Microsoft Sentinel
Access Levels: Advanced | Enterprise
The Censys connector for Microsoft Sentinel (formerly known as Azure Sentinel) enables you to connect Attack Surface Management (ASM) logbook and risk events with Sentinel. This allows you to monitor your attack surface events in the analytics platform of your choice.
Prerequisites
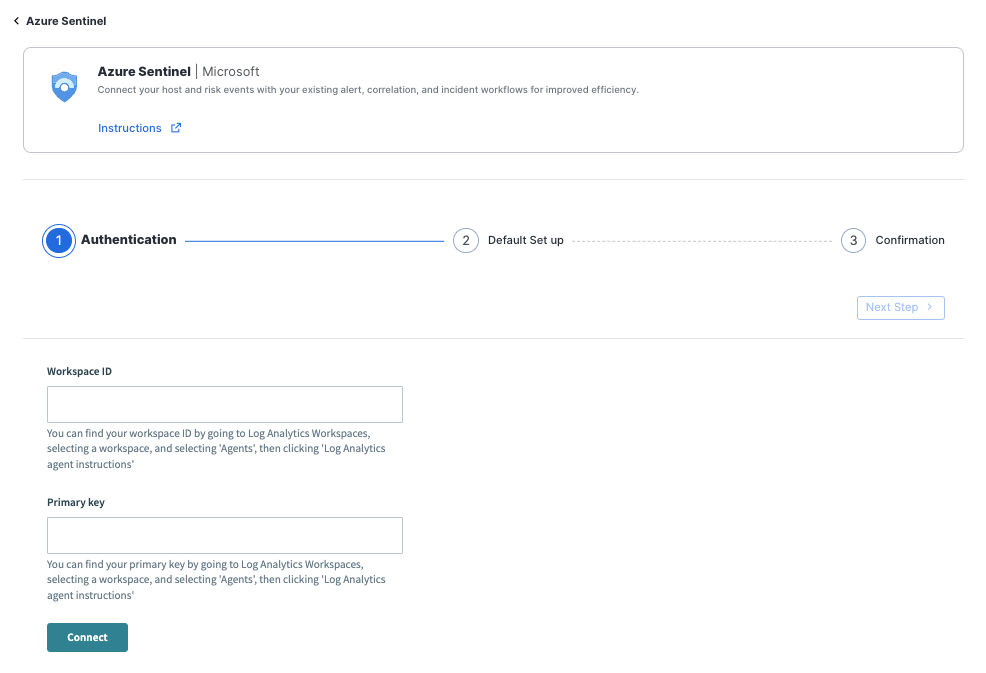
Before you begin, make sure you have your Workspace ID and Primary key from Microsoft Sentinel. To find this information:
- Go to Microsoft Sentinel and navigate to your Log Analytics Workspace.
- Select the workspace, then select Agents.
- Click the Log Analytics agent instructions.
Configure the integration in Censys ASM
- Go to the Censys ASM web console, then click Integrations.
- Locate Microsoft Sentinel and click Set Up.
- Configure the following:
-
Workspace ID: Enter the Workspace ID you obtained from your Microsoft Sentinel Log Analytics page.
-
Primary key: Enter the Primary key you obtained from your Microsoft Sentinel Log Analytics page.
-
- Click Connect at the bottom of the page. Then, click Next Step in the upper right corner.
- On the Default Set Up page, select whether you want to receive logbook events, risk events, or both inside Microsoft Sentinel.
- Click Submit, then click Done.
Modify the integration
If you need to make changes to your integration, follow the configuration steps above.
Query examples
The integration automatically polls Censys for new events, which are sent to Microsoft Sentinel.
Risk events
Open critical risks:
Censys_Risks_CL
| where Severity_s =~ "Critical"
| where Risk_Event_Operation_s =~ "Open"
| where Status_s =~ "Open"
| sort by Last_Seen_tCount of risks by name:
Censys_Risks_CL
| summarize Count = count() by Display_Name_s
| order by Count descLogbook events
Associated hosts:
Censys_Logbook_CL
| where Operation_s =~ "ASSOCIATE"Disassociated hosts:
Censys_Logbook_CL
| where Operation_s =~ "DISSOCIATE"Configuration Options
The following tables detail the objects sent to the custom log analytics tables.
Risk events
| Description |
|---|---|
Risk Event ID | The ID of the Risk Event. |
Risk Event Operation | The Operation of the Risk Event:
|
Timestamp | The timestamp of the risk event. |
Risk Instance ID | Identifier for a specific risk instance. |
Display Name | Human-readable display name for a risk instance. |
Severity | Severity for a risk instance:
|
Status | State of the risk instance:
|
First Seen | Timestamp when the risk was first observed in the workspace. |
Last Seen | Timestamp when the risk was last observed in the workspace. |
Impacted Asset | The asset impacted by the risk. |
Logbook Events
| Description |
|---|---|
Event ID | The ID of the Logbook Event. |
| Event Type | The type of event from Logbook:
|
Operation | The operation of the event:
|
IP Address | The host associated with the event. |
Timestamp | Timestamp when the event occurred. |
Updated 10 months ago
