Storage Buckets
Censys Attack Surface Management (ASM) categorizes Storage Buckets as cloud-based containers used for object storage. It identifies buckets hosted on Google Cloud Platform (GCP) and Amazon Simple Storage Service (S3).
The Storage Buckets page displays buckets that may be linked to your organization. Censys Attack Surface Management leverages your organization’s DNS domain and subdomains to conduct Internet-wide bucket discovery, identifying potentially relevant assets.
The Storage Buckets page allows you to view discovered buckets, determine whether they belong to you, and remediate risks for known buckets.
Storage buckets list
Go to the ASM web console and click Inventory > Storage Buckets.
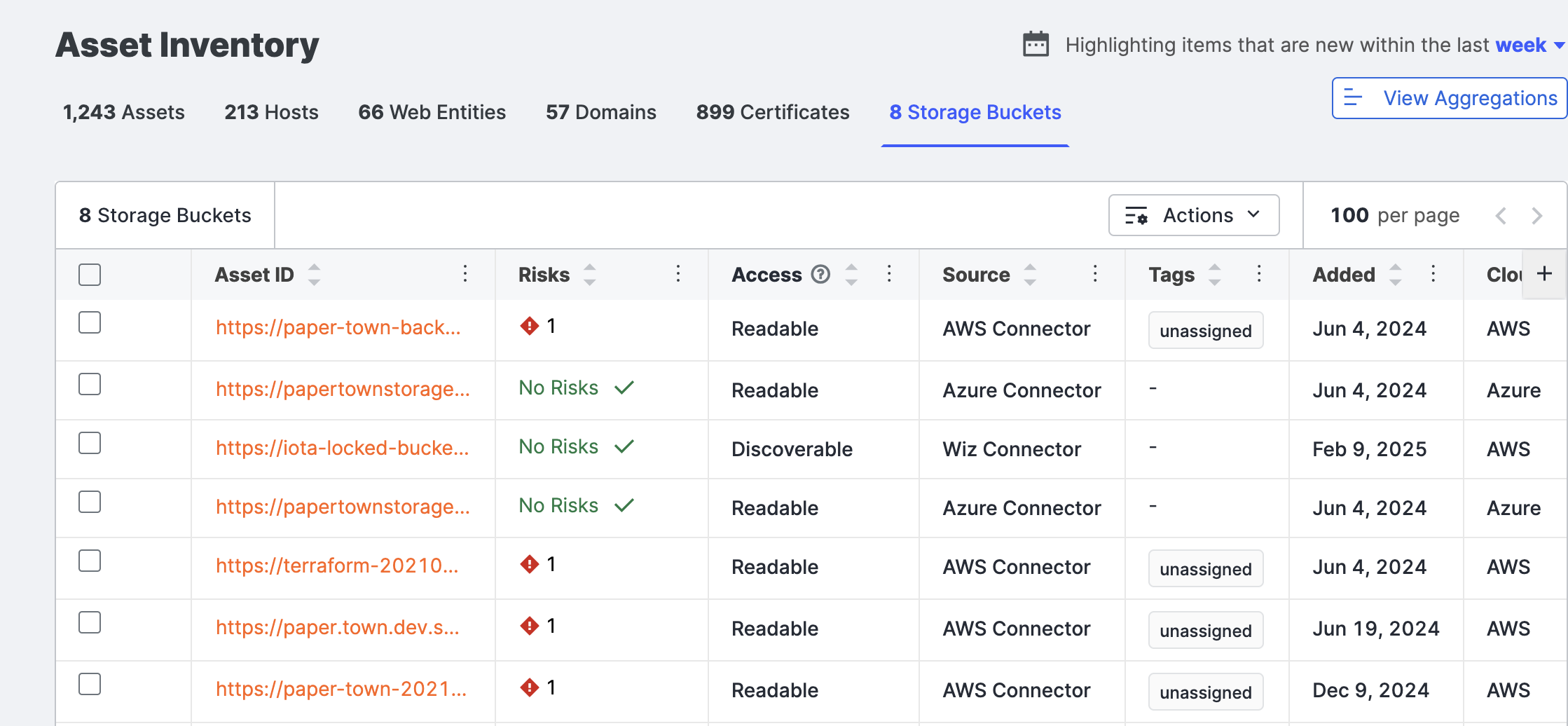
Default columns include:
- Risks: The risk severity associated with this bucket’s configuration.
- Access: The access configuration for this bucket. Access levels include Readable, Writeable, and Editable Settings.
- Readable: Contents of the bucket might be read publicly.
- Writeable: Contents of the bucket might be editable.
- Editable Settings: Anyone can edit the read/write settings for this bucket.
- Source: The source that uncovered this bucket. Sources include Cloud Connector, the integration provided by Censys to automatically identify your organization’s known buckets and Censys Scan, the Censys method to discover potentially unknown buckets.
- Cloud: The cloud storage provider hosting this bucket.
- Account ID (AWS specific): The AWS account associated with this bucket.
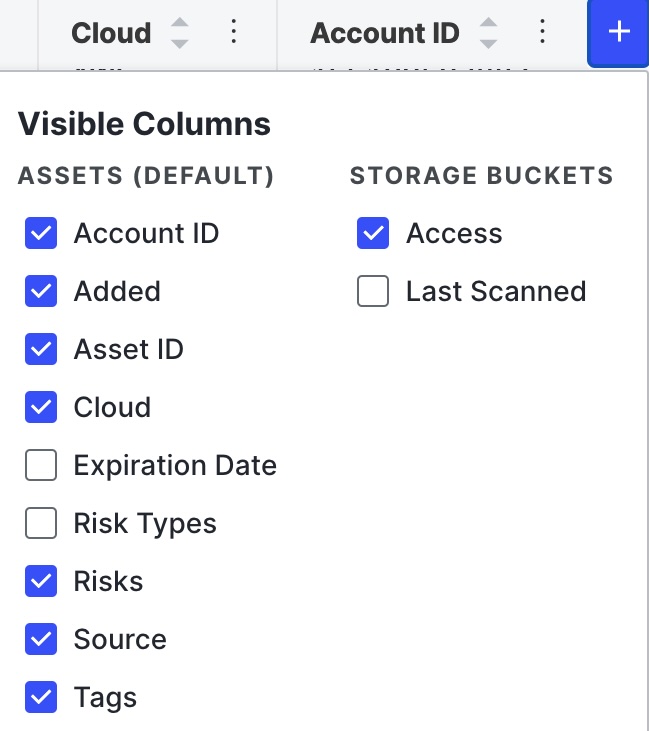
Column selection
Click the above the table to open additional columns with more information about your storage buckets. Select or clear the columns to create your view.
Additional columns include:
- Risk Types: A string representation of the risks associated with this bucket.
- Tags: Tags added to this asset.
Sort columns
The default sorting for the table is ascending (A-Z) for the Asset ID column. Use the arrows on the other columns to sort the table by those.
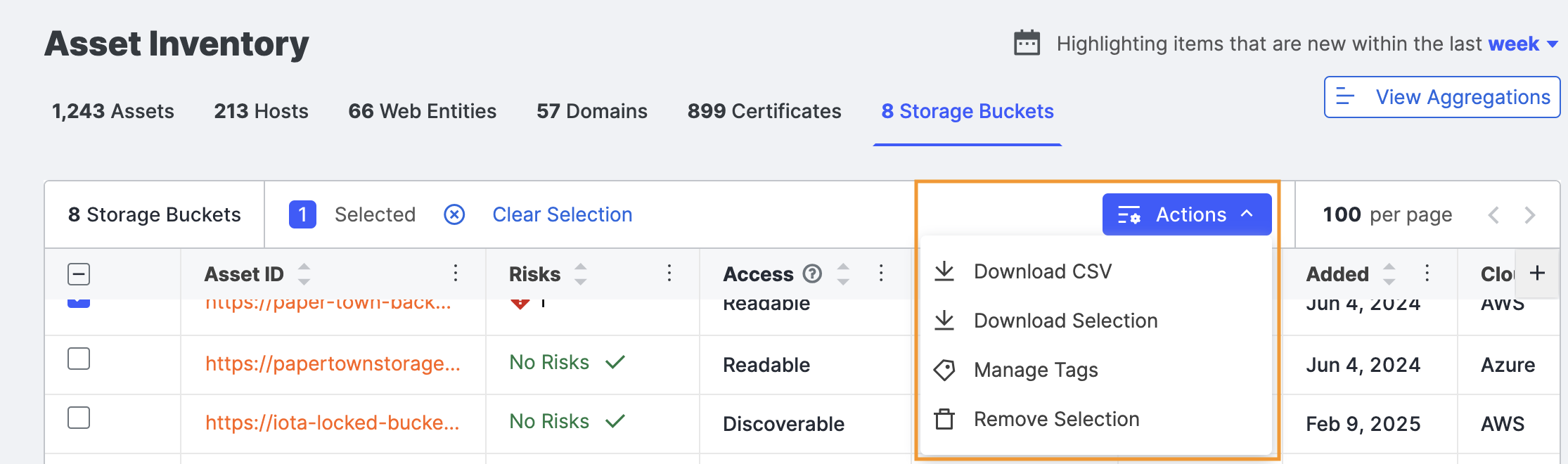
Download storage bucket data
You can download storage bucket data as a comma-separated value (CSV) for use in other products and workflows.
- Click Actions > Download CSV. The default filename is
{timestamp}_{customerName}_ObjectStorageExport.csv. The columns in the CSV file reflect the columns shown in the table when exported.
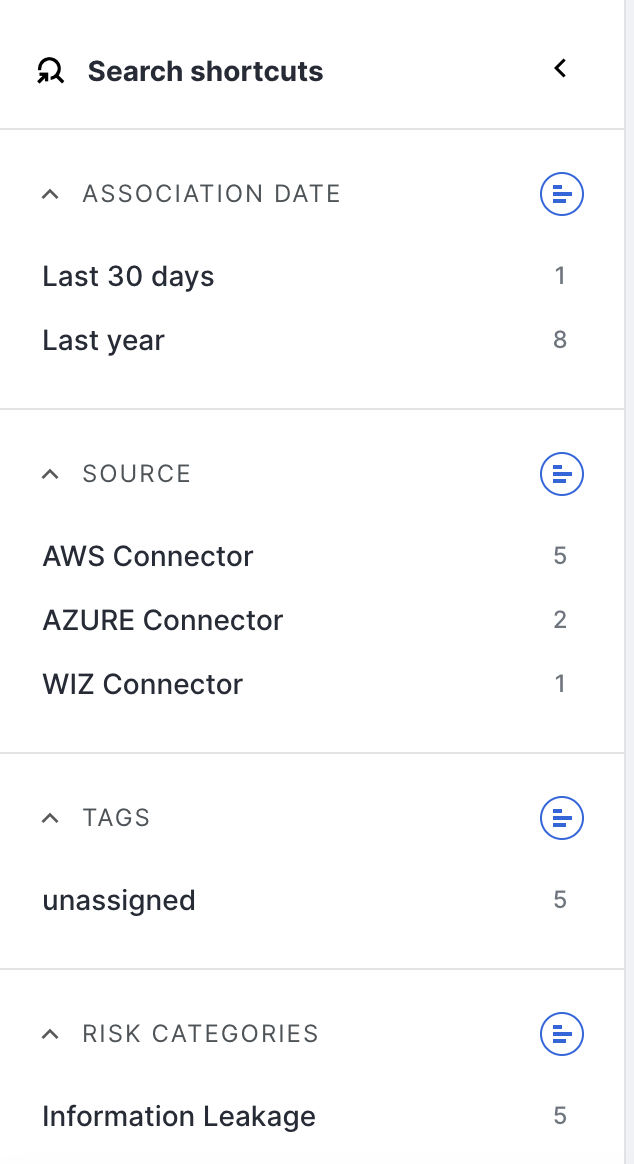
Search shortcuts
Shortcuts include:
- Association Date: The date when the storage bucket was first linked to your organization’s attack surface.
- Source: The method by which the storage bucket was discovered, such as a cloud connector or external scan.
- Tags: Labels assigned to storage buckets for categorization or tracking purposes.
- Risk Categories: The types of security risks associated with the storage bucket, such as public exposure or misconfiguration.
- Risk Severity: Any storage buckets that have a risk severity of high.
- Risk Type: The specific nature of the security risk, such as public exposure, misconfigured permissions, or weak encryption.
- Account ID: The unique identifier associated with the cloud account that owns the storage bucket.
- Editable Settings: The level of access discovered for this bucket.
- Readable Objects: Contents of the bucket might be read publicly.
- Writeable Objects: Contents of the bucket might be editable.
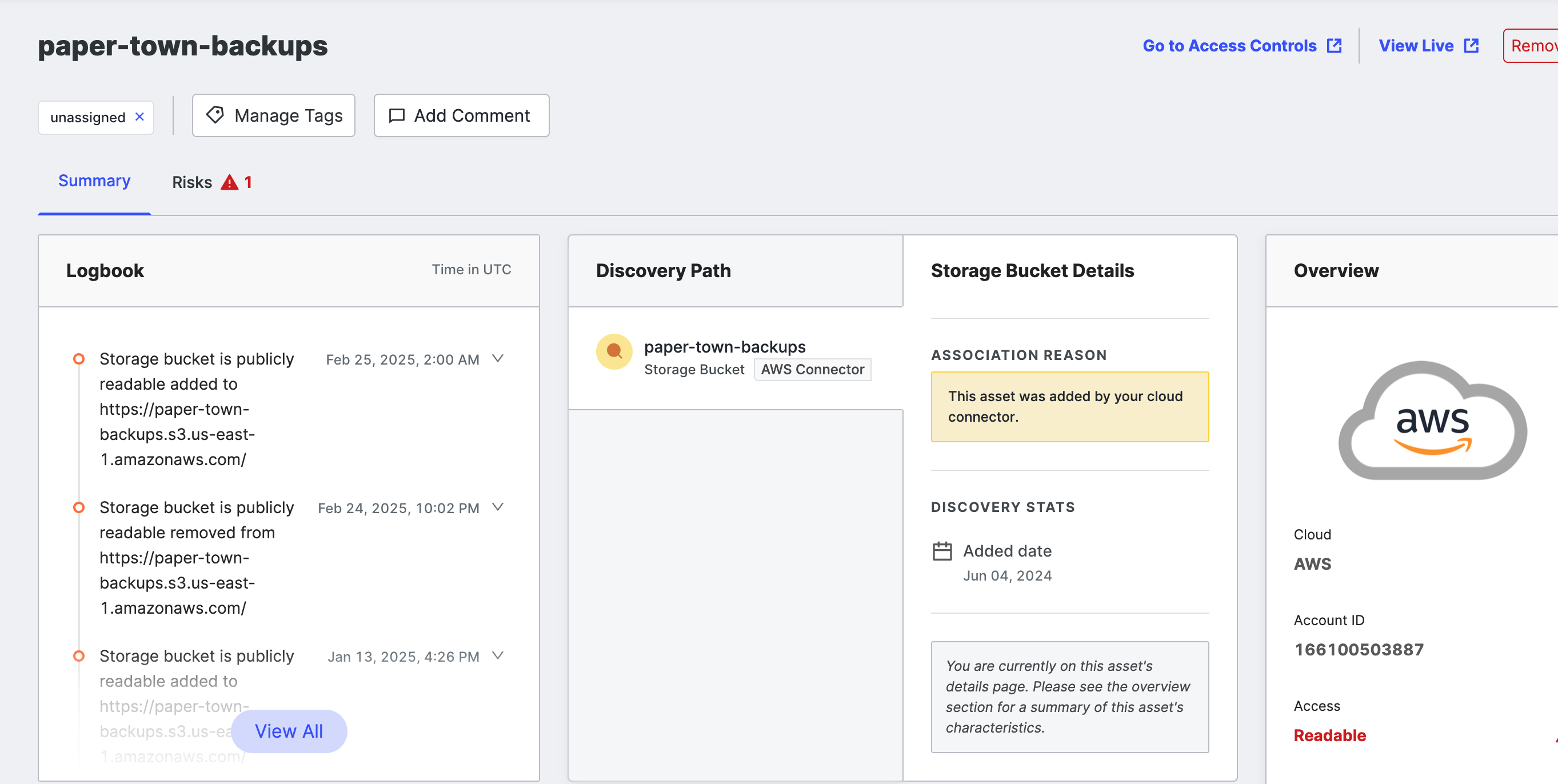
Storage Bucket details
Click the Asset ID to see a storage bucket detail page with additional information.
Risks
The Risks tab shows the count of risks associated with this storage bucket. Click the tab to open the list and show more information.
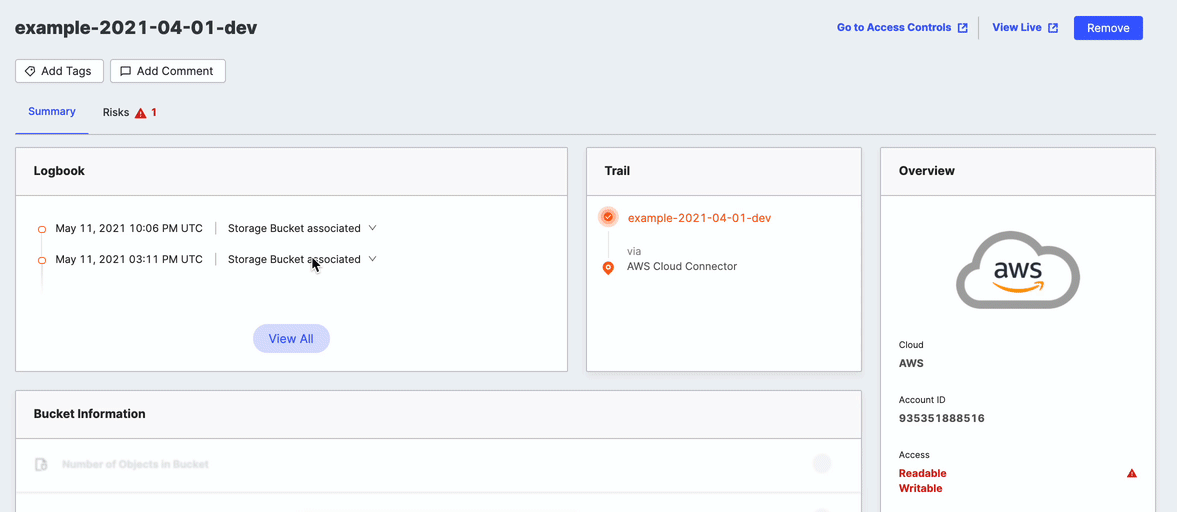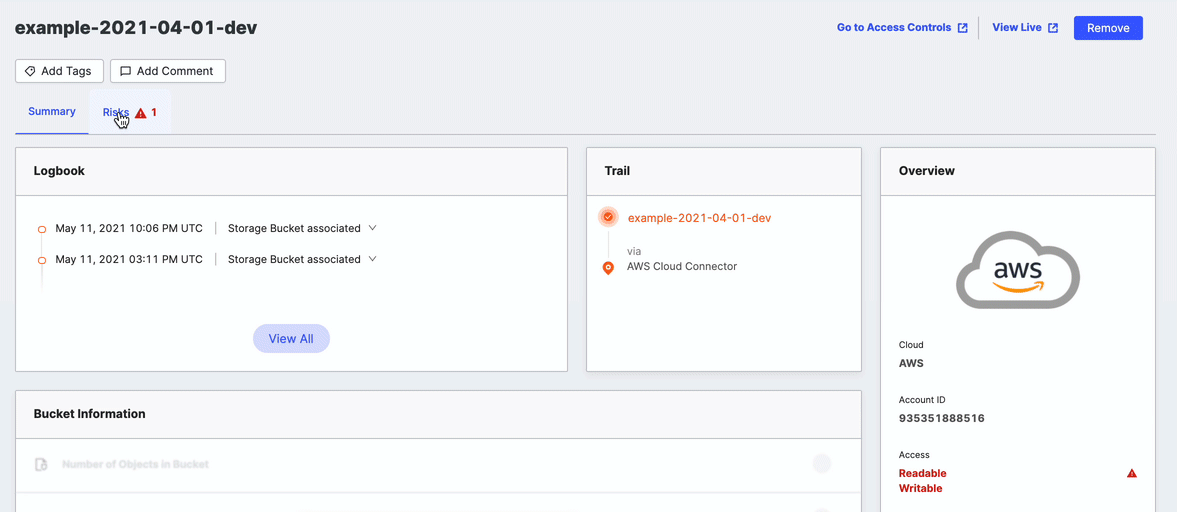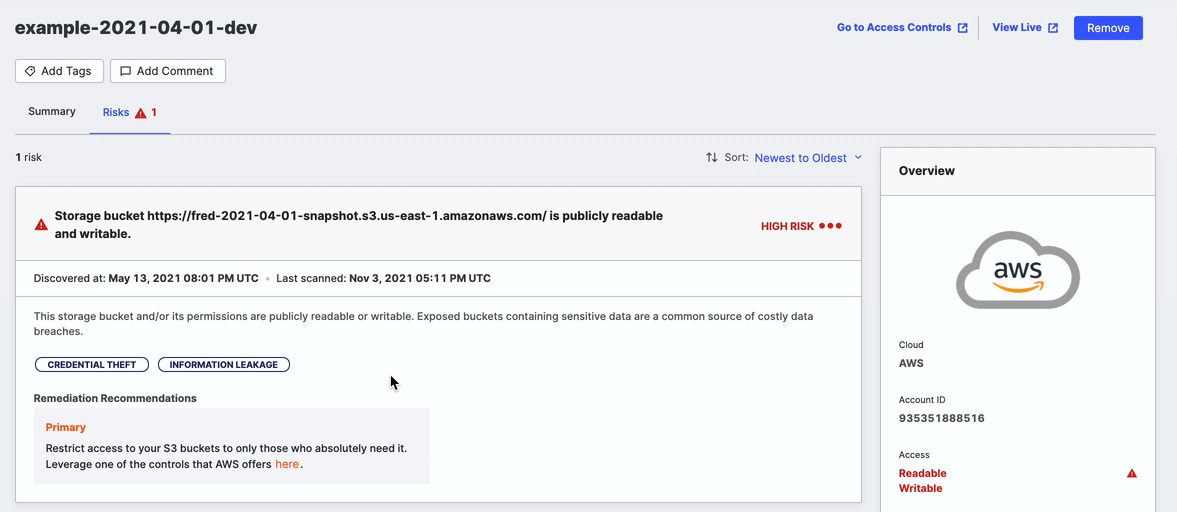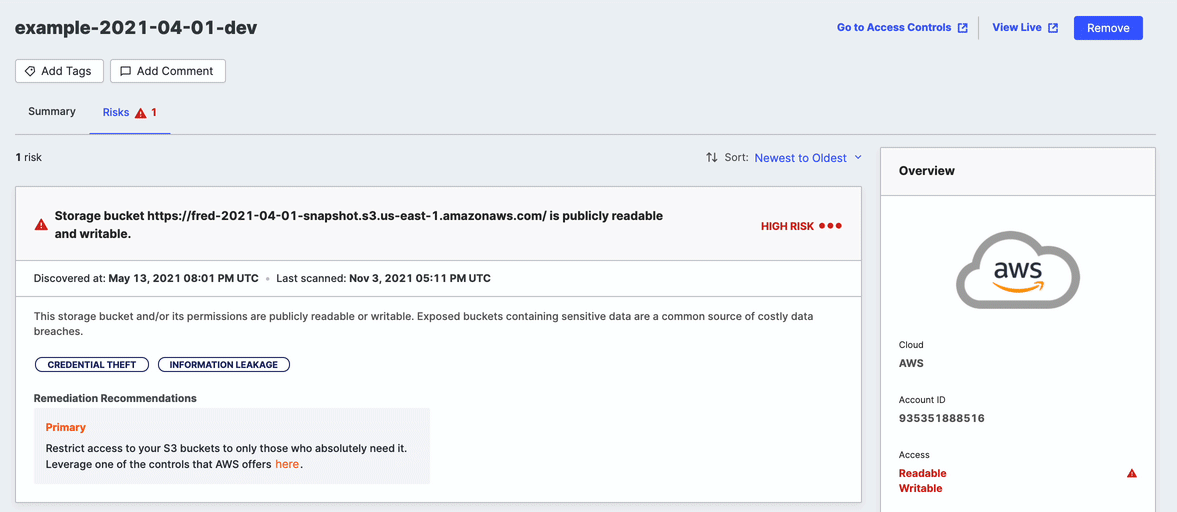
Logbook
The Logbook shows important updates and events related to this storage bucket.
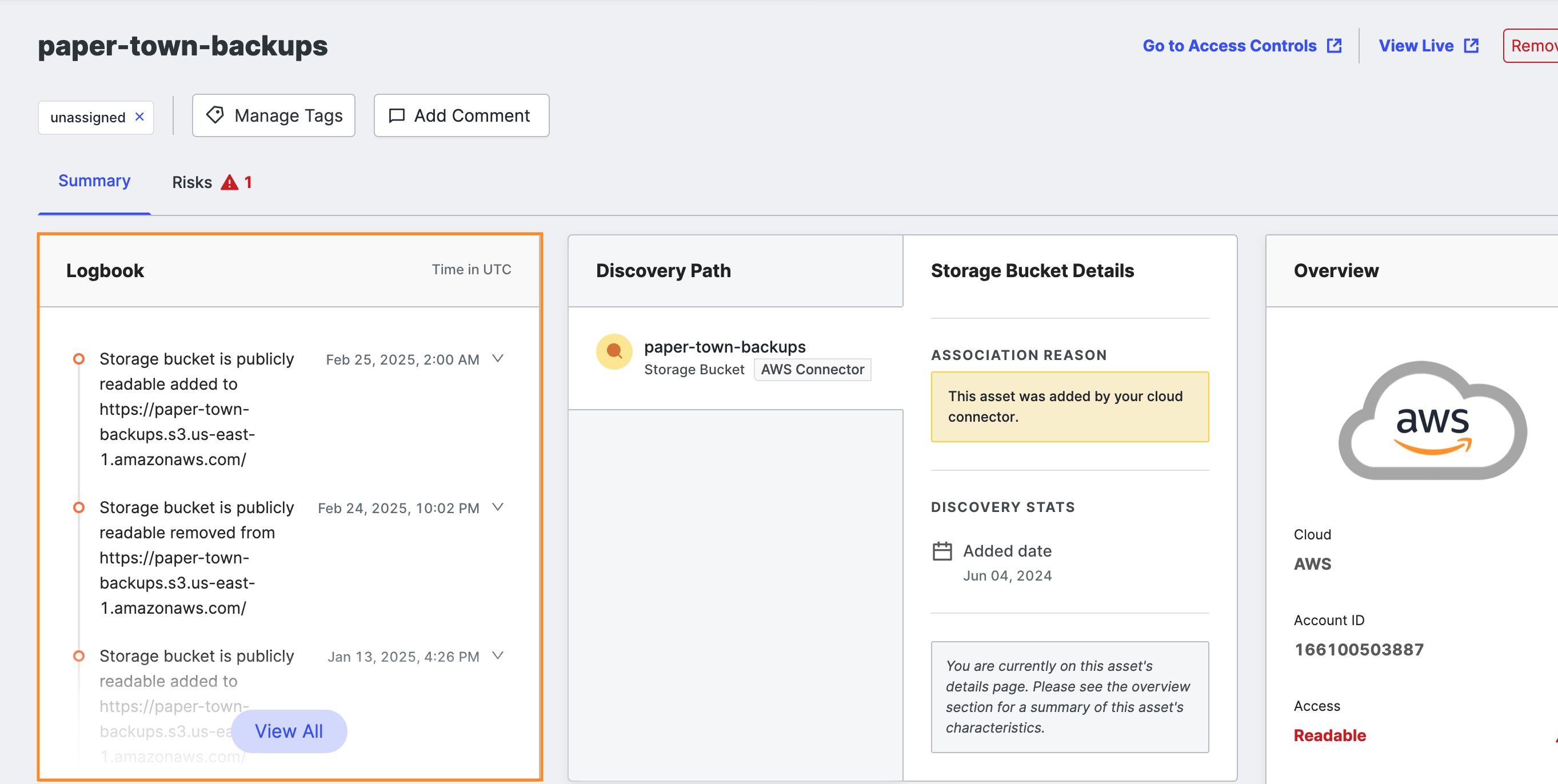
Click View All to expand the logbook to show all events related to this storage bucket after it was added to your inventory.
Discovery Path
The Discovery Path shows the pivots used to discover this storage bucket, which can help you identify why a storage bucket is associated with your organization. Note that the Discovery Path does not display multiple pivots for storage buckets found by a cloud connector.
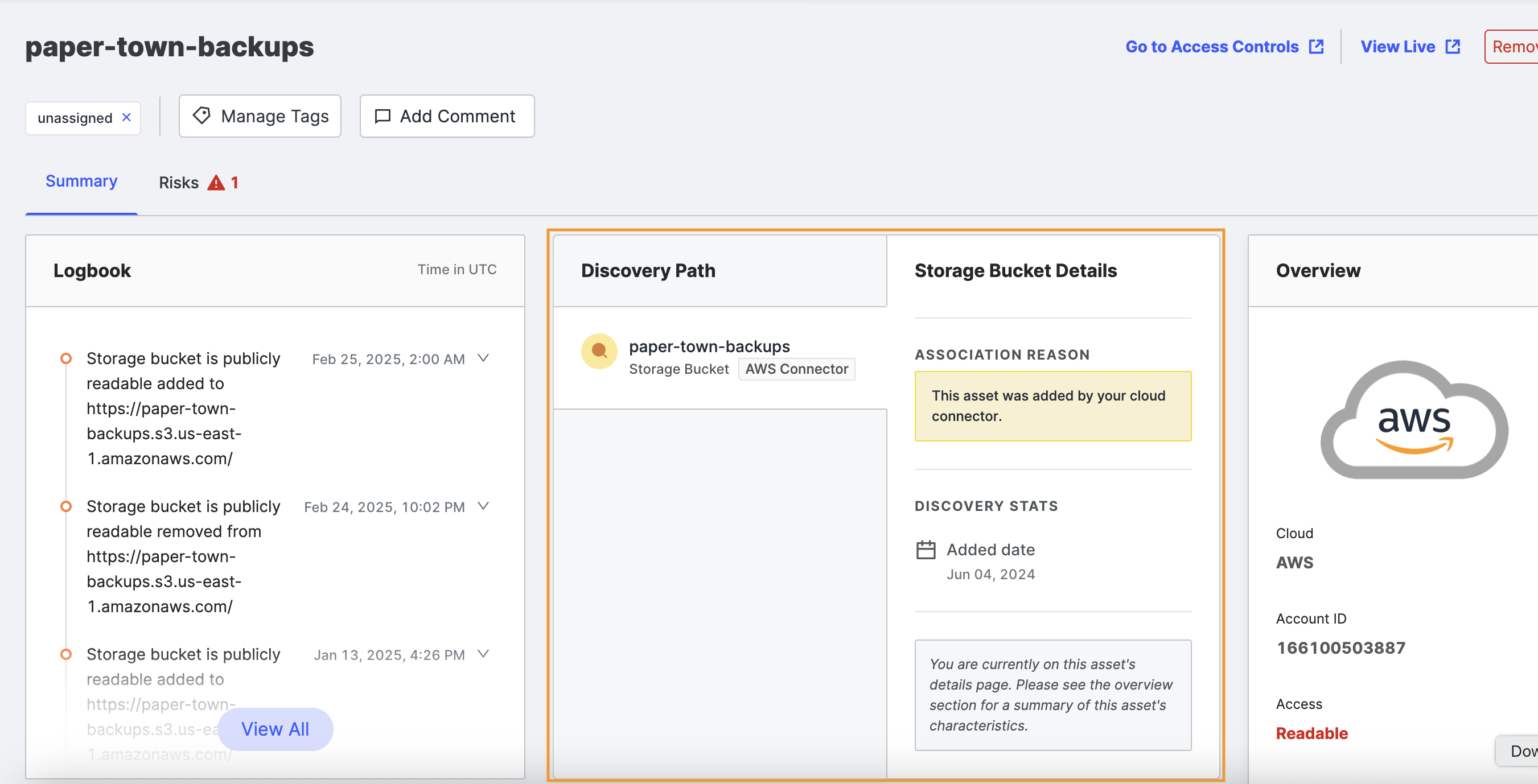
Overview
The Overview area on the far right of the page provides the most important storage bucket information.
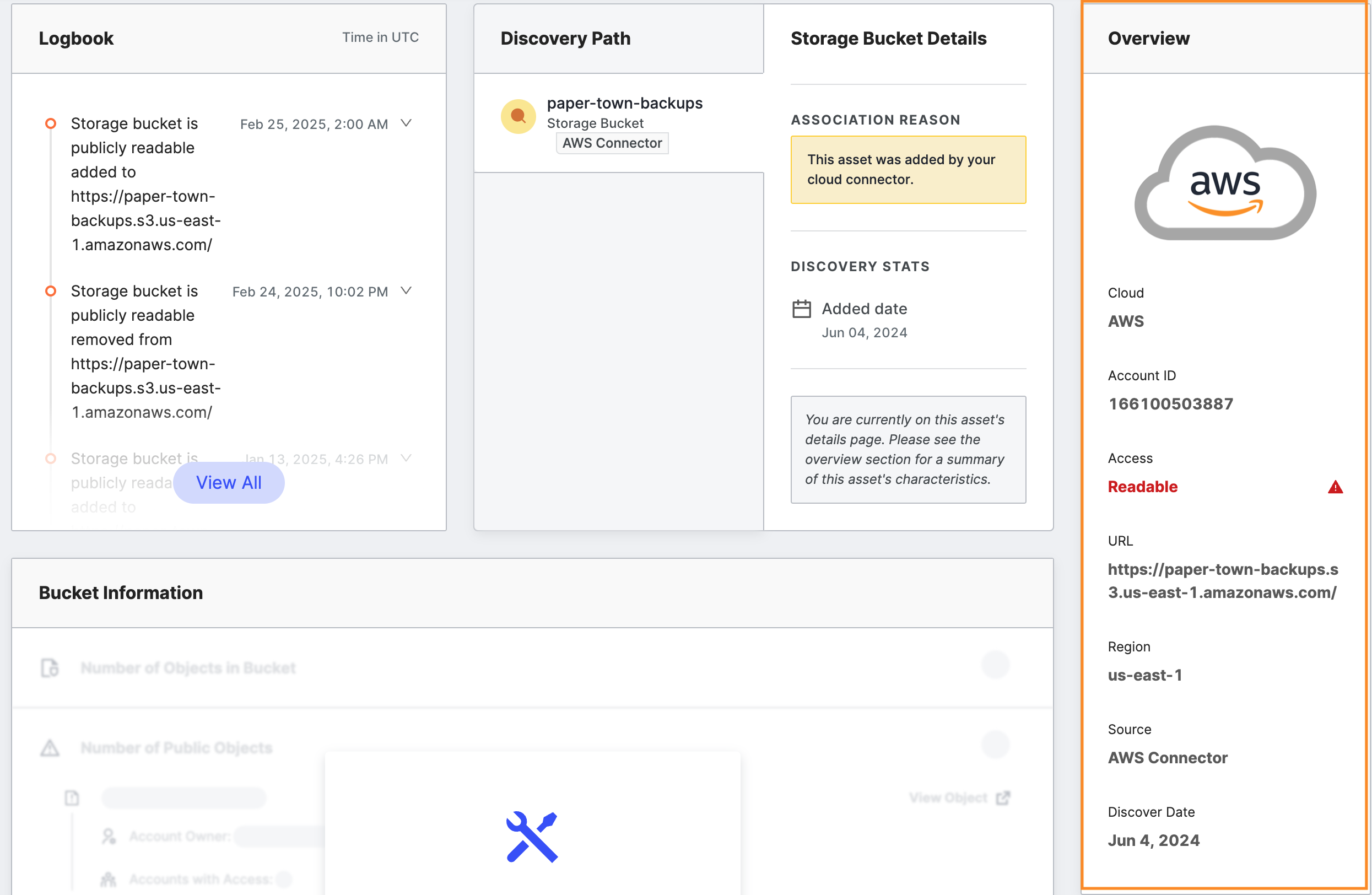
In the Overview area of the page, general information about the bucket includes:
- Cloud: The name of the cloud storage provider.
- Account ID (AWS specific): The AWS account ID associated with this bucket, if known.
- Access: The access configuration for this bucket. Access levels include:
- Discoverable: Buckets can be found but not viewed or altered.
- Readable: Contents of the bucket might be read publicly.
- Writeable: Contents of the bucket might be editable.
- Editable Settings: Anyone can edit the read/write settings for this bucket.
- URL: The URL associated with this bucket.
- Region (AWS specific): The geographic location housing this bucket.
- Source: The source that uncovered this bucket. Sources include Cloud Connector, the integration provided by Censys to identify your organization’s known buckets automatically, and Censys Scan, the Censys method to discover potentially unknown buckets.
- Discover Date: The date when this bucket was first discovered.
Asset Management
At the top of the Software Bucket Details page, several buttons help you manage this bucket.
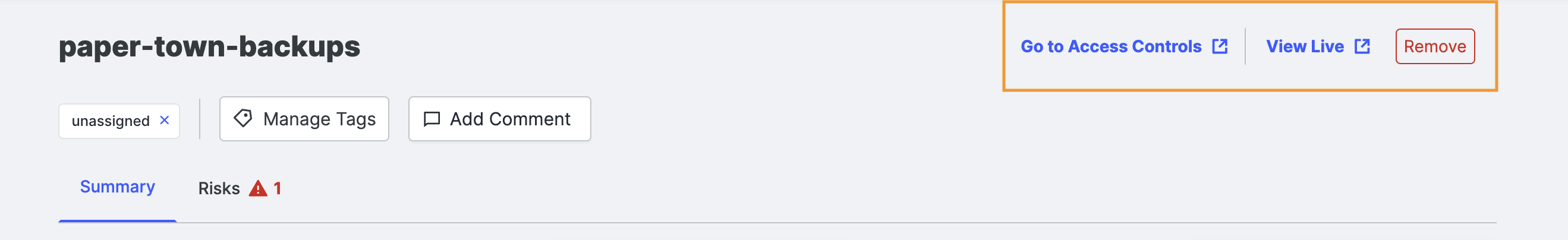
- Go to Access Controls (AWS specific): Click this button to open the AWS console for managing this bucket.
- View Live : Click this button to navigate to the URL linked to this bucket.
- Remove: If you no longer want Censys Attack Surface Management to track this bucket, click Remove to take it off your inventory. Removed buckets remain visible on the Excluded Assets page.
Remediate risks with known buckets
Use the storage buckets list page to easily manage risks tied to your buckets. You might discover that a bucket you own is mistakenly set as Readable, Writeable, or has Editable Settings that could pose a security risk.
- Go to the Censys ASM Web console and click Inventory > Storage Buckets.
- To remediate risks associated with a bucket, click the bucket’s name to navigate to the details page.
Censys Attack Surface Management provides several workflows for remediating risks associated with a bucket. - Click Go to Access Controls to navigate directly to the AWS console for managing the bucket.
NoteIf this bucket's risks do not require immediate action, use Add Tag or Add Comment at the top of the page to categorize it or add a note. This lets you and your team keep your inventory of buckets organized and secure.
Updated 10 months ago
