October 20, 2025
5 months ago
Summary
- Rapid Response advisory and queries for exposed F5 BIG-IP products affected by recent nation-state breach.
- Threat data now visible for Platform Enterprise customers.
- One new fingerprint for Interactsh servers.
Platform
-
Some threat data for hosts and web properties is now viewable by all users on Enterprise accounts.
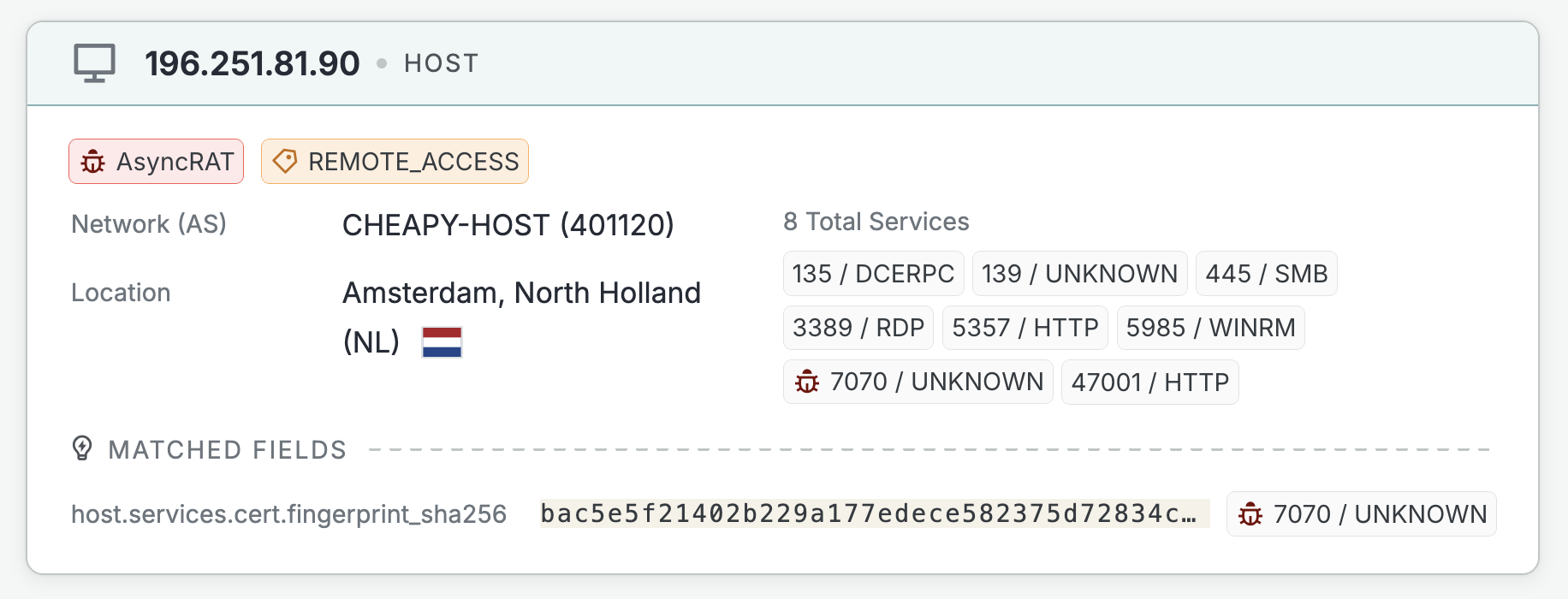
An example search result for a host showing that an AsyncRAT threat is present.
-
The following fields can be seen in the Platform web console and retrieved via API, but may not be searched for or pivoted across unless you also have access to the Threat Hunting module.
Data field Description *.threats.idA unique identifier for the threat. *.threats.nameName of the threat, such as Cobalt Strike.*.threats.tacticHow the threat behaves and the purpose of the activity, such as COMMAND_AND_CONTROLandPERSISTENCE.*.threats.typeThe role of the service, such as PHISHING_SERVERandWEBSHELL.
-
Rapid Response
The Censys Rapid Response team published information about and queries for the following issue.
-
Nation-State Breach of F5 Networks — Exposure of BIG-IP Source Code & Undisclosed Vulnerabilities
- The queries below can identify F5 BIG-IP instances, but they cannot determine whether systems are vulnerable.
New fingerprints
Added the following fingerprint.
| Type | Name | Description | Query |
|---|---|---|---|
| software | Interactsh Server | This is an Interactsh server. Interactsh is an OOB interaction gathering server and client library. | Platform query |
