Identify Unsanctioned Cloud Usage
Many organizations have a list of sanctioned cloud service providers (CSPs) that development, operations, or marketing teams use to run their business systems.
Infrastructure in unsanctioned clouds introduces risk into an organization’s external attack surface because it is often unknown to IT and security teams and not managed.
The following guide explains how to identify hosts in unsanctioned clouds. In Censys Attack Surface Management (ASM), you can detect unsanctioned cloud usage through:
- Cloud Connectors: Utilize Cloud Connectors to differentiate between managed and unmanaged cloud assets.
- A manually curated list: Create a list of sanctioned cloud names used across an organization to distinguish between managed and unmanaged assets.
Use Cloud Connectors
- Configure a Cloud Connector to import external asset identifiers from each sanctioned cloud your organization uses into the Attack Surface Management platform.
- Filter the cloud assets on the hosts and domains lists to assets not present in one of the cloud accounts you connected to the platform.
Identify hosts in unsanctioned clouds
-
From the Dashboard, click the Cloud Assets card.
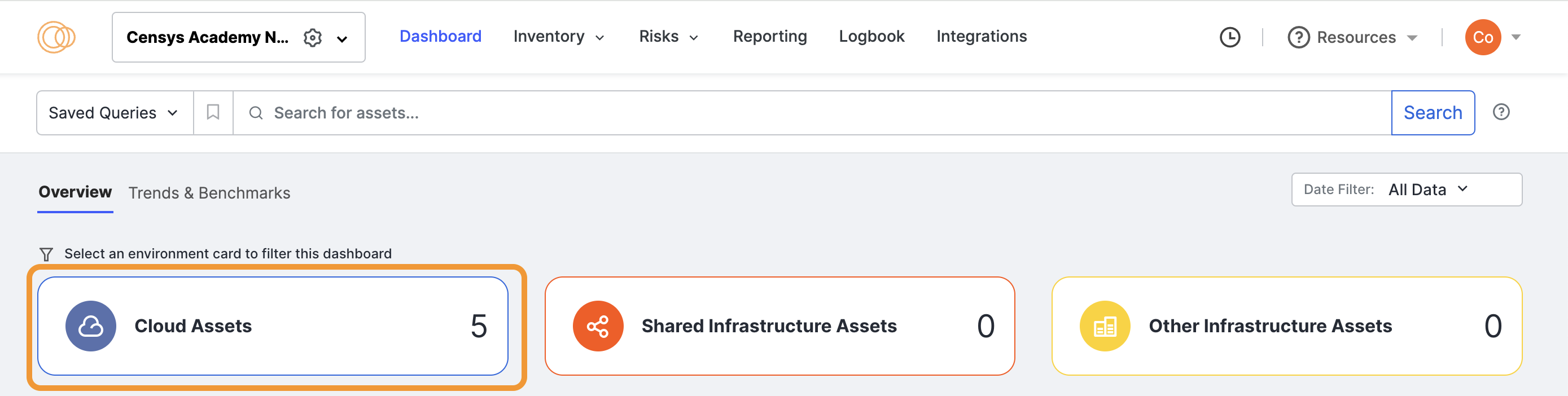
-
Scroll to the Discovery Source area, and click See Hosts Found By Censys Scan to open a filtered view of the Host List page.
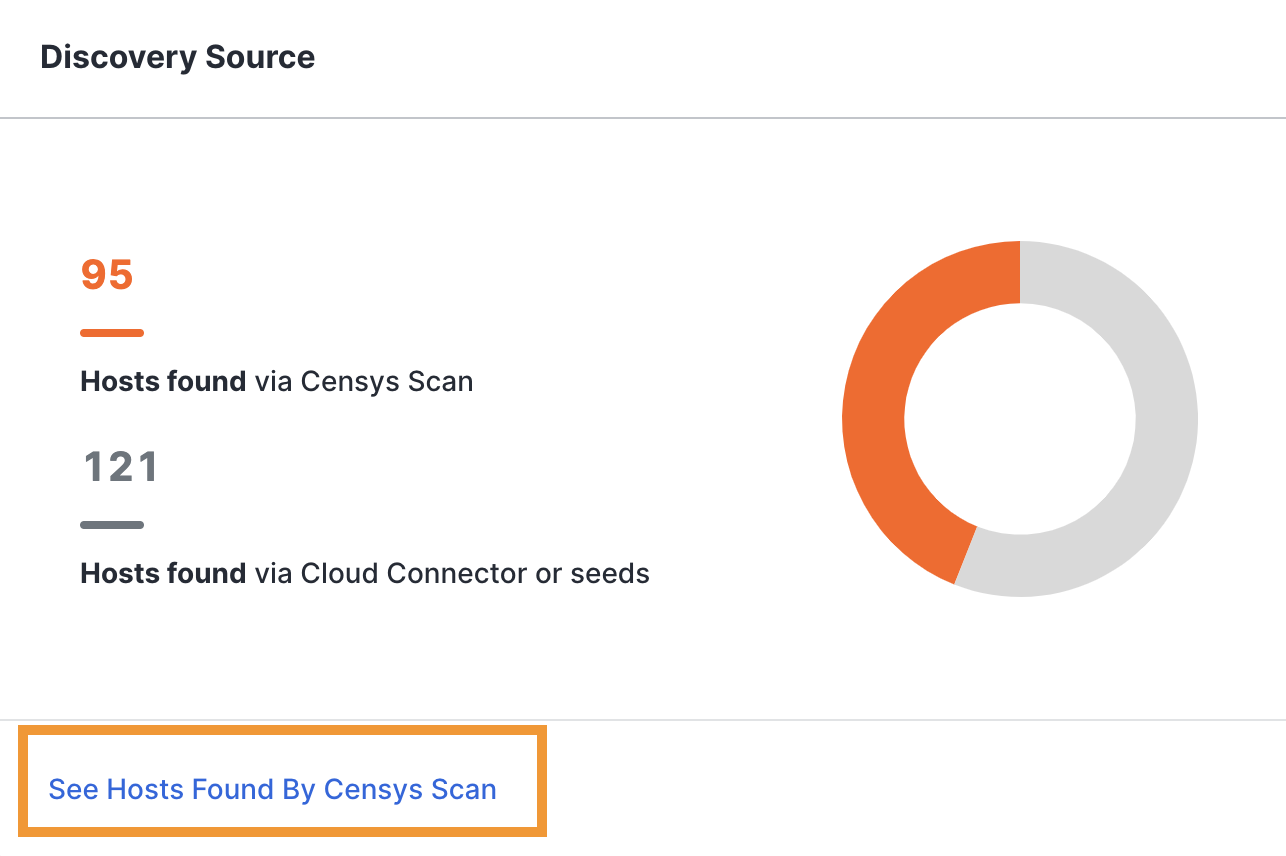
-
Review each of the hosts in the list:
- Determine what it is.
- Find out who is responsible for it.
- Make a plan. Should it:
- Migrate to a known account?
- Be removed?
- Stay where it is with a new IT/security policy?
Identify domains and subdomains in unsanctioned clouds
- Filter the Domains list:
-
Set Source to is not Cloud Connector.
-
Set Cloud Provider to is Any Cloud.
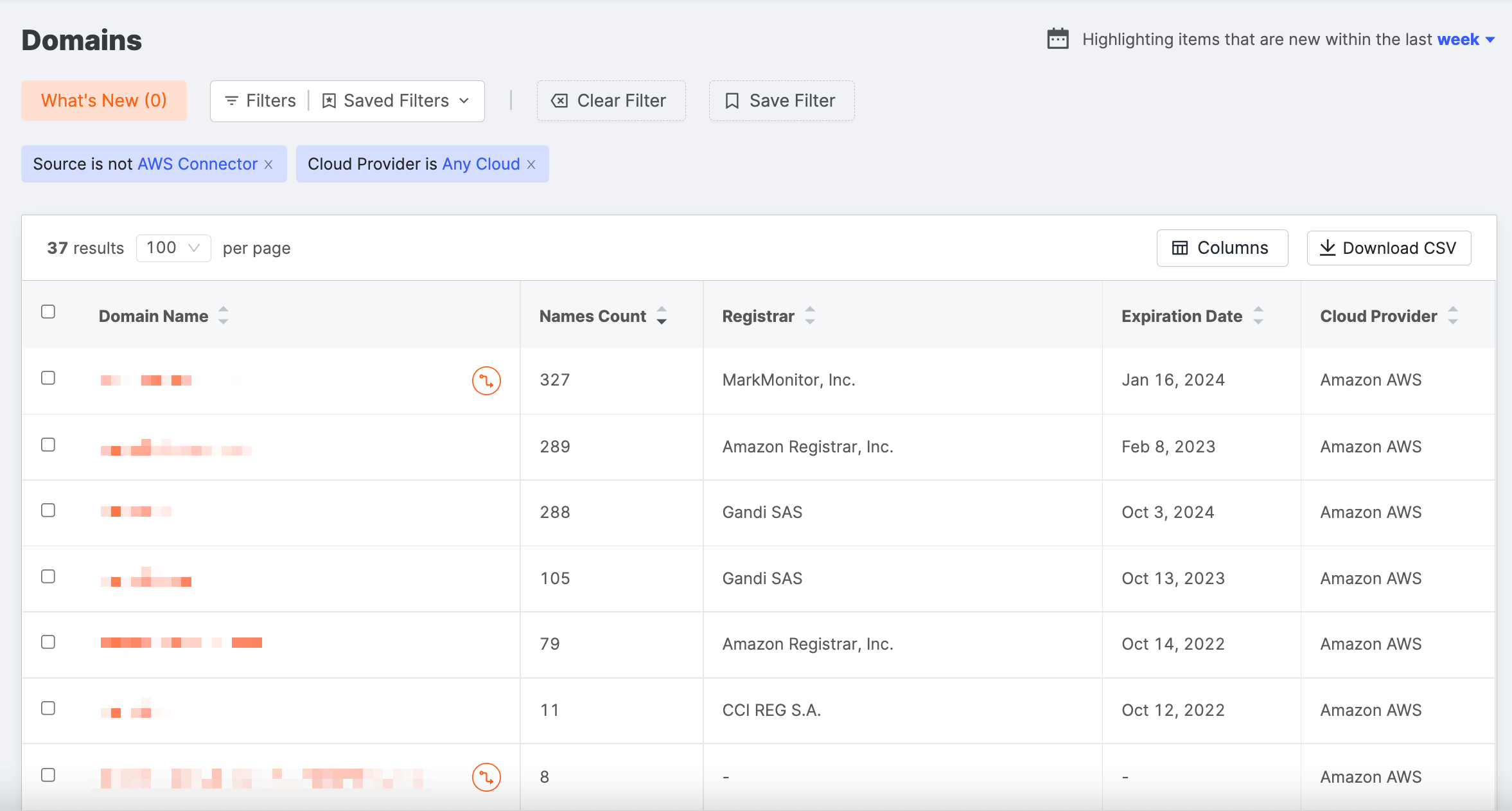
-
- Review each unsanctioned asset. Should it:
- Migrate to a known account?
- Be removed?
- Stay where it is with a new IT/security policy?
Use a list of sanctioned CSPs
If your organization cannot integrate your cloud accounts into ASM, you can still follow the steps above. Use the filters to exclude hosts and domains in your sanctioned cloud providers.
Updated 11 months ago
