January 12, 2026
Summary
- Added aliases for Platform threat, screenshot, SHA-1 hash, and organization data fields.
- Deployed several enhancements to the ASM web UI.
- One new software fingerprint for Coolify and one new ASM risk fingerprint for n8n services vulnerable to Ni8mare (CVE-2026-21858).
- Two new Rapid Response advisories:
Platform
- Added the following aliases for Platform data fields:
threatsscreenshotssha1org
ASM
- Several improvements to the ASM web UI were made, including:
-
The workspace selection dropdown is now on the right side of the navigation bar.
-
Icons have been added to many of the items available in the top navigation dropdowns.
-
Scan frequency information is now located at the bottom of the Resources dropdown.
-
Added links to the Integrations dropdown to see all integrations, connected integrations, available integrations, and integrations that need attention.
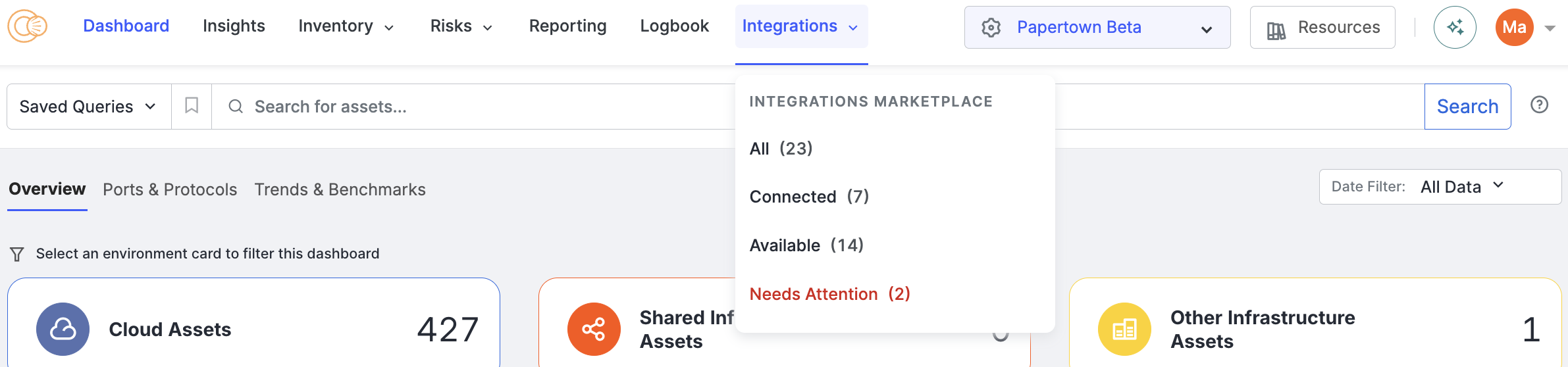
-
Rapid Response
The Censys Rapid Response team published information about and queries for the following issues.
-
Three Vulnerabilities in Coolify Self-Hosting Platform [CVE-2025-64424, CVE-2025-64420, CVE-2025-64419]
- The following queries can be used to identify exposed Coolify instances.
-
n8n Unauthenticated Remote Code Execution (NI8MARE) [CVE-2026-21858]
- The following queries can be used to identify exposed and potentially vulnerable n8n instances.
New fingerprints
Added the following fingerprints.
Type | Name | Description | Query |
|---|---|---|---|
software | Coolify | This is Coolify, an open-source self-hosted platform for managing servers, applications, and databases. | Platform query |
risk | Vulnerable n8n (Ni8mare) [CVE-2026-21858] | This is a service running a version of n8n workflow automation platform that is vulnerable to CVE-2026-21858 (Ni8mare), a critical unauthenticated Remote Code Execution vulnerability caused by a Content-Type confusion flaw in the webhook and file handling mechanism. Attackers can exploit this by sending specially crafted HTTP requests to form-based workflows to read arbitrary files, extract credentials, forge administrator sessions, and execute arbitrary commands.. | ASM risk query: |
