June 23, 2025
CVE risk exploit context in ASM, two new software fingerprints, and one risk fingerprint.
ASM
- Use new CVE risk exploit context data to help you understand, triage, and remediate risks in your attack surface.
- New context data includes risk exploit maturity status, threat actor, botnet, and ransomware enrichment, EPSS scores, and CVSSv4 scores.
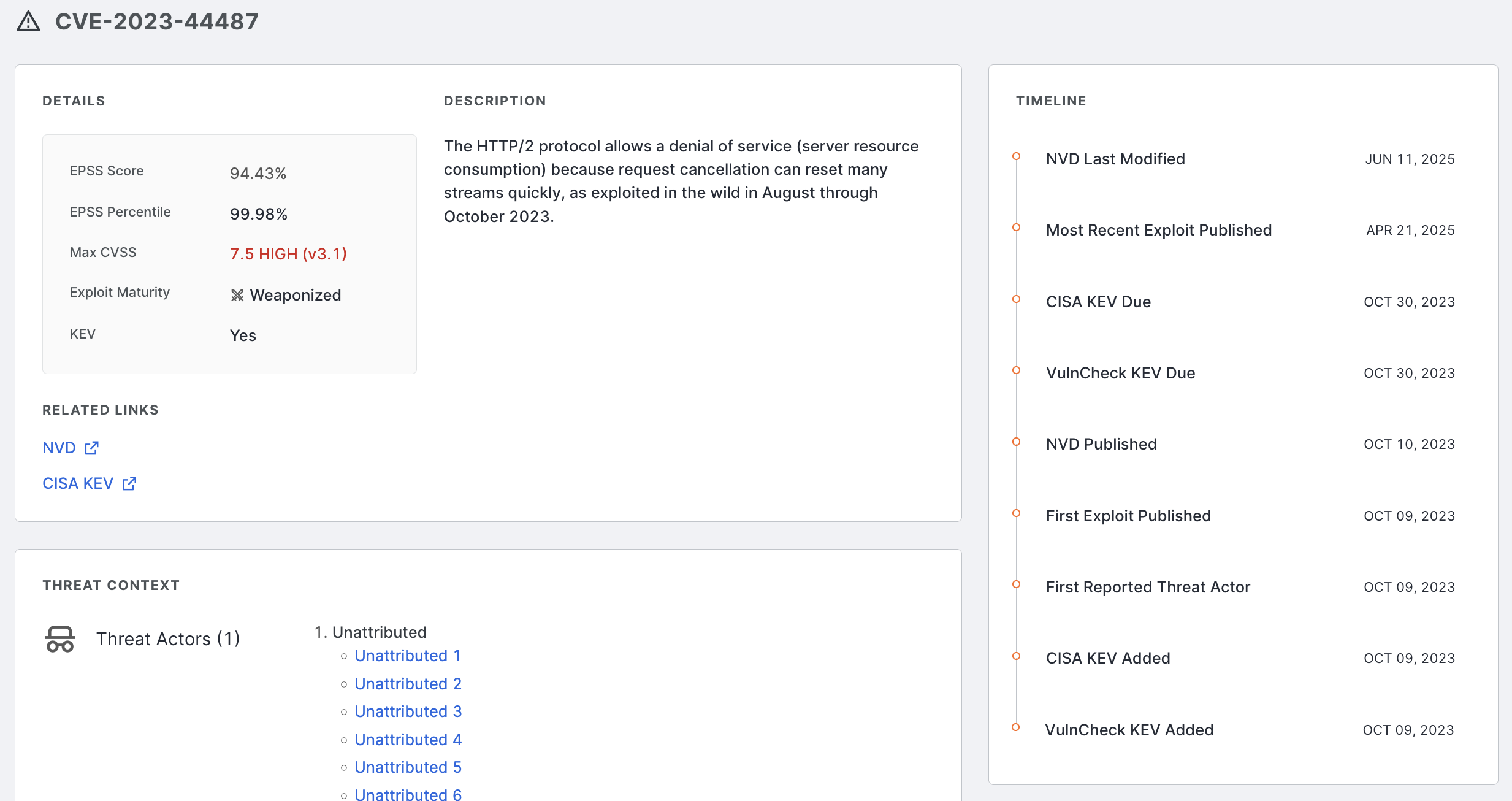
Details, description, and threat context information on the CVE details page.
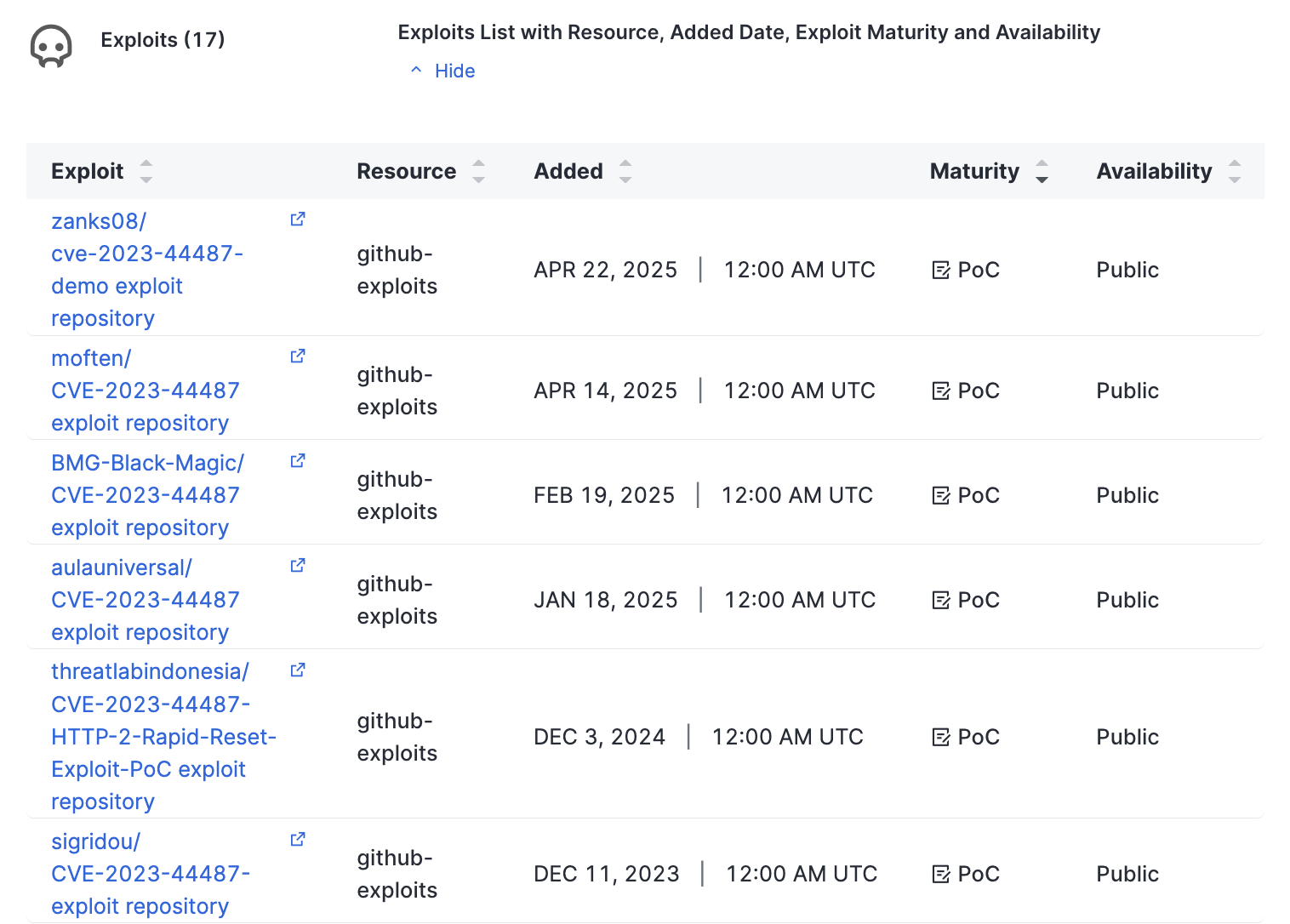
Exploit information and links on the CVE details page.
- CVE risk exploit context is available to all ASM Enterprise customers. ASM Advanced customers may purchase access to it.
- New context data includes risk exploit maturity status, threat actor, botnet, and ransomware enrichment, EPSS scores, and CVSSv4 scores.
New fingerprints
Added the following fingerprints.
Type | Name | Description | Query |
|---|---|---|---|
risk | Vulnerable Erlang OTP Instance [CVE-2025-32433] | This service is running a vulnerable version of Erlang OTP that is affected by unauthenticated remote code execution vulnerability CVE-2025-32433. Prior to versions OTP-27.3.3, OTP-26.2.5.11, and OTP-25.3.2.20, a SSH server may allow an attacker to perform unauthenticated remote code execution by exploiting a flaw in SSH protocol message handling. | ASM query: |
software | Mottech ICC Pro Control System | ICC PRO is a control platform for centralized and remote irrigation management. It communicates with system components to monitor and control sites, providing real-time status and performance data for devices such as valves, water meters, sensors, and pumps. The software supports continuous monitoring and execution of irrigation programs. | Platform query |
software | RainMachine Web Application | RainMachine is a web-based application that allows users to monitor and control their irrigation system from remote devices. | Platform query |
