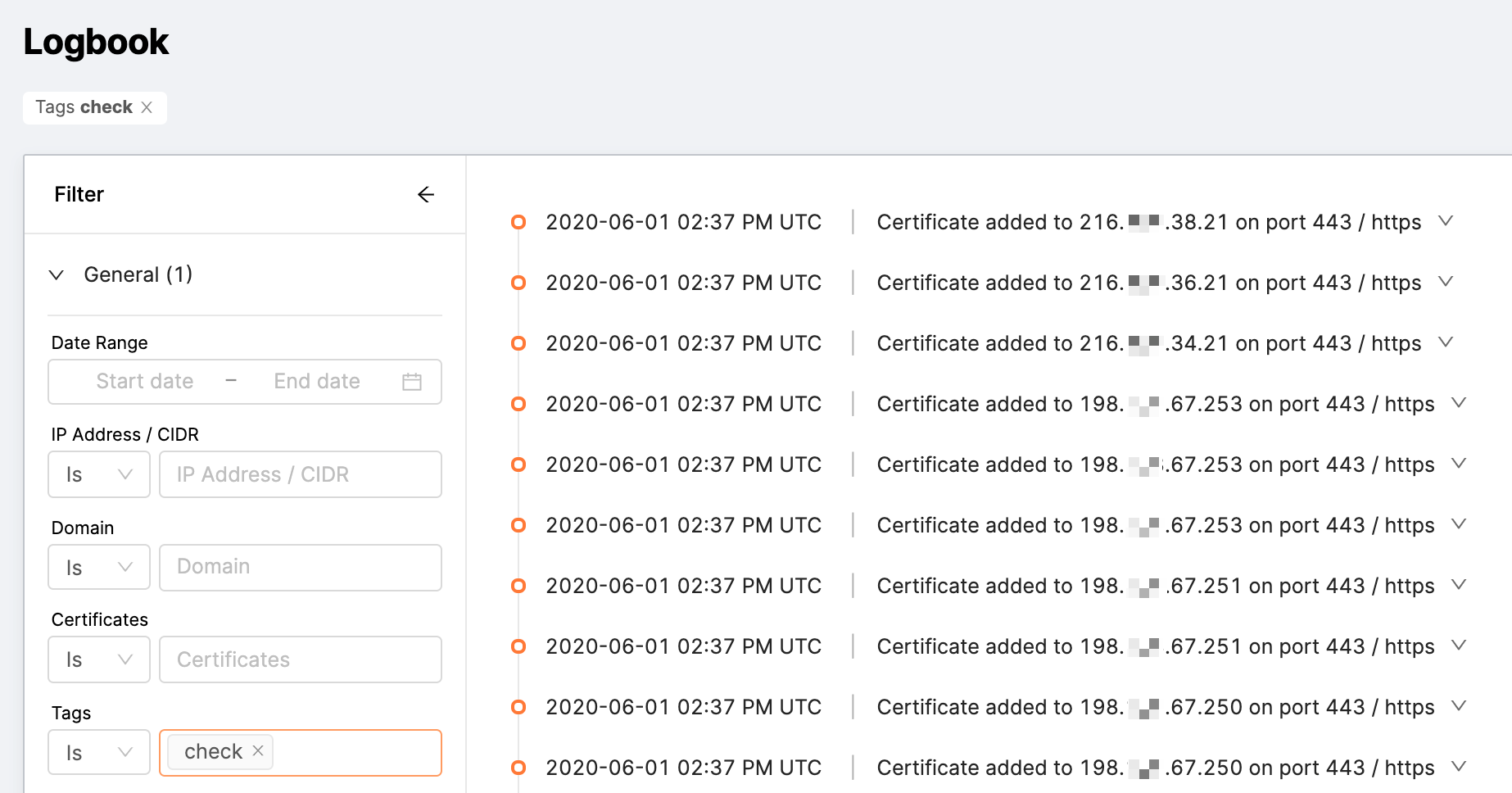
-
Included Log Types: Types of events that you can hide from the view or restrict the view to.
Certificate
Use the Certificate filter to see when certificates were associated to your organization (Associate) or when they were removed (Disassociate).
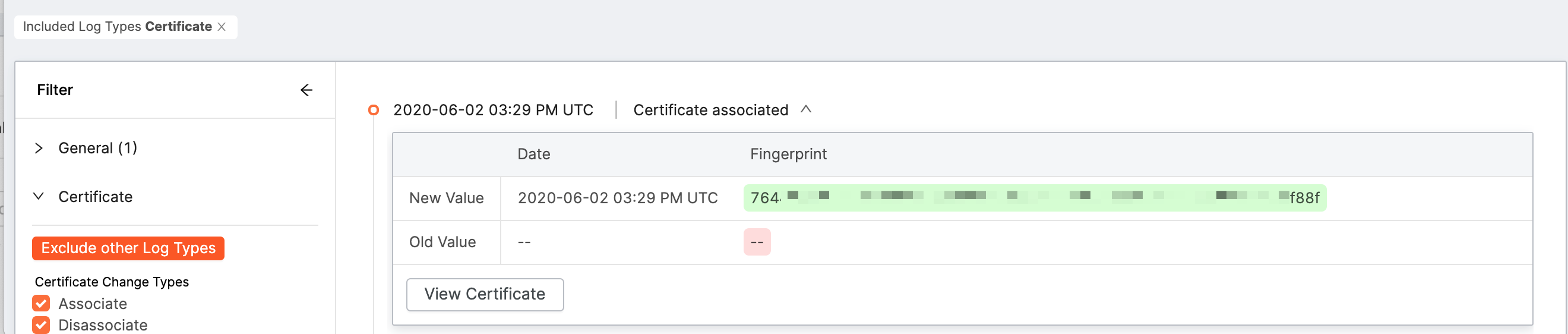
A certificate associate event can occur in the following circumstances:
- Your TLS Certificate Issuer issued you a new certificate (perhaps your old one expired), which we discovered in our scan.
- In following the connections between Internet objects, Censys global scanning engine finds an existing certificate of yours that it has never seen before and adds it to your asset collection.
A certificate disassociate event occurs when a certificate is no longer connected to other assets belonging to your organization.
Vulnerability (CVE)
With the Vulnerability filter, you can restrict the view to only vulnerability event types and then filter those events by CVE-ID, CVSS score, or when a vulnerability was added to a host (Add), removed from a host (Remove), or when the CVE-ID itself was updated (Change).
A vulnerability Add event can occur in the following circumstances.
- A new host running a certain software with a CVE-ID was attributed to your organization. In this case, other preceding events, such as Host Associate and Software Add events, accompany the Vulnerability Add event.
- A host belonging to your organization reports a new software package or version, and a CVE-ID is found for that version. In this case, other preceding events, such as Software Remove, Vulnerability Remove, and Software Add events, accompany the Vulnerability Add event.
A vulnerability Remove event can occur in the following circumstances.
- A host that was running a certain software with a CVE-ID was disassociated with your organization. In this case, other preceding events, such as Host Disassociate and Software Remove events, accompany the Vulnerability Remove event.
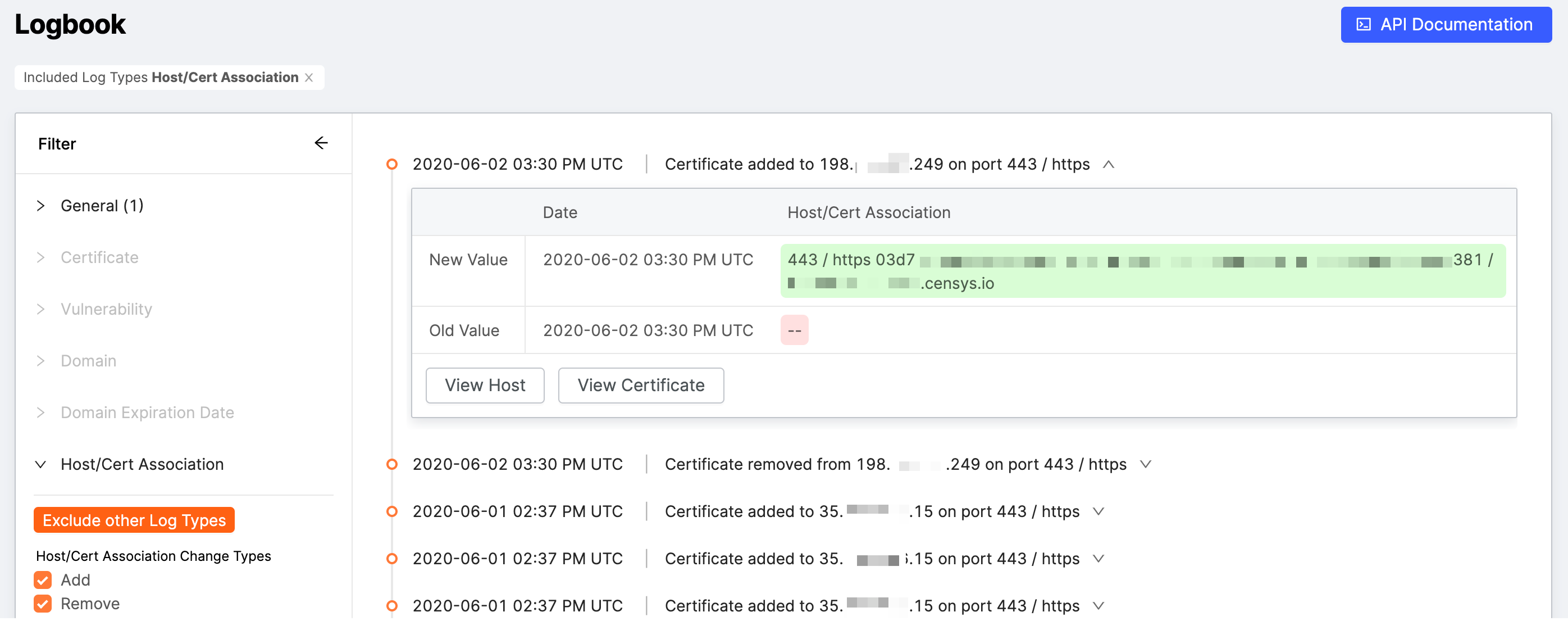
Host/Cert Association
With the Host/Cert Association filter, you can see when a certificate was seen on a host (Add) or not seen on a host (Remove).
Updated 23 days ago
