Google Security Operations
Access Levels: Advanced | Enterprise
The Censys connector for Google Security Operations (SecOps) enables you to connect Attack Surface Management (ASM) logbook and risk events with SecOps. Thus, you can monitor your attack surface events from within Google SecOps.
Prerequisites
Before you begin, make sure you have your Google Security Operations ingestion account email, customer ID, and private key.
To find your account email and private key:
- Go to the Google Security Operations console, and go to Settings > Collection Agents.
- Locate the Ingestion Authentication File and download it.
- Within the file, the ingestion email address is listed in the
client_emailfield. - Within the file, the private key is listed in the
private_keyfield. Make sure to include '-----BEGIN PRIVATE KEY-----', '-----END PRIVATE KEY-----\n' and everything in between.
To find your customer ID:
- In the Google Security Operations console, navigate to Settings > Profile.
- Under Organization Details, note your customer ID.
Configure the integration in Censys ASM
- Go to the ASM web console and click Integrations.
- Locate Google Security Operations and click Set Up.
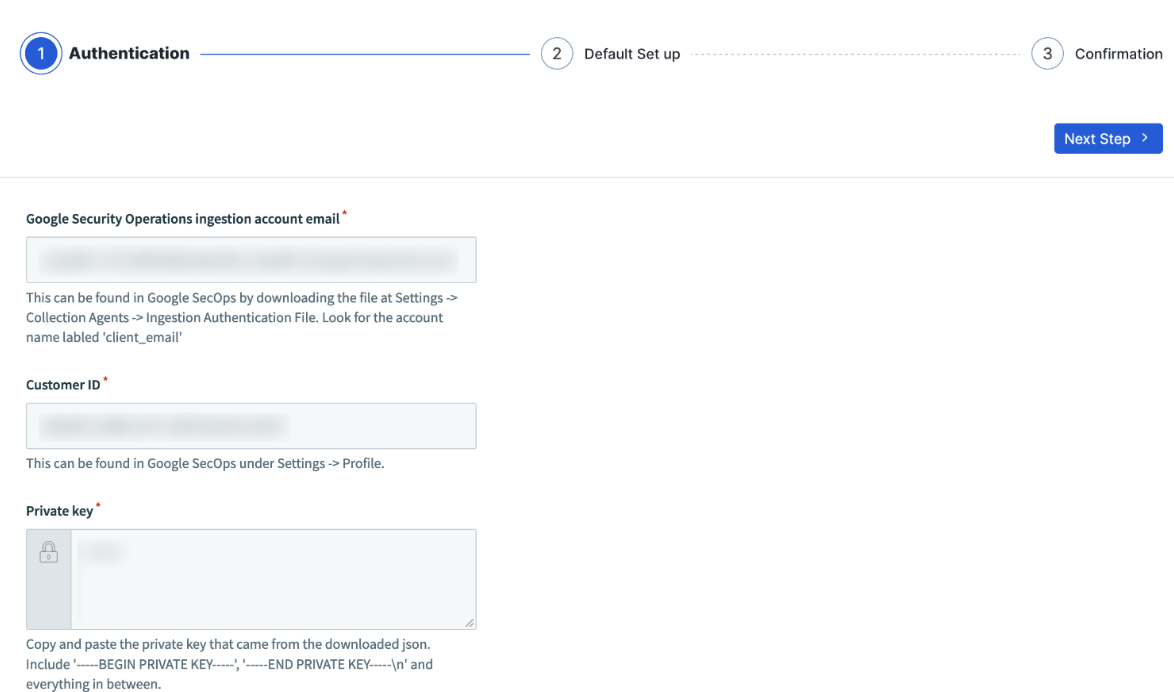
- On the Authentication page, enter the following:
-
Google Security Operations Ingestion Account Email: Enter the account email you obtained from the Ingestion Authentication File.
-
Customer ID: Enter the customer ID you obtained from your SecOps profile.
-
Private Key: Enter the private key you obtained from the Ingestion Authentication File.
-
- At the bottom of the Authentication page, click Sign in with Google.
- Click Next Step.
- On the Default Set up page, select whether you want to receive logbook events, risk events, or both within Google SecOps.
- Click Submit, then click Done.
Modify the integration
If you need to make changes to your integration, follow the configuration steps above.
Query examples
The integration automatically polls Censys for new events, which are sent to Google SecOps.
All Censys ASM events
This query will show all events that have been ingested from Censys ASM.
metadata.product_name= “Censys Attack Surface Management”Risk events
These events track whether a risk instance has been opened, closed, or updated in your attack surface. To show all risk events ingested from Censys ASM, you can use the following query:
metadata.product_name= "Censys Attack Surface Management" AND security_result.category = "POLICY_VIOLATION"To filter by severity, you can add the following to the query above. This will only show events with High severities in ASM.
AND security_result.severity = "HIGH"Logbook events
These events track which hosts have been associated and disassociated with the attack surface. To show all host associate and host disassociate events, you can use the following query:
metadata.product_name= "Censys Attack Surface Management" AND (metadata.description = "ASSOCIATE" OR metadata.description = "DISASSOCIATE"You can use the following query to filter for only associate events. Replacing ASSOCIATE with DISASSOCIATE filters for only disassociate events.
metadata.product_name= "Censys Attack Surface Management" AND metadata.description = "ASSOCIATE"Event fields
The following tables detail the objects sent to the custom log analytics tables.
Risk events
UDM Field | Description |
|---|---|
| Risk Type Name |
| First Seen by Censys |
| Last Seen by Censys |
| Risk Severity |
| Risk ID |
| Indicates whether the risk is open or closed ACTIVE: Open in Censys CLEARED: Closed in Censys |
Updated 10 days ago
