CVE Risks
In Censys Attack Surface Management (ASM), you can leverage Common Vulnerabilities and Exposures (CVE) data, Known Exploited Vulnerability (KEV) information, and the Common Vulnerability Scoring System (CVSS) to quickly prioritize vulnerabilities and initiate remediation.
CVEs are common identifiers for publicly-known security vulnerabilities. Their severity is determined based on CVSS scores. CVSSv4, v3, and v2 are supported though not all CVE risks will have a score using each methodology. If a CVE is on the Cybersecurity and Infrastructure Security Agency (CISA) KEV list, it is listed as a "KEV" CVE. This list includes any CVEs that CISA has verified as exploited in the wild. With the CVE risk feature, these metrics are tracked for all software detected in Censys Attack Surface Management.
When a new CVE is cataloged by the National Vulnerability Database (NVD), it becomes discoverable in Censys ASM alongside its CVSS score within 24 hours. When Censys discovers new software in a given attack surface, Censys maps all known CVEs for that software and presents them as risks. Use the CVSS score and KEV flag to understand the severity and exploitability of the vulnerability immediately.
By default, only CVEs that match the following criteria are enabled:
- CVSS Score High to Critical
- Present in KEV catalog
- Network Attack Vector
CVE risk information
On the Risk Instances page in the ASM web interface, you can see CVE risks for new, active, and closed software vulnerability risks. On the Risk Instances page, CVE risks are shown using the following format: “Vulnerable [software vendor] [software product] [associated CVE count]”. The associated CVE count links to a table in which you can see all of the individual CVEs associated with the software.
NoteOn the Risk Instances page, risks with the naming format
“Vulnerable [software product] [CVE ID]”, such as“Vulnerable OpenSSH [CVE-2024-6387]”are rapid response risks.Rapid response risks do not include CVSS scores, KEV catalog information, nor attack vector information.
CVE risk data access
CVE risks are available to all ASM customers. However, certain CVE risk data is only available to customers who have access to CVE risk exploit context. CVE risk exploit context is available to all ASM Enterprise customers and may be purchased as an add-on by ASM Advanced customers. The following table describes CVE risk data access in greater detail.
| CVE risk data feature | Available to Core/SMB | Available to Advanced | Available to Enterprise |
|---|---|---|---|
| CVSSv3 and v2 scores | Yes | Yes | Yes |
| KEV catalog presence | Yes | Yes | Yes |
| Network Attack Vector information | Yes | Yes | Yes |
| CVSSv4 scores | No | Yes, if CVE exploit context add-on purchased | Yes, included as part of Enterprise plan |
| Exploit Prediction Scoring System (EPSS) scores | No | Yes, if CVE exploit context add-on purchased | Yes, included as part of Enterprise plan |
| Exploit maturity information | No | Yes, if CVE exploit context add-on purchased | Yes, included as part of Enterprise plan |
| Threat actor, botnet, and ransomware enrichment for CVE risks | No | Yes, if CVE exploit context add-on purchased | Yes, included as part of Enterprise plan |
View CVE context on the Risk Instances page
-
Log in to the ASM web console and click Risks > Risk Instances at the top of the page.
-
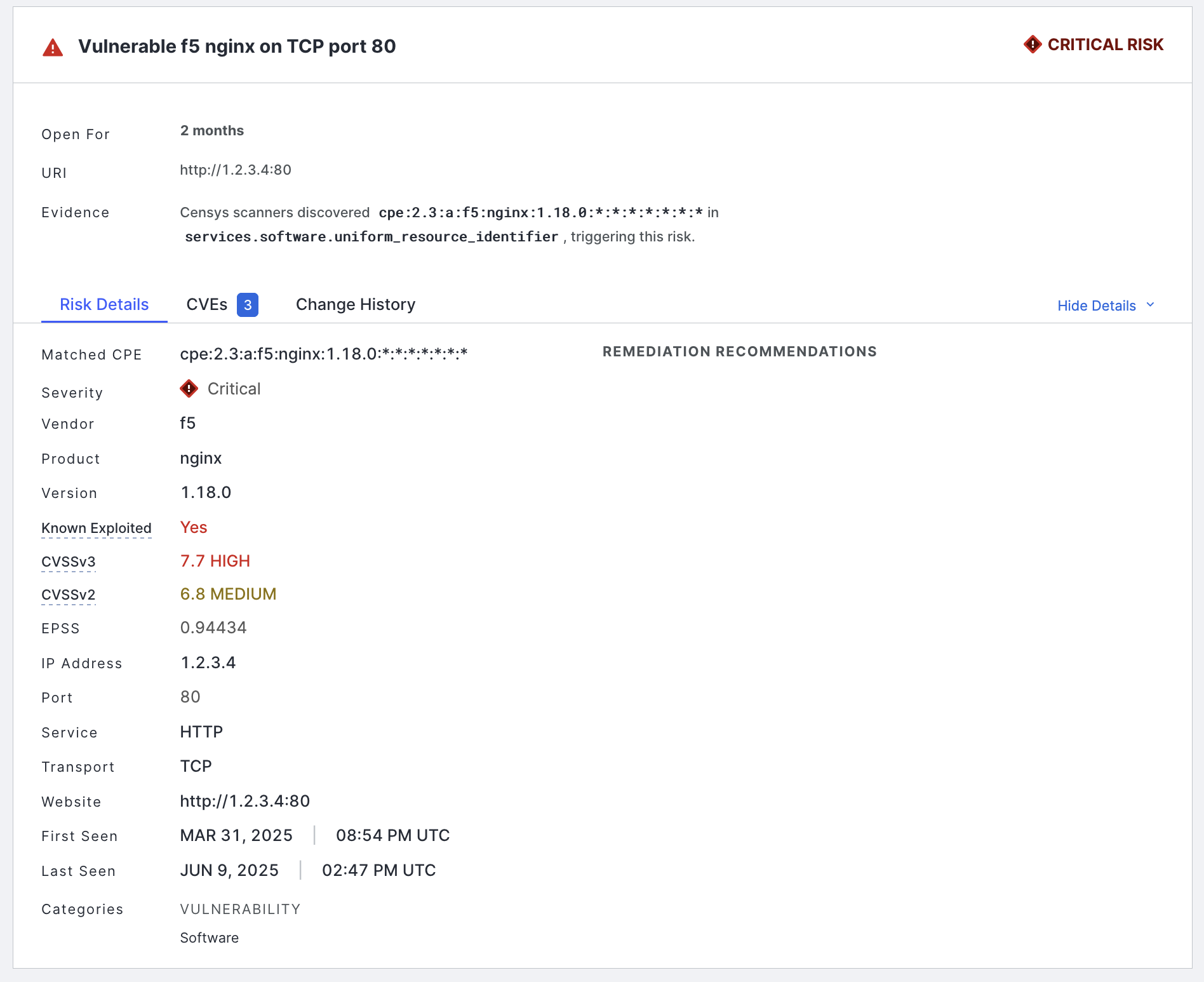
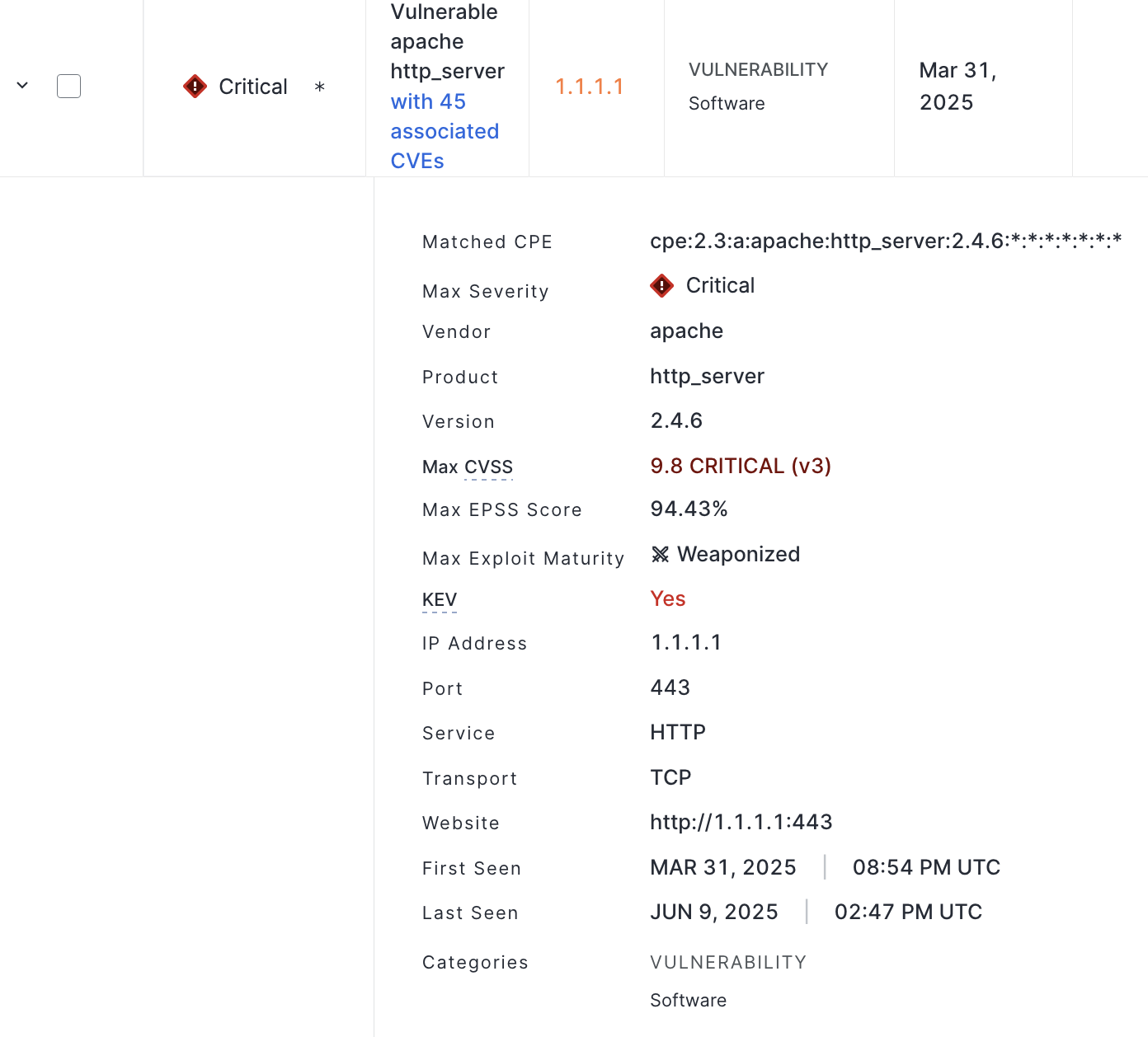
On the left side of a CVE risk entry for an asset, to the left of the checkbox, click the chevron icon to expand its details. A summary of information about the CVE or CVEs associated with software is shown, including the following. Note that some information may not be displayed depending on whether you have access to additional CVE exploit context data (see the table above).
-
The CPE string used to identify the software.
-
The maximum severity level of associated CVEs.
-
The vendor name.
-
The product name.
-
The product version.
-
The maximum CVSS score and its attendant scoring methodology.
-
The maximum EPSS score.
-
The maximum exploit maturity classification (Weaponized, PoC, or Unreported).
- Unreported: There has been no reported proof-of-concept (PoC) nor weaponization of this vulnerability.
- PoC: A proof-of-concept for how to exploit this vulnerability has been released publicly or privately.
- Weaponized: This vulnerability has been exploited by a threat.
-
Whether any of the associated vulnerabilities are present in CISA’s KEV catalog.
-
The highest CVSSv3 score of associated vulnerabilities.
-
The highest CVSSv2 score of associated vulnerabilities.
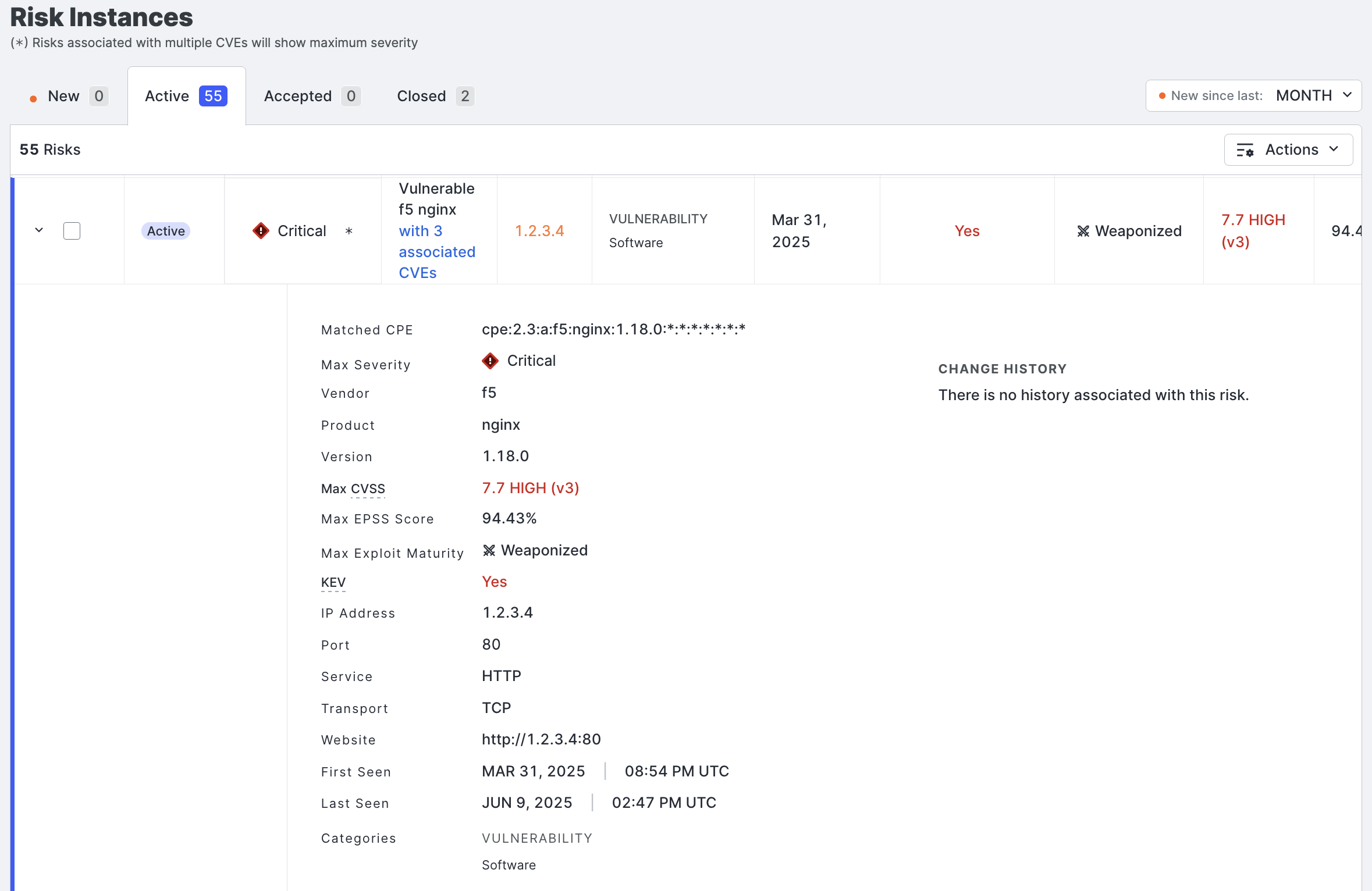
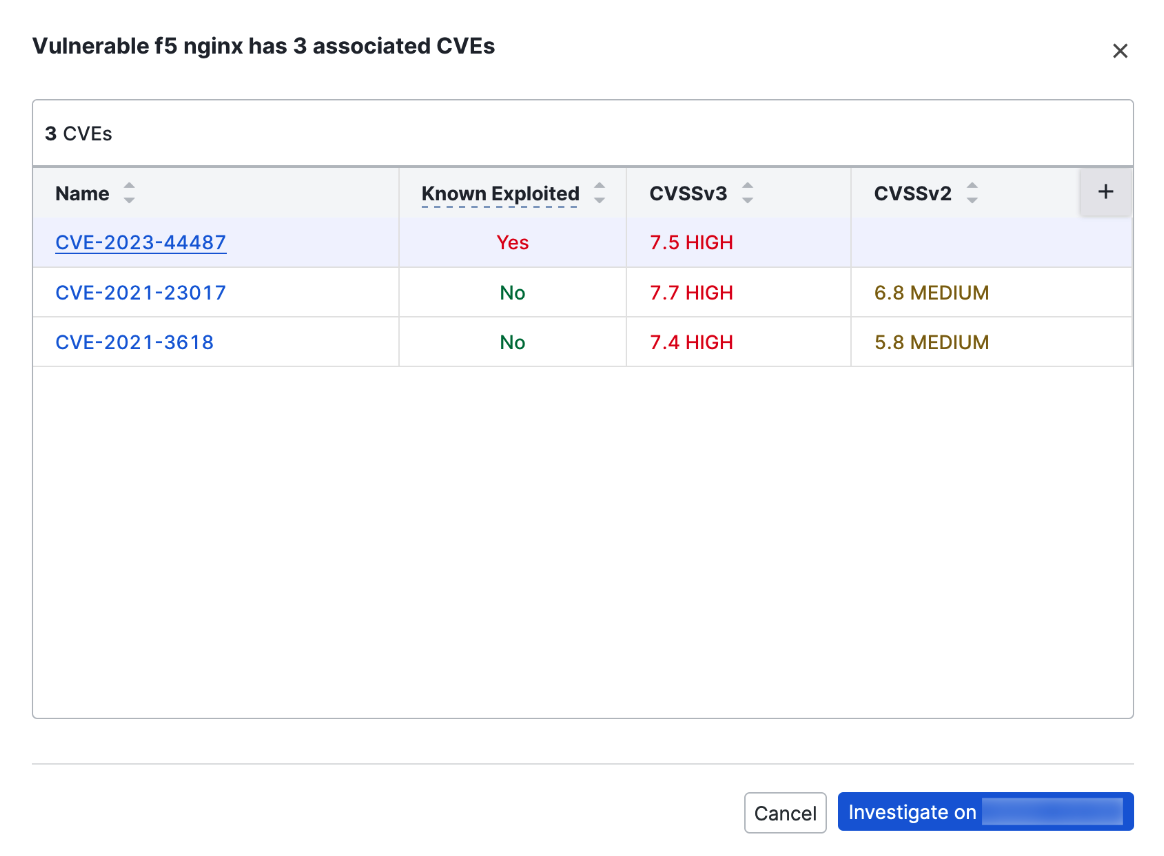
In this example screenshot, three CVE risks have been detected for this instance of F5 nginx. Not that this screenshot displays information available in the CVE exploit context add-on.
-
-
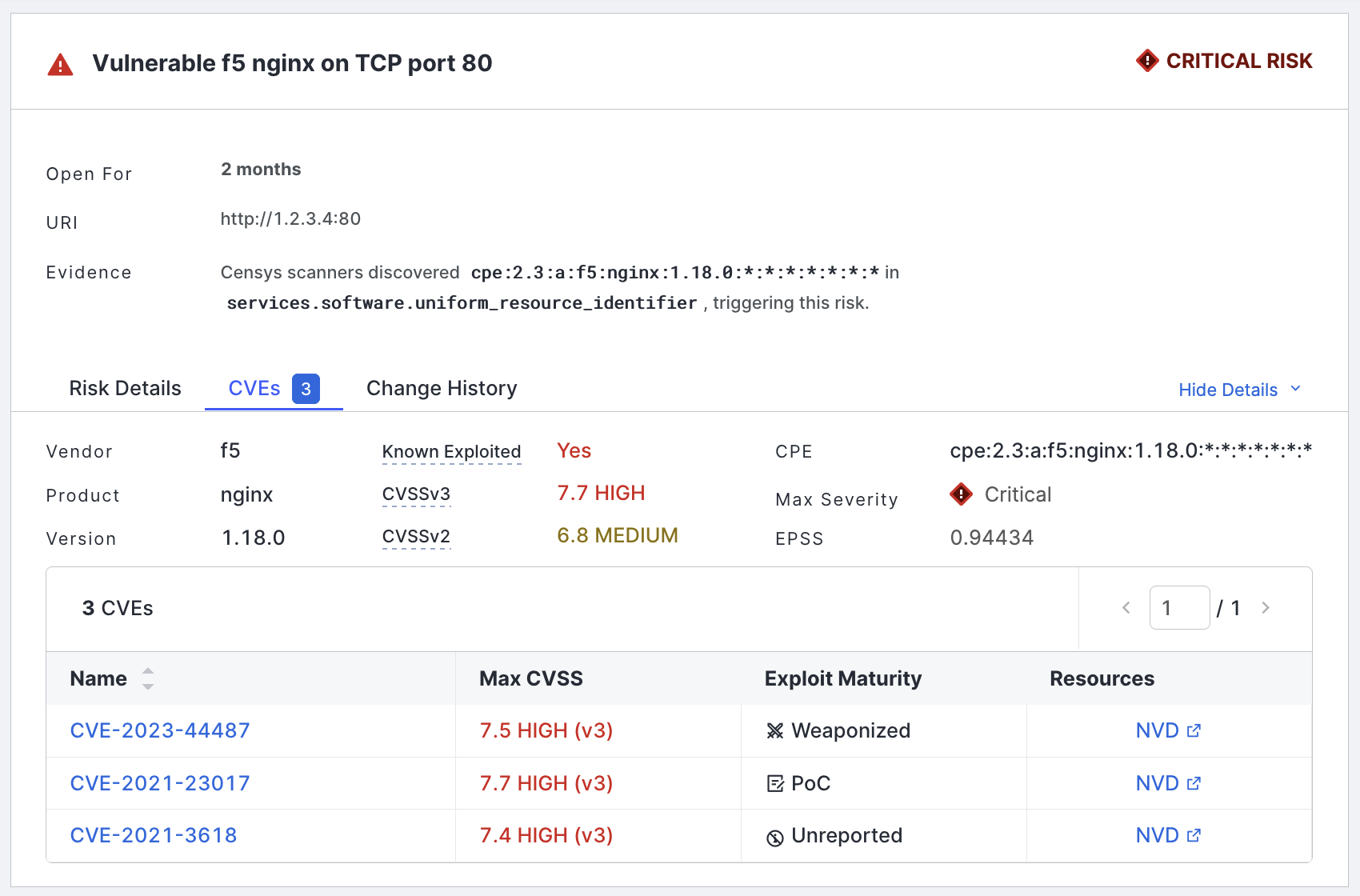
Click the link to see the full list of CVEs.
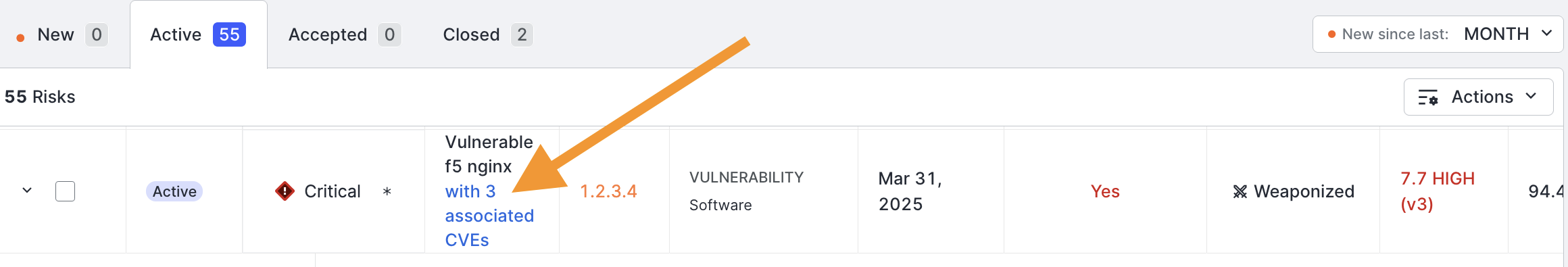
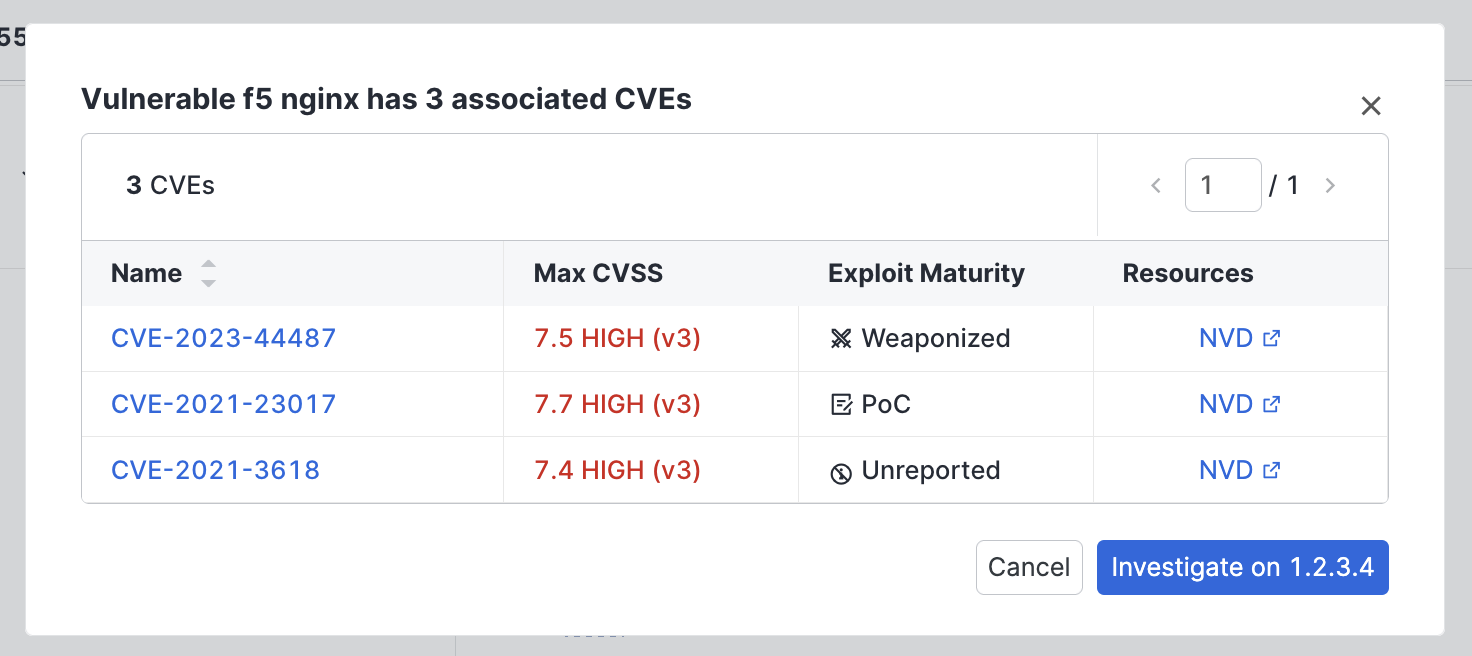
In this list, you can see each CVE ID, its max CVSS score, exploit maturity, and a link to the vulnerability's entry in the National Vulnerability Database (NVD).
-
Click a CVE link to see more information about that vulnerability, including its description, a timeline of events related to the vulnerability, associated threat actors, and links to exploit information.
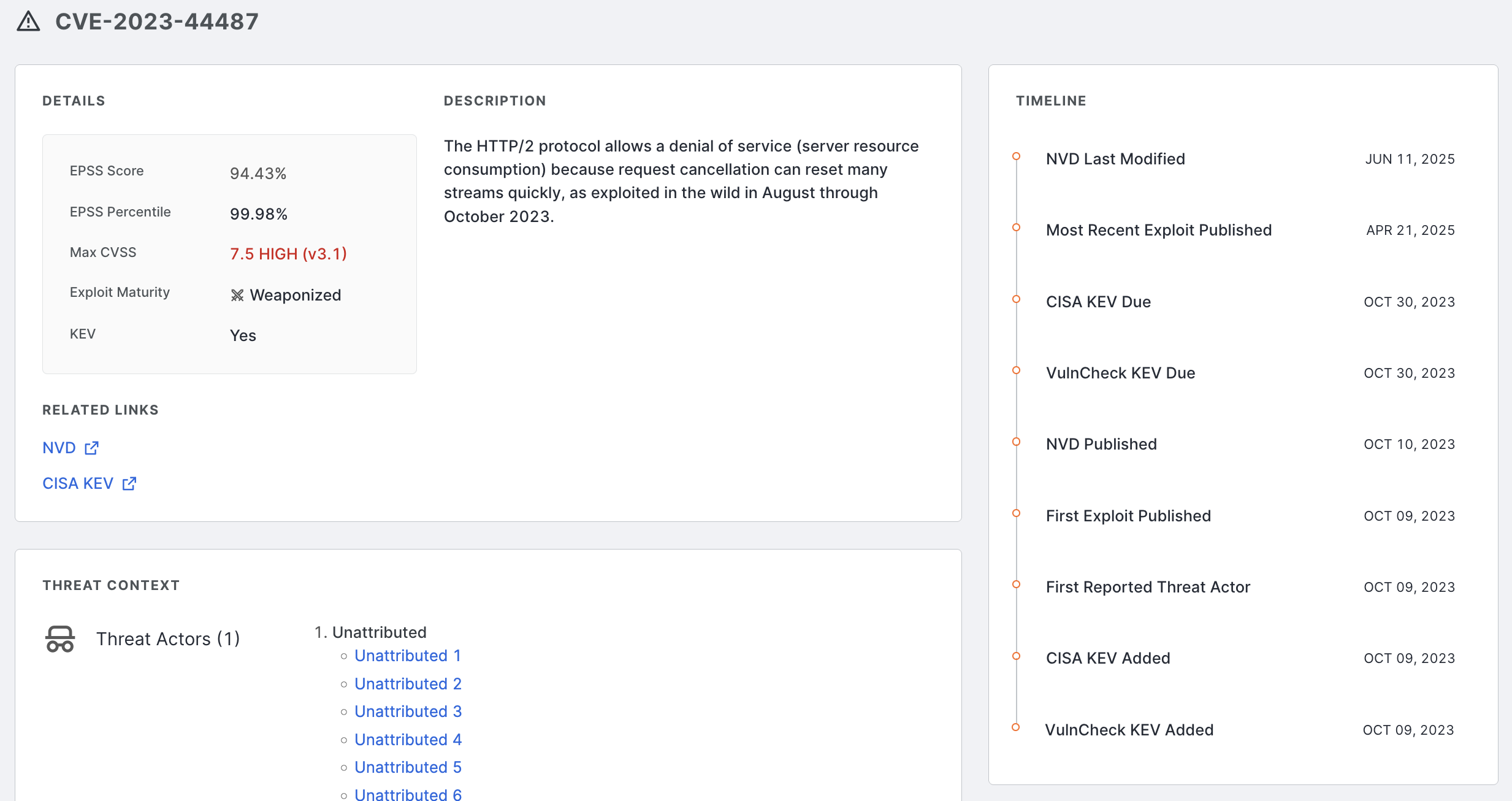
Details, description, and threat context information on the CVE details page.
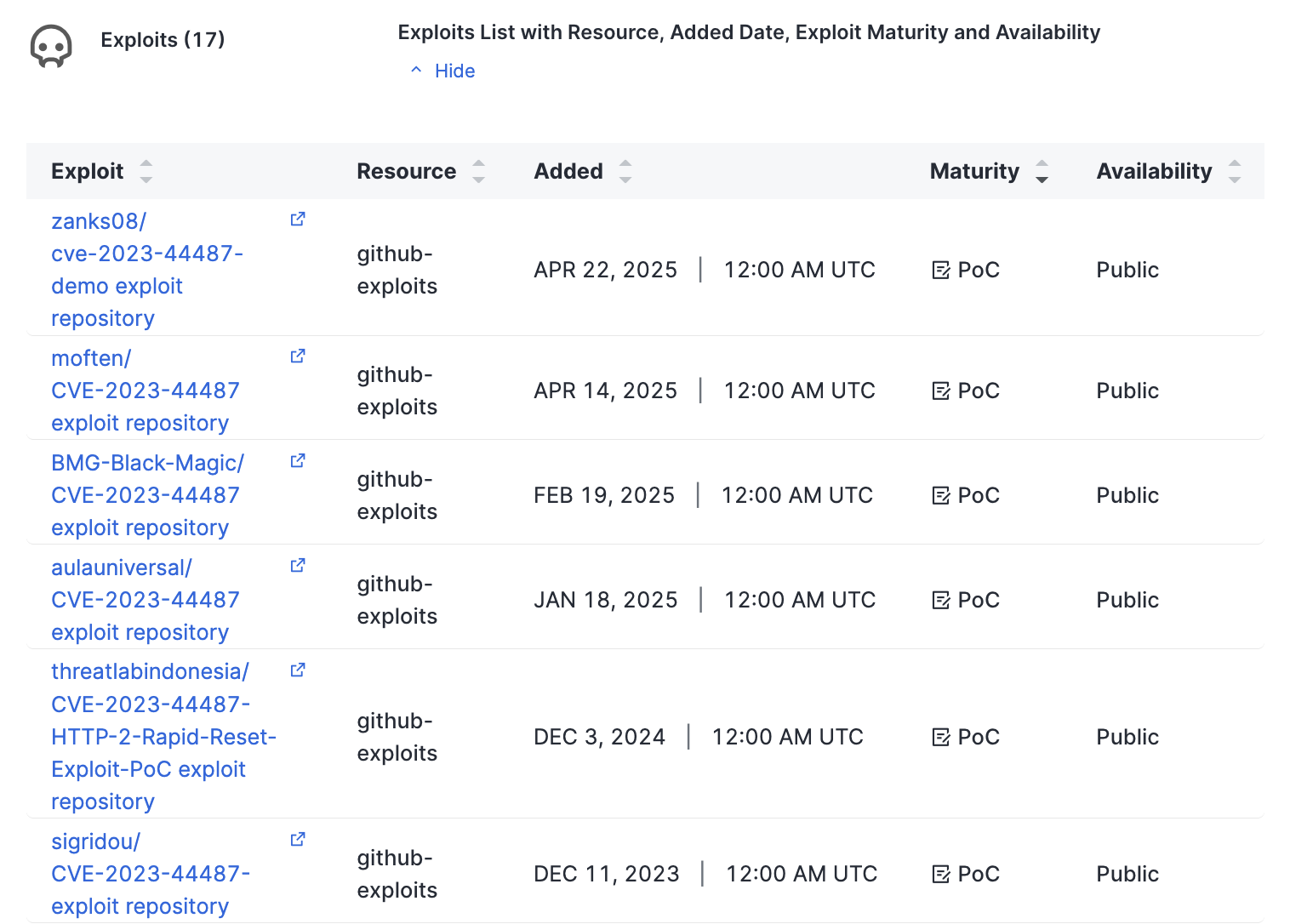
Exploit information and links on the CVE details page.
-
On the list page, click the Investigate on button below to navigate to the associated CVE information on the affected asset's inventory page.
-
CVE risks on asset details pages
When viewing the CVE risk details for a CVE risk on the asset details page, you can see the same information provided in the risk instances list page.
Click the CVEs tab to see the list of CVE IDs.
Tune vulnerability alerts for CVE risks
The number of CVEs you see in Censys ASM depends on your attack surface. Censys recommends that you start by enabling the highest-severity CVEs and then determine whether to adjust your filters to include more CVEs.
In ASM, navigate to Risks > Configure CVEs to manage your CVE risk settings. Whenever you make changes to your configuration, click Submit at the top of the page. Click Reset to return settings to their default configuration.
Disable or enable CVE risks
The toggle in the top-right corner of the page allows you to enable or disable CVE risks in your workspace.
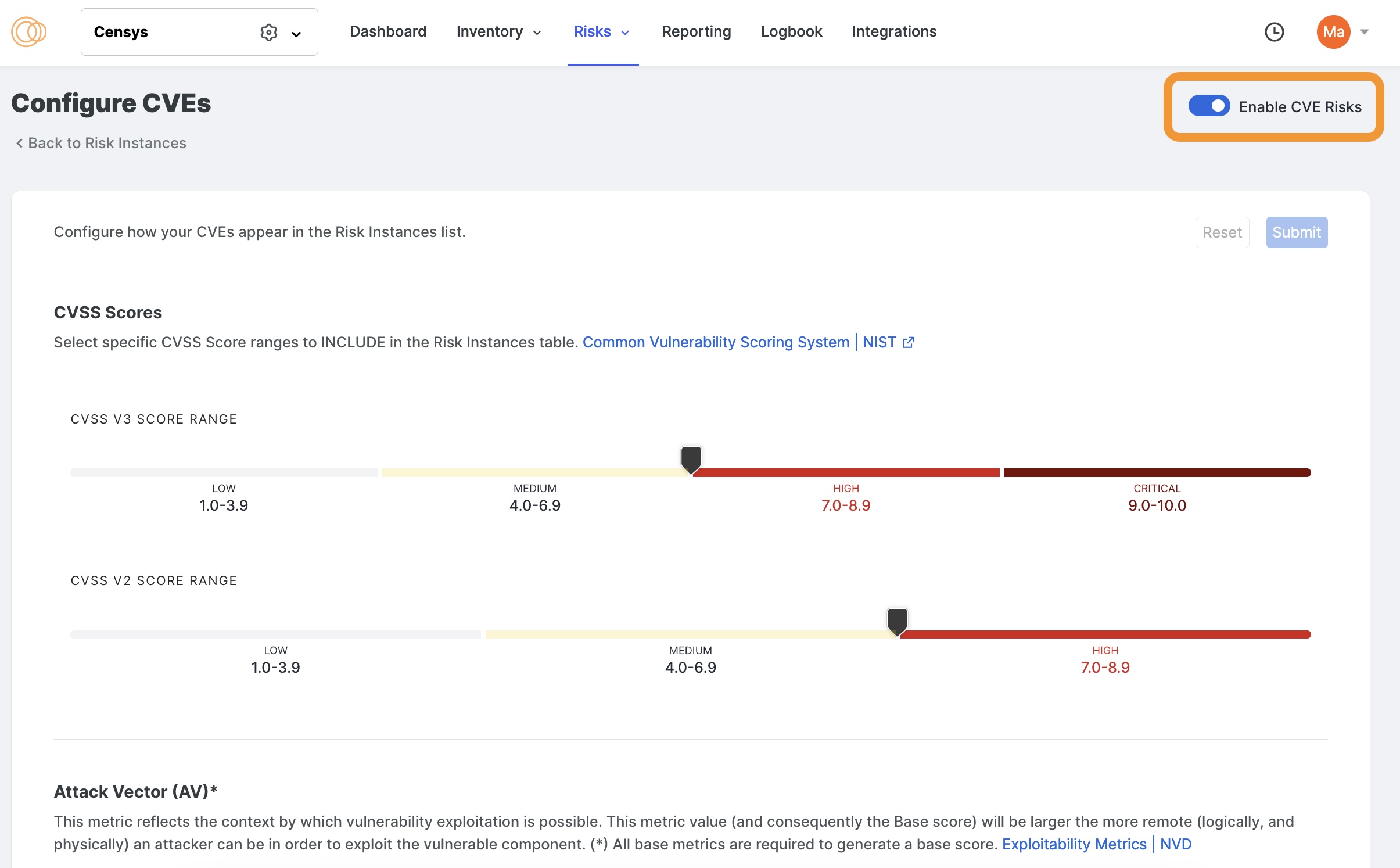
Tune by CVSS score
Select which score ranges to include in the Risk Instances table. By default, this is set to include high and critical severities.
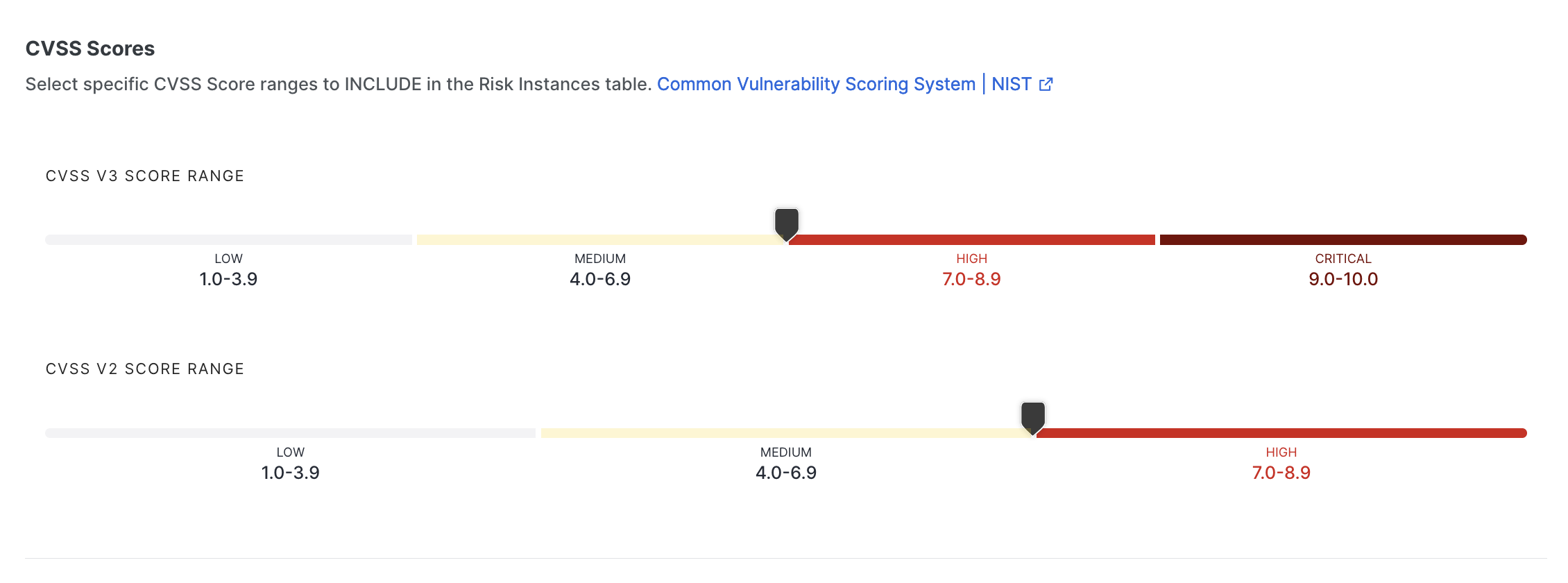
Tune by Attack Vector
Choose which attack vectors to include in the Risk Instances table. By default, only the network attack vector is selected.
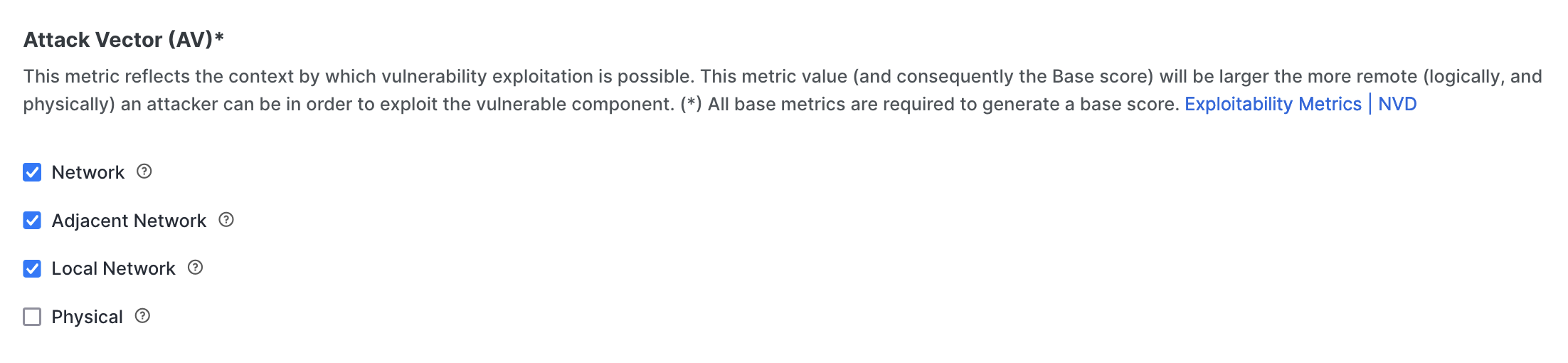
Tune by KEV
Select whether to always include Known Exploited Vulnerabilities in the Risk Instances table, regardless of severity. This option is recommended because KEVs are known to be exploited by threat actors and pose a serious risk to your attack surface. By default, this option is enabled.
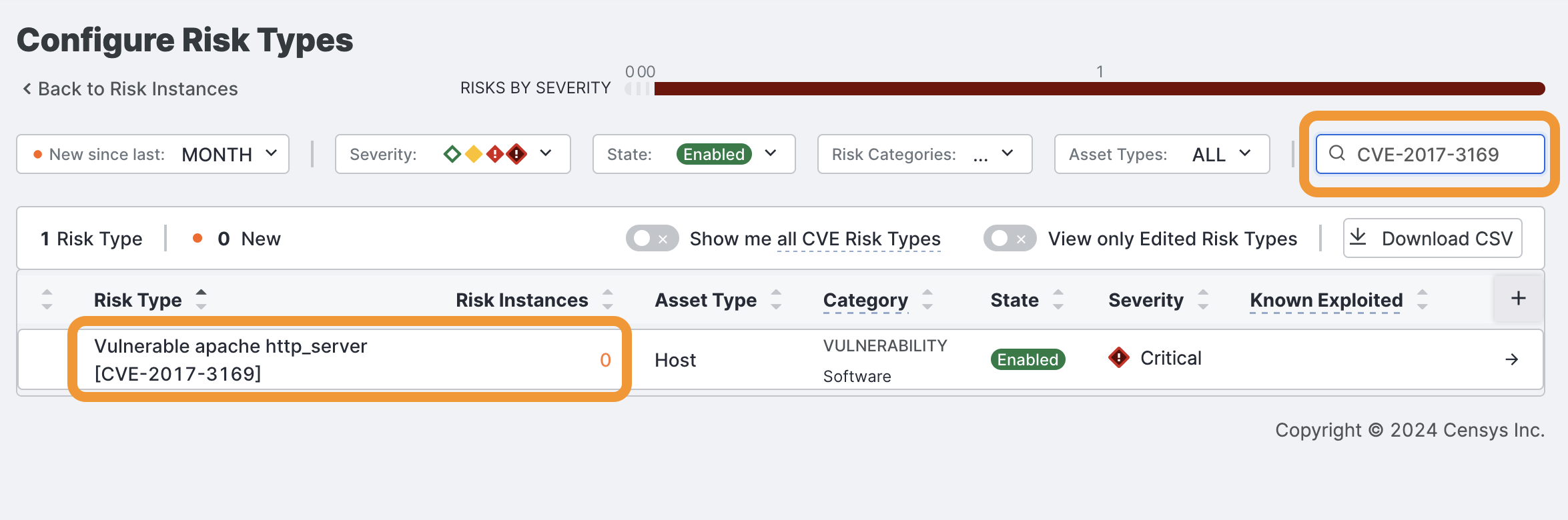
Search for CVEs on the Configure Risk Types page
To see whether a specific CVE is present in your attack surface, you can search for it on the Configure Risks page.
- Go to the ASM web console and click Risks > Configure Risk Types.
- Locate the search bar on the top right. Enter the CVE ID you are searching for.
- In the results, check the Risk Instances column to see if a count appears.
- Click the Risk Type to see important context about the CVE, like CVSS score and whether it is a KEV.
Common use cases
Investigate critical vulnerabilities
If you are an analyst investigating a specific vulnerability, like CVE-2022-47966, you need to confirm whether the vulnerability is in your environment and whether the data is fresh. To accomplish this task using CVE risks in ASM, use the following process.
-
Go to the ASM web console and click Risks > Configure Risk Types. New risk types are added here within 24 hours of NVD publishing a CVE.
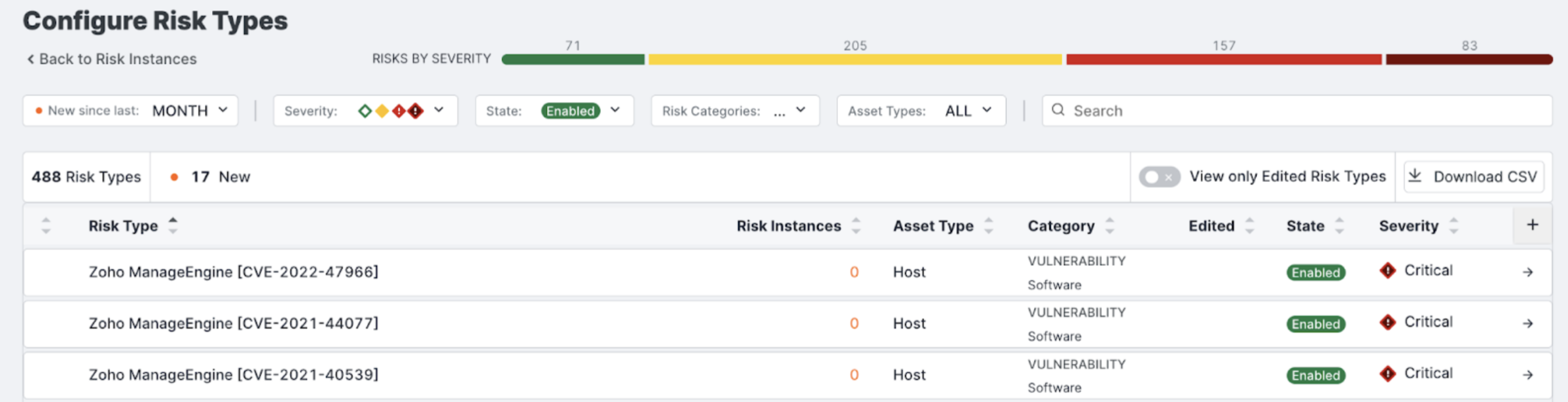
-
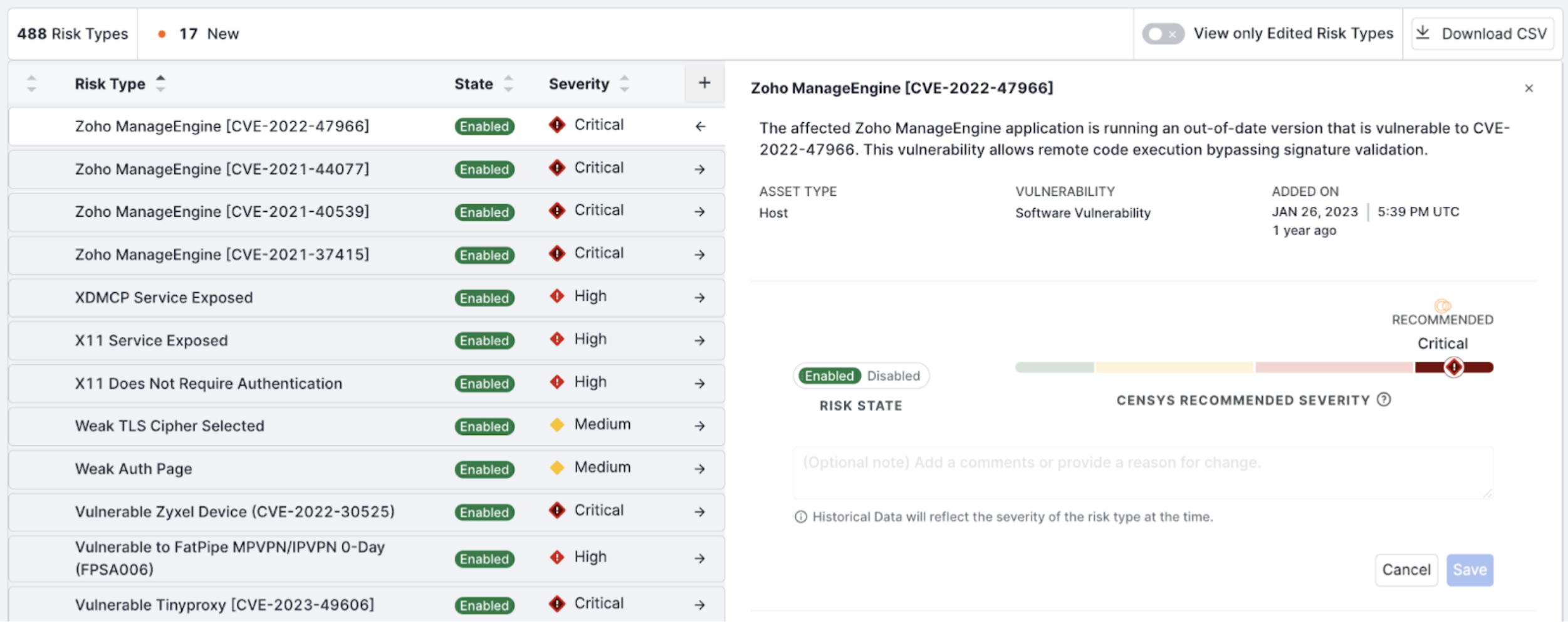
On this page, search for CVE-2022-47966 in the upper right corner. From the list view, look at the Risk Instances column to see if there are any instances of this CVE in your attack surface.
-
Click on the CVE to view its details. This will allow you to quickly determine if the vulnerability is actively being exploited and assess its severity.
Monitor vulnerabilities on your external attack surface
If you are an analyst who needs to monitor any potential vulnerabilities in your environment, you need to understand and remediate the highest-priority vulnerabilities quickly. To do this using CVE risks in ASM, use the following process.
-
Go to the ASM web console and click Risks > Risk Instances. On this page, you can see at a glance whether there are new vulnerabilities, how many CVEs are associated with the vulnerabilities, whether they are known to have been exploited, the exploit maturity level, and EPSS scores. Use this information to help you triage and prioritize vulnerabilities.
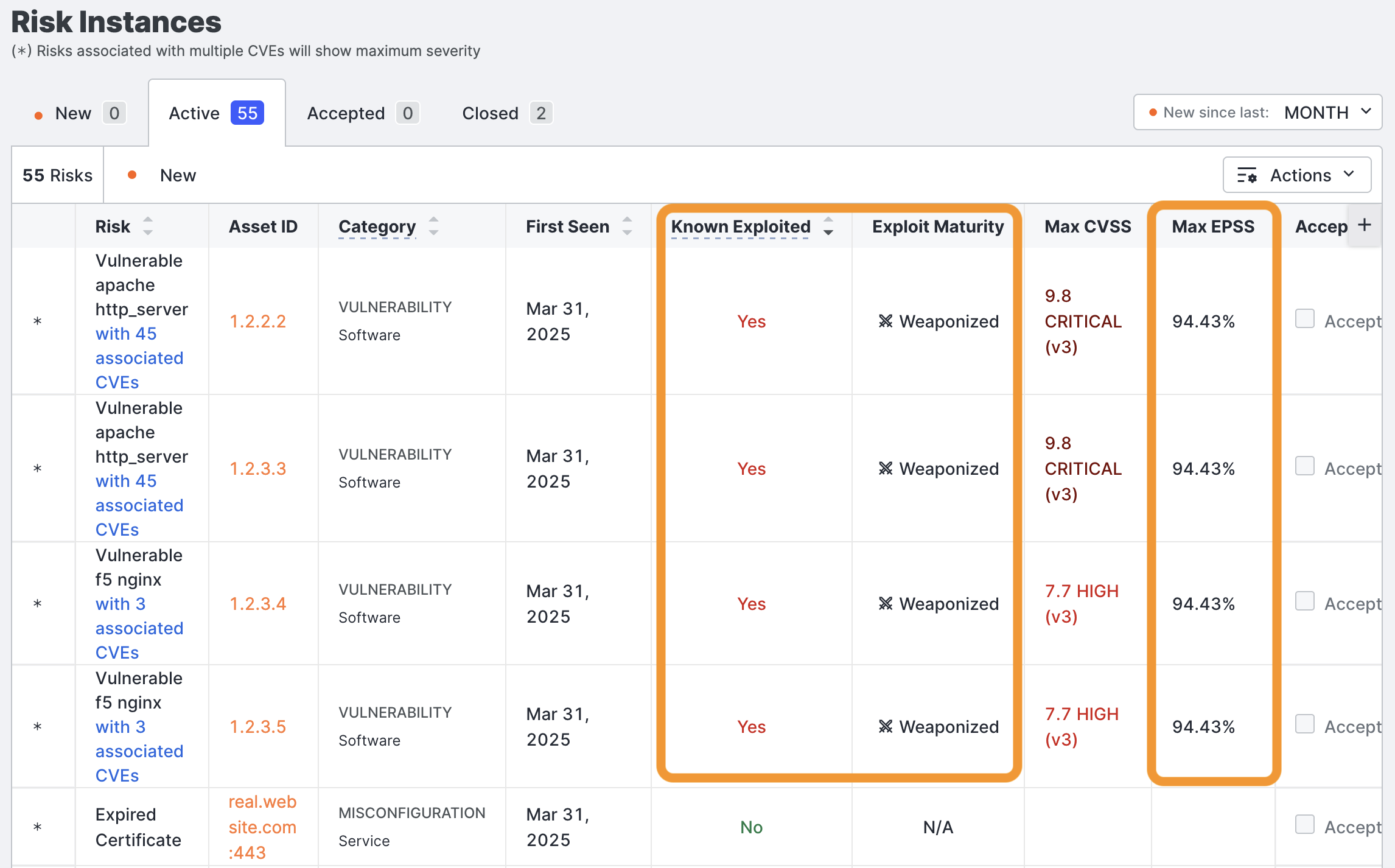
-
Expand the details of the risk to view these details and remediation recommendations. To assess risk and prioritize vulnerabilities, look at the CVE contextual data and length of exposure:
-
You can also click the associated CVEs to view and investigate all CVEs associated with the software. In the Associated CVEs table, click the CVE ID to view the related NVD page with additional information.
-
Updated 8 months ago
