Tenable Vulnerability Management
Access Levels: Advanced | Enterprise
In Censys Attack Surface Management (ASM), you can connect your host association/dissociation Logbook events with Tenable Vulnerability Management to gain insight into your attack surface and exposures.
After configuring the integration, it will poll ASM for new host association and host disassociation events in your Logbook.
- If a host is associated with your attack surface (via a host association event), the host is sent to Tenable Vulnerability Management.
- If a host is disassociated from your attack surface (via a host disassociation event), it is deleted from Tenable Vulnerability Management.
- Before adding a host to Tenable Vulnerability Management, the integration checks whether it already exists. If it does, it is not imported. If it does not exist, it is imported.
Prerequisites
- You must have an active instance of Tenable Vulnerability Management.
- You will need to generate a new API key to use with this application.
- Tenable does not support using a single API key for multiple applications; be sure to create a separate key to use with Censys ASM.
Configure the integration in Censys ASM
-
Go to the Censys ASM web console and click Integrations.
-
Locate Tenable and click Set Up.
-
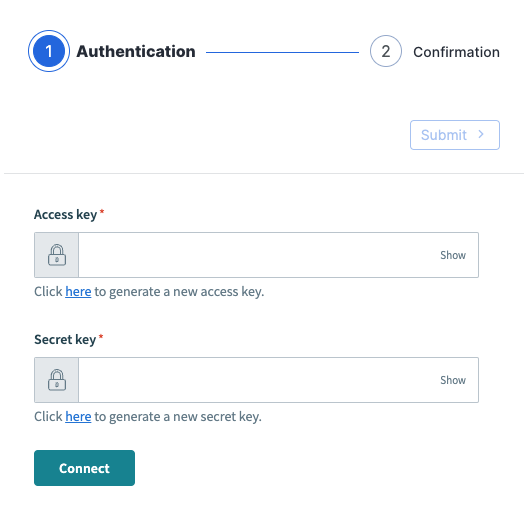
On the Authentication page, enter your Access key and Secret key from Tenable.
-
Click Connect, then click Submit.
-
Click Close.
Modify the Integration
- Go to the Censys ASM web console and click Integrations.
- Locate Tenable and click Manage.
- Go through the setup wizard, as described in the section above, and make any necessary changes.
Verify that the assets appear in Tenable
Note that hosts may take a few minutes to appear in Tenable.
-
Go to Tenable and click Vulnerability Management > Explore Overview > Assets.
- A list of hosts displays.
-
Click filter in the upper left.
-
In the Filter menu, configure
Source is equal to Censys, then click Apply.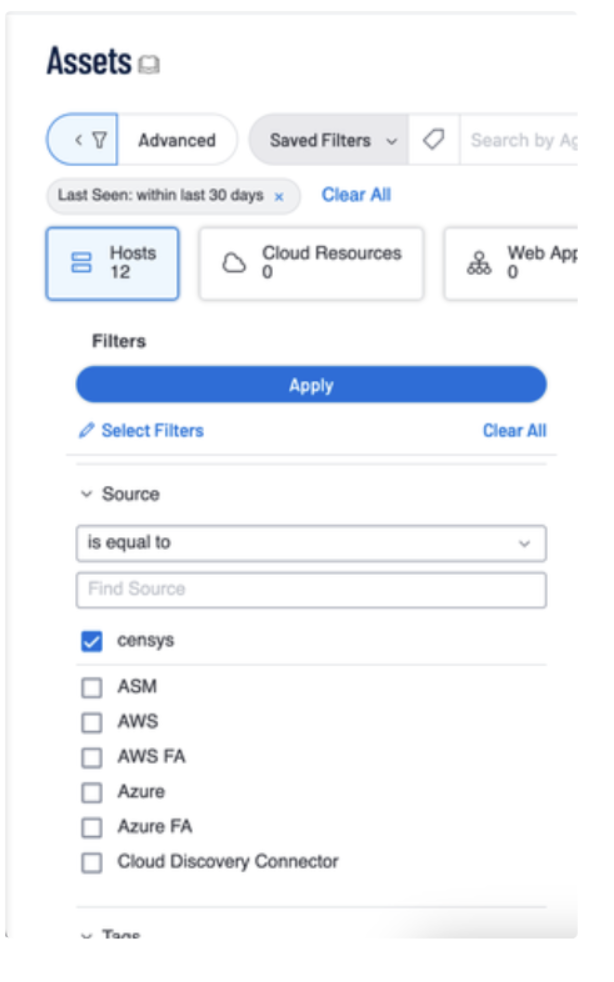
Updated 4 days ago
