August 25, 2025
Summary
- New historical hosts for a certificate API endpoint.
- Several enhancements for the Investigation Manager to make it easier to create, navigate, and pivot from investigations.
- A new fingerprint for N-able N-central.
- Two new risks for ASM.
Platform
Threat Hunting
- Use the get host history for a certificate API to retrieve the historical observations of hosts associated with a certificate. This is useful for threat hunting, detection engineering, and timeline generation.
Investigation Manager
-
Added the ability to create investigations directly from host, certificate, web property, and collection pages.
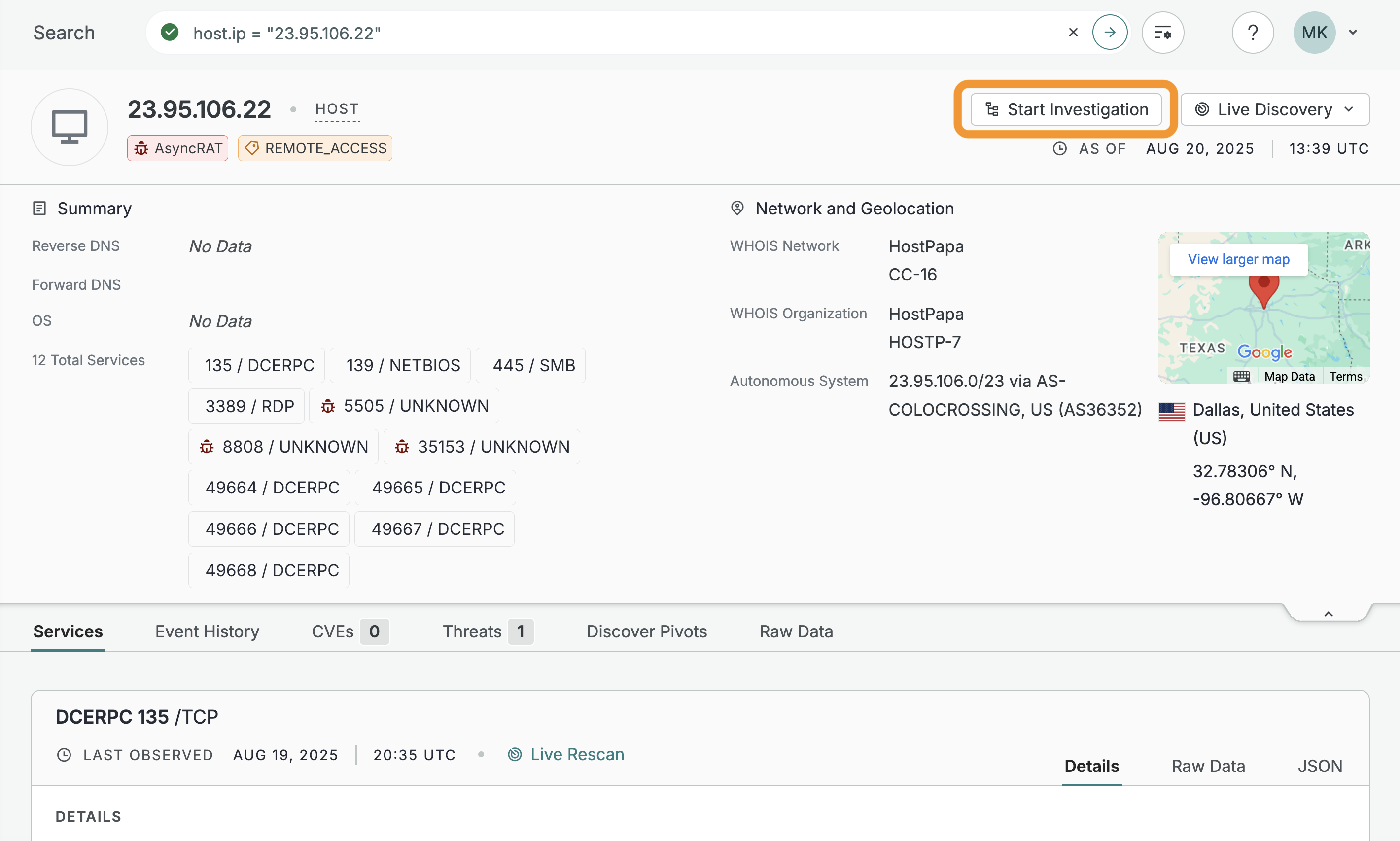
-
Added an asset node details card for hosts that includes geographic location, labels, reverse and forward DNS, service ports and protocols, and more contextual data. This card appears when you click on host nodes in the investigation manager UI.
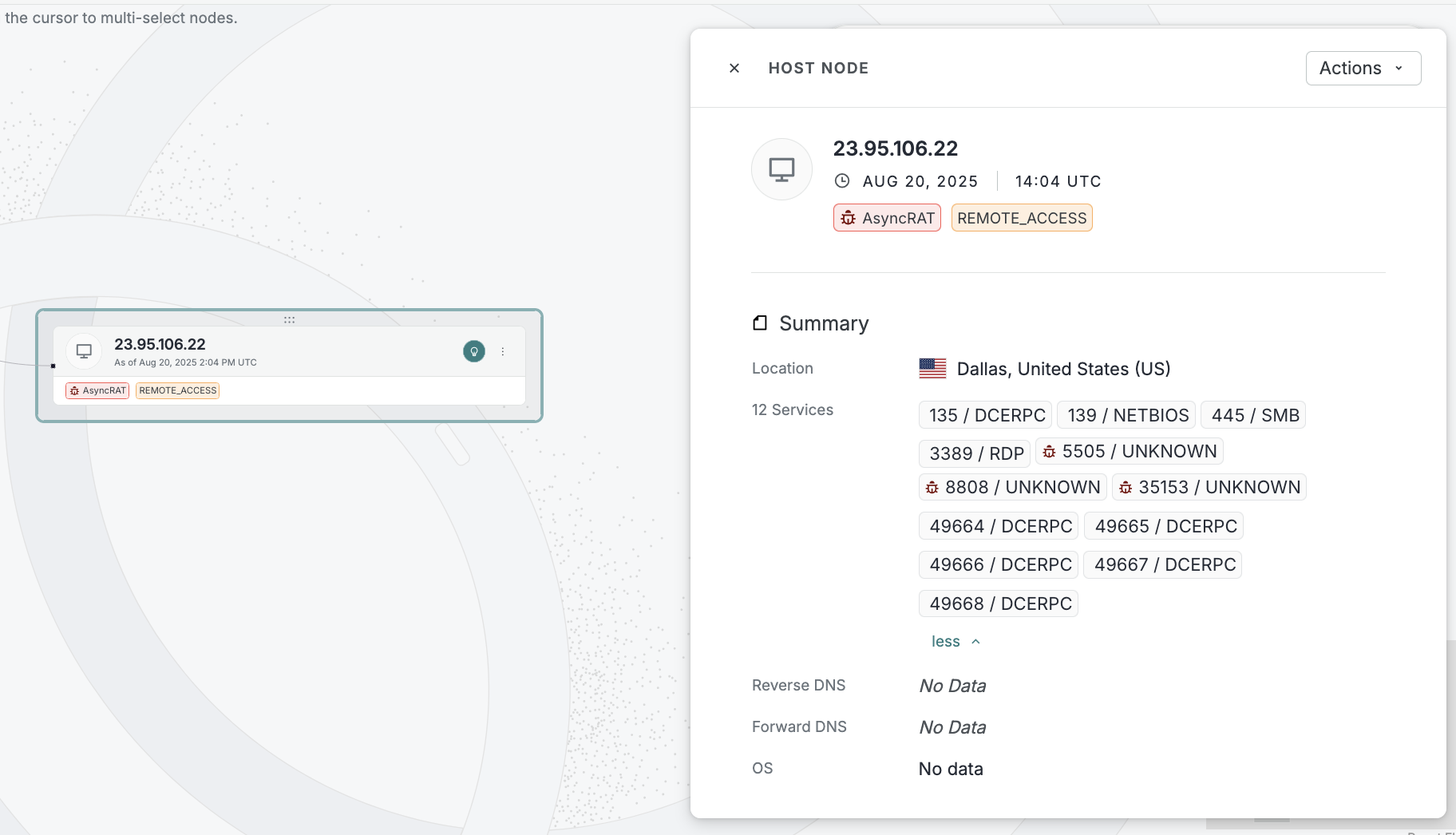
-
Added a minimap to the bottom right corner of the investigation UI to make it easier to navigate your investigations.
Rapid Response
The Censys Rapid Response team published information about and queries for the following issue.
- Plex Warns Users to Patch Security Vulnerability in Plex Media Server
- Use the following queries to find Plex Media Server login portals. Not all of these are necessarily vulnerable.
New fingerprints
Added the following fingerprints.
Type | Name | Description | Query |
|---|---|---|---|
risk | WDBRPC Service Exposed | This service is running WDBRPC (VxWorks WDB Remote Proceudre Call), a debugging protocol used by VxWorks real-time operating systems. WDB enables remote debugging, memory access, and system control of embedded devices. Exposure allows attackers to read/write system memory, execute arbitrary code, access sensitive data, or completely compromise the embedded system. | ASM query: |
risk | Vulnerable N-able N-central [CVE-2025-8875 & CVE-2025-8876] | This is a service running a version of N-able N-central that is vulnerable to CVE-2025-8875 and CVE-2025-8876. | ASM query: |
software | N-able N-central | This is an N-able N-central Remote Monitoring & Management solution. |
