Platform MCP Server
Use the Platform Model Context Protocol (MCP) Server to give your AI agents and workflows secure, governed, and direct access to the entire Censys Internet Map and Platform APIs, empowering you to hunt, triage, and respond at machine speed.
MCP is an open standard designed by Anthropic to help AI agents leverage trusted external data and tools.
The MCP Server is a service hosted by Censys that you can integrate with tools like Cursor, Claude Code, and Continue.dev. The server can be used by any Platform user with access to the API. API calls executed via integration with the server count against your credit balance.
Prerequisites
- Obtain or set up a Platform Personal Access Token (PAT).
- You must have the API Access role to create a PAT.
- Obtain your Platform organization ID.
Integrate with the Censys hosted MCP Server
Use the instructions below to integrate the Censys hosted MCP Server with your tools. Note that the following are just some examples; the MCP Server can be incorporated into many different applications.
Add the following to your Cursor MCP configuration file (~/.cursor/mcp.json). You can access this file in the UI by going to Cursor Settings > Tools & Integrations and clicking + New MCP Server.
{
"mcpServers": {
"censys-platform": {
"url": "https://mcp.platform.censys.io/platform/mcp/",
"headers": {
"X-Organization-ID": "your-organization-id",
"Authorization": "Bearer your-censys-personal-access-token"
}
}
}
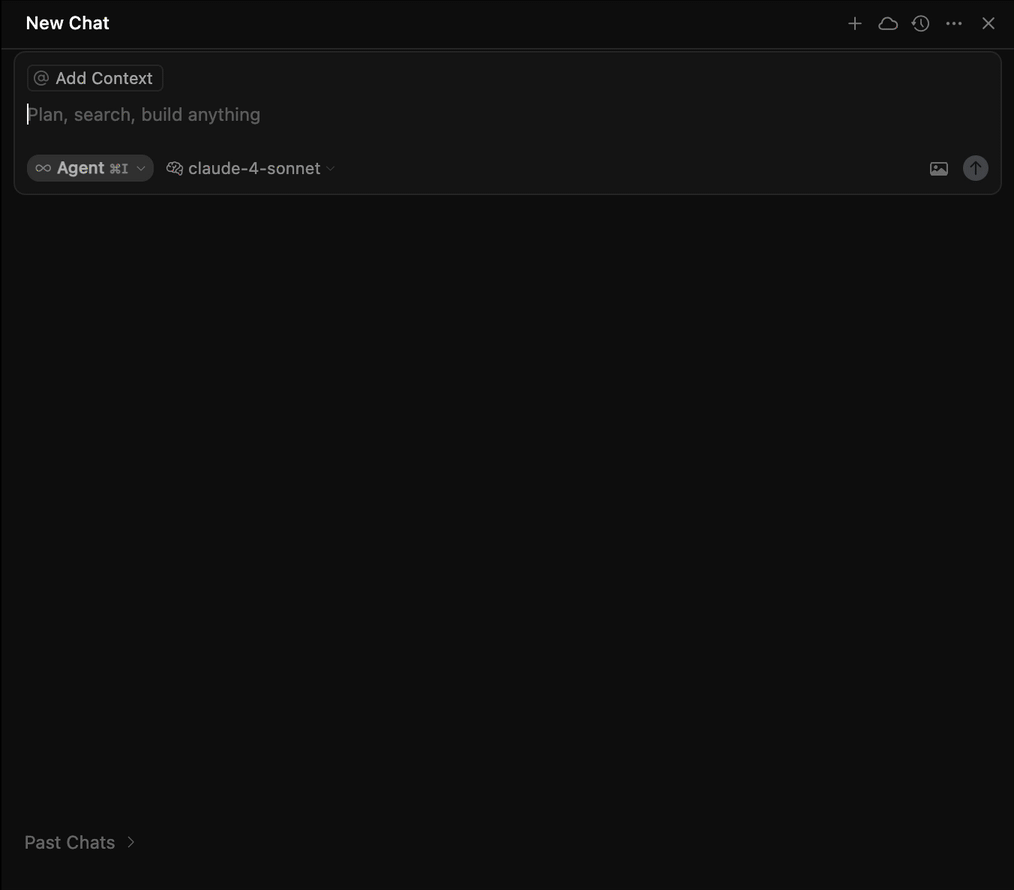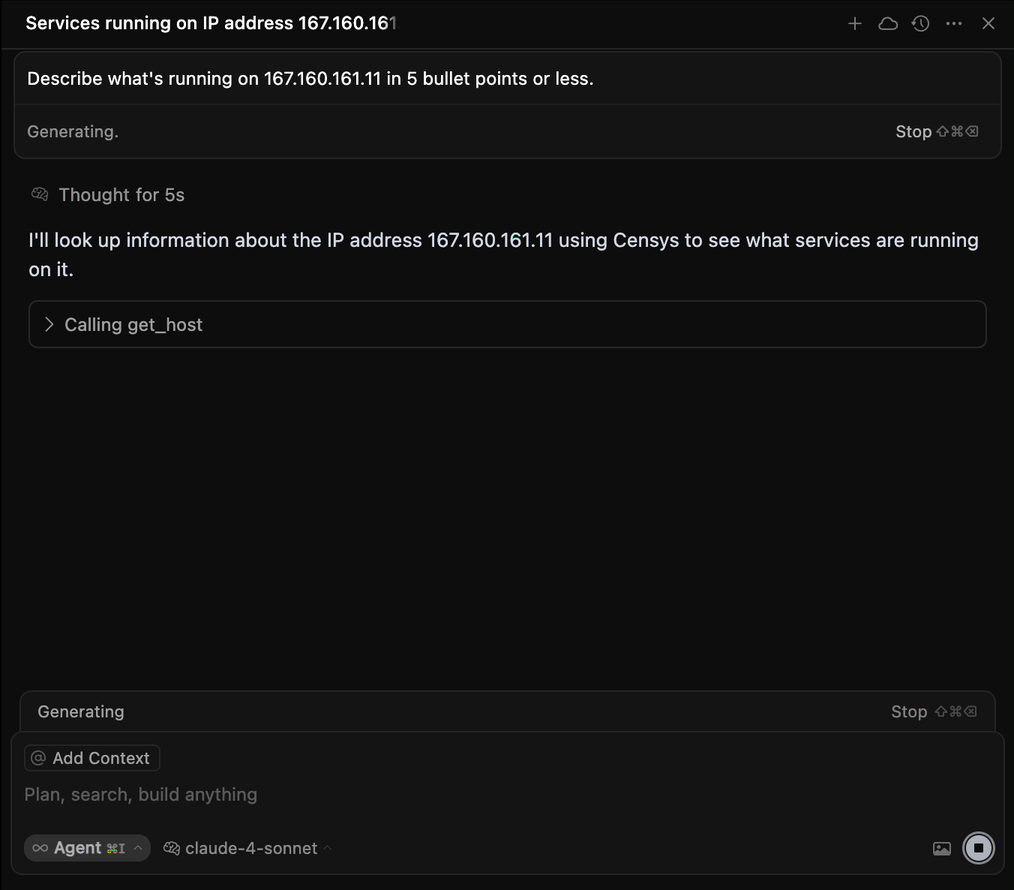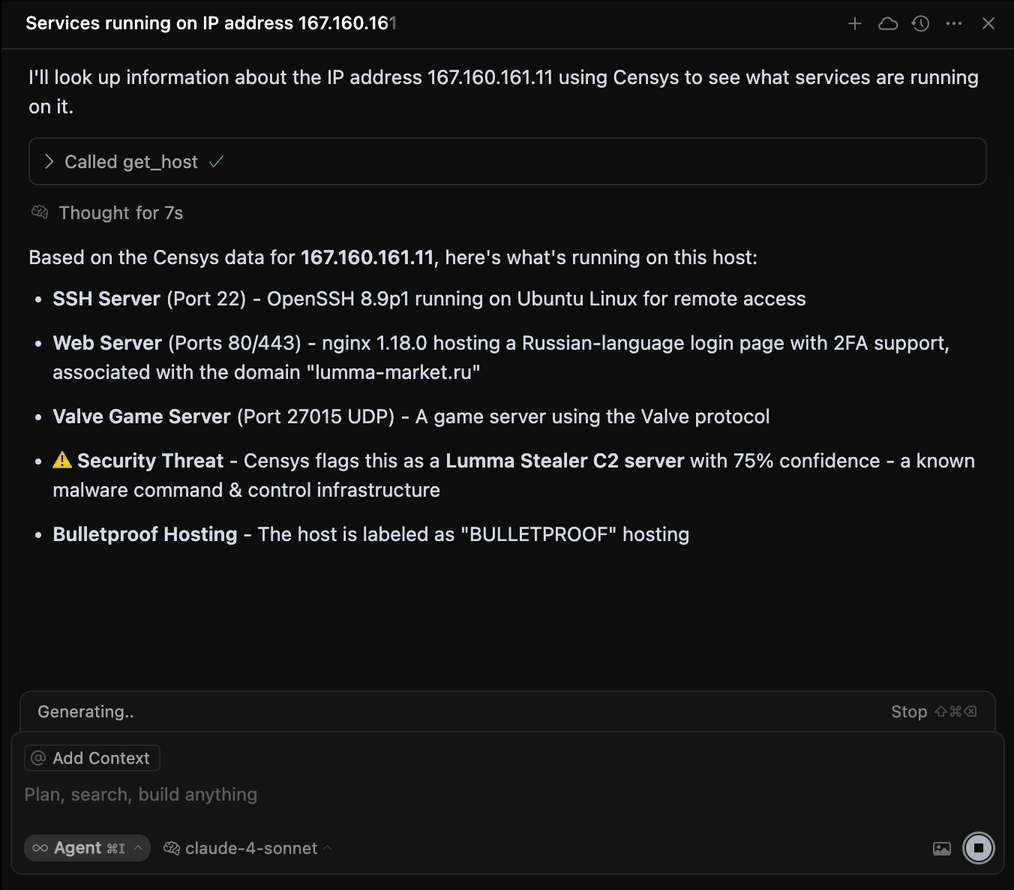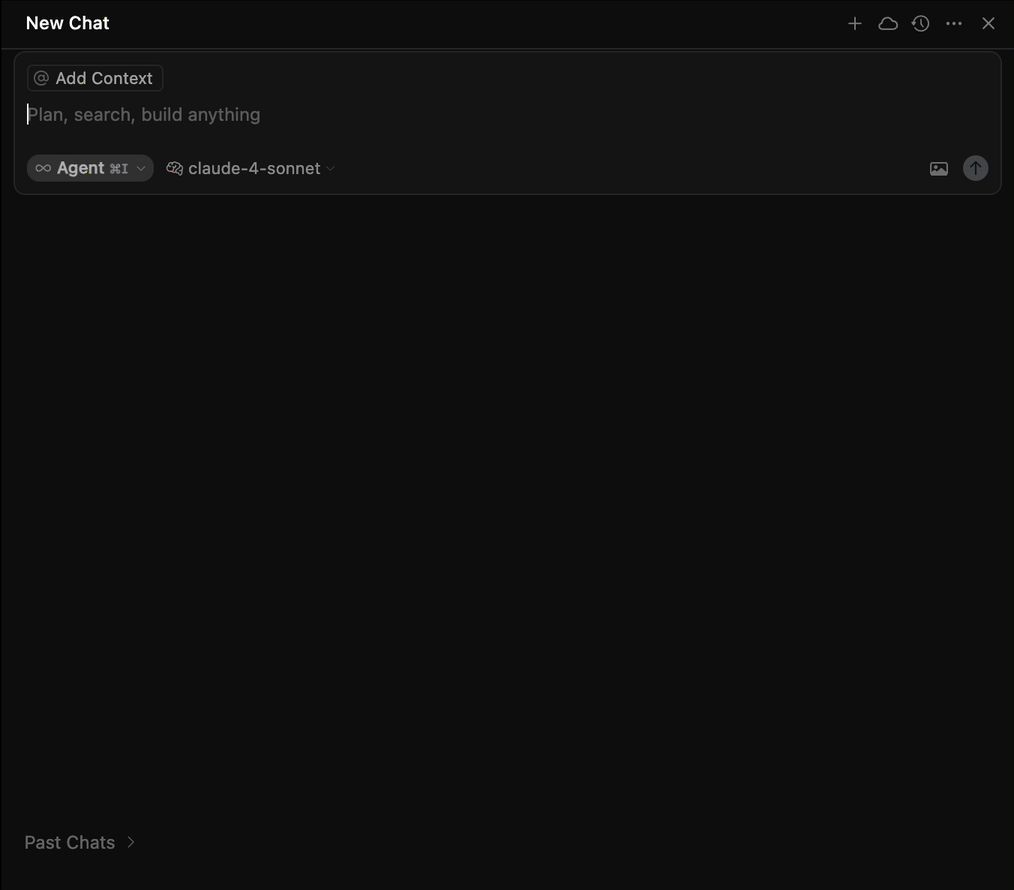
}After configuring your integration, test it by prompting your agent with a question like "What services are running on 8.8.8.8?"
The output may depend on your specific configuration, but your agent should use a GET HOST Platform API endpoint to retrieve information about the host and provide a human-readable summary.
Example use cases
The MCP Server currently works best for retrieving and summarizing information about individual or bulk web assets and pivoting from information obtained from those lookups.
Investigate and pivot from a suspicious IP or web property
- Use your AI agent to look up details about the host or web property a system in your environment has connected to using input like "what services are running on 1.1.1.1?"
- If the asset appears unremarkable in its current state, instruct your agent to investigate the asset's history in a time frame that interests you.
- If you obtain values of interest, instruct your agent to perform additional searches using those values to find related infrastructure. For example, prompt it to find other host services or web properties running the same certificates that you found on your first host or web property.
- If you are able to identify indicators of interest, instruct your agent to build a collection targeting those indicators. Then, set up alerts to receive notifications about changes to the collection.
Gain visibility into exposed assets
- Instruct your agent to search your organization's CIDR.
- Identify host services associated with your organization that should not be exposed.
- Use your agent to investigate the history of a host with an exposed service to identify when the service was exposed.
- Remediate the exposure and consider using your agent to build a collection monitor for additional exposures.
Platform MCP tools
In addition to functionality that is equivalent to the Platform APIs, the Platform MCP server features the following tools.
| Tool | Description |
|---|---|
retrieve_cve_details | Discovers which internet-facing systems are affected by security vulnerabilities. Uses the CVE ID format CVE-YYYY-NNNNN. |
validate_censys_query | Checks field names, suggests corrections, and validates search query structure to avoid syntax errors. |
search_field_help | Discovers relevant fields for your search when unsure about exact field names. |
get_query_examples | Uses proven, working examples of Platform queries to learn proper query syntax and find starting points for searches with validated examples. |
list_available_data_definition_groups | List all available data schema groups (such as host, certificate, or web property) that define searchable fields in the Platform to understand what types of data you can search and analyze, organized by asset type. |
list_available_data_definitions | Shows all searchable field names available for a data type. |
get_data_definition | Provides comprehensive documentation of a field including description, data type, and usage examples. |
generate_query | Converts natural language requests into valid CenQL queries. |
investigate_cve | Investigates a specific CVE vulnerability across the internet to provide comprehensive threat intelligence. |
investigate_host | Conducts comprehensive security analysis of a specific IP address. |
discover_attack_surface | Automatically searches for organization assets, analyzes exposed services, identifies security risks, and provides comprehensive attack surface assessment. |
generate_and_search_query | Generates a Censys search query from natural language and searches the query. |
Updated about 1 month ago
