Summary
- New
cenclicommand line tool to bring Platform features and data to your terminal. - Censys Assistant in the Platform web console for rapid investigations using natural language input.
- Support for integrating the Censys ASM MCP Server with Microsoft Copilot Studio.
- New fingerprints for Ivanti Endpoint Manager, Oracle Cloud Infrastructure Load Balancer, and Oracle Traffic Director.
- One new ASM risk fingerprint for Redis servers vulnerable to CVE-2025-49844.
Platform
-
The
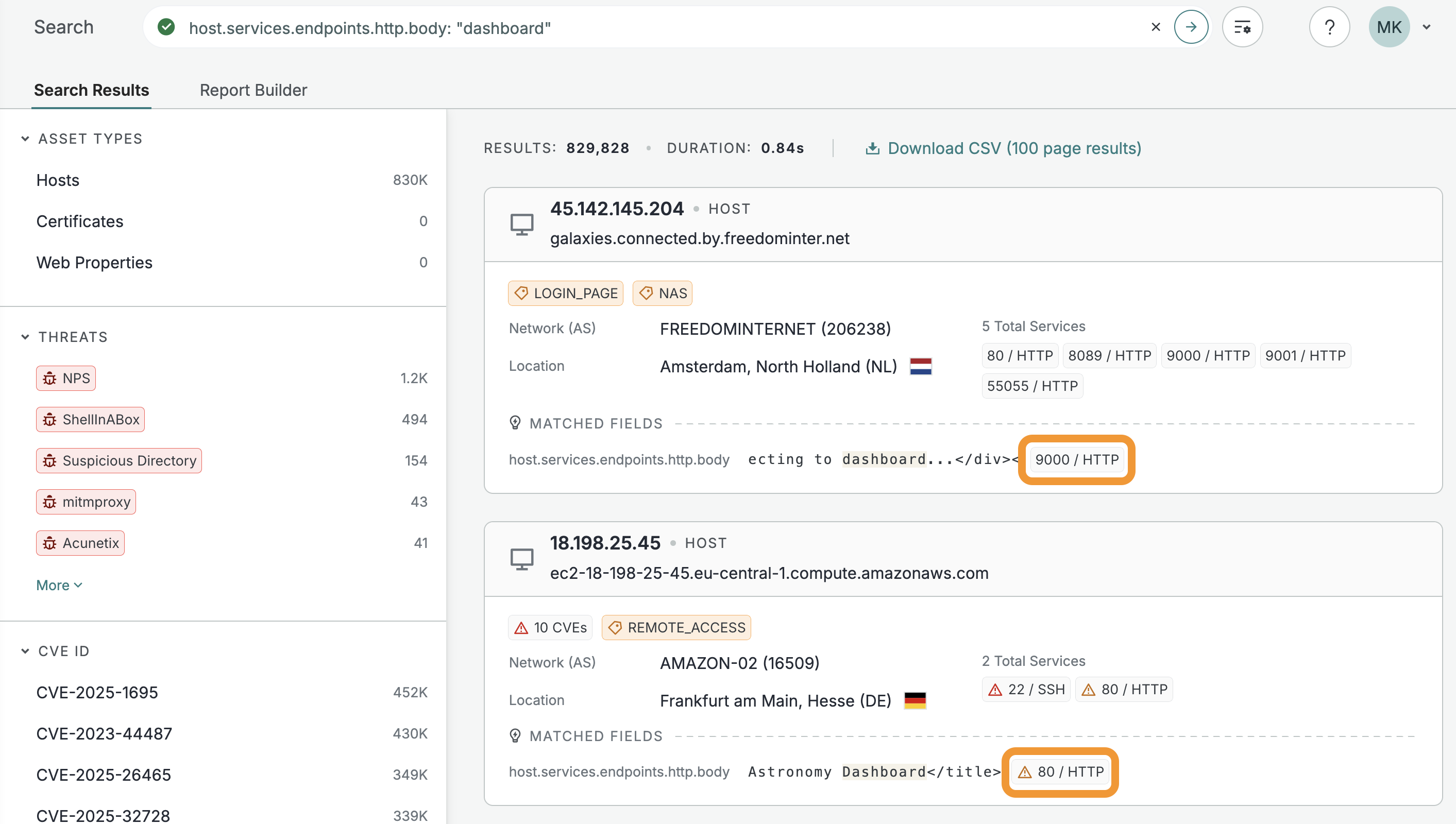
cenclicommand line tool enables you to run search queries, look up assets, perform aggregations, and more from your terminal window.
cenclican be used by all registered Platform users.
-
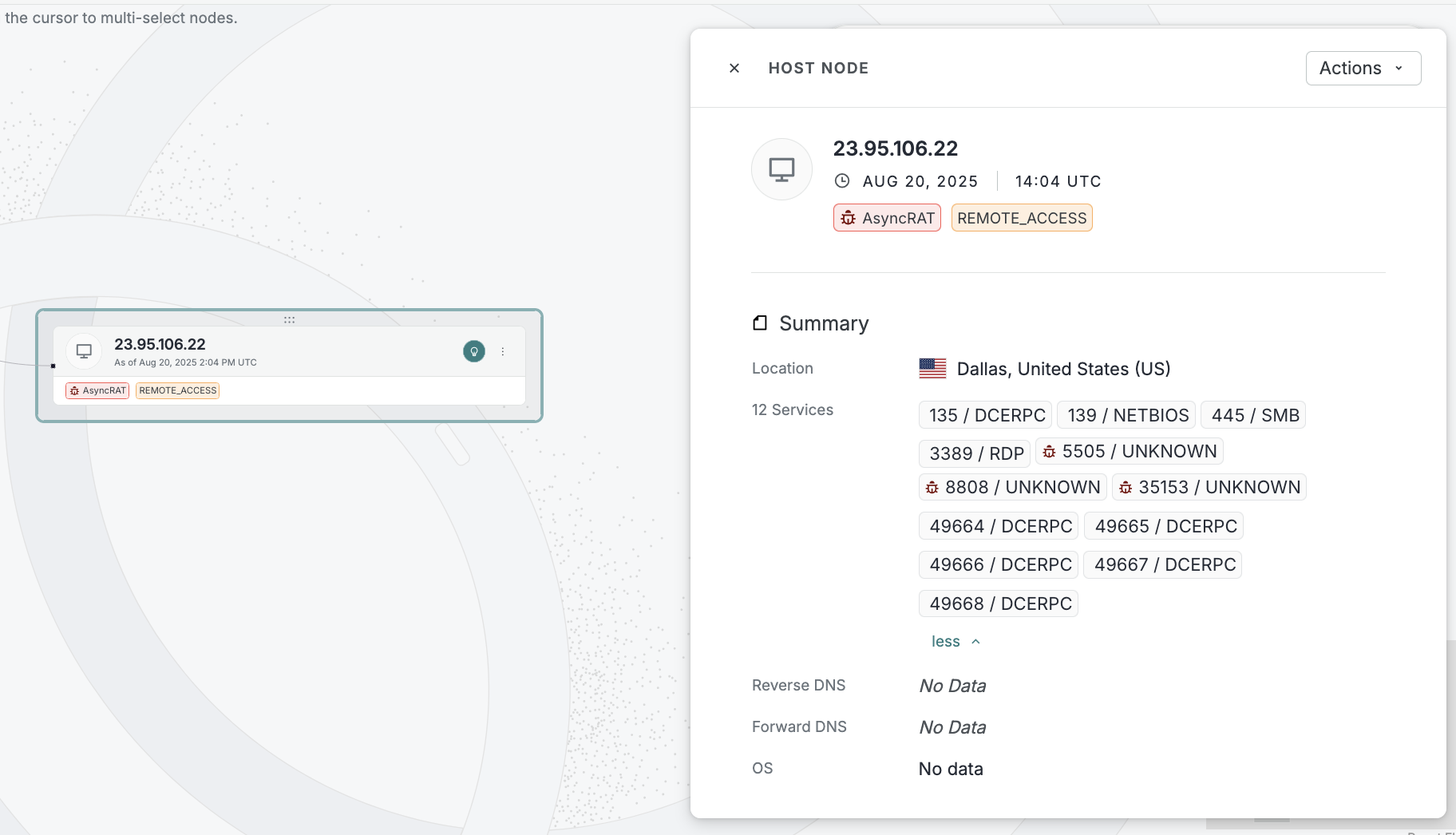
Use the Censys Assistant AI tool in the Platform web console to input questions in a natural language and obtain answers based on the assets and data present in the Censys Internet Map.
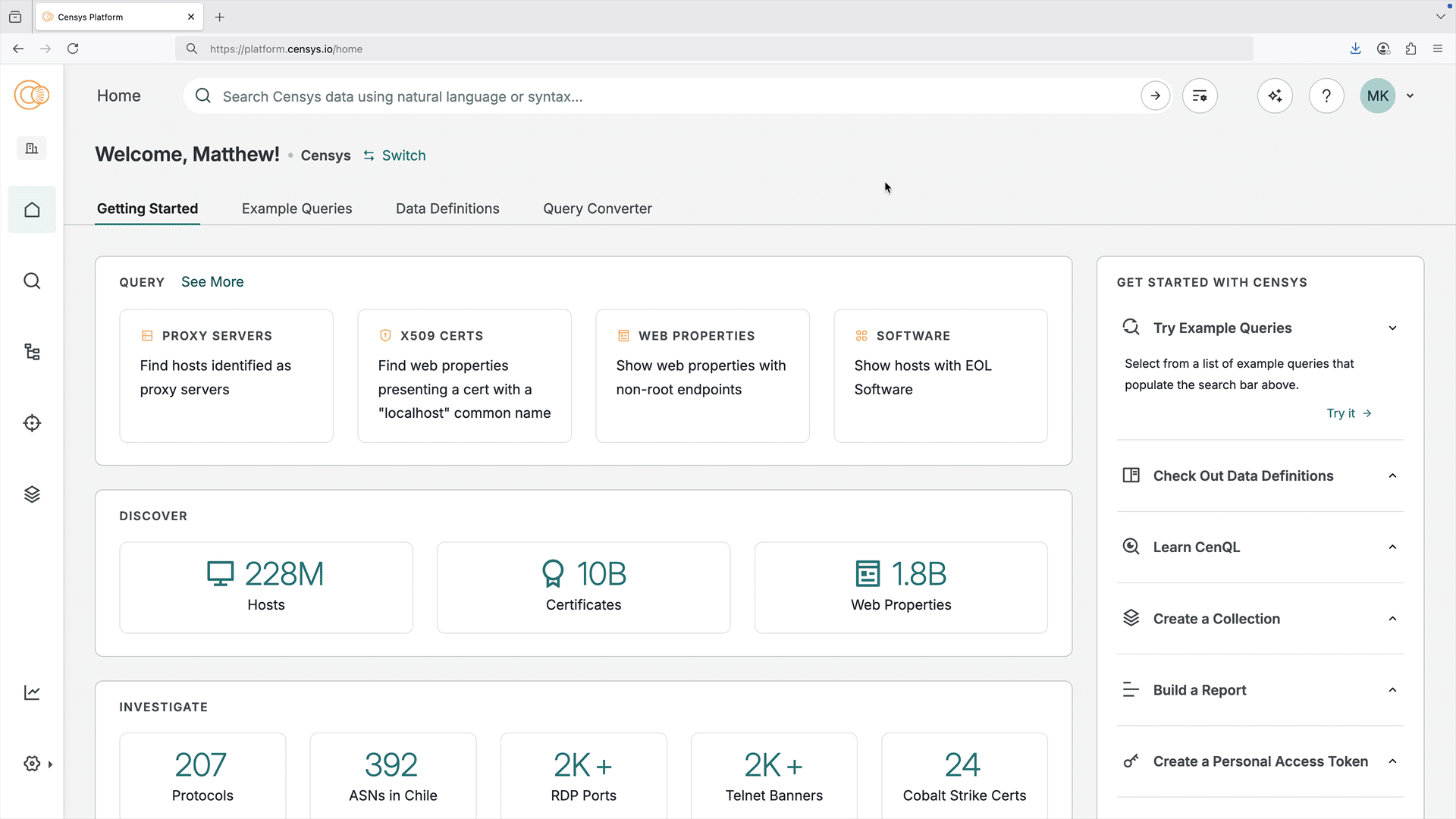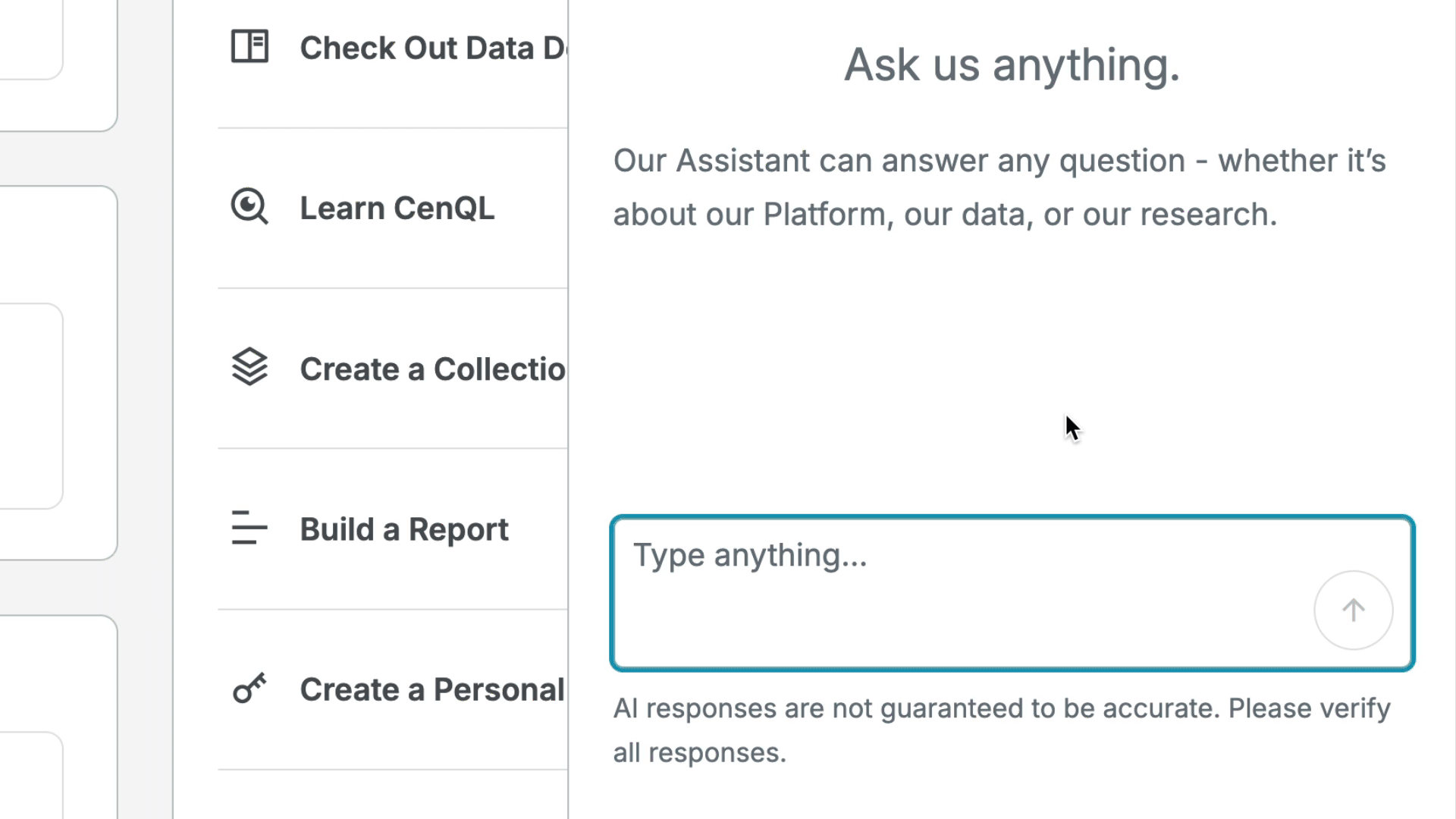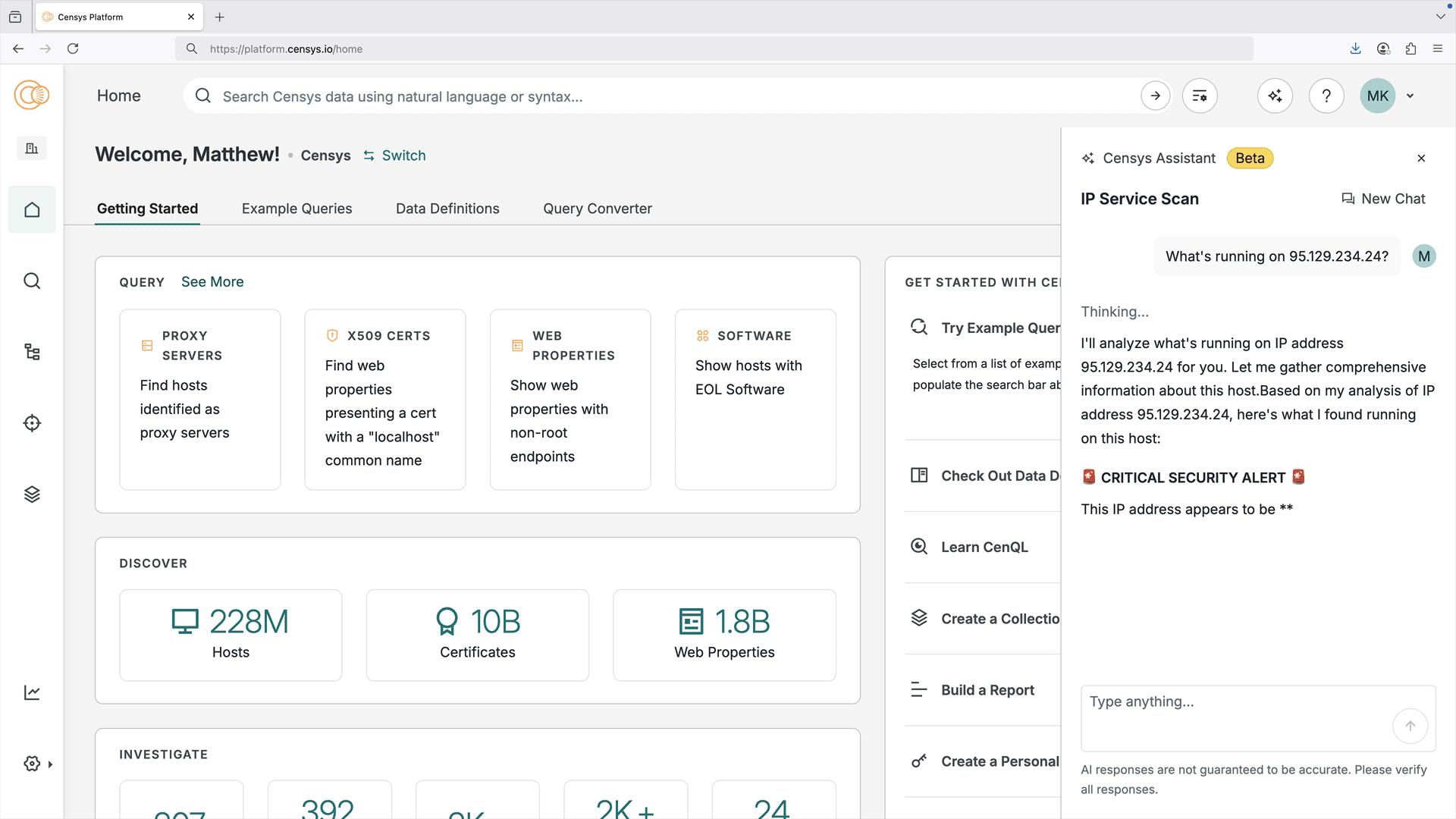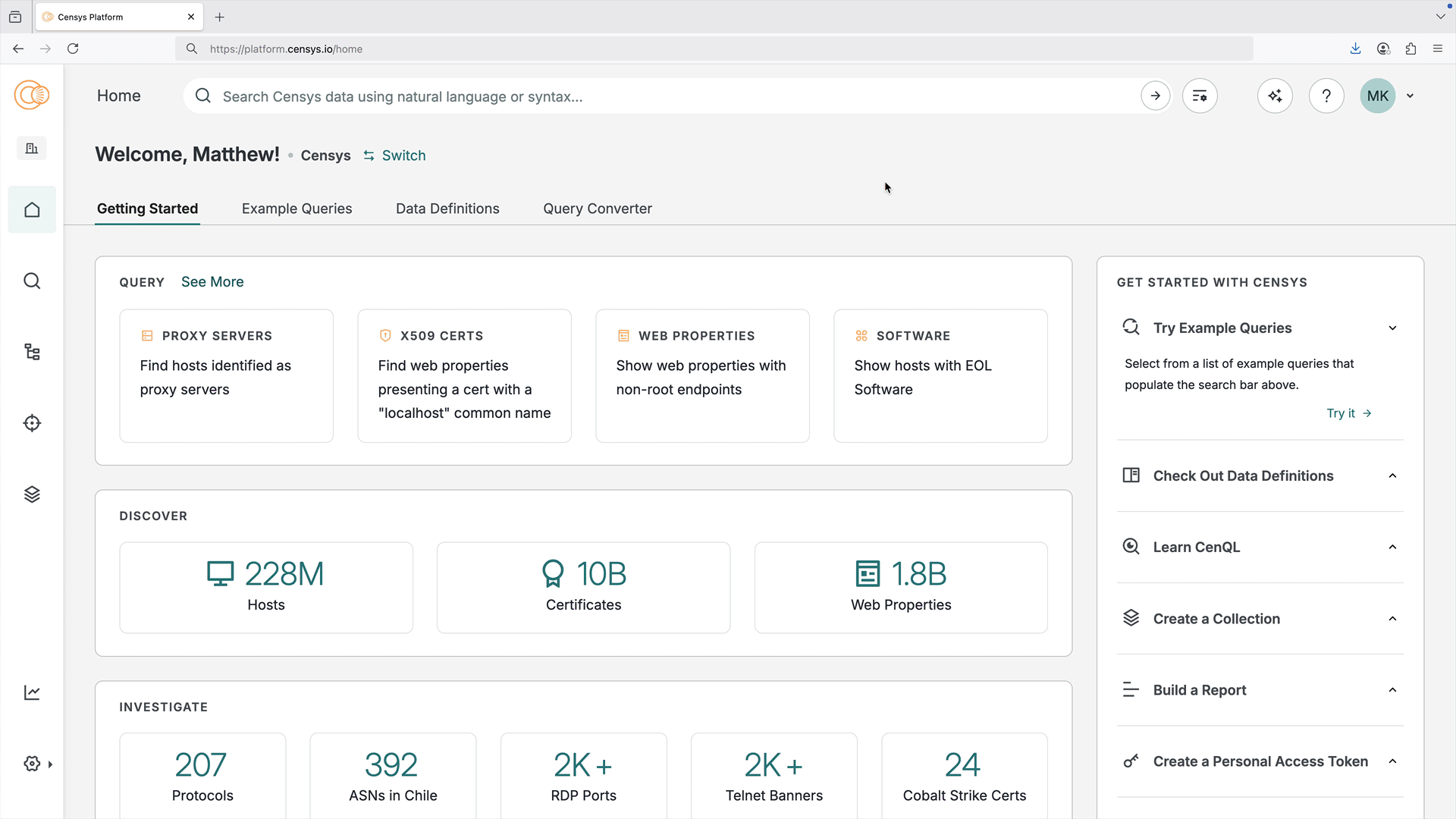
- The Censys Assistant is available to all Starter and Enterprise users.
ASM
- Integrate the Censys ASM MCP Server with Microsoft Copilot Studio to seamlessly incorporate Censys ASM functionality with your AI tools.
Rapid Response
The Censys Rapid Response team published information about and queries for the following issues.
-
Pre-Auth RCE Chain in Oracle E-Business Suite Software [CVE-2025-61882]
- The queries below can help identify Oracle E-Business Suite instances, but they cannot determine whether systems are vulnerable.
-
13 Unpatched Zero-Days in Ivanti Endpoint Manager Enabling RCE
- The following queries can help identify exposed Ivanti Endpoint Manager / LANDesk instances, but they are not necessarily vulnerable.
New fingerprints
Added the following fingerprints.
Type | Name | Description | Query |
|---|---|---|---|
risk | Vulnerable Redis Server [CVE-2025-49844] - RediShell | This Redis service may be vulnerable to CVE-2025-49844 (RediShell), a critical Use-After-Free vulnerability that allows an authenticated attacker to execute arbitrary code by sending a specially crafted Lua script. The vulnerability affects all Redis versions with Lua scripting support (versions 8.2.1 and below) and has existed in the codebase for approximately 13 years. | ASM query: |
software | Ivanti Endpoint Manager | This is Ivanti Endpoint Manager (formerly LANDESK Management Suite), an enterprise endpoint management solution for unified IT operations. | Platform query |
software | Oracle Cloud Infrastructure Load Balancer | This is an Oracle Cloud Infrastructure (OCI) Load Balancer. An OCI Load Balancer provides automated traffic distribution from one entry point to multiple servers in a set. | Platform query |
software | Oracle Traffic Director | This is an Oracle Traffic Director. Oracle Traffic Director is a layer-7 software load balancer. | Platform query |