AWS Hosted Cloud Connector
Access Levels: | Advanced | Enterprise
The Censys Cloud Connector for Amazon Web Services (AWS) enumerates your cloud environment, ensuring that Censys Attack Surface Management (ASM) is always up to date and your security teams are working with the most current data. This integration scans each resource to determine whether it is public.
You can configure this integration via the API or in the Censys ASM UI.
The Censys AWS Cloud Connector authenticates to an IAM Role with the following permissions:
AWSOrganizationsReadOnlyAccessSecurityAudit
These are the least privileged permissions required to access your cloud resources and import them into Censys.
Data refresh frequency
Cloud Connectors refresh more often than other connections. After you set up Cloud Connectors, your data will refresh as often as every four hours.
To see the latest refresh time in Censys ASM:
- Go to the ASM web console and click Integrations.
- Scroll down to see the date within the Cloud Service Provider cards.
Configure the Censys Cloud Connector for AWS
There are two options for configuring Censys Cloud Connectors for AWS: using the Censys ASM UI or via the Censys API.
Prerequisites
You will need the following before you get started:
- Your AWS Organization Management Account ID
- Optionally, you may need:
- A list of accounts or services you wish to exclude from being sent to Censys ASM
The following users and permissions are required:
- Censys ASM user with the workspace role Manager
- AWS Admin with the following privileges:
- Access to the AWS Organization management account.
- Ability to deploy a CloudFormation Template, creating a StackSet in the AWS Organization management account.
Option 1: Configure the Cloud Connector in the ASM UI
Step 1: Configure the integration in Censys
- Go to the ASM web console and click Integrations at the top of the page.
- Locate AWS and click Set Up.
- In the setup wizard, configure the following:
- Role Name: Enter a role name or leave this field blank to use the default name.
- Account ID: Enter your AWS account ID. If you are configuring this for an AWS organization, enter your organization management account ID.
- Excluded Fields: Optionally, enter any resource types or regions you wish you exclude from being sent to Censys ASM.
- Click Next Step.
- On the IAM Resource page, click Create Stack next to the template where you are deploying.
- You must create an IAM role in all of the accounts associated with the Cloud Connector. If you configure this for an AWS organization, it will automatically deploy to all AWS accounts within the organization and auto-deploy the IAM role to any new accounts added to the organization via StackSet.
- The page will redirect to your AWS console.
Step 2: Configure the stack in AWS
-
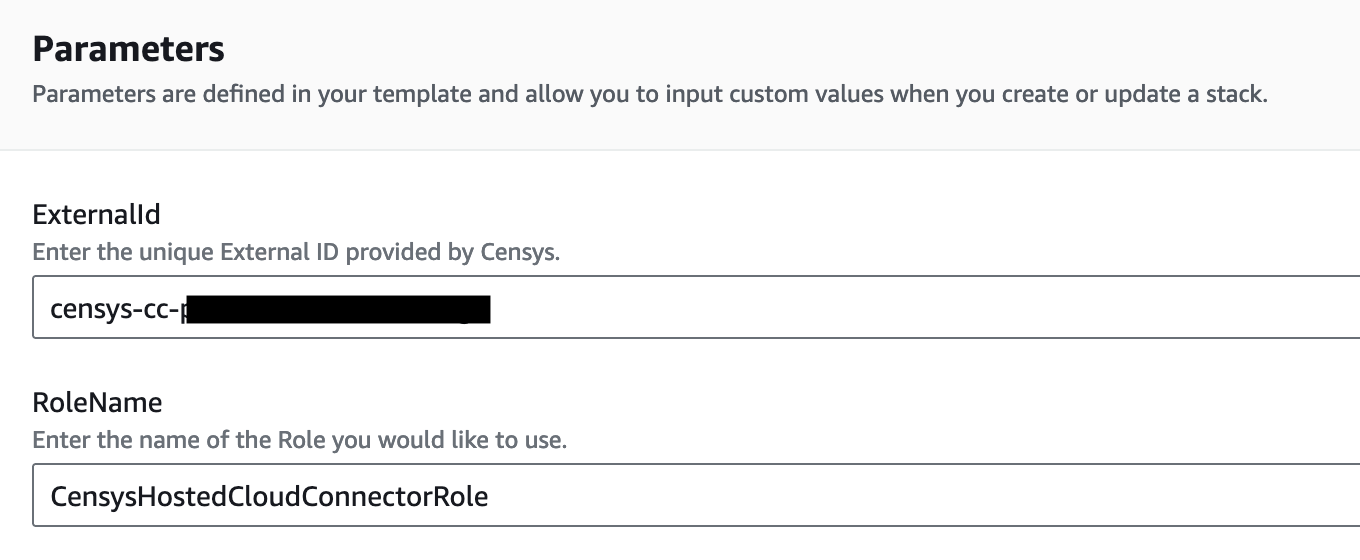
In the AWS web console, verify that your parameters are configured properly:
-
ExternalId: This field should contain the external ID provided in Censys ASM.
-
Do not make changes to the RoleName parameter.
-
-
Check the box next to I acknowledge that AWS CloudFormation might create IAM resources with custom names.
-
For a standalone AWS account, click Create stack. For an organization, follow these additional steps:
-
Navigate to CloudFormation > StackSets.
-
Click Actions > Add stacks to StackSet.
-
For the deployment target, select Deploy to organization.
-
Under Specify regions, select your AWS region.
-
Click Next, then click Next again.
-
Verify your configuration, then click Submit.
- This will add all member accounts within the organization to this StackSet.
-
-
Click Create stack.
- The page will redirect to an Events page within the AWS console, showing that the stack creation is in progress.
Step 3: Finish configuration in Censys
- Go to the ASM web console and click Next Step, then click Done.
Option 2: Configure the Cloud Connector via Censys API
Step 1: Creating the connector using Censys API
- Craft a JSON body with the appropriate scopes describing how you want the Cloud Connector to scan your AWS environments. Any combination of Organizations and standalone accounts is acceptable.
- To include an AWS Organization, provide the Organization’s Management Account ID and any optional account, region, or service type exclusions.
- Provide the Account ID and any optional account, region, or service type exclusions to include a standalone AWS account.
- For examples, see the JSON section below.
- When the JSON body is ready, create a new hosted connector using the Censys Hosted Connectors API endpoint.
- Go to the Integrations Marketplace.
- Copy your API Key to your clipboard.
- Follow the link to API documentation.
- Click Authorize and paste in your API key.
- Click Authorize > Close.
- Expand the hosted connectors header to expose the Hosted Connector endpoints.
- Expand the POST /v1/hosted-connectors endpoint.
- Click Try it out, then replace the example value with your own JSON body.
- Click Execute.
- Censys will return a response body including two URLs to deploy a CloudFormation template as a stack.
- For a standalone account, use the accountTemplate URL.
- Use the organizationTemplate URL to deploy to an entire AWS organization or specific OUs. You must be logged in to your AWS Management account to deploy to the organization.
- For a standalone account, use the accountTemplate URL.
NoteIf your Organization does not use Cloudformation templates, build similar logic using Terraform or another preferred method. Ensure that a role is created with permissions and that a trust relationship contains our Account ID and the provided External ID.
Step 2: Deploy in AWS
- After signing in to AWS, copy the proper URL from the response body, paste the URL into your browser, review the Stack options, and deploy.
- If using an accountTemplate, no additional steps are required.
- If using organizationTemplate, navigate to the CensysHostedCloudConnector StackSet created in your Management Account to add stacks to the StackSet:
- Click Actions, then click Add stacks to StackSet.
- Choose your deployment targets. The recommended target is Deploy to organization.
- Choose your preferred region and deployment options.
- Click Next, click Next, then click Submit.
- Wait for the StackSet to create the IAM Role in all of the specified Member Accounts.
- Initiate a permissions check to verify that all permissions are properly granted.
- Go back to the API documentation.
- Expand the
POST /v1/hosted-connectors/{id}/checkendpoint - Click Try it out.
- Paste in the ID of the connector you want to check.
- Click Execute. In the response body, use the Date field to note the time that the check was started.
- Using the
GET /v1/hosted-connectors/{id} endpointcheck the status.- Expand
GET /v1/hosted-connectors/{id}and click Try it out. - Paste the ID of the connector you wish to check, then click Execute.
- Verify that statusTimestamp is the same time as what you noted from the /check endpoint.
- Verify that status is either checking-configuration or connected.
- If status is connected, your connector is correctly configured.
- If status is checking-configuration” wait a few moments and Execute the GET call again.
- If status is not-connected, check the response for errors that need to be corrected
- Expand
JSON examples
Example one
This example has one scope, which includes all asset types in all regions for all accounts within the AWS Organization.
{
"aws": {
"partition": "AWS",
"roleName": "censys-hosted-connector-role",
"scopes": [
{
"organization": {
"managementAccountId": "123123123123",
"excludedAccountIds": []
},
"excludedAssetTypes": [],
"excludedRegions": []
}
]
}
}Example two
This example has two scopes. The first scope includes all asset types in all regions for all accounts except 789789789 contained within the AWS Organization. The second scope is to scan account 789789789789, excluding the API Gateway and API Gateway v2 asset types and the entire us-east-2 region.
{
"aws": {
"partition": "AWS",
"roleName": "censys-hosted-connector-role",
"scopes": [
{
"organization": {
"managementAccountId": "123123123123",
"excludedAccountIds": [
"789789789789"
]
},
"excludedAssetTypes": [],
"excludedRegions": []
},
{
"account": {
"accountId": "789789789789"
},
"excludedAssetTypes": [
"API_GATEWAY",
"API_GATEWAY_V2"
],
"excludedRegions": [
"us-east-2"
]
}
]
}
}Updated 8 days ago
